Living in a Connected World/Print version
| This is the print version of Living in a Connected World You won't see this message or any elements not part of the book's content when you print or preview this page. |
The current, editable version of this book is available in Wikibooks, the open-content textbooks collection, at
https://en.wikibooks.org/wiki/Living_in_a_Connected_World
The Online Real-Life Divide
[edit | edit source]Introduction
[edit | edit source]he introduction of technology as we know it has brought about a new understanding of how we comprehend both ourselves and our interaction with others. This struggle with identity displays itself through the use of social media platforms and the choices made in regards to how one presents themselves to their "followers" or "friends" as well as the information they choose to share. Every social media account is a construction of identity that brands an individual and how they present themselves under a specific presentation. This display of the self through public and private personas can often lead to a blurring of the line between private life and public account, and as a result the individual's identity is altered through their online, marketed self, leading to questions of identity, self-presentation, authentic representation, and community pressures. As well as this, with modern technology the line between what constitutes 'the online' and consequently what constitutes real-life is ever changing and evolving as our understanding of the use of technology changes.
This chapter will highlight the history behind today's technological wave and consider the various platforms through which identity is divided. It notes the pros and cons of anonymity online, singular and fragmented identities, theories associated with the digital divide, as well as covers the effects that this divide has on society and the self.
History and Application of Digital Media
[edit | edit source]History of Digital Media Development
[edit | edit source]The conceptual work of digital media can be traced back to the scientist and engineer Vavennar Bush and his work “As We May Think”, published in The Atlantic Monthly in 1945. In this essay and “Memex Revisited” (1967) Bush envisioned a device which allows us to compress and store knowledge, which memorizes everything, and builds as well as combines trails [1] with exceeding speed and flexibility, the so called Memex. [2] “If we wish it, a whole private library could be reduced to the volume of a nutshell” [3], writes Bush about the notion of his Memex. Moreover, he assigns the computer to aid humans by storing and providing data, to engage with us and even to be our gaming opponent in chess. Bush predicted different technology invented after his publications such as personal computers, speed recognition, the World Wide Web and online encyclopaedias such as Wikipedia. The Memex would mimic a human’s mind and its associative process, hence it would be a Technology as an Extension of Self.
First Analog Computers
[edit | edit source]In the early 19th century Charles Babbage, an English mechanical engineer conceptualized the first Machine-readable codes and information. He invented the first mechanical computer, The Difference Engine, which he designed to detect and solve the problem of error in calculations. Ada Lovelace, a mathematician, wrote the first instructions for Babbage’s analytical machines for calculating numbers, which are considered to be the first computer program. [4]
Digital Computers
[edit | edit source]
Digital Media itself emerged with the rise of the Digital Computers. Whereas analog computers consist of physical and mechanical parts only, digital computers use a binary code and Boolean algebra. It is a system consisting of ones and zeros, the “digits” of digital media, that combined can make hundreds of characters to store and process information. The first digital computers were the ABC invented by John Vincent Atanasoff and the ENIAC by J. Presper Eckert and John Mauchly between 1942 and 1946. [5]
Digital Revolution
[edit | edit source]“But aren’t we living in a world where knowing how to get information is more important than memorizing it? Aren’t we moving away from an industrial economy into an information one?”[6]
Michael Mandiberg, an American programmer and educator, writes about the shift between media creators and consumers and the collective transformation from an industrial economy to an information-based economy, known as the Information Age. [7]
Since the invention of the first digital computers continuing to the present day the Digital Revolution keeps exponentially expanding and improving modern digital media. Personal Computers, smartphones, and the latest innovations surpass each other in computing power and storage capacity and make it possible for billions of people to access, modify, store and share digital media. Combined with the Internet and the World Wide Web, digital media has enabled a shift from a one-to-many to a many-to-many communications capability [8]as well as networked media. The rise of Digital Media demands a new way of communication, called transliteracy, media literacy, or digital literacy. [9] Other than in the traditional literacy these skills do not only include reading and writing but the abilities to evaluate sources, navigate the internet and create digital content . [10] This change within the 21st century towards a Digital Age is frequently compared to the impact of the printing press[11]and the fear of a paperless society accompanied by the many challenges of copyright laws, censorship, the digital divide[12] and the idea of a digital dark age.[13]
Future
[edit | edit source]More than 20 years ago Bill Gates , co-founder of Microsoft, predicted the technological changes and the advances affecting our lives such as the beginnings of the internet and the interconnectivity of personal computing in his book “The Road ahead”. [14], which we are still undergoing today. With the rise of the Information Age and the growing importance of Digital Communications Media and Multimedia Platforms the human behavioural norms and social values may have changed. The next step could be directed to create a fully 'always-on' world as Mark Zuckerberg, CEO of Facebook, plans on expanding the boundaries of the internet and to put every person online. In essence, to provide everyone in the globe an affordable, basic access to the internet service. Zuckerberg expects to do so through the use of wireless drones, satellites and lasers. [15]
The Evolution of Digital Culture
[edit | edit source]Jill Walker Rettburg, in her article "Written, Visual and Quantitative Self-Representations" [16] suggests that "there are three distinct modes of self-presentation in digital media: written, visual and quantitative." She goes on to suggest that each of these modes has a specific and different pre-digital history. Diaries, memoirs, books and autobiographies are the antecedents of today’s blog posts and written social media status updates; selfies, for example, have taken over from visual artists’ self-portraits. Quantitative modes - those which feature personal statistical data previously found in lists, graphs, and maps - have been replaced with spreadsheets and GPS activity trackers. Despite the variety of digital and pre-digital methods of self-presentation, Walker Rettburg emphasises the concept that "technology is a means to see part of ourselves," whichever form that might take.
“The assumption is that we’re addicted to the technology. The technology doesn’t matter. It’s all about the people and information. Humans are both curious and social critters. We want to understand and interact. Technology introduces new possibilities for doing so, and that’s where the passion comes in. We’re passionate about technology because we’re passionate about people and information, and they go hand in hand.” [17]
Following Mandiberg’s assumption and the notion of technology as an extension of ourselves together with the rapid development of our digital media, it changed our culture, our everyday behaviour and our social engagement on every level possible. How the different mediums work and which effects the connected world has on ourselves, our identity, self-representation and our perception of each other is discussed in the sections below.
Media
[edit | edit source]Social Media
[edit | edit source]Man is least himself when he talks in his own person. Give him a mask and he will tell you the truth—Oscar Wilde[18]
The concept of the social networking site (SNS) has become popular in the culture of the mid to late 2000s and as such is often linked with the creation of platforms such as Myspace and Facebook, however its origins date back several years prior, to the late 1990s.[19] The understood concept of a social media platform that introduced both a sense of community through friends as well as a sense of individualism through profiling was Six Degrees. Six Degrees was a website marketed as a tool for connection with friends that launched in 1997 and lasted until 2001, when it was shut down.[20] The basic layout of the site consisted of a personal profile for each user, an ability to add friends and, after 1998, the ability to search through lists of friends. Six Degrees, although the first to combine the personal features with a community aspect, crashed in late 2000 due to what the founder believed as being "simply ahead of its time".[21]
Following the creation and failure of Six Degrees, the launches of Friendster and Match.com began a competition involving online community growth. Both websites introduced an emphasis on the individual profile and gained popularity through their specialization in online dating. The issues in fidelity led to the decline of both websites, specifically Friendster as it gained the reputation for "Fakesters", those who created false profiles using the images of others in order to draw people in. Friendster's system experienced several difficulties as the website saw more traffic than expected and was one of the first social networking sites to see one million users.[22]
The website often credited with the introduction and popularity of social media platforms is Myspace. This website launched in 2003 and, after the announcement that Friendster would begin asking a fee of its users, gained a large amount of attention from previous users of other SNS platforms. Myspace gained popularity for being a community that accepted the outcasts of other platforms, noteably indi-rock bands who had been previously removed from other social networking sites. While Myspace was not designed with the intent, their acceptance of these rock bands led them to gain a connection with music that brought them a new demographic of users - teenagers.[23] The Myspace battle for users began to decline as the website became associated with false personas and sexual predators. As the concerns of identity rose in 2005, in came a new platform that gained the attention of the population: Facebook.
Facebook rival Myspace is about being someone fake on the internet...[it's] very healthy that the real people have won out over the fake people—Peter Thiel[24]

Facebook was created in 2004 by Mark Zuckerberg as a Harvard based networking site that was expanded to include other university students across the United States and later, in 2005, high school students, professional workers, and other individuals. The website encouraged community growth and offered a privacy option to all members that protected a portion of an individual's profile from outside attention. An aspect of individuality was created through profile creation as Facebook targeted not only basic biological facts about its users, but offered the ability to personalize one's profile to include likes and dislikes such as movies, shows, books, and music.[25] Facebook's defining trait came from its emphasis of the "true self", encouraging users to portray their personalities through their online posts with no disguising usernames or alternate identities that had been created on previous SNS platforms. Facebook, unlike its competitor Myspace, encouraged a single identity that synced with the legal information of an individual one was given at birth. This emphasis on the individual, true self came about as a response to the 9/11 attack that took place in New York on September 11, 2001.[26] The unity of oneself contrasted the previously understood "escapism" of taking on a different persona online.[27] The previously therapeutic location to present another side of oneself became a place in which professional and private self became blurred. Facebook identities displayed an understanding of an individual as their "best, fastest, smartest"[28] self and began the societal drive to self-realization as a deeply embedded concern.
Facebook, although a social media platform for building community, has often been linked to personal archives and noted as a modernized version of scrapbooking.[29] Although the main purpose behind the website is a social aspect, it has been suggested that Facebook posts often have an archival aspect to them as they mark an event or moment of one's life that can later be reflected upon and celebrated. Both platforms also depict an image of one's life that has been carefully selected to portray a version of the self to others. With the development of Facebook, the SNS platform offered multiple variations to display one's individuality through the selection of "bumper stickers" that would decorate one's page with bands chosen by the individual. These "bumper stickers" often coincided with the "likes" and "fan pages" individuals prominently displayed on their profile. The combination emphasized select traits carefully chosen to portray a slightly augmented version of the self.
Instagram launched in 2010 as a free photo-based application that offered individuals the opportunity to edit and share photographs taken from their mobile devices. [30] The mobile app offers a live connection with followers as photographs can be taken and instantly uploaded with the option of editing through a filter before posting. This instant picture upload is then able to be liked and commented on by followers, similar to Facebook but with a higher emphasis on the visual aspect of one's life as well as quick and easy access.[31] The company was bought out by Facebook in 2012 and as such now offers a link to Facebook profiles when joining the Instagram community. Instagram posts are therefore able to be posted directly to Facebook, connecting the communities of both applications and steadying the single identity enforced by Facebook accounts.
Instagram offers a similar "scrapbook" layout in marking moments of one's life through pictures displayed for followers or personal satisfaction. All pictures have the option of being geo-tagged, marking the location the image was taken as a way of noting the event that took place. Instagram offers an altered reality through the filter option available to all photos before being published. Individuals are able to not only select what pictures they wish to post, but they are able to alter them to depict a mood or change the quality of the picture. In relation, personal pictures (aka "selfies") of the user are occasionally posted with the comment "#nofilter" to display the beauty of the object in the posted image and emphasize the lack of editing done. This displays how society has grown to associate pictures with editing as the natural assumption has become alteration and clarification is now only needed for unedited material.[32]
Snapchat
[edit | edit source]Snapchat, launched in 2011, is a visual-based application that originally allowed users to send pictures and videos that "disappeared" in seconds. The origin of this app was to emphasize the true self in the moment and allow life to be shared with friends.[33] Through the development of the app, pictures are now able to be saved to one's "memory" as well as posted on one's "story" that is visible to all snapchat contacts. Development has also introduced photographic and video filters that offer a voice alteration and the option of sharing pictures for up to ten seconds at a time. Snapchat now offers an option to follow the stories of news, celebrities, and current events, alongside its original concept of a friend-based platform.[34]
Snapchat's focus on the instant appeals to a youthful demographic as it offers the ability to maintain relationships over long distances through pictures and videos that share a moment over distance and time. Snapchat also offers an escape from the concerns of identity management that other forms of social media contain.[35] Snapchat is similar to face-to-face interaction in its lack of permanence. Similar to a conversation, messages and images disappear and, aside from a brief moment of presentation, the message will likely be forgotten. With written forms of communication through social media one offers up a message that is meant to permanently be on display and will therefore present a part of their identity through their comment or reaction. Snapchat's creation appeared during a time of high anxiety regarding pictures and data of oneself on the internet. The ability to quickly send and receive pictures that "disappeared" offered an answer to the concerns of the public.[36] This answer provided people a safe location to send quick shots of their lives without the fear that it would be held against them for a longer period of time.
Gaming and Virtual Reality
[edit | edit source]This "escape from reality" that virtual reality in gaming has had such a large impact on society. It can effect how people feel about themselves, with research showing that a taller avatars can make a player feel more confident out with play as well as a smaller avatar doing the opposite. [37] As entire culture though, the Japanese culture has seen an actual affect on their country, in a vice documentary [38] "The Japanese Love Industry", the lead of the video explores and discusses the severe decrease in population due to things as the gaming culture with government surveys showing that "more than 60% of men aged 18-34" are single, talking how it is because of the generation's obsession with virtual reality and gaming. Saying they "prefer cyber girlfriends over real girlfriends". This kind of behaviour, combined with a lack of interest from the female side has had a direct effect on Japanese culture. It is an example of a society that would rather live inside, or through their screens rather than engage in the world around them.
Avatar Creation
[edit | edit source]Online gaming communities present an escape from the real world into a simulated and controlled environment. With the introduction of gaming avatars, researchers began to look into the blurred line between real and fantasized environments and personas in regards to the link to identity creation and presentation. A lead researcher in the area of multi-user domains (MUD's) is Sherry Turkle whose research in 1995 considered the self as "not singular and unitary, but multiple and fragmented".[39] This discovery of a fragmented self led to the conclusion that MUD's were a source through which one could display multiple personae and highlight the various aspects of oneself. The ability to create an avatar to exact details provided users an opportunity to create what they envision as their "true self" by displaying the characteristics that they often chose to hide. Avatars "give expressive freedom over an otherwise anonymous and static online presence"[40] and provide a unique sense of self to the individual playing the game. Avatar appearance has been linked to self-perception for the owners of these games and characters. It has been found that those who choose more attractive and taller avatars are often linked to more confident actions and far more likely to approach others of the opposite gender.[41] The use of physically ideal avatars leads to an alteration and experimentation in identity which "is often understood through acts that dislocate embodied identity from the self online and how such a dislocation enables one to enact multiple, contradictory identities"[42]
Turkle's research has been highly contested as others have argued for the extension of the singular self through an idealised visual version in avatar creation.[43] Turkle's argument offers the avatar as an alternate self through which one can express characteristic through physical features in a fantastical manner (such as skin colour, size, shape, human, animal, alien, etc), however her approach has been commented as being an "over-fragmented depiction of the avatar-self relationship"[44] and researchers have suggested that gamers often have one or two avatars whose physical creation is meant to represent the idealised version of themselves and in turn provides users with confidence when interacting online. The avatar, although based on the self, acts as a tool to create distance between the user and those they associate with in online gaming communities. It should be noted that the connection of the self with one's avatar is often a link that is manifested in the real world through an aspect known as cosplay. Cosplay allows individuals to dress like characters from games, movies, comics, and other fantasy universes in an attempt to connect with the character and other like-minded individuals in similar communities. Cosplay is common at conventions and can be viewed as the real-life complement to avatars. While online avatars hide one's true identity and allow for the emphasis of certain aspects of one's personality, the same can be said for cosplay within a physical world environment.
Second Life
[edit | edit source]
Second Life is a virtual reality game created in 2003 that offered a world in which there was no goal to be achieved, merely a reality for the player to self-create. Players in Second Life are represented through avatars that are created upon registration of the game. These avatars, known in the game as residents, are capable of being whatever form the user chooses (human, animal, abstract figure) and can appear as the user's physical appearance or another figure entirely.[45] Avatars act as the player's extension providing a self that is aware and controlled by the member. These avatars are capable of interaction with each other, places, and objects; similar to real life experience. Second Life offers an extension of reality through the ability to explore the world, meet others, join groups and communities, set up shops, and buy and sell virtual property.
Second Life provides the user an opportunity to live their life in a different manner, beginning with the creation of their "other self" or avatar. The naming of your other self creates a distance through the anonymity of a username capable of being whatever the user imagines.[46] The next step is the visual creation of the avatar through which "users can attempt to replicate their real world bodies digitally, or they can create extravagant, idealised bodies, or go further still and inhabit animal or robot bodies"[47] changing size, shape, skin colour, and more. The draw of virtual realities such as Second Life is the opportunity to experience things you otherwise would never achieve. Second Life offers flight, teleportation, travel, and adventure in a safe space where one can never truly be harmed. Living vicariously through the avatar presents gamers a chance to experience a different life in which they are not judged based on their physical appearance, but rather through their avatar's interactions within the Second Life community. Second Life provides an escape from reality, just as social media platforms used to prior to the invention of Facebook when one operated solely under a username, often with little association to one's true self. Second Life separates itself as a platform through the participation involved in the game's creation. Almost every element depicted on the game (architectural, natural, etc) was created by a Second Life user, making the world completely user-dependent.[48]
Media Portrayals Through Black Mirror
[edit | edit source]Fifteen Million Merits
[edit | edit source]The Channel 4 turned Netflix Original show Black Mirror is a fantastic resource when discussing both the ideas of Avatar Creation and Virtual Reality, in particular reference to the episode mentioned above "Fifteen Million Merits", which gives a reasonable depiction of a futuristic virtual reality where members of society carry out a meaningless task, aimlessly cycling on a bike that physically goes no where in order to earn money. Living through a virtual avatar, people can purchase items of clothing, possessions, subscriptions to different television programmes, etc. Literally carry out something meaningless to create virtual money to spend on a virtual existence. In the show there is one character who is heavily involved and invested into this process of buying and creating a better avatar. The avatar can travel and explore different experiences, interact and be part of something different but their real life selves are actually stuck within a small four walled room and on a bigger trapped being a slave to the system. This character and lifestyle, is a scary, yet realistic view of where our society could go if the obsession and dedication that people have for their avatars on games. This obsession lends itself to the extension of self, and also living through online brings us nicely on to the idea of virtual reality, and how some prefer the online life than reality and the damages this can cause.
Playtest
[edit | edit source]This episode of Black Mirror [49] is another fantastic episode that takes modern day culture discussed here, the ideas of Virtual Reality in combination with gaming. The push in current culture is to create more and more realistic games. From the mundanity of "Sims" [50] where gamers can create debatably realistic characters and do everyday mundane things, (therefore real in their actions) to one of the newest installments of "Call of Duty: Advanced Warefare"[51], which features an almost identical reconstruction of the actor Kevin Spacey [52]. This constant and current push for the most realistic gaming experience links very well to the upcoming market of Virtual Reality, (real in it's visual experience) and that growing industry is what is featured in this episode of "Black Mirror". The main character signs up to try out a new gaming experience, in the final most extreme stage of testing he enters a horror genre of game. Where the game uses his own memories and mind to create personally scary situations. This incredibly realistic scenario is enjoyable until the game turns on the main character and experiences his darker, deeper fears and spirals out of control. This escalation really explores the dangerous path this realistic gaming experience society is venturing down. Like most Black Mirror episodes it takes a current piece of culture that is damaging or has a strong possibility to be damaging and pushes it to the extremes to show a scarily realistic digital future.
Chat Rooms
[edit | edit source]Chat Rooms
[edit | edit source]Cyber-bullying
[edit | edit source]Cyber-bullying is defined as harassment or abuse using electronic mediums of communication. It can involve all the typical forms of bullying except physical harm. It should be noted however, that encouragement to inflict self-harm is common within the context of cyberbullying. The effects of cyberbullying are not just visible online. Their real-world effects can be sever and according to the Cyberbullying Research Center self-harm, substance abuse, school problems and delinquency are related to instances of cyberbullying. In a meta-analysis on the subject, Kowalski et al. noted that among victims of cyberbullying, stress and suicidal ideation (the thought and intention of committing suicide) were the most common effects of cyberbullying.[53]
Real-life influence of cyber-bullying then, is incontrovertible. In the age of social media and always-on culture, the online world is at the forefront of so many adolescent minds that real-life effects will naturally happen. Emotional investment in one's online presence, and the varying ideals of self-presentation that different social media platforms dictate in our culture mean that the effects of hurtful language and actions online feels the same as in the real-world.
In the 2015 film Cyberbully the main character is coerced using threats of the release of private photographs, files, and evidence of her own cyberbullying tendencies. Such is the prevalence of online abuse that it now forms a narrative in media that engages with it and shows through different lenses, the effects of it. Similarly in the 2010 film Chatroom characters engage with each other and through herd mentality encourage each other to cyberbully.
The nature of cyberbullying lends itself to a detachment by its perpetrators from the consequences of such behaviour. Because of a currently-still-perceived divide between real-life and the online, a measure of detachment and inability or refusal to think about potential effects of online behaviour exists[54]
Public and Private Forums
[edit | edit source]Public Forums
[edit | edit source]A Public Forum can be defined as a space, both physical and non-physical, where a group can gather and freely discuss their views on any topic. Within reason. As long as they abide by the guide lines set by the First Amendment – free speech[55].
By traditional standards a sidewalk, a park, and a street can all be defined as Public Forums. They are considered as spaces open to public discourse, and can also be referred to as ‘open forums’. As to can all Public Forums. Forum (legal)
The term ‘Open Forum’ harkens back to Ancient Rome where the Forum was at the centre of every Civitas – settlement. The Forum in these settlements would have been the beating heart and were most often used for markets. However most major events, speeches, and discussions would also take place within them.Forum (Roman)
As human civilization has evolved so has our means to share information. Now the most common forms of the Public Forum used are non-physical online platforms. Arguably the most popular platform, boasting over 1.8 billion active monthly users, is Facebook[56]; Tumblr is also an exceedingly popular platform, and provides its users far greater freedom of expression than Facebook. Reddit is another big platform that has been described as the front page of the internet w: Reddit ; where its registered users can submit content, such as text posts or direct links.
It is upon these three platforms that this piece shall focus on as full the number of online Public Platforms is too great to discuss them all.
The three social platforms already mentioned (Facebook, tumblr, and Reddit) work in a similar manner. In the case of both Facebook and tumblr you follow/befriend those you wish to and then you are able to open, or join, a discussion with them and their peers. Reddit provides numerous forums that cover an immeasurable number of topics; ranging from basic tech support, to cooking recipes. They are all Public Forums as most of the information and discourse is readily available to any user.
Tumblr [[36]] is a blogging website where users create their own urls and build their own blogs. The users have the freedom to choose whether they upload their own content or to “reblog” content posted by another user that they follow. Because of this users of tumblr have a great deal of freedom to express themselves, and an expansive platform for discussion.
Facebook [[37]] is one of the most widely used social media platforms in the world and therefor acts as one of the largest Public Forums there is. Though users can only see the content shared, posted and liked by their ‘friends’ they can communicate with all users via pages, groups and events. As such it is a platform that is frequently used to organise political marches, and to its page/group system enable likeminded individuals to easily meet; and to share ideas.
Reddit [[38]] is described as an American social news aggregation, web content rating, and discussion website. As mentioned its forums cover a massive amount of information and has a discussion open for anyone that wishes to join.
Private Forums
[edit | edit source]By nature Private Forums are very similar to Public Forums, however where they differ is in the control of discussion content. Whereas Public Forums function along the lines of free speech, each Private Forum is controlled by its administrators. The nature of both forums is the sharing and discourse of information, but as mentioned, Private Forums are controlled by individuals rather than laws.
Private Forums will generally require potential users to be invited by an existing member of the community, and will sometimes require membership fees be paid. The Forums will be created with a particular topic in mind, and membership – it can be assumed – is requested due out of a desire to actively participate and benefit the discussion.
The Private Forum will be owned by its administrator(s) as it enables them to control privacy settings, along with content.
Deep Web
[edit | edit source]When discussing the differences between Public and Private Forums an interesting topic is the Deep Net, or Deep Web, which exists as a grey zone between the two. The Dark Net is quite literally the murky depths of the internet and is referred to as the ‘deep web’ because of how much is hidden within it.
Though its contents are open to anyone that wishes to search them, and it does provide the user with unparalleled levels of freedom, one does first require a deep web browser to access it[57]. The browser takes the first steps away from the concept of a Public Forum as it makes you anonymous, allowing you to search in safety – allegedly users cannot be guaranteed their safety according to a recent Wikileaks publication [58]. From the users’ new position of anonymity they then possess the freedom to explore. Content on the Deep Web ranges from sites that provide any illegal substance you can think of; to weapons; and the deeper you go the darker it gets with a massive availability of illegal pornography.The Guardian reported that is thought only 0.03%[59] of the web’s content comes up in regular searches, and the rest lies in the dark web’s depths.
It is in this anonymity and the way each site is controlled by it administrator(s) that it resembles more a Private Forum. However as it is so huge it cannot simply be referred to as one or the other.
Online Dating
[edit | edit source]History
[edit | edit source]Like many aspects of the digital world, Online Dating has its roots in different mediums of the past[60]. The personal advertisement is the predecessor of today’s online dating. The first personal ad appeared in a British agricultural journal in 1685[61]. In the early 1900s personal ads became popular once again in the United States: especially in its sparsely populated western region. During World War I there was an emphasis on marriage by the age of 21 so personal ads were popular among young soldiers[62]. In 1959 the first computerized match making system was developed by a Stanford University student. It used an IBM 650 to determine similarities between 98 subject from answers on a 30 question survey. Operation Match took off in 1965 by a group of Harvard Students. They used a IBM 1401 , a mass marketing computer. For $3.00 the 1401 would analyze a questionnaire filled out by students and give them 5 matches. In 1995 the public gained access to the World Wide Web, allowing people to be connected online. Email became popular in 1998, becoming a part of day-to-day life and allowing people faster communication across long distances. In 2000 eHarmony, a compatibility website with the goal of establishing long-term relationships, was established by Dr. Neil Clark Warren. The use of Skype video call in 2003 allowed long distance relationships to flourish. With the dawn of the smartphone in 2007 online dating was taken “on the go.” Location based applications became popular in 2012 and play a huge part of online match making.[63] In today’s world countless dating websites and apps are easily accessible to the masses.
Prevalence
[edit | edit source]Online Dating has become extremely popular. The term “online dating” is searched over 135,000 times a month[64]. In 2013 there were an estimated 2,500 online dating websites in the United States, 1,000 opening every year, and about 8,000 worldwide[65]. Websites like match.com provide information about their community. About 1 in 3 relationships and 1 in 5 marriages start online. 31% of US singles met their last first date on a dating website[66]. These numbers show that online dating is becoming more common and leading to “successful relationships.” In 2012 the Harris interactive conducted a survey and said that on average 438 eHarmony members get married every day.[67]
Catfishing
[edit | edit source]
Catfishing is a slag term for creating fake profiles on social media to create false identities. [68] The Term became popular after the 2010 film Catfish (film) that follows a man as he find out the person he has established a friendship/relationship is not who they seem. The documentary highlights a story about how seafood suppliers faced problems with shipping cod. They meat supposedly would mushy because the fish had been sluggish. The suppliers decided to put a catfish into the tank, a natural predator, to keep them active. The correlation between the fish story and the online is, "the catfish in real life are supposed to keep you on your toes, keep you guessing, keep you thinking, they keep you fresh." [69] Although the term "catfishing" did not become popular until the early 2010s, the practice of adapting online personas that are not your true identity is common place. The act happens mostly on social media platforms and on dating sites. Catfish normally reach out and initiate conversation, establish a some form of relationship, but will do anything to maintain their fake identity. [70]
Psychological Breakdown of Catfishing
[edit | edit source]The psychological impact of catfishing is extremely complex. It is not just about why people catfish, but also how does it impact the victim. People catfish for several different reasons. Every person is different and catfishing may fulfill different needs. Some reasons are, loneliness, revenge, greed, and people just seeking a thrill. [71] People who are lonely may take on fake personas because they have no one. They may feel isolated from their communities and do not see a different outlet for developing relationships. Someone who feels they are inadequate may pretend to be a fitness model, or maybe someone is struggling with their sexuality or gender may turn to catfishing as a way to cope. [72] Revenge is also a common. It is an unfortunate reality, but people will seek revenge on their significant others, relatives, or exs. Greed is incredibly damaging. People who use this to motivate their catfishing go in with the intention of being harmful. Sensation Seekers are often not malicious, but they get a thrill from taking on a new personality. These people use it to feel a certain emotion or sensation.[73]
It is often believed that people who catfish do not have the intention of hurting others for the most part, of course there are exceptions. Secrecy is often found in most long-term relationships. It is not necessarily a bad thing. Catfish relationships, are not dissimilar from face to face relationships. People develop an intimacy and feelings for one another. The problem is, the secrecy is what the catfish needs. In these relationships the relationship flourishes with the secret intact. When the secret is revealed it the relationship dies. The trust that may have been established is gone.[74]
Tinder and Online Dating Websites
[edit | edit source]Introduction
[edit | edit source]Tinder is technically a social media app most commonly used as a dating app by logging onto the users Facebook, that started up September of 2012. On Tinder you swipe right to 'match' with someone- where they have swiped right on you and you both now have the option to talk to each other. The people you see on Tinder are sorted by how far away they are, meaning that Tinder lets the people in your area or neighbouring cities see you depending on how far away you are
Online Dating websites however are different in that the websites can range from different themes that are specific to the individuals likes or views. For example by religion like Christian Mingle or by hobby such as Equestrian Cupid.
Realism and Deception
[edit | edit source]Online deception across the internet is defined as a users modification of his / hers self description between real life and the dating profiles they have created (Toma et al 2008) Several different factors affected the realism of their profiles and lead to deception online. These include factors of gender and the individuals personality under the presence of anonymity.
Evolutionary psychologists have looked into the deception of realism between males and females, the modification of traits in online dating can mainly be explained through socially desirable responding. Enhancing the individuals “reproductive viability” [75] Meaning that each gender placed focus on certain elements. It was found that men were more prone to exaggerating their economic stability and physical strength, woman were more likely to emphasise upon their physical attraction. These discontinuities in reality had been pinned down to the social constructions and expectations of each gender Each genders main misrepresentations also followed a pattern; where women are more prone to being discreet about their weight while men are more prone to misrepresent their age and personal interests.
Deception over the internet is a phenomenon caused by a lacking process to verify information five by misleading profiles, that negatively affects the reputation of online dating websites, adding an element of mistrust through enabling misleading profiles the ability to pop up. [76] [77] Sztompka backs this up, continuing to link an individuals intent to claim falscitalities as a result of a “lack of method for verification” [78] which is especially vital when information given about an individual is communicated textually. This deception can easily lead to frustration and mistrust that could potentially lead to an individuals emotional and psychological damage.
A study by Mills [79] states that individual identity is broken down into 3 elements; physical appearance, attributed data and biographical data (ie education) Age, gender and appearance were the most commonly mislead factors within this. [80]
Anonymity Diminishing Accountability
[edit | edit source]In short, individuals online who intend to deceive other do so through creating an online indignity different to the one in real life. However, it can be those who don't intend to deceive that are allured by the possibilities of personal gain that a lack of accountability through anonymity gives.
This can be evidenced through Toma et al's study that 80% of online daters felt that people misrepresent their physical appearance in their online dating profiles.[81] To extend physical boundaries, the individual user tended to expand on their self presentation. This correlates with the anonymous nature of the internet .
A study by Suler concluded that internet induced anonymity is a key influencer on the difference between the real world and online world, assuring that this was also a key factor in causing the online disinhibition effect where there was a clear disassociation between online and offline identities. [82]
Realism, Anonymity and Technology
[edit | edit source]The free-form ‘descriptive’ set up of online dating websites and apps where users can create themselves in a more favourable light, even when what they have been writing is exaggerated or emphasised. When a certain image of an individual is then altered elements of their personality and herby identity are fictitious. The ability to edit your profile also encouraged other users to modify and shape their information. Reasoning behind this may be down to appeal to certain individuals (changing their values to align to someone on the website ) and change aspects that received negative feedback. Overall, the motives behind online daters point to the goal of wanting to be seen as more “attractive” and “likeable” in order to achieve their end goal. [83]
Tinder has this to a certain extent, however the app lets you link up to Instagram which can be a good way of backing up what the users may say about themselves on the app.
Though the different textual and intertextual communication online vs real life we can view that anonymity is a key enabler for individuals to deceive others. Deception is made easy because its difficult to link online dating users online identity to their real identity without obtaining personal information.
The technical nature of computer mediated communication (CMC) creates a different situation in which we can express ourselves in, dissolving geographical boundaries and the affect of real time communication creating a platform by which users have time to to reply to messages (as an example) allows the user to overthink their messages and present their idea of a best possible reply. This nature of CMC specific to online dating allows the users to present the best picture of themselves, which is inconstant to real time conversations where there is less time to reply. On top of this, information online about our individuality is given textually compared to intertextual communications face to face communication is where there are an infinite amount of facial features and body language to communicate what a person is ‘saying’ without actually speaking. Individuals can also subjectively interpret the reactions they get online towards another user, which can shape an individuals behaviour and by extension their identity.
This ‘intermediary platform’, of which Tinder and Dating Websites are on, can provide individuals with a sense of safety and anonymity compared to the vulnerability that many feel they face through face to face interaction. Some feel that the social expectations of them are more pronounced in the ‘real world’ which can suppress on individual thoughts or views. In this perspective, online dating may ‘free’ an individual more online more online rather than surpassing their actual thoughts.
Communication intermediates influence have online identities are generated and presented under the influence of the ability in not having to disclose a lot of personal information, given that online environments do not have mechanisms to immediately authenticate its users.
On the other hand however, anonymity provides its users with the ability to truly express themselves or even 'liberate' themselves where their true selves are revealed without prejudice and judgement.
Anonymity and Accountability
[edit | edit source]When the purpose of the account on social media is to keep in touch with friends and family members, like Facebook is, profile attributes are as close to the truth as possible since the individuals affiliates act as an authentication mechanism (ref B) This can be related to Tinder in that the way in which you make an account is through your Facebook account and you can see your 'common connections' with the person you are matching with. On top of this, since your Tinder searches people relatively close to you there is always the potential that you can see people that you know in the surrounding area, and those people cans see you. The constant threat of having someone you know see your Tinder profile destroys the idea of anonymity on this particular dating app, and therefore is more likely to be realistic in relation to the profiles on it due to this.
While the presence of perceived anonymity has a tendency to combine with the received lack of accountability and attachment to the real world, this lets the user become their own authoritative figure in which they put online.
Warranting Theory
[edit | edit source]Adapted by Walther and Parks [84] from a study by Stone [85] it suggests that in the presence of anonymity, a person may misrepresent information about his or herself. It was an observed phenomenon where some people met in person after having met online and were dissatisfied with the partner. The potential for autonomy resulted in the potential for discrepancy in online dating profiles. 'Warrants' and describes by Walther and Parks were perceived reliable cues that observers use to cause how ones true identity matches their online profile.
Digital Culture
[edit | edit source]Digital Divide
[edit | edit source]The term “digital divide”, also called “digital gap”, refers to the demographical, social, economic and regional inequality regarding the access, distribution and use of information and communication technologies (ICT) and its impacts. This is with regards to people who have, and those who do not have, the necessary skills, abilities or knowledge to use ICT. It exists between rural and urban areas, between economic classes, between socioeconomic factors such as race, income, and education, between people who can afford an internet access and those who cannot, between the quality of connection as well as the local adaption and availability (i.e. via wideband) [86] and on a global scale between industrial and developing countries. [87]

Dimensions of the Divide
[edit | edit source]The digital divide shapes the global and local flow of information. Even if access to online information is available, a free information flow is often restricted or blocked through network censorship. At national level some governments constantly restrict the access to certain webpages and filter any expression that may threaten their national security. Often this is the case in some Middle Eastern countries and especially in China and North Korea. At organisational or family level, firewalls or access limiting software can be installed to prevent employees or children from accessing undesirable or harmful online contents. [88] Elad Segev argues that there are more subtle reasons for the digital divide in the online community i.e. that it is a result of the commercialisation of the internet and the operation of hugely dominant information agents and search engines such as Google. Furthermore, that the divide emerges as a result of information-skilled users tearing it wider apart.[89]
Knowledge Divide
[edit | edit source]Knowledge has become a valuable resource in the Information Age, increasingly determining who has access to power and profit. Apart from the demographical, social, economic and regional gaps of the digital divide, knowledge continues to expand and has a growing impact of inequalities in science and technology capacities which create an impenetrable barrier for those, who wish to mobilise knowledge, and those who which to obtain it. The spread of information on a global scale through the internet and the uneven assimilation of global access to the internet expands gaps in knowledge between individuals and nations has been called the Knowledge Divide . [90]
Technological Determinism
[edit | edit source]Technological determinism is the theory that the technology that people create and see themselves surround by determines the culture in which they find themselves. Therefore a dramatic change towards a societies technology should in turn result in a dramatic change in that societies culture. For example the emergence of phones changed the way people communicated, and in turn changed the way they acted and thus changed their culture. This theory is heavily discussed by Marshall McLuhan in his book McLuhan, Marshall. (1964) Understanding Media: The Extensions of Man [91] where he describes the theory in detail and furthermore applies it to the real world . He does this so well that other theorists have since taken and adapted his ideas towards Technological Determinism itself, for example Transforming McLuhan by Paul Grosswiler is one of the examples of the many books devoted purely to McLuhan's ideas over the theory.[92]
Cultural Determinism
[edit | edit source]Cultural determinism is he stance that common patterns of behavior, attitudes, and values which persist for generations are the result of cultural factors rather than biological or other factors[93]. This presents the argument of nurture vs. nature. In this case how one is reared determines who they are as a person. In order to understand cultural determinism, it is important to understand what culture is. Culture is defined as “the beliefs, way of life, art, and customs that are shared and accepted by people in a particular society.[94]” The concept of cultural determinism emphasizes that your culture determines the type of person you are. This theory possesses some weak points. For instance, if one were to grow up in a neighborhood with crime and deviance, is it guaranteed that the person will participate in criminal activity and deviant behavior? In the digital age one looks to cultural determinism and how people easily interact with technology and how ingrained it is in our world.
Identity and Persona in relation to our online real life divide
[edit | edit source]Online and Offline our personalities can differ very much.
Online, people generally tend to undertake a process known as portraying an ‘impersonation management’[95]. This is a term described in detail in Psychology of C G Jung by Jolande Jacobi (1999) that means we present ourselves in what we believe is the best light in each scenario. For example, on Instagram or Twitter (and other Social Media platforms alike) someone will normally try to only post up their most flattering photos that paint them in the best light (both figuratively and literally), in an attempt to manage the presentation of themselves.
This concept can be argued further when using Erving Goffmans idea of 'masks'[96], as discussed in his book The Presentation of Self in Everyday Life (1959) where Goffman argues that our personalities are fluid and thus change depended on the scenario we may find ourselves in. In terms of our Online/Real-life Divide this in turn means we are likely to change the way we behave on- and off-line; but also that we are also likely to change the way we behave on different online platforms themselves. For example one is very likely to present themselves in a different mask on Wiki*edia as opposed to Facebook, because the purpose of each environment differs greatly, and thus how one can present themselves in the best light also differs greatly. This results in a change of ones 'mask', or persona, as a result of the process of 'impersonation management'. This idea is illustrated well by Stephen Fry here: https://www.youtube.com/watch?v=6Z0XS-QLDWM [97]
Psychosocial Approaches
[edit | edit source]Psychosocial study is a relatively new field which explores the ways in which psychological and social experiences are intertwined and interdependent. Psychosocial approaches are interdisciplinary, reflecting the belief that psychological and social experiences cannot be independent of each other but are rather part of one whole experience based on a sociological, historical and cultural context. As such, psychosocial approaches draw on existing fields of study including sociology, psychology, philosophy, post-colonial studies and post-structural theories. [98] A psychosocial approach to the online/real-life divide would suggest that life can no longer be neatly compartmentalised into an online life and a real life, but that the prevalence of our interaction with digitisation affects our real life and vice versa.
The Effects of the Connected World
[edit | edit source]Representation
[edit | edit source]Introduction
[edit | edit source]The emergence of new technologies and social networks has created almost a new aspect of how we can have and form an identity, and how others play a part in the formation of this representation. The “user profile” that has become so popular on the almost all large social media platforms [including Wiki]. This “profile” function allows users to create an individual page centred around them, whether it be voicing their thoughts and research on a topic like on Wiki or whether it be creating a photograph wall of yourself and photos you have taken seen on Instagram. So the issue of representation seems undoubtedly complex and it is apparent that there is a lot more at play than people simply building up an online reflection of the self, allowing for a lot more fabrication.
The Proteus Effect- Nick Yee
[edit | edit source]Yee and Co’s [99]studies around the Proteus effect shines light on the notion of an online self by examining avatars in Collaborative Virtual Environment (CVEs) and studies people’s online behaviour when given an avatar with certain traits seen as more desirable on the platform.
Yee notes that “Instead of focusing on the structural affordances of the computer-mediated environment, studies in TSI have shown how strategic changes in an avatar’s appearance or behaviour can affect how other users interact with that avatar”. From this we know that there is a strong relationship between an offline self and their online counterpart – being an avatar or a personal profile page – and this relationship dictates how exactly people proceed to present themselves online. It continues saying it seems that people want to see the best qualities and be most desirable version of themselves online [from their behavioural tenancies when their avatar is more “desirable”] this seems extremely telling on the issue of representation. It can thus be noted that people don’t want a full realistic version of them shown but there is a strong selection process in which people pick and choose factors they want other to see. This can be said to constitute a strong real life online divide as how people wish to be represented on any platform involving exhibiting a form of themselves is noticeably different to real life interactions where it can be argued to be a simple case of what you see is what you get. The study goes on to discuss Multiuser Domains (MUDs) and the findings here help to shine light on the key issue within this sub-topic, being misrepresentation. It states that on certain platforms there is an aspect of gender bending, so people are creating profile and personas yet gendering them differently than their own and acting in ways they possibly think is more suited to that gender role. The behaviours and character traits that are used are noted to not fit the individual’s own and so we see here that people use the divide from real life to misrepresent themselves and escape on identity into another, escapism being a whole other topic in itself. However this shows us that the divide that exists can offer opportunities to escape one notion of self that exists offline and in a positive way misrepresent a version of ourselves which can be noted as a clear effect of living in this connected world.
Although these MUDs and CVEs differs from platforms in which user profiles are a more “direct” representation of you [featuring photos, your thoughts in posts, etc] this study can still be seen as useful to learn about this whole notion of an offline online representation as it quite concisely examines how we present ourselves behaviourally when there is a keyboard and screen to hide behind.
Narrative
[edit | edit source]The way we choose to tell the story of ourselves online is a complex way in which we can examine how we see our lives and the effects the connected world has had on us. I believe storytelling on social media platforms goes above simply writing long posts about what happened to you recently and is more interactive and importantly encouraged by these large platforms. When we travel somewhere Facebook encourages us to post this journey with geo-location, when we attend an event we are encouraged to tweet using a hashtag for the event and when we watch a television show we are now encouraged to watch along – giving every thought and opinion on some app or social platform. These alone do not tell much of a story but it is on these user profile timelines as seen on Twitter, Facebook and the Snapchat story that when viewed for their collective value begin to build up a narrative around the individual or organisation and so creates a more rounded identity.
Aisling G M Kelliher (2007) [100] describes the online storytelling that has become prevalent in recent years as “transforming our fragmentary narratives into shareable narratives [which] helps us to understand and communicate who we are as individual and social beings”. This seems to eloquently summarise this idea of taking the offline experiences we have on a daily basis and turning this into content we can like, share and comment on. It can be argued both that this feature of creating narratives of our offline world on social media platforms in bridging the offline/online gap that exists or that it distances us further from reaching that point as the selection process of what we deem glamorous enough to share on social media can be seen to giving a false account of the “real” that we are striving to understand in this study.
Privacy and Security
[edit | edit source]Introduction
[edit | edit source]As discussed earlier, in this day and age the technology needed to establish your identity and create your own image is not just available, but it is a necessary part of everyday life with the internet being an integral part of most work and social lives. Social media and dating websites are the two most widely used ways to share private information. Through messages and status updates etc. there is a lot of content shared (supposedly to a selective audience) that people don’t want to be public. This ranges from people hobbies and interests to nude photos and all other types of content: there is a lot of information out there which is shared with the intention of being private, only available to certain individuals. Unfortunately, the expectation that privacy is an option will often leave people disappointed.
Is Snapchat Secure?
[edit | edit source]Although privacy is intended by most social media and dating apps, they all tend to have their loopholes and issues that lead to what is meant to be private becoming public. Snapchat is arguably the riskiest social media platform to use in terms of privacy because of the false sense of security they very deliberately provide. This makes is a great example of the limits of to which private information is secure compared to what people believe. One of the key concepts of the app is that the content you share or send is deleted. They claim very openly that they do not store the data that you post, it is automatically deleted. This feature has dictated the way people use the app, posting content pretty much care free because it will disappear after ten seconds. But the assumption that the information will be gone forever is a decidedly wrong one. There are main reasons that Snapchat is not as secure as people believe. The first is the one that most are aware of. Even though the image sent is gone (and supposedly deleted forever) that does not stop the receiver from very easily screenshotting the image on their phone; even though Snapchat doesn’t necessarily store it, somebody else can. The saving grace of this loophole is that it is a well-known problem with maintaining privacy; by in large, everybody knows how to do it. On top of this, Snapchat do not deny that screenshotting is a thing. Since the knowledge is public it is not as harmful; people can send Snapchats based on their trust relative to who they are sending the image to. The second security threat to Snapchat is one that people are not aware of. It demonstrates the dishonesty which comes from social media platform and other apps concerning security and privacy of information. Snapchat clearly states that they do not store any data, it is deleted after it disappears from your phone screen. This is even a core marketable feature of the app. However, this has been proven to be untrue repeatedly. Data shared is not gone forever as promised. This is a little known, though publicly reported fact. The FBI has access to information shared on snapchat and has the right to request it to work on cases. What this means is that Snapchat does indeed store the data users share on its servers.
What Does The Lack Of Security Mean?
[edit | edit source]dangerous way in which this fact can be exposed is with hacks. Snapchat’s server has been hacked in the past and supposedly private and deleted content has been shared publicly online. The most famous instance of this was the occurrence of “The Snappening”, the name of which was a reply to “The Fappening”. These were both instances of thousands of naked photos of celebrities (which were obviously intended to be private) being hacked, stolen from the servers (which Snapchat claimed did not hold such data) and posted publicly online. This all means that Snapchat is an unsafe way to share information privately as people you know can use it in ways you don’t intend and strangers can acquire it without the user’s knowledge. Other social media platforms are very similar in how information that is meant to be private can lack the security people expect. In modern times the personal image of oneself can be created online and offline. It is now clear that doing so online through Social Media etc. offers at most the same amount of privacy as living in reality, where it is also difficult to guarantee security of information.
Production and Consumption
[edit | edit source]Social Media Careers
[edit | edit source]For students studying a degree like Film and Media it can be very difficult to find work once the degree is done. The field of study is known partially for having few clear job prospects or career paths at the end. The vast number of students in that industry cannot all fit into internships or job placements; there are not enough to go around. Fortunately, there are many new opportunities arising which do not include any physical employment; rather they are done over the internet. There are job opportunities as well as entire careers which centre around social media and producing content entirely online. An example of this is working as a social media manager for a company or even a celebrity. Companies and celebrities use social media to control their image online, which is very important. Thus, there are many opportunities to post content on behalf of a corporation as a Social Media Manager. This is just one of the career paths that can be found online because of new technology. This demonstrates the extent to which online image is important and how one’s career can be defined by online work.
Creative Practices
[edit | edit source]The internet can be described as a marketplace- in the way that a market place is a structure where buys and sellers exchange goods, services and information. The internet can be used for all of these things, however the 'buyer' and 'seller' can exchange these things with their own information rather than legal tender such as money- creating User generated content. Users are just applying the concept of a marketplace to a more social atmosphere. This user generated content is what fills most of the internet and can come in many forms, for example Facebook as a media platform to communicate and share pictures of yourself and follow your interests, and Wikipedia as a way in which to contribute to an online forum and expand your own knowledge and those that engage with the page.
The news has also moved online. The most popular social media apps are ones that circulate or produce news, such as Facebook where many trustworthy news sites post their articles as links online to enable them to be read more widely.
Artificial Intelligence
[edit | edit source]Definition
[edit | edit source]Artificial Intelligence is defined in Russell & Norvig's seminal textbook Artificial Intelligence: A Modern Approach as a subject that "encompasses a huge variety of subfields, ranging from the general...to the specific."[101] For the purposes of this book, Artificial Intelligence will be defined as a machine that can process and comprehend information, and respond to it, in a way that human beings associate with other human beings. This is a colloquial definition of the subject. For other definitions that encompass the 'general' and 'specific' that Russell & Norvig reference, their textbook covers all.
Implications of Data Collection
[edit | edit source]Automated programs are already widely used for data collection ranging from large companies like Google[102] and Facebook, who even collect data from Internet users who are not signed-up users of its website,[103] to government sponsored data collection[104] like the NSA-run surveillance program PRISM.

These programs store and search for data based on specific parameters set by the company, that then evolve based on what information is eventually seen to be useful or noteworthy. For companies, this tends to be whatever information can generate the most revenue. However, James Canton opines that there can be no 'Big Data' collection without the use of Artificial Intelligence. The sheer volume and processing of the information generated daily needs it. He says "In a world where there is big data everywhere, the extraction of meaning, the monetization of data for a purpose will be driven by AI."[105] However, this is at odds with other theories of Artificial Intelligence development. In the film Ex Machina directed by Alex Garland Artificial Intelligence is only created because of humanity's ability to collect huge amounts of data. In the film, it is theorised that Big Data is less a measure of what people think, but how they think. The scientific advisor for the film, Murray Shanahan, supported such a statement in interview. [106]
When Data Collection has so many real-world consequences then the question of where the divide between online and real-life begins is raised. For the individual, data collection is unseen and silent. It's effects feel vague and slow to alter our lives, despite the fact they have altered them significantly already. When Artificial Intelligence is added into this mix it becomes a different argument entirely. If Artificial Intelligence is developed, will it be given the same rights as humans? If it is given the same human rights then is it considered a single entity? And if a single entity has the ability to collect huge volumes of data, what is stopping every single entity to collect data too?
Chat Bots and the Future of Online Conversing
[edit | edit source]Chat Bots are defined as computer programs that attempt to simulate human conversation through spoken language or through written language. Their purpose is to engage in convincing conversation with the human user on the other end. The first notable chatbot was developed in 1966, and was called ELIZA. development of chatbots has continued until the present day. Originally, the Turing Test was first seen as a measure of a machines intelligence, and consequently of its Artificial Intelligence. Numerous chatbots can now pass the Turing Test, and under specific conditions, the test was passed in 2014[107]
The implications of convincing chatbots are wide-ranging. The nature of communication has changed in the digital age so as to be unrecognisable to pre-digital times. Our smartphones can now automatically respond to received messages with a preassigned response. Additionally, predictive texting algorithms are heavily linked to the development of chatbots. Research was done on the effects of predictive text on spelling and grammar comprehension in children, and found negligible results.[108] However, there has been no research done into the effects that predictive text has on our choice of language. The question must be asked that if predictive text gives us suggestions of which words to use, can it influence our decisions? To what extent does the predictive text algorithm affect and choose our language for us?
The 2013 film Her explores the concept of detached communication further. The character played by Scarlett Johansson is an evolved version of a chatbot, being a disembodied Artificial intelligence program. Communication with her is problematic because she does not have a body and this is explored in the film through her attempted use of an 'avatar' who is a real person. Additionally, the main character in Her works as a letter writer, composing love letters between couples and often writing both person's responses. These people are sending each other messages and communicating without choosing their own language, or being a part of that communication. Again, this strikes one as disembodied forms of communication and speaks to the significant difference between embodied and disembodied Artificial Intelligence.
A.I in Fiction
[edit | edit source]The best science fiction has always been seen to be a precursor and accurate prediction of changes that take place in the world. From dystopian in Nineteen Eighty-Four to utopian in Looking Backward:2000-1887, sci-fi literature and film has always ended up blurring the line between what is real, and what is not real. Through it's very existence and predictive nature it ends up assertively comparing what is real, with what is not-yet-real.
In his landmark book On The Internet, the philosopher Hubert Dreyfus states that "since robots can't be programmed to behave like people, people will have to learn to behave like robots."[109] This is a typical pessimistic view of the development of Artificial Intelligence. However, this is not to say that it is wrong. An argument like this is inextricably linked to the Online/Real-Life Divide.
A.I's Creation to Serve Society
[edit | edit source]At it's essence artificial intelligence is created to serve it's master. This instant relationship between the creator having power over something that is trying at it's core to be as close to humans as possible. That fine line between creating a machine that functions and looks like a human but does not 'think' and 'feel' is the fine that most scifi fiction revolves around. Often the narrative puts the creations in a position of assistance, where humans rely on them in order to function, they are a new piece of technology designed for enhancing or making easier human existence. For example in the Channel 4, TV show "Humans" [110], the "Artificial Intelligence" in the show have human physical features, but their soul purpose is to service humans. From being a nanny and house maid for families to some of the bots being sold to have sex as prostitutes. As an audience, seeing a human face being forced (or not being giving a choice because of programming), to do something they don't want, especially sexual evokes strong conflicting emotions. Yes, the A.I is created for the purpose of serving society but giving it a human face and voice questions ideas of slavery and brings morals and ethics to mind. A.I creation is a form of technological slavery in an attempt to make human existence easier and usually in fiction it has dangerous repercussions for the creators.
There is however a film that shows how A.I can be used in a positive way. The film "Robot and Frank" [111] portrays a wonderful story of a positive use of A.I technology in assisting an elderly man who lives alone, to live alone. The character of the robot does not have a human face, and perhaps this is the difference, the definitions between robot and human are defined clearly between physicality. However throughout the movie there is use of a human voice and suggested attempts at humour, it builds a level of companionship with Frank the other main character, the character is at it's element taken as a human relationship but the difference between the two is distinguished throughout due to the different physical appearances.
These two different pieces of fiction really show the different directions of A.I in terms of fiction writing, focusing on the difference and importance of physical appearance and the boundaries that people expect for the future or A.I. There are a never ending list of sci-fi A.I featuring, movies but I think that these show that with a face the audience become to morally confused between the possibilities of human and machine but even without a face an audience gets emotionally attached to the character of the robot.
Where A.I controls society
[edit | edit source]The dystopian vision of a society controlled by Artificial Intelligence is born from the theory of technological determinism, a phrase that was first coined by the social scientist Thorstein Veblen to describe a society that causally changes because of developments in technology. This is opposed to cultural determinism which posits that culture is what causally alters developing technologies. This is often the mid/or end point of a scifi feature film, where the technology develops a mind of it's own and turns against the creator etc. a fantastic example of this is "Eagle Eye" [112]. The film essentially features a 'super computer' a common trope again within A.I, it has access to everything, the internet, personal records control over electrical equipment, it is a learning machine with all of the knowledge in the world. In order to save the planet, it's primary objective, it decides the only way to achieve this is to wipe out the entire race. So unfolds the fight between man and machine, creator and creation. In a fiction sense control is always in extremes where the A.I takes control of itself and uses it's power to destroy humanity. A common story line even in films such as Wall-e or Meet the Robinsons, humanities fears of the machine rising against us.
Black Mirror - Back to Before
[edit | edit source]This episode of Black Mirror is a fantastic look into the line between humanity and A.I creations, and how it can be blurred. Again it is another example of an A.I that uses a human face, but this time it is a specific person who is re-created using artificial intelligence, data trails left on social media, and private usage, the voice re-constructed from phone calls and personality aspects built on a combination of these things as well as from learning memories and experiences after its 'activation'. It is interesting as it combines many elements of A.I study, it looks at the idea that A.I is created for a particular purpose, in the sense that the main character purchases the A.I creation in order to be re-united with her dead husband, and it really pushes how far humans are willing to accept the use of A.I. This A.I takes information from the chosen persons internet use to compile a character, which is an interesting method that could definitely tie into the theories around the difference between the online self and real self. It is almost as if in this episode these identities are taken to extremes, an example of how the two differ. The main character is driven crazy by the 'half' version of her husband and so attempts to use the overriding power she has as the owner, the creator to order him to kill himself. She uses her status as a human creator to try and destroy her creation, the most interesting element is the fact that then, the creation uses it's knowledge and it's human face, a human face that she adores to portray human emotion, to portray fear in order to "stay alive", a term used loosely. But the machine uses it's knowledge and appearance to further it's existence therefore outsmarting the human, not for malicious intent just to continue it's "life", which again pushes merges the lines between human and A.I.
References
[edit | edit source]
| This page or section is an undeveloped draft or outline. You can help to develop the work, or you can ask for assistance in the project room. |
Privacy in a Digital Age
[edit | edit source]Introduction
[edit | edit source]his chapter of Living in a Connected World will cover various topics relating to Privacy in a Digital Age. The notion of privacy in relation to technology is a discourse which has seen a number of challenges in recent years. There are ongoing debates surrounding data mining and mass surveillance from the revelation that Snapchat saves users images to very recent findings that smart TVs can be used to spy on people.
This chapter will explore the ways in which online privacy has evolved over the years with the following sections:
- Definitions and Theorists - this section will outline various definitions surrounding the idea of online privacy as well as the relevant theorists who have done extensive research into it. This will be an introduction to some of the ideas that will be covered further on.
- Public vs. Private Persona - this section will explore the privacy policies of different sites and apps and will explore how their privacy settings allow users to take control of their own information and determine who their audience is. There will be an additional sub-topic on the notion regarding the individual vs. collective.
- Location Services on Apps - this section will explain what location services on apps are and discuss the benefits and the negative impacts of them.
- Privacy Laws - this section will outline the Protect Intellectual Property Act and the Stop Online Piracy Act as well as the ISP blocking within the UK.
- Internet Censorship- this section will discuss the way governments in China and Myanmar use internet censorship to control and suppress users from viewing undesirable information.
- Surveillance - this section will outline data surveillance and discuss the Investigatory Powers Act 2016.
- Personal Information Online - this section will discuss the personal information available online, the dangers of the visibility of this information and the actions that users have taken to avoid potential threats. Security levels and risks of online shops and banking will also be explored in this section.
- Privacy and Leaks - this section is dedicated to exploring the social impact aspect of hacking. Firstly it will explain the technology behind hacking, namely spyware, and how this technology can be used to access private information. Then, it uses different celebrity and non-celebrity examples to demonstrate the social side of privacy breaches and how this impacts on people and our society.
- Privacy in relation to Living in a Connected World - this section will discuss how Privacy in a Digital Age relates to other chapters within the book with the main focus on privacy in relation to the Online/Real-Life Divide, Technology as an Extension of Self, Persistent Connectivity and the Fear of Missing Out, Digital Labour on Social Media Platforms, and Filter Bubbles and the Flow of Information.
Definitions
[edit | edit source]Private Sphere
[edit | edit source]
The concept of privacy is often discussed in relation to the public. Zizi Papacharissi defines the term private as:
“that which doesn’t become public, and thus remains under private ownership. In the realm of the personal or domestic, possibly considered unofficial, and involving action structured around the self.”[113]
The historical roots of the word can be traced back to the works of Plato and Aristotle regarding the idea of private property. There is an emphasis on the domestic domain of the household being the private space for individuals to wind down and relax after spending the day in public.
We come back to this idea of private vs. public in relation to the individual vs. the collective. The private space being an area (whether physical or virtual) for an individual to be themselves (although with developing technological tools such as blogging or vlogging, this idea is contested). The idea of the collective refers more to the public domain located in a public space, such as government institutions within the public sector and the management of public affairs being for the greater good of the city state.[114] Papacharissi argues that within this historical context, “private property ownership signified status and granted individuals participation rights which led to greater power leverage in public life.” Therefore, it is impossible to define one concept without the other.
One case study which highlights the divide between public and private is the graphic novel and film, Persepolis by Marjane Satrapi. She presents her life growing up in Iran during the Islamic Revolution and how in order to survive physically they had to publicly conform to the regime, whilst to survive psychologically they had to privately rebel by throwing secret parties. This divide between public and private, individual and collectivity is significant in relation to identity and visibility. While Persepolis is arguably an extreme example of the divide, identification and online portrayal is still prevalent in every Facebook profile. While Facebook is arguably both a public and private social networking tool, the way in which individuals engage with it indicates how it blurs the line between the two definitions.
Public Sphere
[edit | edit source]The Public Sphere is a concept that has been defined by many, but put most simply as:
“public is that which does not remain private, and thus can be shared in common.”[115]
The very term Public Sphere happens to be the English translation of the German term Öffentlichkeit, noted by Jürgen Habermas in 1962 in Strukturwandel der Öffentlichkeit (The structural transformation of the public sphere).[116] Historically, Greek and Roman philosophers associated the term public with principles of governance, democracy, and deliberation, “thus, the public man emerged as a citizen of the world, a member of a civil society with civic duties”.[117]
Ideally, the Public Sphere is often seen as private people coming together as a public entity and is often associated with ‘the greater public good’. Habermas noted that some important dimensions of the Public Sphere included the formation of public opinions, which all citizens have access to, and the freedom of conference in an unrestricted fashion.[118] For example, politics (in theory) is transparent and kept in the open for the public to witness and debate on. When a petition receives above 10,000 signatures from the public, the government must respond to it and when it receives above 100,000 they must debate on it in parliament.[119]
Today, both the Public Sphere and Private Sphere can be looked at in relation to the Digital Age we live in as with the introduction and advancement of technology, the spheres have gained an online presence. Not only that, but we, as a nation, are more literate and politically outspoken and the Public Sphere has expanded to almost the stage where it is no longer existent. Arguably, in this day and age, very little is kept in the Private Sphere of people’s lives and the Public Sphere is all encompassing, blurring the lines between the two spheres.
Digital Age
[edit | edit source]The Digital Age can be referred to the information age that has developed due to economic growth. The industrial revolution was a major factor in technological growth. The technical developments in such revolutionary machines, such as the steam engine was just a starting point to what we have now in terms of machinery and computers. The Industrial Revolution also was a pivotal point in society for allowing more work and trade unions. More people were learning new skills to cope with the technical developments. It can be seen clearly as to why the Information Age can also be called the Third Industrial Revolution. Both lend opportunities for society to organize itself and its economic activity. [120]
“There are claims of the new media will replace old media.” [121]
Burnett and Marshall describe the Internet having a “chameleon like nature”. It merges together and lends itself to suit every situation. The digital age allows a range of transmitted information regarding factual, entertainment and shopping. The development of technology means that the use and need for pen and paper is becoming obsolete. Since starting in the 1970s, the Digital Age was a catalyst for filmmakers and writers as they “danced between utopian and dystopian” worlds within their work. For example, Terminator and Matrix, where men manage in a machine world. Now in 2017, the ideas used in such films doesn’t seem to far away.
Global Village
[edit | edit source]Like the industrial revolution, according to Marshall McLuhan, technology recognises society. New skills, new ways of conversing and sharing information allowed McLuhan to coin the idea of the ‘global village’. The global village refers to society being able to easy transfer and share knowledge through technology. The community that is formed is maintained by the structure that the global village has created. “The community structure of exchange occurs at the level of transnational interest of communities who maintain their linkages through the internet” p18. It is this structure that has formed the notion of ‘collective intelligence’.
Collective intelligence “is a form of universally distributed intelligence, constantly enhanced, coordinated in real time and resulting in the effective mobilization of skills.” [122] The digital age has allowed a vast amount of information to be shared, learned and developed further. It is a never ending cycle as the digital age is continuing to grow as we become more advanced and so users knowledge can be enhanced. However, with all this information being sent back and to through transmitters, it is always recorded and coded into the system online. The privacy is not there, completely. There are always ways to trace back this information.
Web 2.0
[edit | edit source]Web 2.0 refers to a second wave of Internet that focuses on User Generated Content (UGC). According to Tim O’Reilly (2005) it is made up by the main characteristics of:
- Radical decentralization.
- Radical trust.
- Participation.
- Users as contributors.
- Rich user experience.
- Remixing data.
- Collective Intelligence.
- Better software by more users.
- Control of one’s data.
UGC has been increasingly popular in terms of media communications. Through social media sites such as Facebook and Twitter, organizations use it to attract views or customers. It has become apparent that users of the internet thrive off being able to share their knowledge or opinions. News organizations allow their readers to comment on social media, and share thoughts and opinions. Clothing brands allows customers to review their purchases which then informs other buyers as well as the company.
It was a term used after the dot.com crisis in 2000 when a large amount of internet companies crashed. By using the term Web 2.0, it suggested a new fresh idea of UGC, even though they were already in the process prior. O’Reilly states that Web 2.0 was needed for “identifying the need for new economic strategies for internet companies”. By suggesting that society and technology is driven by each other, it can be argued that the contemporary WWW is developing in a continuum. Fuch’s claims that the tech and informational structures of the Internet have to, a certain degree, changed in order to guarantee the continuity of the characteristics. [123]
Web 2.0 can also be seen as an "approach to the web", according to David Gauntlett and by collecting ideas, creativity can be enhanced in a way it hasn't been able to before. From this, it can be argued that Web 2.0 has a political aspect to it as users network and connect. [124]
Theorists
[edit | edit source]Danah Boyd
[edit | edit source] | |
| Born | Altoona, Pennsylvania |
| Nationality | American |
| Notable work(s) | Participating in the Always-On Culture (2012) Social Media: A Phenomenon to be Analyzed (2015) |
Danah boyd studied Computer Science at Brown University then went on to pursue her master's degree in sociable media and got a double BA in Economics and Media Studies at Mount Holyoke College in 1995. In 2009, she joined Microsoft Research as a Social Media researcher.[125] She is a frequent blogger and is involved in addressing issues surrounding youth and technology with articles focusing on the implications of social networks for youth identity.
In her chapter on ‘’Participating in an Always-On Culture’’, she outlines the ways in which we have become somewhat “tethered” to our technological devices. The statement “…those little devices in our pockets are so psychologically powerful, that they don’t only change what we do – they change who we are” effectively supports the underlying argument of this Wikibook in that we don’t really know how much these big Internet based corporations know about us; we just go along with the terms and conditions because we have been drawn into the addictive nature of online social media.
Her overarching argument is that the distinctions between online and offline worlds are becoming more and more blurred. That these practices of technologically communicating over a network emulate previous forms of communication. She argues that there is a challenge towards finding the balance between the two distinctions as they are increasingly shifting, that we should embrace this new 'always-on' reality and learn to find a balance between online and offline existence. The notion that we are constantly linked to the network in a state of persistent connectivity presents numerous problems in relation to privacy. The collection (or mining) of data from millions of users allows companies to build up a very detailed profile of user, even if they don't have a particularly broad online presence.
Christian Fuchs
[edit | edit source]Christian Fuchs is a Professor of Social Media at the University of Westminster, UK. He is a Director of the Communication and Media Research Institute and he is also a Director of the Westminster Institute for Advanced Studies.
In 2011 (until 2015) he was Chair of the European Sociological Association’s Research Network 18 (RN18), carrying out Sociology of Media and Communications Research.
In 2012 (until 2016) he became Vice-Chair of the EU COST Action “Dynamics of Virtual Work” that studied unpaid and paid forms of digital labour.
In 2015 he became a member of the European Sociological Associations Executive board and he is currently preparing for the 13th European Sociology Conference which will take place in Athens from August – September 2017.
His interest and expertise lies within social theory, critical theory, critical digital and social media studies and internet and society studies.
His 2014 work ‘Social Media: a critical introduction’ has provided a good base for the ideas which are explored in this Wikibook with a particular focus on his discussions of Web 2.0, Habermas’ concept of the Public Sphere and of his discussion of Google as a Surveillance Machine.
Helen Kennedy
[edit | edit source]Kennedy is a Professor at the University of Sheffield and joined the Department of Sociological Studies as a Faculty Research Chair in Digital Society in November 2014. [126] She first attended the University of Birmingham where she got a BA in English and American Studies, and after that a Masters in Cultural Studies. She worked in the University of East London for eleven years where she set up the one of the country’s first digital media programmes.
Her research focuses on:
- Social Media and Data Mining
- Big data, data visualisation, and data in everyday life
- Digital Media and Work Practices
- Digital and other inventive methods
Kennedy's research is very applicable to Privacy in a Digital Age as she outlines the practices of data mining in her recent book Post, Mine, Repeat: Social Media Data Mining Becomes Ordinary (2016). She has also published Net Work: Ethics and Values in Web Design (2011) and Cyborg Lives? Women's Technobiographies (2001) as well as a number of journal articles on the same topics.
In relation to this Wikibook, data mining is a very prevelent topic for the digital age. Kennedy's book Post, Mine, Repeat is very informative in showing how data mining fits into commercial monitoring and organisations. This topic will be covered further in the book in the sections on Policies and Settings and especially in relation to data mining and adverts tailored to individuals. She also outlines the role of data mining regarding activism and public sector services, how it is adapting and how it relates to surveillance.
Marshall McLuhan
[edit | edit source]Canadian Professor, Herbet Marshall McLuhan (21st July 1911-31st December 1980) was most well known for devising the term, “the medium is the message” and Global Village. His ideas on technical development and society made him a main figure in the media discourse in the 1960s. [127] In his book, The Gutenberg Galaxy, he argued that new technologies would move society from individualism to form collective identities and that “the world would become a computer, an electronic brain”. [128] Though his work was critiqued, McLuhan argued that he 'probed' other thinkers and gave tools to analyse the media and society.
Understanding Media: The Extensions of Man (1964) went to me his most cited work. Here, he suggested that media, in the form it comes in, has an effect on society, rather than the content the media offers. [129] He went on to publish many books and influenced many critics and thinkers on media as it has continued to develop.
Zizi Papacharissi
[edit | edit source] | |
| Born | Thessaloniki, Greece |
| Residence | Chicago |
| Nationality | Greek and American |
| Notable work(s) | A Private Sphere (2010) Affective Publics: Sentiment, Technology and Politics (2014) |
Zizi Papacharissi is one of the key theorists relating to Online Privacy. Papacharissi graduated from Anatolia college in 1991 and received a double BA in Economics and Media Studies at Mount Holyoke College in 1995. She then went on the achieve a Masters degree in 1997 for Communication Studies. She has continued to contribute her research and insight into online communications by focusing on the socio-political impact of new technologies in her book A Private Sphere. She argues that these technologies have seen a shift in the public and private divide and how this shift has altered our engagement in both. She focuses on the way in which the Internet can be used as a political medium to shape democracies. Papacharissi presents her argument around contesting the notion that new technologies can fix old democracy and how citizenship is exemplified in public, private or hybrid online domains.
She has gone on to have four books published, edited two collections and had over fifty journal articles published. She is currently a professor and head of the Communication Department at the University of Illinois-Chicago. She also serves as Editor of the Journal of Broadcasting and Electronic Media as well as being on the board for eleven other media journals. She has been consulted by a number of large conglomerates including Microsoft and Apple and even the Obama 2012 lecture campaign which she discusses in A Private Sphere. [130]
Private vs. Public Persona
[edit | edit source]Introduction
[edit | edit source]In this section of the chapter, the policy and settings of numerous popular social media apps and websites will be looked into in regards to their influence on the online persona of their users. The privacy settings of different social media apps and websites allow users to decide on their audiences. The opportunity to do so reflects the way in which users express themselves online. If a user can determine who their audience is with features and settings, they may be more inclined to be open with what they post and expose more about their true self, likewise, if they are not as in control of who can access their posts, they may be less likely to be as open. In the following section different apps and sites will be explored in relation to their privacy policies and the privacy settings that they offer to their users.
Policies and Settings
[edit | edit source]This section of the Wikibook will explore the privacy policies and different privacy settings that Google, Facebook, Facebook Messenger, Twitter, Snapchat and Instagram all have to offer to their users.

Collecting user data and information is an important aspect of most companies for numerous reasons and even the household name Google can be considered as a “surveillance machine” which [131], monitors its users’ use of its services and collects their data and information whenever they use access Google.
Google’s Privacy Policy states that “When you use Google services, you trust us with your information.” The policy highlights that Google collects information that its users provide, including any personal information used to set up accounts with Google such as names, email addresses, telephone numbers and credit card details. Google also collect any information and data about their users from the way that they use the different services that Google provide for them such as the device information that the users are operating, the log information and their location information. Through the use of cookies and other similar technologies, Google can also access information about the browsers and devices that its users are operating.
Search Engine
[edit | edit source]Google offer a range of different services that user data is collected on including Google’s most popular service, Google Search. Google is the most used search engine of the World Wide Web to date, followed by Yahoo and Bing[132], processing over 3.5 billion search queries daily.[133] As Christian Fuchs stated, “Google has become ubiquitous in everyday life – it is shaping how we search, organise and perceive information in contexts like the workplace, private life, culture, politics, the household, shopping and consumption, entertainment, sports, etc.”[134] Using an algorithm called PageRank, Google orders its search results based on how many links lead to a page. The organisation and ease of the Google search engine because of this algorithm makes it popular both for desktop use as well as mobile browsing. Each search conducted through Google’s search engine is recorded and allows Google to its users interests.
Google can “build a detailed dossier that describes virtually every aspect of your character, food preferences, religious beliefs, medical problems, sexual inclinations, parenting challenges, political leanings and so on”[135] – Robert Epstein, 2013.
Google has its own program called Google AdSense which tracks the browsing history of its users. Through the information Google gains from tracking users search habits, they can personalise the content the user sees and show ads that are specific and relevant to what the user has used Google to previously search for.
“We use the information we collect from all of our services to provide, maintain, protect and improve them, to develop new ones, and to protect Google and our users. We also use this information to offer you tailored content – like giving you more relevant search results and ads.”[136]
Although Google collect and store numerous information of their users and offer personalised content and ads based on this information, Google also states that “When showing you tailored ads, we will not associate an identifier from cookies or similar technologies with sensitive categories, such as those based on race, religion, sexual orientation or health.”
In 2008 Google launched its own browser in competition with other browsers such as Firefox and Safari. Google Chrome allows its users the option to use a private browsing mode called “Incognito”. Unlike a regular search session with Google, Incognito sessions do not save the cookies or the search and the browsing history of the user. [137]
Gmail
[edit | edit source]Google has an email service known as Google Mail or Gmail. Those who have Gmail accounts will need to firstly provide Google with their personal information to set up the account. Google can scan the content of emails sent from non-Google accounts so that it can target ads to its Gmail users.[138]
"Just as a sender of a letter to a business colleague cannot be surprised that the recipient's assistant opens the letter, people who use web-based email today cannot be surprised if their communications are processed by the recipient's ECS [electronic communications service] provider in the course of delivery."
As most Google services are free to use, the majority of Google’s income comes from selling advertisements [139]. As their policy states, Google has automated systems that analyse the content of emails to provide their users with “relevant” product features and tailored advertising. The analysis occurs as emails are sent, received and stored.[140]
Some disagree with this and many have criticised Google for intruding on the privacy of its users’ emails.
“Sending an email is like giving a letter to the Post Office. I expect the Post Office to deliver the letter based on the address written on the envelope. I don't expect the mail carrier to open my letter and read it. Similarly, when I send an email, I expect it to be delivered to the intended recipient with a Gmail account based on the email address; why would I expect its content will be intercepted by Google and read?"[141]

At 1.86 billion users on Facebook each month (as of December 2016)[142], the social networking giant lives up to its name with more monthly active users than other social networking giants Whatsapp, Twitter and Instagram combined.[143] The average Facebook user now has around 338 friends.[144], which is a fair few more than the 130 that Daniel Miller suggested back in 2011.[145]
“Every 60 seconds on Facebook: 510,000 comments are posted, 293,000 statuses are updated, and 136,000 photos are uploaded.”[146]
Despite it being created for the use of students to contact each other in college, Facebook now reaches far and wide across the world and is accessed by a range of age groups.
There is a detailed help page which Facebook has dedicated to explaining privacy settings. The page is very user friendly, accompanied by well organised sections with bold titles and graphic icons. While the page appears to be transparent in its bid to inform users of how their data is used, there are somewhat ominous undertones. It emphasises how much the user has control over who sees what with the heading in large font claiming “You’re in charge”. After looking through the privacy basics, there is a section about Facebook’s Data Policy. A lot of the way this policy is phrased is very biased towards presenting a particular image of Facebook: “We collect information about the people and groups you are connected to and how you interact with them”. This suggests that the collection of data is in the user’s best interest, in order to “provide, improve and develop Services”.
Facebook users can change the settings of their accounts to different levels of privacy so that, in theory, the audience seeing the information they post is controlled by them. A profile account which is set to private means that only friends can see the content that they post. Likewise, a profile account which is open can be viewed publicly. Facebook also allows its users to control the privacy of individual posts and individual information in their “about me” sections. A user can decide between sharing what they post “everyone”, with “friends of friends” and with just “friends”.
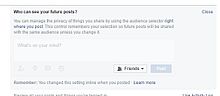

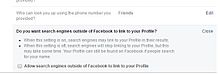
Some of the main features of Facebook’s user security can be found be going into the “Privacy Settings and Tools” page. In this page users can edit a number of things:
- Users can change who can see their future posts
- Users can also “Limit The Audience for Old Posts” on their timelines, which means all their previous older posts can be hidden from the public and from friends of friends and only be able to be seen by friends.
- Facebook allows its users to control who can search for them and contact them, too. Once again users can choose from “everyone”, “friends of friends” and “friends”.
- Users also have the option to keep their profile from appearing in search engines when people type in their names.
Not only can Facebook users change the privacy settings of their own posts to suit their desired audience, but if a friend tags them in a post, posts on their timeline or tags them in photos they can edit their settings so that they control who can see these things.
By going into the Timeline and Tagging Settings in their account Facebook users can:
- Edit who can post on their timeline and choose between their friends or limit it to just themselves.
- Review posts that friends have tagged them in prior to them appearing on their own timeline. This means they can filter which posts they want people to see that they’ve been tagged in and which ones they don’t want on their timeline.
- Aside from reviewing posts, users can also edit their settings so that no posts that they’ve been tagged in appear on their timeline at all and no posts that others have made to their timeline show either.
Facebook also let their users control who can add tags to their own photos so that other users cannot tag themselves or other people in a photo without the original poster’s permission.
Facebook Messenger
[edit | edit source]Released in 2011 as an app dedicated to instant messaging, Facebook Messenger now has over 1 billion users (as of July 2016), a seventh of the world’s population.[147] The app imports the user’s contacts from the Facebook service and can be used on a number of devices. Over the years, Facebook’s messaging service has adapted its features to show who is online, how long ago someone was last online and the time someone has “seen” a message. Interestingly, Whatsapp is the most popular messaging app (although it was bought by Facebook in 2014), while Facebook Messenger is the third most popular, a Chinese messaging service called QQMobile taking second place.
There aren’t any clear sections on the individual policies regarding private messaging data collection, but a Google search brings up this article which details their tracking practices breaching European law[148]. On the surface, Facebook’s privacy basics help page paints a picture of the user being in complete control of their data. The reality is that the network tracks the web browsing of everyone who visits a page on its site, even if the user doesn’t have a Facebook account or has opted out of tracking. There are two new options which Messenger has added to its service in relation to privacy - payments in messenger and encrypted messages.
- Payments in Messenger - This service was implemented in March 2015 in the US. It allows users to send money to their friends by tapping the '$' sign followed by the amount you want to send. The Facebook newsroom[149] has a guide on how to send and receive money along with information about security including the assurances that Facebook “uses layers of software and hardware protection that meet the highest industry standards.” There is a lot of scepticism surrounding this kind of service as there is no further information on the page about how their security works. The effectiveness of this service ultimately lies with the user’s own responsibility and trust with the system. The main concern would be people stealing user’s phones and sending money to themselves.
- Encrypted messages - In October 2016, Facebook released an end-to-end encryption option for messages. The function is an optional feature known as ‘Secret Conversations’. These encrypted conversations allow users to set messages to ‘disappear’ after a certain length of time. In theory, end-to-end encryption means only the communicating users can read the messages and the systems have been designed to defeat any surveillance attempts since no third parties can decipher the data being communicated or stored. However, for the strong encryption to work effectively, only the sender or receiver of a message can have the ability to decode that message. If Google or Facebook has the ability to process the messages, it’s hard to guarantee that only the two people messaging one another are the only two reading.

Twitter is an online news and social networking service where users post and interact with messages, "tweets," restricted to 140 characters. Twitter has a dedicated page explaining their privacy policy and how information is collected, used and shared. It states clearly that “when using any of our Services you consent to the collection, transfer, storage, disclosure, and use of your information as described in this Privacy Policy.”[150] It goes on to describe where the data controllers are located (in the USA, they’re based in San Francisco, outside the USA they’re based in Dublin).
They frequently reiterate that the user alone is responsible for what content they submit through their services. They state that “most of the information you provide us through Twitter is information you are asking us to make public”. They allow a great degree of control over privacy settings and what information is shared with third party services such as the ad tailoring suggestions; if you do not want Twitter to tailor suggestions based recent visits to websites that have integrated Twitter buttons or widgets, you can turn off this feature using the Twitter account settings or Do Not Track browser setting.
They also receive the following Log Data information when their service is used: IP address, browser type, operating system, the referring web page, pages visited, location, mobile carrier, device information (including device and application IDs), search terms, or cookie information. They emphasise that they use this information to analyse data trends (through Google Analytics) in order to improve the service they provide.
Like a number of websites, Twitter uses cookies to collect this data. They use cookies in the following ways: Authentication and security (log on details and security protection), preferences, analytics, research, personalised content and advertising. The information collected in relation to advertising is used to customize their services with more relevant content, like tailored trends, stories, ads, and suggestions for people to follow. There is an option in the user settings to opt out of this.
With the direct, private messaging service Twitter provides, they also store the user data. They say “When you privately communicate with others through our Services, such as by sending and receiving Direct Messages, we will store and process your communications, and information related to them. We do not use the content you share privately in Direct Messages to serve you ads.”
There is also a section on their website here which demonstrates the ways in which Twitter supports online safety and actively advocates for lobbyists who work on issues reflecting internet freedom, national security reform, ECPA reform and patent litigation reform. The information collected in relation to advertising is used to customize their services with more relevant content, like tailored trends, stories, ads, and suggestions for people to follow. There is an option in the user settings to opt out of this also.
With the direct, private messaging service Twitter provides, they also store the user data. They say “When you privately communicate with others through our Services, such as by sending and receiving Direct Messages, we will store and process your communications, and information related to them. We do not use the content you share privately in Direct Messages to serve you ads.” There is also a section here which demonstrates the ways in which Twitter supports online safety and actively advocate for lobbyists who work on issues reflecting internet freedom, national security reform, ECPA reform and patent litigation reform.
Snapchat
[edit | edit source]
Snapchat is an image sharing application that allows users to send one another pictures which "disappear" after a set amount of seconds. According to The Online Real Life chapter, the development of the app has introduced photographic and video filters that offer a voice alteration and the option of sharing pictures for up to ten seconds at a time. Pictures are also able to be saved to one's "memory" as well as posted on the user's "story" that is visible to all of the users in their Snapchat contactg list. It also offers the option to follow the stories of news, celebrities, and current events.[151] This on-going development in applications is a continuous and fluid process which allows user feedback to be implemented on the software.
The website has a section dedicated to the company's privacy polices which can be found here. There are four sections which outline the company's policies:
- Your Privacy Matters - an introduction to the privacy policies.
- Our Approach to Privacy - an outline of all their features and how privacy and security is applied to each.
- Transparency Report - a description of their bi-annual transparency reports in relation to judicial requests. This section covers requests from the government if they need information regarding a legal case.
- Privacy Policy - a list of what data Snapchat collects from users and why. This section has a very in-depth explanation of all the information the company collects along with this advice: "So, the same common sense that applies to the internet at large applies to Snapchat as well: don’t send messages or share content that you wouldn’t want someone to save or share."
The app has been criticised for its lack of transparency regarding user's privacy. Because Snapchat is commonly used for sharing sensitive and private images, the perceived promise of images "disappearing" forever was incorrect. According to this article from The Independent website, "Snapchat’s terms of service allow the company to look through your snaps and share them publicly."[152] The distinctions between public and private spaces is challenged here as users sign up for the service without being aware of their privacy being breached.

Instagram is a social media platform originally curated to provide a space to share photos which can be edited through the app itself. Through the developments of other apps, Instagram has seen an increase in features, most recently 'Stories" which now competes with popularity with Snapchat. Melson and Papachrissi claim that photographs can be a "mnemonic and symbolic device" [153] and by uploading them online, on whatever platform, they can record memories, and they are forever stored online. The idea that photographs can be used to portray a persona is stressed and Instagram, it can be argued uses this, as each photo, encouraged to crop and filter, can only capture the moments the user wants to share and remember. Users actively choose what to share and what to keep private, however, the body of the users are no longer hidden through the increase in visual communication, compared to 1970s-1990's, only when the webcam was introduced and became a strong feature in ways of communication online. [154]
According to help.instagram.com, “By default, anyone can view your profile and posts on Instagram.” Only by selecting the “Private Account” setting can the user make their account private. However, on the help page, it raises the issue that if the user shares their post to another platform, the post can be seen by non-followers and anyone can still directly send videos and photos. If anyone wants to follow a private account, it will have to be requested and approved or ignored by the account holder.
Boyd highlights the meaning behind the power of choosing your followers, referring to them as an ‘audience’ just as a television personality must tailor their content to a specific target audience. She argues that “privacy settings allow teens to limit their expressions to the people they intend to reach by restricting who can see what.” [155] This links back to Rettberg's idea that photographs are taken to preserve a memory that we want to see, and what we want others to see and perceive as a portrayal of a lifestyle or persona.
However, Instagram can be used by accessing it through a third party application, for example, flipboard. Instagram’s privacy settings highlights that posts can appear on Google through these sites, despite being a private profile. Instagram states that it “isn't directly associated with third-party apps that utilize our API such as web viewers, desktop apps or image printing services, and we can't assist you in speeding up the process to remove any Instagram images that may appear on Google”
Instagram is owned by Facebook which uses cookies to track data. Instagram introduced adverts to their feed and according to their help page, Instagram wants to “show ads that are interesting and relevant to you”. Due to Facebook being the parent company, the adverts are encouraged by what you search, ‘like’ and apps that you visit. Facebook also tracks the cookies that you search through your browser and so links that to Instagram.
Individual vs. Collective
[edit | edit source]This section will outline the ways individuals and their relationship to the collective has transformed since the advent of the digital age. The section will cover the historical context of the terms as well as an outline of the socio-political benefits that have been discovered.
The concept of privacy has varying definitions depending on the individual. In societal terms, property bought by an individual is deemed to be their private space which they own. Of course, there are historical buildings belonging to Kings and Queens which would have been closed off to the public, but are now open as a site of tourism. Public space such as parks and town centres are looked after by the community, either through council tax or volunteer work. Therefore, the concept of public and private in relation to the individual and collective is very fluid and often historically interconnected. The notion of shared space tends to revolve around maintaining it to a high standard for the benefit of all the community, something which has been translated to digital space. Papacharissi defines privacy in contrast to the public:
“What is individual, versus what is collective or affects the interest of a collectivity of individuals”.[156]
In relation to the digital age, the Wiki project can arguably be paralleled with the community projects of towns and cities, it’s just that the individuals contributing to the sites are from all over the world. This shift from local and regional to global interconnectivity has seen a transformation in the way communication occurs. Because users are anonymous on Wikimedia, people are no longer pre-judged based on appearance. They are now evaluated based on a level of engagement and specialist knowledge. Therefore, each individual’s input on an area of expertise allows the overall collective project to improve.
Papacharissi states that “civil society is conceptualised as distinct from the market or the bureaucracy of the state, either of which carry the potential of suppressing the will and actions of atomized individuals operating collectively”. This statement is very prevalent in today’s society, with the advent of “fake news” and “alternative facts”, individuals now have to carefully determine what is true and what is false propaganda. The use of petitions in order to accelerate change has been one of the oldest forms of collective public engagement with the state. In the digital age, citizens are now able to sign a petition online with an email address and post code. The ability to quickly share this petition via social media shows the speed at which communication has improved. The notion of the online world being a tool for political engagement is further discussed in the chapter The Hive Mind and Collective Intelligence.
One fictional case study which can be applied to the individual vs. the collective is the Borg in Star Trek. The Borg are a collection of species that have been turned into cybernetic organisms functioning as drones in a hive mind called "the Collective" or "the Hive". The show explores the benefits and drawbacks of collective intelligence. It challenges the ethics of freedom, individuality and creativity especially in relation to the character Seven of Nine, who was liberated from the collective and spends the rest of the series of Voyager attempting to rediscover her individuality. At first, she struggles to lead a life without the voices of millions of other Borg, but she eventually learns to work within the collective of the Voyager crew.
The Borg are a very effective example of how technology can be used to work together in order to improve efficiency, with their sole aim as "achieving perfection". Yet the show arguably foreshadows the challenges and dangers of this kind of technology. Dery argues that "our interaction with the world around us is increasingly mediated by computer technology, and [thus] bit by digital bit, we are being "Borged"...transformed into cyborgian hybrids of technology and biology through our ever-more-frequent interaction with machines".[157] This blurring between human and machine is further explored in Technology as an Extension of Self.
To sum up, the relationship between the individual and the collective depends on a distinction between public and private space. In the "real world", the distinction is made between ownership and community based spaces, but in the virtual world those distinctions become somewhat blurred. With Wikimedia projects, the community space is no longer limited to proximity; it is part of the global space with interconnecting contributors from all over the world taking part and engaging. In relation to privacy in a digital age, this topic highlights the notion of transparency in politics. Laws that affect the public are able to be discussed openly and with increasing interconnectivity through social media, people are able to organise petitions and marches to encourage positive change.
Location Services on Apps
[edit | edit source]As smartphones and the internet become more prominent in our lives, users are becoming more aware of the idea of having their search habits and locations tracked. Privacy in the digital age recedes further into the distance as the tech companies tell users it’s all in the interest of a better, faster and more efficient service. However, users may also find location services invasive, targeting you with local ads or letting apps track you when you don’t want or need them to.
What are Location Service Apps?
[edit | edit source]Firstly, what does location services mean? Well with the users’ permission, location services allow native apps such as, (iOS’s Maps, Weather and Clock), third party apps (Uber, Facebook), and also system services (Compass, Location-based alerts, Time Zone) to use information from cellular, Wi-Fi, GPS and Bluetooth to determine the approximate location of the user. The prime example of using a location service app would be Uber. The innovative taxi service requires the users to download the app, register and provide credit card information. When they request a car, the app uses GPS technology to find their location and alerts available drivers within a certain radius. If no driver responds then the radius grows.
Benefits of Locations Services
[edit | edit source]Location services help companies like Apple and Google, which may in turn help the user. They companies can learn which apps are most geographically relevant to people in your area, which can help track all the places you have recently visited for improved traffic routing. Another beneficial use for location services is, “Find My iPhone” or “Android Device Manager”. These apps rely on access to your device in order to locate and track your lost device.
Here are some examples of how popular iPhone and Android apps use your location information:
- Instagram: Requires your location in order to name it in your post.
- Facebook: Geotags your posts and photos to create a digital journal of all the places you have been. Location services also enables check-ins, tips about places you are visiting, recommendations and notifications about which friends are in your area.
- Twitter: Geotags photos and tailors trending stories to you.
- Tinder: The dating app which finds matches near your location.
- Foursquare: Suggests nearby businesses or products.
- Google Maps: The service offers turn by turn instructions from your journey start point to your destination. It can also inform you about nearby points of interest.
Use Apple as an example, they offer three location-based settings, “Never”, “While Using the App” and “Always”. These settings are put in place for users to choose what app they allow access to their location. The reality of it is, in order for consumers to share their information they need to give permission to do so. However, not everyone understands the real benefits of allowing their location to be shared and questions are asked about the privacy of users [158].
Negatives of Location Services
[edit | edit source]Location based apps are changing the way all sorts of industries interact with their consumers. While location services have upsides they have as many downsides. Despite draining your battery life, users find sharing their location information with certain apps discomforting. Having your location monitored comes with privacy and security risks. Sharing this sort of information can be advantageous to criminals, putting your security at risk. One of the most evident problems with using location based service apps is the ability to switch them off. There are obvious complications associated with using this technology.
There seems to be a fine line between convenience and privacy. At what point do users want their data hidden and what point do they want to take advantage of crowd-sourced data.
'Knowledge is Power'
[edit | edit source]As location based technology advances increased privacy concerns arise. Some location based apps require users to opt-in before sharing any information, but users are still uncomfortable with the idea of being tracked. Despite its conveniences, sharing any kind of information can also be risky. However, 'knowledge is power' and people should try and educate themselves so they can understand how their data is being used or know how to disable the features of location service apps [159].
Privacy Laws
[edit | edit source]Since 2011, the discussion of laws affecting and moderating the internet have grown significantly. Several laws of passed or attempted to pass in major nations such as the United States, the United Kingdom, and China, which have or would have seriously affected the use of the internet. These affects include blocking sites, legally restricting search engines from displaying certain results, blacklisting entire online services, and in general called into question the rights of individuals on the internet.
PIPA
[edit | edit source]One the first major law that dealt with online privacy, or at least the first one to meet massive criticism was PIPA or the Protect Intellectual Property Act. It came about in 2011 and was made to counter the massive amount of pirate sites on the web. It was heavily lobbied by corporations in order to more heavily enforce copyright law [160] which was a goal wanted to be achieved since the creation of websites such as Napster and LimeWire who helped popularize internet piracy, with one of the bigger problems now being that the servers for these new pirate sites where no longer in the US and were out of the Government's jurisdiction.
It key selling point was to be able to target specific sites who's activities were deemed illegal, and have a court order force search engines to not only blacklist those sites from the search results but also disable all hyperlinks to said websites, effectively cutting off access to torrent sites from anyway other than typing the URL in directly.
It was met with massive criticism with many people claiming it could be used as a stepping stone for harsher internet laws and that Corporations could abuse the Act, using individual acts of copyright infringement to target massive legitimate sites such as Youtube, Twitter, Facebook. There were also claims that this law could be used to target individual creators who could be hit with false claims that they could not afford to counter. There were many comparisons to China's massive firewall in this argument. Ultimately the bill was put on indefinite hold until its many flaws were rectified
SOPA
[edit | edit source]Much like its Sister bill PIPA, SOPA (Stop Online Piracy Act) was designed to target online piracy to help better enforce copyright in the face of an ever-growing world wide web filled with illegal torrent and streaming sites. It also had the angle that it was targeting piracy outside of the United States which it claimed would be hurting the US economy as well as weakened the strength of copyright. The bill received strong support from both the House of Representatives and the Senate, as well as the Better Business Bureau, and several other major Corporations who believed they were being seriously harmed by piracy.
The affects of the bill would have been almost identical to PIPA, removing blacklisted sites from search engines, blocking ISP addresses, ect. And much like PIPA, SOPA was met with mass negative backlash. Many people claimed that this bill actions would not only jeopardize the foundation of the internet by stifling creation and shared media due to how easy it would be to abuse Copyright claims, but the idea of forcing search engines to blacklist sites was seen as a violation of the first Amendment. Several websites, including Wikipedia participated in online blackouts to showcase the affects the bill could have on the internet. It aimed to remind people of the importance of a free and open web. [161]
Ultimately, much like PIPA, the bill was not put through, much to the disappointment of many of its supporters.
UK ISP Blocking
[edit | edit source]In the UK, with the introduction of the Digital Economy Bill 2016-17, a new law came into place that forced several Broadband supporters to automatically block any Adult sites as well as certain blacklisted pirated sites. The original idea for the law stemmed from the EU's discussion of new Net Neutrality laws. The aim of this was to prevent children from having easy access to pornography in the face of an ever-growing digital world where most devices can easily connect to the internet, as well as prevent access to pirated sites and crack down on any child pornography. There was also the option for the customers to opt out of the adult content filter though this had to be done manually.
This law was met with criticism because while its affects on piracy and child pornography was praised, many people felt it was being used to wedge the government's will into online rights via moral panic. Some members of the online community argued that by targeting pornography the UK government was able to make a first step towards further Internet censorship by going after something people were uncomfortable or less comfortable defending. Many people also called into question what would happen to a site if it was wrongly blocked, as well as what the term adult website would actually be categorized as? [162]
In the end however, the bill was tabled on November 24th and now it remains in the air as to what will become of it. [163]
Internet Censorship
[edit | edit source]Introduction
The Internet in the 1990’s was described by Jaron Lanier as being a space where users could promote individuality, as early web pages had “flavour of personhood” [164]. The internet also holds a vast expanse of useful information that can help users gain knowledge and has the capability to let users communicate with other users across the globe, sharing news or collaborating to create new forms of information. But what happens when the user’s individuality and the information being shared between users expresses conflict with the over-ruling government ideologies?
Internet censorship can be used to squash and decimate any conflicting information which is very concerning when discussing user privacy. For instance, the Government of the People’s Republic of China and the Myanmar (Burmese) Government have a long history of using extreme internet censorship as a method to control what information users can access and publish online [165]. In 2008, cybercafés in Myanmar (Burma) were required by state regulations to screenshot the user’s computer every five minutes and upload this information to the government every two weeks [166]. This example gives an idea on how intrusive governments can operate and track the publics usage of the internet.
Methods of Internet Censorship
Filtering is a key process for creating internet censorship. Most Web filters use blacklisting and keyword blocking techniques to filter out the undesirable web pages. (See above to view blacklisting Privacy Laws) A blacklist is a list of web sites that are deemed undesirable by the companies that make the software or the governments who use web filters. Keyword blocking filters examine the words searched by the user on search engines like Google or Bing to determine if the web pages are inappropriate. In 2017, most internet providers like Sky or BT offer the option of filtering through parental controls settings, users can decide to restrict access to dangerous sites like pornography, chat rooms or gambling. This filtering is used to control what children can view on the internet, censoring any inappropriate information. Government filtering shares the same principle as parental controls but on a much grander scale, the general population is portrayed as being the children in this circumstance.
With 721 million internet users in 2016 [167] the Government of the People’s Republic of China have an enormous job of keeping track of users viewing undesirable information. Hence the “Great Firewall of China” [168]. Firewalls act as a security system that controls and monitors the network traffic of users based upon the security rules of the company or government servers installed on [169] . It often acts as a barrier against any unwanted or potentially harmful websites. Due to the restrictive content of the internet by firewalls in China, a growing number of users rely on virtual private networks (VPN’s) to gain more freedom on the internet to visit sites like Facebook or YouTube which are often blocked by the government. However, the Chinese government in 2017 is reportedly stepping up the fight against illegal VPN’s in a bid to discourage the population from western media [170].
Pros and Cons of Internet Censorship
It is difficult to argue that there are positives for invading user privacy just because the information seems undesirable to government ideals who then make it inaccessible for other users to see or share. But there are some nonetheless.
Pros
• It creates a safe environment for children using the internet. With the average age of kids receiving their first smartphone at 10.3 years [171] old, access to the online world is becoming increasingly easy for children to reach. Censoring filters help eliminate any inappropriate information that could be viewed by kids.
• Strict censorship filters show potential in discouraging illegal activity online, as it makes it extremely difficult for users to illegally download movies and music. It also has a low risk of user accounts being hacked due to the level of firewall security.
Cons
• The main con about Internet censorship is that it discourages freedom of individuality and self-expression. The internet is a creative network with individuals coming together to create new ideas or expressing opinions, censoring these creative instincts will diminish any opportunity for cultural and social growth.
• Censoring information may lead to a stalemate of knowledge growth. The internet holds a vast amount of information in web pages and it can be complicated to decide what sites show useful or harmful content. So, governments will block and censor harmful content but in the same process might block pivotal information. For example, some keyword blocking filters have struggled to understand context. A simple search of “chicken breast recipes” will single out the word breast and deem it as an inappropriate search.
Top 20 Worst Countries For Internet Freedom[172]
| Countries | Ranking | Internet Freedom Score (the less the better) |
|---|---|---|
| China | 1 | 88 |
| Syria | 2 | 87 |
| Iran | 3 | 87 |
| Ethiopia | 4 | 83 |
| Uzbekistan | 5 | 79 |
| Cuba | 6 | 79 |
| Vietnam | 7 | 76 |
| Saudi Arabia | 8 | 72 |
| Bahrain | 9 | 71 |
| Pakistan | 10 | 69 |
| United Arab Emirates | 11 | 68 |
| Gambia | 12 | 67 |
| Thailand | 13 | 66 |
| Russia | 14 | 65 |
| Sudan | 15 | 64 |
| Kazakhstan | 16 | 63 |
| Egypt | 17 | 63 |
| Belarus | 18 | 62 |
| Myanmar | 19 | 61 |
| Turkey | 20 | 61 |
This table shows the top 20 worst countries in the world for freedom online. China tops the chart due to its extensive censorship and its crackdown on social media, discouraging many users [173]
Surveillance
[edit | edit source]For most of us, posting information online is a part of our daily routine. We use the internet to stay connected with our friends and update the people closest to us about what is going on in our lives. When we post something online we don’t assume that it goes further than the people we intended it to. However, this couldn’t be further from the truth. Our personal information, even that which we don’t make absolutely public, is being tracked and can be accessed by the government and third-party-marketers.
All of the information contained within the tweets we write, the emails we send or the photos we upload is comprised of metadata. Metadata is “increasingly a fundamental aspect of our modern existence, as it records the shape of our lives and then reshapes life accordingly”. [174] Metadata gives information about other data, so that includes the date, time and the IP address. With this in mind, through the information we post online whether it be via a laptop or mobile phone, we could be tracked down very easily and quickly.
Data Surveillance
[edit | edit source]Data surveillance can be defined as “the collection of information about an identifiable individual, often from multiple sources, that can be assembled into a portrait of that person’s activities.” Due to the fact that a majority of computers automatically store and track data our online activities leave behind what are known as ‘data trails’. These data trails make it simple for organisations to gather information about us, including our current location, without us being aware of it. Jay Stanley and Barry Steinhardt believe that it will soon be possible, due to data surveillance, to gather and combine information about an individual so that their online activities can be recreated “with such detail that it becomes no different from being followed around all day by a detective with a video camera.” [175]
Investigatory Powers Act 2016
[edit | edit source]Receiving Royal Assent in November 2016, the Investigatory Powers act legalises the most extreme surveillance in the western world. The act allows police and intelligence agencies to hack into mobile phones and computers regardless of whether the person under scrutiny is suspected of wrongdoing or not. The main purpose of the act is to counter terrorism and catch criminals however Julian Huppert, former MP and lecturer, states “some of the powers in the bill are deeply intrusive, and with very little possible justification. All of us want to be safe, and protected from terrorists and the like – but the evidence that these powers are all needed is thin indeed. However, the cost to all of our privacy is huge.” [176]
The act has come under scrutiny and privacy groups are challenging the powers set out by the act in the European court of human rights. These groups have argued that these powers are more applicable to a dictatorship than a democracy because citizens can be monitored and analysed closely. Chief executive of the Big Brother Watch, Renate Samson, stated "none of us online are now guaranteed the right to communicate privately and, most importantly, securely.” [177] Whilst the act is in place to monitor illegal activity and fight back against criminals, it opens up the opportunity for everyone to be monitored. Sometimes we post information online or search for topics which can be misinterpreted by someone who doesn’t know us. This could potentially put us in a difficult position if we are being watched so closely.
Personal Information Online
[edit | edit source]Nowadays, online users, without realising it, may be revealing a huge amount of personal information to other internet users. This of course can be advantageous but it also has many disadvantages. Personal information could be used against the user, which could be potentially dangerous or damaging to their reputation or status. While many users take particular precautions to prevent exploitation of their information, it remains extremely difficult for them to stay invisible online.
In July 2013, Princeton Survey Research Associates International conducted a survey along with Pew Research Center’s Internet Project, in which 1002 adults above the age of 18 were interviewed about their personal information online.
“For results based on the total sample, one can say with 95% confidence that the error attributable to sampling is plus or minus 3.4 percentage points and for the results from 792 internet and smartphone users in the sample, the Margin of error is 3.8 percentage points.”[178]
| Personal Information | % of adult internet users who say this information about them is available online |
|---|---|
| A photo of you | 66% |
| Your birth date | 50% |
| Your email address | 46% |
| Your employer/company you work for | 44% |
| Things you’ve written using your name | 38% |
| Your home address | 30% |
| Which groups/organisations you belong to | 29% |
| Your mobile phone number | 24% |
| Your home phone number | 21% |
| A video of you | 21% |
| Your political party/affiliation | 20% |
The survey continues to look at some of the users’ problems that they have encountered in terms of breaching of security. Their online visibility became inflicted and personal information had been stolen from a vast amount of the users. Email and social media accounts had been seized, Social Security/credit card numbers had been exploited, as well as stalking, harassment and victimization being taken place.
- 21% of internet users have had an email or social networking account compromised or taken over by someone else without permission.
- 13% of internet users have experienced trouble in a relationship between them and a family member or a friend because of something the user posted online.
- 12% of internet users have been stalked or harassed online.
- 11% of internet users have had important personal information stolen such as their Social Security Number, credit card, or bank account information.
- 6% of internet users have been the victim of an online scam and lost money.
- 6% of internet users have had their reputation damaged because of something that happened online.
- 4% of internet users have been led into physical danger because of something that happened online.
- 1% of internet users have lost a job opportunity or educational opportunity because of something they posted online or someone posted about them. [179]
The survey reveals that 86% of online users have tried to use the internet with different methods to minimalize their online visibility, whether it was from hackers/criminals, advertisers, certain friends or people from their past, employers, the government or from the people who run the websites they visit.
| Strategies people use to be less visible online | % of adult internet users who say they have done these things online |
|---|---|
| Cleared cookies and browser history | 64% |
| Deleted/edited something you posted in past | 41% |
| Set your browser to disable or turn off cookies | 41% |
| Not used a website because it asked for your real name | 36% |
| Used temporary username/email address | 26% |
| Posted comments without revealing who you are | 25% |
| Asked someone to remove something posted about you | 21% |
| Tried to mask your identity | 18% |
| Used a public computer to browse anonymously | 18% |
| Used fake name/untraceable username | 18% |
| Encrypted your communications | 14% |
| Used service that allows you to browse the web anonymously | 14% |
| Given inaccurate information about yourself | 13% |
Online Shopping and Banking
[edit | edit source]Online shopping is a type of electronic commerce that allows digital users to purchase goods or services online, on internet websites or applications run by retailers or vendors. This can be done on computers, tablets and smartphones.
Online banking is a digital payment system that allows users of a bank to make financial transactions through the banking website or application. This can be done on computers, tablets and smartphones.
Certified websites prove their security by including a ‘https’ at the beginning of the URL.
“Hyper Text Transfer Protocol Secure (HTTPS) is the secure version of HTTP, the protocol over which data is sent between your browser and the website that you are connected to. The 'S' at the end of HTTPS stands for 'Secure'. It means all communications between your browser and the website are encrypted. HTTPS is often used to protect highly confidential online transactions like online banking and online shopping order forms.”[181]
Some web browsers also display a yellow padlock on the toolbar to indicate security.
However, on some online shops, this ‘security’ isn’t displayed. While some companies may be completely genuine and moral towards customers and their personal information, other online users can exploit the websites and obtain this information. This information can be used unethically, and be sold to advertisers who contact their ‘new customers’ via email, text or post with ‘offers’ and company information. While this isn’t harming the victims, it can be seen as immoral and annoying. In alternative situations, people can steal personal information and commit Identity theft. No banks are completely secure and once a user’s information is compromised, it can take sometimes years to correct the damage, and can even cost a lot of money to fix.
Privacy and Leaks
[edit | edit source]Ess (2009) argues that “many people assume that their email communications are more or less private.” [182] However, he notes that although the emails we see don’t contain much information – just the content, the email address, a time stamp – they do in fact contain a lot of information about ourselves that we perhaps would not like to share.[183] As most people are not aware of the extent of personal information they’re sharing, this can lead to problems when they are hacked. This section will investigate case studies of celebrity and non-celebrity hacks in order to demonstrate the broader social consequences and impact of hacking private information.
Spyware
[edit | edit source]What is Spyware?
[edit | edit source]
In Adrian Athique’s Book “Digital Media and Society” he claims that at least 89% of computers and infected with spyware.[184] There are multiple kinds of spyware with varying objections, but spyware overall can be defined as a piece of software that was undesired by the installer. It falls under the category of malware, meaning it is designed to intrude the software and is of malicious intent. Spyware often “piggybacks” with instalments that the user chose to make, and can infiltrate a device undetected. It is used to gather information on the user, be it something as small as their browsing habits, all the way up to their security details and bank numbers. Spyware is the main culprit in the majority hackings, as it allows passwords and other such private information to be collected and stolen discreetly, most often unbeknownst to the victim. The first recorded usage of the term “spyware” was coined in 1995, contained in a post mocking Microsoft’s business model, and it was continued to be used in reference to the malware that was becoming more and more frequent.[185] Subsequently, the first anti-spyware (“OptOut”) was created in 1999 after Steve Gibson of Gibson research suspected that his software had been infected and was stealing his personal information.[186] Since then, anti-virus software has become a prominent part of internet usage. A study conducted by Microsoft in 2013 found that computers that browsed without anti-virus software were (on average) 5.5 times more likely to become infected.[187]
The Dangers
[edit | edit source]There are several consequences that can follow a device being infiltrated with spyware. Software that has been affected doesn't necessarily mean that this results will occur, as they are the most severe result and therefore the worst-case scenario, but each instance does still run the risk.

- Keylogging: Keylogging is the act of tracing what the user is typing, as it records each key as it is pressed and in what order. A lot of spyware is programmed to flag up any succession of numbers that resemble card numbers, but it is also used for finding out users password and other confidential account details. A device that contains keylogging spyware is unsafe to use for any form of money transaction, as well as anything password-sensitive.[188] Keylogging, however, isn't just restricted to spyware that sneaks in through other instalments, as it can be achieved through external hardware plugged into the computer itself. This form of keylogging is often committed by employers or parents that want to keep a track of what employees/children do with their time online. These hardware devices are commonly plugged into the USB port of the computer and are easy to recognise after being made aware of them.
- Identity Theft: This is when a real-life identity is stolen and used to commit fraud. Through spyware, enough personal information on the user can be gathered which then allows their identity to be stolen by another. Identity theft can be used for taking out loans, applying for jobs, catfishing other people and other high-risk acts that can leave the victim with irreversible damage. A recent study revealed that in 2015, 13.1 millions U.S citizens collectively lost over $15 billion as a direct result of identity theft, which averages to roughly $1,145 per person.[189]
- Loss of System Performance: When a device is infected with spyware, performance quality can take a massive as a result. This can cause difficulty connecting to the internet, a slower running speed, as well as frequent crashing. Spyware is the leading cause in trips to professional repairers, as it can cause a 50% decrease in performance[190] in the most severe cases, it even becomes an "invisible" cause, therefore very few understand why the loss of performance quality has even occurred.
Google AdSense
[edit | edit source]One potentially disturbing fact frequently gets lost amidst debates about the fate of privacy in the digital era and the crossfire between celebratory and critical claims about the online economy; namely, the emerging commercial model for the interactive economy has become reliant on the prospect that information-based target marketing and data mining will be increasingly effective in manipulating and channeling consumer desire
Google AdSense is designed to generate contextual advertising. Through the use of Google AdSense, companies and sites can pay to advertise a more targeted audience, as Google AdSense tracks the browsing history of the consumer and then presents them with advertisements that are relevant to their previous searches. This is turn produces a larger amount of clicks, and allows Google to charge more for displaying adverts as opposed to general advertising. As mentioned, this functions through the use of browser tracking. While this wouldn't be considered spyware, as Google AdSense isn't a separate feature installed into a device nor does it have malicious intent, this still causes discomfort among users as this form of advertising and the process behind it isn't considered common-knowledge and many are unaware of the search-tracking that takes place.
Due to many spyware programs being designed to: 1. Track browsing habits and 2. Cause pop-up advertisements, it is fair to be sceptical of Google AdSense. Benjamin Edelman is a professor at Harvard Business School who looks into how online markets function[192], and found that the "pay-per-click" function of AdSense was being exploited through the use of spyware. AdSense partners were paying a company (180solutions) that was considered spyware to project their advertisements through unwanted pop-up adverts, increasing the number of clicks and therefore their revenue. While Google was not actively encouraging the use of spyware in these situations, they failed to prevent it and allowed their system to be exploitable through spyware and inadvertently caused an increase.[193] It also can't be known if the spyware's function was solely dedicated to the creation of pop-up advertisements, or if they were simultaneously keylogging or stealing personal information, creating a potentially even severer scenario.
Celebrity Scandals
[edit | edit source]Some of the most popular scandals is Janet Jackson and Justin Timberlake’s in the 2004 Superbowl performance. [194] After announcing that it was "an accident" many people on the media started saying that was well planned and not an accident at all. Theories say that the reason it was planned is because it started bringing a lot of attention to the half time shows therefore it brings in more people to watch the Superbowl. Things that are contractual mostly happen in the half time show another example in relating with this is when Beyonce's halftime show in 2016 [195] many people started saying that it was a political statement about the "Black lives matter" movement and this brought a lot of controversy to the Superbowl. Some controversy is wanted to bring more attention to something however it only become a problem when the publicity is unwanted this can have negative effect on someones life if they are tying to live out of the light of fame.
Some of the famous people do not wish to share details about their private lives. For example Emma Watson stated many times that she wishes to keep her personal information about her life private.[196]
I don’t think it’s fair that, all of a sudden, intimate details of their personal life are public as a direct result of me…I wish I could protect them.”
However, some reporters do not respect that request and choose to publicize about her private life.
- That is not the only consequence of over sharing information. One of the most recent stories that made headlines is the Kim Kardashian robbery at gunpoint on the 3rd of October 2016, this was one of the most talked about news at the time. Kim Kardashian decided to stay out of the social media spotlight for a while to protect herself hand her children from future attacks, she also said that she would be a lot more careful of what she posts and shares with everyone. this was a huge wake up call to the whole family about oversharing personal information. [197]
Young Public Figures
[edit | edit source]This is especially a problem when it comes to younger celebrities. The best example that explains this point is how social media reacted to Malia Obama smoking as people thought that it was un-properer for the first daughter to do such action however it should have not even be reported on because even though she was the presidents daughter she is still considered a private citizen. Whatever she chooses to do in her private life even though they disagree with it. [198]
Another example is Macaulay Culkin who was the young boy who acted in Home Alone however, as he grown older some false accusations about him started to spreading that he got into doing some heavy drugs however he only experimented with some drugs but never got addicted or needed to go to rehab. This can corrupt to someones image in the public eye as many people judge others based on how the media presided them. [199]
Moreover, the son of action hero Will Smith and actress Jada Pinkett Smith has been the subject of cruel rumours that he has committed suicide, with a 'video' being uploaded to Facebook which claimed to feature him saying goodbye to his famous parents. [200]The hoax involves getting permission to post on the user's page on the social media site, and it has been spread for weeks now, with people noticing it on their news feed as more and more people click on the fake link. However, this kind of event will cause some seriously negative effects to children both psychologically and mentally.
Photo Scandal of Hong Kong Actor Edison Chen
[edit | edit source]In February 2008, intimate and private photographs of Hong Kong actor Edison Chen with various women, were illegally distributed over the Internet. The scandal shook the Hong Kong entertainment industry and received high-profile media attention locally and around the world. Edison admitted being the author and copyright owner of most of the photographs, and stated that the private photographs had been stolen and published illegally without his consent. He made a public apology, especially to the women involved, and also announced that he would "step away indefinitely" from the Hong Kong entertainment industry.
At this time I am not able to discuss matters related to the case, but I do feel it is my obligation to accept full responsibility and take action to help both the victims and those associated with them to heal their wounds.
In this regard, I plead with everyone to please stop forwarding the images on the Internet. Furthermore, to completely rid the images from your computer...
The news of the scandal received international media attention, notably on the Wall Street Journal [202], the BBC [203], The Guardian [204], and Der Spiegel [205].
- Impact and Consequences:
The scandal has shocked the general public and ignited debate about sexual morality. The blanket coverage of the local press, their reporting style, and the appearance of photographs has also been met with public complaints to television and entertainment licensing authority. This event had a great influence on celebrities and the society, which affected people’s life and seriously violated the privacy rights of the celebrities.
South Korean Stars Commit Suicide After Internet Rumours
[edit | edit source]In South Korea, the online libel cases rose to 10,028 in 2007 from just 3,667 in 2004. Iconic Korean actress Choi Jin Sil, who apparently succumbed to a suicidal impulse provoked by malicious online rumours, and police examining the case concluded that Choi, who told an interviewer that she "dreaded" the Internet, was driven to suicide as a result of the vicious web rumours, which also homed in on her bitter divorce and single- mother status. [206]
- Impact and Consequences:
While online rumours can prove fatal for some celebrities, malicious Internet rumours are being blamed for the rash of celebrity suicides in South Korea that has prompted its government to put forward a controversial new bill to punish derogatory online comments. "Internet space in our country has become the wall of a public toilet," commented Hong Joon Pyo, a senior politician in the South Korean government. For years, whether and how to regulate the Internet has been a hot topic in South Korea, where almost 80 percent of the households have broadband access. Here, most Web portals and online news sites have discussion boards where users can post uncensored, anonymous comments. Some news articles attract hundreds of feedback entries, ranging from thoughtful comments to raving obscenities. [207]
This issue was not only limited to South Korea, it was world wide, Celebrities who faced false accusations or got too much exposure about their lives not only go through depression but they also increase the intake of drugs.
iCloud hack 2014
[edit | edit source]In 2014, there was a hack into the iCloud system which, according to Apple, was “targeted” at celebrities’ accounts.[208] Apple was quick to announce in a statement that the attack didn’t compromise the iCloud system but rather solely the specific accounts of celebrities, however, Kovach (2014) notes that this doesn’t explain how the hackers were able to get into those accounts.[209] This hack therefore affected celebrities only and triggered a wide range of different responses and opinions. The information leaked that got the most attention was the nude photos of female celebrities including Jennifer Lawrence, Kate Upton and Kirsten Dunst.[210] Some of the photos circulating at the time turned out to be fake, presumably created by people jumping on the bandwagon in order to get recognition, but many were confirmed to be real.[211] The photos were spread all over the internet on sites like Imgur, Reddit and 4chan. This led to debates around privacy and whether viewing these photos and seeking them out, despite not having personally leaked them, made an individual complicit in the violation. For example, in this opinion piece from The Guardian, Badham (2014) argues that circulating the photos is “an act of sexual violation.”[212] She also argues that:
- “The need for privacy is not only a sacred place to work out who we are, what we do or how we think; it’s a psychological refuge from overwhelming public dissection necessary for anyone’s mental health, famous or not.”[213]
This argument ties into much of the dissent and outrage from many public figures, including celebrities and journalists. Emma Watson and Lena Dunham were among the female celebrities who spoke out, requesting that people not look at the photos and talking about how it was a violation of privacy.[214][215] Meanwhile, several publications spoke out against the public reaction towards the nude photos, calling for people to stop circulating them and stop using crude language to describe the breach of privacy. [216]
In the aftermath, Apple was keen to assure their users that their privacy was not in jeopardy. The BBC reported that Apple had added an extra step of log-in verification[217], while Forbes encouraged users not to delete their iCloud accounts and remove their information, but rather to up their security measures such as using more complex passwords.[218]
Non-celebrity hacks
[edit | edit source]Ashley Madison data breach
[edit | edit source]There was an attack on 15 July 2015, they threatened to reveal the identities of Ashley Madison's users.[219] This site was basically for those who were married or in relationships to cheat and have a safe place to contact one another without their significant others finding out about them. This was one of the most recent attacks of private citizens' privacy. Although many cheated the hackers and stood by them saying that cheating was wrong so sharing their personal information was not much of an issue as it seemed justified with many people. This resulted in many people to lose their families, jobs and relationships.[220]
Yahoo! hacks
[edit | edit source]Yahoo! is a technology company whose services include Yahoo! Search, Yahoo! Mail, Yahoo! Answers and many more. It also owns Flikr and Tumblr. Yahoo! users are able to access all Yahoo! services as well as to link with Tumblr and Flickr accounts. This means that when a user’s security is compromised, the hacker has access to the information provided by the user across several services, which may include bank details.
When Yahoo! was hacked in 2013, one billion accounts were accessed by a government hacking programme, according to several news sources. [221][222] Not much information has been provided from Yahoo! about who hacked them and why. [223] However, we do know that the hackers were able to access “names, email addresses, telephone numbers, dates of birth, hashed passwords.” [224] There was also a hack in 2014 by the National Security Agency (NSA) which the company allowed to happen. [225] The NSA used a similar programme to Prism, the surveillance programme revealed by Edward Snowdon and they also requested that Yahoo! search for a certain “set of characters” in the emails going through their servers. [226] According to Woolf (2016), this is the only known time that a company has agreed to letting a spy agency access their information. [227] After investigations of these subsequent hacks, the head lawyer of Yahoo! has resigned and their CEO has lost their bonus.[228]
Ess (2009) talks about breaches of privacy in relation to government intervention. He argues that "Governments may be (somewhat ironically) the worst culprits" for hacking private information.[229] Weber (2012) argues that “the most important objective of privacy is the prevention of improper use of personal information” [230] Therefore, these hacks carried out by government agencies must justify their surveillance programmes, however, we have yet to have an explanation of what they were looking for in Yahoo!. Conversely, so long as the agencies are managing that information securely and appropriately, the argument can be made that their intervention is justified.
PlayStation Network Hack
[edit | edit source]
In the early months of 2011, Sony's PlayStation Network went offline, and after seven days[231] they went on to admit that it was the direct result of a hacking. At the time of the hack Sony had an estimated 70 million users[232] registered under the network, resulting in the possible breach in security of the personal information of millions. Sony explained that in the hack, user details were potentially left exposed. This included names, date of births, addresses, as well as card details due to the network being used for the purchasing and distribution of games, music, films and software.
Due to the delay between the hacking occurring and Sony admitting that personal details were potentially compromised, this left an expanse of time where users were unaware of the breach in their privacy and were left exposed to the consequences. While they claimed there was no evidence of card details being stolen, Sony warned: "Out of an abundance of caution, we are advising you that your credit card number (excluding security code) and expiration date may have been obtained."[233] The hacking was considered one of the largest security breaches in history, as well as being one of the biggest intrusions within a store of credits cards, as only sites such as Amazon, PayPal and iTunes are known to store more.[233]
Privacy in Relation to Living in a Connected World
[edit | edit source]The Online/Real-Life Divide
[edit | edit source]As discussed in the full chapter of the same title, there is a new understanding of the way people present themselves online because of the rapidly changing and growing technological culture. But how well are we coping with the ability to remain private with these constant changes?
At first glance there would be an obvious divide between the online and real life divide, but with the rise of social networks and the technology to be on the internet at any time of the day and almost anywhere, the boundaries of online and offline privacy are starting to be minimised and potentially blurred. The privacy that some people strive to keep online sometimes isn’t as private as it should be because the privacy settings on some social networking sites are incredibly relaxed, and still reveal quite a lot about a person, whether via another account or not. This then leads to a question of security, whether people are online or offline.
Because a lot of people are able to access the internet and their preferred social networking sites via apps on their phones, their locations can constantly be pinged and their movements tracked, and no matter how private they keep their original pages a lot can still be seen by people who are essentially strangers. In real life, it is much easier to keep privacy especially if people are offline – it is much like living in a house, if privacy is truly wanted, it is just a case of locking the doors and closing the curtains. Online, this privacy is much harder to achieve as despite putting the privacy settings on to what could be considered as the optimum, for a lot of social media networks a lot of personal data can still be found online, and what is more shocking is that there are sites where information can be found which was gathered offline.
One of these sites is 192.com [[39]] where the electoral roll of people in the UK is stored and people are able to search and find anyone of interest to them. Before the internet, people had to register to vote by post (something which is still an option today)[[40]] but with the ease of applying online, anyone can sign-up and keep their addresses up to date with no problems whatsoever. As this service makes it easier to check the immigration statuses and movement of people throughout the country, it also means that the information uploaded can be searched for by any Tom, Dick or Harry on Google looking for anyone they want. As a funny pastime for a lot of primary school children, searching for each other or for family members was fun and not easy and would start a lot of laughs and giggles because of all of the random pictures that would appear which were clearly unrelated... little did those children know how quickly the change in technology would be and how easy it is for them (now as adults) to do the same search, but find more than they realised was available. Most of the information online is something that some people willingly share, but others who strive for the utmost privacy – online and offline – will be very surprised at the things they can find, especially when there are plenty of loopholes. For example on the same 192.com [[41]] website, typing in the name of a certain person might give search results of a few people and just a green tick next to the ‘home address’ box which, when clicked would lead to a sign in/ sign up page for further information, but type in said same name on Google, and clicking on the link to the same site will give you the rough address and list of other/ former occupants at the address too. If people are striving for privacy online and offline, here is a number one way to ensure that it is already lost to a certain degree, and without their permission.
Another way in which privacy between the online and real-life divide is challenged is the ease of access to the internet itself, and through the different platforms it is available. For some people, they prefer gaming and having more anonymous profiles which only their friends in real life can be friends with, though are able to connect with other people online and playing the same game, and for the rest, they may choose every available platform for social networks. The privacy is challenged here as a lot of people can also be at home when they are online which can mean that they can potentially be tracked through their activity too. Slightly linking to the surveillance section above – no form of the internet is not in some way being watched, especially via social networking sites which are free to sign up for. ‘These services are free because they are selling access to you’ [234], which means that the advertisements that appear are specifically tailored because of the search history or general activity related to anything shared, it also means that every conversation is monitored and that privacy is almost non-existent. This is different from the real-life divide as not everything will be monitored, and not all of the adverts passed will be tailored, but would rather just pass unnoticed - which is quite a feat considering that the average person is exposed to 3,000 to 20,000 adverts a day [235]. There is more freedom in the real-life rather than online, as there is also the possibility of being whoever you want to be, and either be noticed or not as privacy in reality (and being offline) means that there are infinitely less worries about someone hacking any devices used for socialising, or someone making sure that you are not some sort of terrorist spy.
Privacy in relation to the online/ real-life divide is by far and large something that is slowly vanishing with the technological advances modern societies are developing, which means that before long, there will be no privacy in the real life either, rather than just a false sense of privacy online.
Technology as an Extension of Self
[edit | edit source]As previously discussed in the chapter on Technology as an Extension of Self, users of modern day technology and social media are willingly and unwillingly giving out personal information and details more and more. Those with accounts on common social media sites such as Snapchat, Instagram, Facebook, Twitter and Youtube are becoming increasingly invested, and private lives and online lives are being further merged the more time is spent online.
Youtube
By far the most prevalent example of the blurring boundaries between private and online personality is the recent inflation of Youtube Vloggers. Arguably the most popular type of vlog (short for video blog) that is uploaded to Youtube is the day-in-the-life type montage, that can showcase the creator doing anything from making breakfast to snowboarding through New York City. This moving image, diary-entry style of content differs considerably from Facebook statuses or Instagram posts, the videos are typically around 5-15 minutes long, the most popular getting millions of views and provide a real insight into what for most people would be seen as a private day in the life.

Casey Neistat found filmmaking fame through the vlogs he uploaded to the site every day for almost 2 years, which earned him over 5 million subscribers and billions of views. He documented his adrenaline-filled lifestyle in New York with his family and friends and showcased his apartment, workspace, holidays, meetings and more to his growing audience online. An increasing number of viewers of his videos began turning up outside his office for a chance to be in the “vlog” as his following grew. Neistat stopped his daily videos in November 2016 and now focuses on uploading short films more sporadically.
Youtube stars and celebrity couple Zoe Sugg and Alfie Deyes, known online as “Zoella” and “PointlessBlog”, also vlog their daily lives. Both started on the platform over 5 years ago and have accumulated over 15 million subscribers between them. The majority of their vlogs take place in the home they share in Brighton, and although care is taken to not show the front of the house or the surrounding streets, often is the case, like with Neistat, that fans of their vlogs do turn up uninvited. In 2015 the couple took to Twitter to voice their complaints about a lack of privacy after the location of their house was revealed through their videos:
Although the majority of fans agreed with the pair, a lot hit back at them for not realising the price that comes with fame. Although not conventional celebrities, the amount of personal details Youtube creators intentionally and unintentionally upload online, particularly in the form of day-in-the-life videos, blurs the line between a private life and a public one excessively. Sugg often gets very personal in her videos, speaking out about her issues with anxiety and expressing how she often finds the lack of privacy and newfound exposure overwhelming.
Persistent Connectivity and the Fear of Missing Out
[edit | edit source]Both the concept of the Fear of Missing Out and privacy issues are described by Nancy Baym as “cultural anxieties”[236] caused by new media. Most of the popular understandings of privacy are related to the concept of isolation, or the ability to feel alone and cut off from others.[237] Missing out has direct links to privacy. Having strong privacy settings reinforces these ideas and feelings of solitude, and the subsequent concept of the fear of missing out on things. There is a sense of mass panic on not having a “window to the world”[238] through social media platforms, and this window shrinks even further when information becomes increasingly private. There is a sense of dissatisfaction when we aren’t allowed access to a certain page or account due to the privacy settings. Friends and followers influence others behaviour online, the more information that is open to each other, the more the fear of missing out is heightened. Michael Hogan Ph.D. notes that a decrease in personal privacy is a fundamental driver of the negative consequences of FoMO.
In an age where Facebook is the platform where the majority of planning, organisation and discussion for projects, events and clubs takes place, barriers of privacy have to be broken down in order to contribute. Often is the case where accounts will friend and follow people not necessarily known to them personally, in order to be invited into something, or joined onto a group chat. It is the simple logistics of the website, yet friending someone to communicate with them is also opening up to them everything that account posts, and all the information, photos and details already on the profile. This is particularly prevalent in students, where University project groups, sports clubs and societies often require them to be more relaxed in adding people on Facebook to stay in the loop. Focus group discussions with young people show that they have an increasing dislike for Facebook due to issues of people sharing excessively, yet keep using it because participation is an important part of overall teenage socializing.
The effects of oversharing on privacy controls
The 2008 word of the year according to Webster’s World Dictionary was “overshare”.[239] Too much self-disclosure is becoming an increasing problem in social media in the modern day, and the nature of it also has a direct effect on privacy controls. Sue Scheff explains that posting on social media “excessively” can increase the possibility for people, especially teenagers, to be negligent with their privacy controls, even if it is accidental[240]. Oversharing is more effective the larger an audience an account has, and privacy settings can determine the difference between the size of followings. Jaron Lanier suggests that users should never "post anonymously unless you really might be in danger", in order to stay as a "person" online and not a "source of fragments to be exploited by others"[241]. The more advanced technology becomes, the more its users become less private.
“if we became digitally abstinent tomorrow, the vast amounts of personal information already available would render us vulnerable for decades to come[242]
Out of the most popular social media groups; Facebook, Instagram, Snapchat and Twitter, Twitter is the platform in which user’s privacy controls are at their most relaxed. The data that Twitter stores from individual accounts is fairly comprehensive, but while Facebook profiles tend to have the most private settings enabled, Twitter users are much more likely to have a public account . A Pew Research Centre Study on teenagers and their privacy controls on social media concluded that whilst 60% of teen Facebook users have private profiles, 64% have public twitter pages. The number of teens using Twitter has also increased by 8% since 2011. Twitter is a platform in which information spreads the fastest and most easily, especially when privacy settings are at their most lax, due to its Retweet function. Retweeting allows someone else’s tweet to be shown on your account to all of your own followers, and only works if the original account who tweeted it, doesn’t have their account on private. Retweets are described on Twitter’s Help Centre as a re-posting feature that “helps you and others quickly share that Tweet with all of your followers”[243]. The retweet feature is not available for accounts that are protected.
“If you see the lock icon next to a user's name on their profile page or on their Tweets, their Tweets are protected and you will not be able to Retweet their content”[244]
In terms of | virality, a single tweet can rack up thousands of interactions in the space of a few hours if it’s been retweeted enough, but it wouldn’t be possible for an account with “protected tweets” to achieve as much recognition. Because protected accounts have chosen not to share their Tweets publicly, their Tweets cannot be Retweeted by anyone else. A non-private page allows further interaction and involvement with others on the site, whether this be with real-life friends or not. A protected account is one that can heighten feelings of FoMO more so than a public one.
Digital Labour on Social Media Platforms
[edit | edit source]Where would one be if one did not have access to social media? This question tends to be asked by many people nowadays as so many individuals rely on social media and the Internet so heavily. Social media plays a huge part on the majority of people's lives. The Internet as a whole, has become thoroughly embedded and routinized in the societies where it is most likely to be used, according to Frank Webster. This includes societies and environments such as workplaces and educational facilities whereby the Internet is almost second nature to its users. But the reality surrounding how this digital world is created is one in which seems to go unnoticed. Technologies altogether have played a huge part in the restructuring of capitalism since as far back as the 1970s. One would say the world of technology allows rapid communication which is required for organising international markets and value chains. Nick Dyer-Witheford therefore describes the value chain as “the dirty secret of the digital revolution”. The clean, immaculate and advanced surface of modern computer products hides the dirty reality of their production process. Concepts such as “digital sublime” [245] or “technological sublime” [246] suggest that certain myths and utopian ideals are attached to media and communication technologies. Maxwell and Miller argue that this has as a consequence that the “way technology is experienced in daily life is far removed from the physical work and material resources that go into it” [247].
To elaborate on the point made by Frank Webster, the Internet has not replaced older forms of media completely. He believes that people's information and communication environments have become increasingly more individualised. Throughout this Wikibook exercise, Dr Thomas Allmer posed a question which would make one "consider how do the constraints and emancipatory potentials of new media look like and to what extent can digital and social media strengthen the idea of the communication and network commons and a commons based information society? [248].
New media studies demonstrate a variety of ways in which a mass society has been transformed into a new and emergent environment of networks, dynamics, roles and relations. As Marisol Sandoval states "Conceptualizing digital labour only as mental and immaterial labour misrepresents the character of ICTs and digital technologies as it tends to downplay the physical and manual labour that goes into them" [249]. Sandoval's statement acknowledges the fact that in order for us, as social media and internet users, to be able to maximise the use and make the most of this digital world one is exposed to, one must realise that the process of this does not just happen without hard work. Dyer-Witheford states that the social factory is a "factory without walls" [250] as capital extends exploitation to networks, it also automates the entire social factory of human society. These developments within the social factory cause a restructure within the concept of traditional working-class. Dyer-Witheford proceeds to discuss that corporate social media platforms are social factories having extended logics of the factory to the Internet and have subsumed society and social activities into the capitalist process of the productions. Technological giants such as Facebook, Appleand Googlehave changed exploitative aspects from the workplace into cyberspace. Despite having said this, those who use social media belong to the social factory that work for free in their own time by fulfilling social and communicative needs. The entirety of anything regarding social life is subsumed under capital on the Internet. Despite the fact that productive forces of social media are shaped by value creation in capitalist societies, the continuous development and progression of productive forces signify the opportunities of the commons within different relations of production.
How does this relate to privacy?
How does social labour relate to anything privacy related one may ask? To conclude and address this question, it must be said that the client-server environment which is taking over the Internet is built as a control and a piece of surveillance technology (which will be addressed elsewhere within this Wikibook) which is submerged in the capitalist relations of production. This specific technology could increase the risks and dangers of people who may not know where their data and information is stored and what is happening with it. It runs the risk of strengthening the sense of 'uncontrollability' of personal data and files. This possible danger is reflected when social media users admit their fears of social networking sites.
Filter Bubbles and the Flow of Information
[edit | edit source]
Definition
So what is a filter bubble? According to Techopedia, "a filter bubble is the intellectual isolation that can occur when websites make use of algorithms to selectively assume the information a user would want to see, and then give information to the user according to this assumption". So effectively, information is extracted from the user in order to present the most 'relevant' information for the user. The algorithms tailor what is shown to the user online and consequently decide on what is hidden.
The image on the left is a graphic which has been created to demonstrate the concept of a filter bubble. Although a filter bubble is not truly a physical object, by creating a visual way of depicting how a filter bubble functions the concept should (ideally) become clearer. The inner circle (with the yellow outline) represents the filter bubble. The circles inside of this demonstrate the information which gets filtered into the user's view. The white arrows pointing towards the centre represent the algorithms of different search engines, sites and platforms which control what is filtered through to the bubble, and in turn, what is kept out. The other coloured circles outside of the bubble are sites and information which the algorithms reject. This may be because they are assumed to be of no interest to the user or they present new, different or opposing concepts to that of the user's common patterns. This can stifle knowledge and form the metaphorical concept of tunnel vision as the user does not receive a democratic perspective.
This YouTube video entitled The Filter Bubble: How the hidden web is shaping lives provides insightful information on the definition of filter bubbles. It also draws upon the effect it has on the flow of information which is presented to the user. The next section discusses how this affects online privacy. More information on filter bubbles and the flow of information can be accessed in the chapter Filter Bubbles and the Flow of Information in this WikiBook.
How this affects online privacy
So, why is the relationship between filter bubbles and privacy important to consider? Zizi Papacharissi evaluates the meaning of privacy using terms such as: ownership, personal, domestic, unofficial and (structured around the) self. [251] But is this an illusion online? Filter bubbles extract information from the user which cancels out/changes the meaning of these terms. Online privacy in relation to filter bubbles and the flow of information remains "structured around the self" but in a different way to that which Papacharissi intends. This is because it is no longer personal, the user loses control over what is structured for them. Algorithms in the form of filter bubbles structure what is presented for the user and simultaneously, what is hidden from the user. The algorithms structure information around the user's information.
Amongst other subjects, Google is discussed in the afore mentioned clip (The Filter Bubble: How the hidden web is shaping lives). The speaker, Eli Pariser, highlights that Google acts not only as a search engine but as a platform to extract information from the consumer. This information is used to tailor searches to make the results more "suited" to the individual. If people X, Y and Z all searched for the same thing, the results would be different. The algorithms of the filter bubbles display what the user is most likely to want to see. User interest is based on click behaviour, browsing and search history and location [252]. This function assists and helps the user by breaching privacy as the user does not have a choice against sharing what they search, browse etc. Does this demean the user's control? This is the first example of how privacy relates to filter bubbles and the flow of information.
A primary factor in the relationship between privacy and filter bubbles is the distortion problem [253]. Due to filter bubbles deciding what is 'best' or 'most suitable', the user becomes unaware of how they are viewing the world and in turn what they are missing. Thus their perception is distorted. In the opening definition of filter bubbles the stress on relevance is stated. The matter of relevance is utilised constantly online. For example, Netflix advertises and suggests what you might be interested in watching next. Filter bubbles use information from the individual (and others who follow similar viewing patterns) to determine what the user is most likely to want watch next. The bonus of this is that the user has direct access to more of what they have proven to enjoy. However, this stops the user from seeing everything else. So filter bubbles may help the user to continue clicking on the same kind of media, hence, encouraging the 'always on' culture (see glossary). For a democratic view, the user must be open to a multitude of different opinions and information. Although the user may oppose this information, by viewing new and different ideas they can build a stronger view of what they do believe as they learn more about everything in general.
Essentially, the tug of war between filter bubbles and privacy comes down to a matter of control. If technology truly is an extension of self, then the user should maintain control over the technology [254]. The user should at least be aware of what information is being used and how it is being used. Filter bubbles were created for user benefits but they can spiral out of control since, after all, they are simply algorithms. They have no ethics or human thought processes. However a human did create them. And the sites which own them can use them how they please. If websites can use filter bubbles to control what the user has access to, then companies could easily manipulate this information for commercialisation.
Summary: Conclusion and Possible Solutions
The works of Papacharrissi and Lanier have been drawn upon in this article however there are many other theorists who recognise the complicated concept of online privacy.
“In modern society, privacy is inherently linked to surveillance.”—Christian Fuchs, Social Media: A Critical Introduction
As Fuchs highlights, there will never be 100% guaranteed privacy online. Data trails can and will be followed and used for reasons which may not affect the user or may alter what they see. So there may not be a distinct solution but arguably because this is not a distinct 'problem' - it is more of a situation which has appeared within modern society.
After much debate through doing this work, two possible conclusions have arisen:
1. Creating transparency.
2. Being able to turn filter bubbles on and off.
By having a transparent relationship between websites and the user then it should be clear what results are personalised and on what basis. If the user is aware of what private information is being used (and realises that it is not as private as they possibly first assumed) then in the future they can take care with what they search, browse and click on. Secondly, by having the ability to turn the filter bubbles on and off then user can regain control. The user could search with the filter bubbles off in order to receive a neutral response and then adjust this at their leisure. More work and research on filter bubbles and the flow of information could allow development to further secure online privacy in the future.
- DISCLAIMER - the above 'possible conclusions' have not been academically proven and are simply proposed theories.
How the different Generations are dealing with her Privacy on Social Media
[edit | edit source]This chapter based on a study, published by the 23rd International Academic Conference in Venice. The sample of the study consisted of 736 participants. This participants were selected through stratified random sampling from the research population determined as "Individuals who live in the province center of Konya and use any of the social media tools"
The behavior of the generations on the social media platforms is quite different, also their meanings about which stuff is to private to share there.
The generations are based on the range of birth dates and the classification by Greg Hammill (Hammill, 2005)
| Generation | year of birth | age range |
|---|---|---|
| Baby Boomers | 1946 - 1964 | 53 - 71 |
| Generation X | 1965 - 1980 | 37 - 52 |
| Generation Y | 1981 - 2000 | 17 - 36 |
At first we are looking at the behavior with their "body privacy"
Question 1: I share my photos in a swimsuit taken on the beach.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 71,9 % | 18,2 % | 9,9 % | 0,0 % | 0,0 % |
| Generation X | 77,3 % | 15,0 % | 7,3 % | 0,5 % | 0,0 % |
| Generation Y | 68,8 % | 13,9 % | 12,2 % | 4,1 % | 1,3 % |
Here you can see that 31,5 % of the Generation Y is posting such photos while 22,8% of the older Generation X and 28,1 % of the Baby Boomers are doing this. Based on this you can not say that the younger generations are sharing these photos more frequently than the older generations. But you can see that the number of people who would never sharing these is in the Generation X on the lowest level. The Generation X takes more care about there privacy here than about there self presentation, which is a difference to Generation Y.
Question 2: I share my home and it's rooms (including the spaces such as the bathroom, bedroom, etc.) together with the furniture.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 75,2 % | 19,8 % | 5,0 % | 0,0 % | 0,0 % |
| Generation X | 77,3 % | 16,8 % | 5,5 % | 0,5 % | 0,0 % |
| Generation Y | 72,7 % | 16,7 % | 8,6 % | 1,8 % | 0,3 % |
Here you can see that there is no significant difference observed by the different generations who answered, that the would never share their home and it's rooms together. 72,2% of the Baby Boomers, 77,§% of the Generation X and 72,7% of the Generation Y never would do this. It seems like protecting their home is something all generations consider as important. Maybe this is because they want to be safe in their offline world and do not bring there online life into this.
Question 3: I share my activities about the members of my family in a controlled way.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 10,7 % | 10,7 % | 21,5 % | 40,5 % | 16,5 % |
| Generation X | 4,1 % | 10,0 % | 21,8 % | 44,5 % | 19,5 % |
| Generation Y | 17,2 % | 14,2 % | 22,5 % | 28,1 % | 18,0 % |
Based on this answers you can see significant differences. While 57% of the Baby Boomers and 64% of the Generation X answered this this question "usually" ans "always", only 46,1% of the generation ticked these answers. The reason can be that the Generation Y is quite young and many of them are single and do not have children they use to protect. The Baby Boomers are mainly connected with family members and want to communicate with them, so the are sharing family activities to other family members. The Generation X just started to have children and want to share how happy they are and also share the pictures with other family members and friends.
Question 4: I wear and photograph the clothes I like and present them to my friends' taste.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 62,2 % | 19,0 % | 19,0 % | 0,8 % | 0,0 % |
| Generation X | 48,6 % | 33,6 % | 11,4 % | 4,5 % | 1,8 % |
| Generation Y | 33,9 % | 26,6 % | 24,1 % | 12,2 % | 3,3 % |
You cam see that 66,2% of the Generation Y and 51,3% of the Generation X are sharing these photographs, only 38,8% of the Baby Boomers are doing this. The number of people sharing these pictures are rising withe the younger generations. The baby Boomers are defined as a contented and less consuming Generation. The are grew up after the Second World War and are not that interested in fashion aspects as the Generation X, which were the first who are shopped in shopping centers. For the Generation Y the clothes and there brands represents who they are. The clothes are a part of the self-representation as in Rettenbergs "Seeing Ourselves Trough Technologie". It is really important for the Generation Y to be see from others in a controlled way.
Question 5: I share/can share the photos of private moments I have with my spouse or beloved.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 52,1 % | 21,5 % | 21,5 % | 5,0 % | 0,0 % |
| Generation X | 49,5 % | 23,2 % | 14,5 % | 8,2 % | 4,5 % |
| Generation Y | 40,0 | 23,5 % | 17,0 % | 14,4 % | 5,1 % |
You also can see in this table significant differences between the generation. The willingness to share the "Private Relationship Status" is increases withe the younger generations. 48 % of the Baby Boomer, 50,4% of the Generation X and 60% of the Generation Y are sharing private moments with their beloved persons. The Generation Y grew up with personal computers and smartphones. It is a part of their private practice to share personal moments. With that they are sharing their sex-orientation, which is maybe to private for the older generations. Today in the most societies it is allowed and OK to be homosexual which can be a factor that more people in the Generation Y are sharing this too. For the Baby Boomers and the Generation X this was not accepted by the society and a big taboo.
Question 6: I follow my friends lives on social media.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 7,4 % | 13,2 % | 33,1 % | 36,4 % | 9,9 % |
| Generation X | 4,5 % | 20,9 % | 38,2 % | 31,4 % | 5,0 % |
| Generation Y | 6,3 % | 18,2 % | 31,9 % | 33,2 % | 10,4 % |
With this table you can see that in all generations a very low number of persons do not follow their friends on social media. There is a conflict to the own handling of their private sphere and their urge to look into the private sphere of others. The number of people who are willing to share private moments is much higher than the number of people who want to see the private moments of others (as you can see when you compare table 5 and 6).
Question 7: Views on religion.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 37,2 % | 17,4 % | 24,8 % | 16,5 % | 4,1 % |
| Generation X | 28,2 % | 25,9 % | 24,1 % | 14,5 % | 7,3 % |
| Generation Y | 26,1 % | 28,6 % | 25,3 % | 12,9 % | 7,1 % |
As you can see in table 7 there are no significant differences between the generation, but you can say that the Baby Boomers are the generation with the highest number of people who would never share their views on religion with 37,2% the Generation nearest to this view is Generation X with 28,2% followed by Generation Y with 26,1%. Nevertheless you can say that the generations are acting very similar in this topic. This can be so because we are free to practice our religion in the western world, it even is protecting by laws.
Question 8: Agenda-political views.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 33,1 % | 20,7 % | 24,8 % | 19,0 % | 2,5 % |
| Generation X | 30,9 % | 25,9 % | 18,6 % | 16,8 % | 7,7 % |
| Generation Y | 27,1 % | 25,6 % | 26,1 % | 16,5 % | 4,8 % |
Also in table 8 are no significant differences, but you can say that with the younger generations the people who would never share their agenda-political views decreases. 33,1% of the Baby Boomers, 30,9% of the Generation X and 27,1% of the Generation Y would never share their agenda-political views. Today it is become an issue to discuss with others to form his own opinion and to manage the flood of information who is out there. But religion and the political views are belong to the private sphere as well. political elections in the western world are anonymous to save the private sphere of the electorate, so that nobody can judge by his opinion.
Question 9: Sexual preference.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 92,6 % | 4,1 % | 3,3 % | 0,0 % | 0,0 % |
| Generation X | 92,7 % | 3,6 % | 1,4 % | 1,4 % | 0,9 % |
| Generation Y | 84,6 % | 7,8 % | 5,8 % | 0,0 % | 1,7 % |
With this table you can see that there is a difference between the two older generations to the Generation Y. 92,6% of the Baby Boomers, 92,7% of the Generation X and 84,6% of the Generation Y answered that they never would share their sexual preference.
The own sexuality is one of the most private issues of the private sphere. In the German law there are three spheres to save the general right of personality.
the Individual Sphere which includes: the right to informational self-determination, the Right to Re-socialization and the right to knowledge of one's ancestry.
The second deepest sphere is the Private Sphere which includes: the protection of private life as well as life in the home and in the family circle.
The last and deepest sphere is the Intimate Sphere as well as the most Intimate Privacy, this sphere encompasses the protection of the inner world of thoughts and feelings as well as the protection of the sexual sphere.
Based on the table for question 9 you can say that the youngest Generation Y is breaking the line of their own intimate sphere by their own. While the Generation X is careful about what they are sharing and they are aware of the consequences this can have for their professional lives.
The behaviors of the generations are similar in term of spaces of the home, relationships among individuals and religious ans political views. There are differences in terms of certain parts of the body, family, clothing, private relationship status and sexual preferences. The Generation Y is here the first generation who grew up with personal computers and smartphones. In some cases they are acting more freely with their private sphere than the older generations. The question is, will are there more differences with the next generation? The Generation Z which members are born directly after the Generation Y and who are the second generation who will grown up in a digital world.
Glossary
[edit | edit source]Please put the terms in alphabetical order when adding. |
- Always-on: A term relating to the notion of persistent connectivity to a shared global network.
- Authentication: Where an entity is proved to be valid or a user provides information to prove their identity.
- Collective Intelligence: A term to describe the sharing of knowledge and information in a collaborative for.
- Data Mining: The practice of sorting through data to identify patterns and establish relationships, in relation to online privacy, data mining collects data from users of social media to examine trends and target adverts.
- Digital Age: Also known as the information age that is considered to have started in 1970 with the development of technology such as television and computers.
- Encrypted Messages: Relating to Facebook's secret messaging service, encrypted messages allow end-to-end conversations to occur where only the communicating users can receive the messages.
- Filter Bubbles: The use of algorithms to display information which appeals to the specific user's interests.
- Fear of Missing Out (FoMO): A form of anxiety aroused by the fact that an exciting or interesting event may currently be happening from posts on social media.
- Global Village: Coined by Marshall McLuhan, a social organisation when society can easily transfer and share information as a collective.
- Hacking: Forced access to a closed, private system or device.
- Identity theft: The deliberate use of someone else's identity, usually as a method to gain a financial advantage or obtain credit and other benefits in the other person's name.
- Internet cookies: Small pieces of information in text format that are downloaded to your computer when you visit many Web sites. The cookie may come from the Web site itself or from the providers of the advertising banners or other graphics that make up a Web page.
- Keylogging: The act of tracking what the user is typing.
- Leaks: The public release and circulation of private information against the owner of the information’s will.
- Margin of error: A statistic expressing the amount of random sampling error in a survey's results. It asserts a likelihood (not a certainty) that the result from a sample is close to the number one would get if the whole population had been queried.
- New Media: The means of mass communication using digital technologies such as the Internet and social media platforms.
- Oversharing: The act of revealing too much personal information about oneself online.
- Privacy Policy: A privacy policy is that which states the ways a company gathers, uses, discloses, and manages a customer or client's data. It fulfills a legal requirement to protect a customer or client's privacy.
- Private Sphere: Often defined in opposition or parallel to the public sphere. The private sphere is a section of societal life in which an individual has a degree of seclusion from the public. The concept has become blurred since the advent of social networking as "private messaging" communications are often stored on databases.
- Public Sphere: Often defined in opposition or parallel to the Private Sphere. The Public Sphere is the section of societal life where private individuals come together to form a public entity. The ideology of the Public Sphere is that private people come together to discuss matters involving the greater good of the public.
- Retweet: A function on the social media platform Twitter that allows users to repost or forward a Tweet.
- Spyware: Software designed to give unauthorised access to a system.
- Vlog: A blog in which the postings are primarily in video form.
- Web 2.0: A development of the internet that focuses on user-generated content.
References
[edit | edit source]- ↑ Bush, Vavennar (1967). “Memex Revisited”. In Chun and Fisher (eds.) (2016) New Media, Old Media: a history and theory reader (2nd ed.). London: Routledge, p. 85-96
- ↑ Bush, Vannevar (July 1945)."As We May Think".The Atlantic.
- ↑ Bush, Vavennar (1967).“Memex Revisited”. In Chun and Fisher (eds.) (2016) New Media, Old Media: a history and theory reader (2nd ed.). London: Routledge, p. 91
- ↑ Smith, Scott S. “Math Whiz Ada Lovelace Presaged Our Digital Age Evolve: She wrote the first computer program in 1834 “. Investor's Business Daily. March 18, 2015, A4
- ↑ Gerard O'Regan,” Introduction to the History of Computing: A Computing History Primer”. Springer. 2016. P.55-72
- ↑ Mandiberg, Michael. The Social Media Reader, edited by Michael Mandiberg, NYU Press, 2012.
- ↑ Mandiberg, Michael. The Social Media Reader, edited by Michael Mandiberg, NYU Press, 2012.
- ↑ Marshall T. Poe “A history of communications : media and society from the evolution of speech to the Internet “ Poe, Marshall.2011
- ↑ Gaines, Elliot “Media literacy and semiotics” Elliot Gaines. Elliot Gaines. 2010
- ↑ Johansson, B.;Odén, T “Struggling for the Upper Hand: News sources and crisis communication in a digital media environment “ In: Journalism Studies. (Journalism Studies, In Press, 4 February 2017, :1-18)
- ↑ Pike, Deidre M. „Media literacy : seeking honesty, independence, and productivity in today's mass messages” published by International Debate Educational Association. 20.11.2013. p. 34-50
- ↑ Dewar, James A. (1998). "The information age and the printing press: looking backward to see ahead". RAND Corporation.
- ↑ Cherchi Usai, Paolo. “The death of cinema: history, cultural memory and the digital dark age” Paolo Cherchi Usai. 2001.
- ↑ Bill Gates, et.al., The Road Ahead, Penguin. 1996.
- ↑ Grossmann, Lev “Mark Zuckerberg and Facebook's Plan to Wire the World”In: TIME. December 15 issue.
- ↑ http://jilltxt.net/books/Seeing-Ourselves-Through-Technology-full-book.pdf
- ↑ Mandiberg, Michael. The Social Media Reader, edited by Michael Mandiberg, NYU Press, 2012.
- ↑ Lovink, Geert. "Networks Without a Cause: a Critique of Social Media". Polity Press, 2011.
- ↑ Lovink, Geert. "Networks Without a Cause: a Critique of Social Media". Polity Press, 2011.
- ↑ Boyd, Danah and Ellison, Nicole. (2007). "Social Network Sites: Definition, History, and Scholarship." Journal of Computer-Mediated Communication, 13: 210–23.
- ↑ Boyd, Danah and Ellison, Nicole. (2007). "Social Network Sites: Definition, History, and Scholarship." Journal of Computer-Mediated Communication, 13: 210–23.
- ↑ Boyd, Danah and Ellison, Nicole. (2007). "Social Network Sites: Definition, History, and Scholarship." Journal of Computer-Mediated Communication, 13: 210–23.
- ↑ Boyd, Danah and Ellison, Nicole. (2007). "Social Network Sites: Definition, History, and Scholarship." Journal of Computer-Mediated Communication, 13: 210–23.
- ↑ Lovink, Geert. "Networks Without a Cause: a Critique of Social Media". Polity Press, 2011. pg 41.
- ↑ Boyd, Danah and Ellison, Nicole. (2007). "Social Network Sites: Definition, History, and Scholarship." Journal of Computer-Mediated Communication, 13: 210–23.
- ↑ Lovink, Geert. "Networks Without a Cause: a Critique of Social Media". Polity Press, 2011. pg 41.
- ↑ Lovink, Geert. "Networks Without a Cause: a Critique of Social Media". Polity Press, 2011. pg 39.
- ↑ Lovink, Geert. "Networks Without a Cause: a Critique of Social Media". Polity Press, 2011. pg 41.
- ↑ Good, Katie. (2012) "From Scrapbook to Facebook: a History of Personal Media Assemblage and Archives". New Media and Society, 15:4, pg 557 - 573.
- ↑ Salomon, Danielle. (2013). "Moving on from Facebook: Using Instagram to connect with undergraduates and engage in teaching and learning". College and Research Library News. 74:8. 408 - 412.
- ↑ "FAQ." FAQ • Instagram. N.p., 2017. Web. 01 Mar. 2017
- ↑ Hochman, Nadav. (2013) "Zooming into an Instagram City: Reading the local through social media". First Monday. 18:7.
- ↑ "Snap Inc." Snap Inc. N.p., n.d. Web. 02 Mar. 2017.
- ↑ "Snap Inc." Snap Inc. N.p., n.d. Web. 02 Mar. 2017.
- ↑ Velten, Justin & Arif, Rauf. (2016). "The Influence of Snapchat on Interpersonal Relationship Development and Human Connection". The Journal of Social Media in Society. 5:2.
- ↑ Velten, Justin & Arif, Rauf. (2016). "The Influence of Snapchat on Interpersonal Relationship Development and Human Connection". The Journal of Social Media in Society. 5:2.
- ↑ Lanier, Jaron. (2011) "You Are Not A Gadget: A Manifesto"
- ↑ https://www.youtube.com/embed/qpZbu7J7UL4
- ↑ Leahy, Matthew Michael & Schultze, Ulrike. "The Avatar-Self Relationship: Enacting Presence in Second Life". Association for Information Systems. 2009. 2 - 15.
- ↑ Joinson, Adam N. & Vasalou, Asimina. (2009). "Me, Myself, and I: The Role of Interactional Context on Self-Presentation Through Avatars". ScienceDirect. 25:2
- ↑ Joinson, Adam N. & Vasalou, Asimina. (2009). "Me, Myself, and I: The Role of Interactional Context on Self-Presentation Through Avatars". ScienceDirect. 25:2
- ↑ Murphy, Sheila. (2004). "Live in Your World, Play in Ours: The Spaces of Video Game Identity". Journal of Visual Culture. 3:2.
- ↑ Leahy, Matthew Michael & Schultze, Ulrike. "The Avatar-Self Relationship: Enacting Presence in Second Life". Association for Information Systems. 2009. 2 - 15.
- ↑ Leahy, Matthew Michael & Schultze, Ulrike. "The Avatar-Self Relationship: Enacting Presence in Second Life". Association for Information Systems. 2009. 2 - 15.
- ↑ "Second Life Avatars and their Real Life". Web Urbanist. Retrieved June 18, 2007.
- ↑ Boon, Stuart & Sinclair, Christine. (2009). "A World I Don't Inhabit: Disquiet and Identity in Second Life and Facebook". Education Media International. 46:2
- ↑ Boon, Stuart & Sinclair, Christine. (2009). "A World I Don't Inhabit: Disquiet and Identity in Second Life and Facebook". Education Media International. 46:2
- ↑ Bardzell, Shaowen & Odom, William. (2008). "The Experience of Embodied Space in Virtual Worlds: An Ethnography of a Second Life Community". SAGE Journals. 11:3.
- ↑ Black Mirror
- ↑ The Sims
- ↑ Call of Duty: Advanced Warefare
- ↑ Kevin Spacey
- ↑ Kowalski, Robin et al. "Bullying In The Digital Age: A Critical Review And Meta-Analysis Of Cyberbullying Research Among Youth". Psychological Bulletin 140.4 (2014): n. pag. Web. 7 Mar. 2017.
- ↑ http://users.rider.edu/~suler/psycyber/disinhibit.html
- ↑ Staff, L. (2010, February 05). First Amendment. Retrieved from https://www.law.cornell.edu/constitution/first_amendment
- ↑ https://www.statista.com/statistics/264810/number-of-monthly-active-facebook-users-worldwide/
- ↑ The Ultimate Guide To The Deep Web. Retrieved from http://www.sickchirpse.com/deep-web-guide/
- ↑ MacAskill, E., Thielman, S., & Oltermann, P. (2017, March 07). WikiLeaks publishes 'biggest ever leak of secret CIA documents'. Retrieved from https://www.theguardian.com/media/2017/mar/07/wikileaks-publishes-biggest-ever-leak-of-secret-cia-documents-hacking-surveillance
- ↑ Beckett, A. (2009, November 25). The dark side of the internet. Retrieved from https://www.theguardian.com/technology/2009/nov/26/dark-side-internet-freenet
- ↑ Infographic: A History of Love & Technology. (2013, January 17). Retrieved from http://www.pbs.org/pov/xoxosms/infographic-technology-dating/
- ↑ Infographic: A History of Love & Technology. (2013, January 17). Retrieved from http://www.pbs.org/pov/xoxosms/infographic-technology-dating/
- ↑ Lee, S. (2016, February 14). The History of Online Dating From 1695 to Now. Retrieved from http://www.huffingtonpost.com/susie-lee/timeline-online-dating-fr_b_9228040.html
- ↑ The History of Online Dating (US). (n.d.). Retrieved from http://www.eharmony.com/history-of-online-dating/
- ↑ The History of Online Dating (US). (n.d.). Retrieved from http://www.eharmony.com/history-of-online-dating/
- ↑ Zwilling, M. (2013, March 01). How Many More Online Dating Sites Do We Need? Retrieved from https://www.forbes.com/sites/martinzwilling/2013/03/01/how-many-more-online-dating-sites-do-we-need/#1302f8367882
- ↑ Key Facts. (n.d.). Retrieved from http://match.mediaroom.com/key-facts
- ↑ The History of Online Dating (US). (n.d.). Retrieved from http://www.eharmony.com/history-of-online-dating/
- ↑ Catfish definition. (n.d.). Retrieved from https://en.oxforddictionaries.com/definition/catfish
- ↑ Palmer, R. (2013, January 17). Where Does 'Catfish' Come From? Online Hoax Movie Inspired By Fisherman's Lore. Retrieved from http://www.ibtimes.com/where-does-catfish-come-online-hoax-movie-inspired-fishermans-lore-1022374
- ↑ https://socialcatfish.com/what-is-catfishing-online-dating/
- ↑ Palmer, Roxanne. "Where Does 'Catfish' Come From? Online Hoax Movie Inspired By Fisherman's Lore." N.p., 17 Jan. 2013. Web.
- ↑ Campbell, Kelly, Dr. "Catfish and Secrets." Psychology Today. Sussex Publishers, 24 June 2013. Web. <https://www.psychologytoday.com/blog/more-chemistry/201306/catfish-and-secrets>.
- ↑ "Catfishing – What Is It, Where It Came from and the Psychology Behind Catfish Online Dating Scams." N.p., 02 Aug. 2016. Web.
- ↑ Campbell, K., Dr. (2013, June 24). Catfish and Secrets. Retrieved from https://www.psychologytoday.com/blog/more-chemistry/201306/catfish-and-secrets
- ↑ Evan's and Brase, 2007
- ↑ Ellison, Heino, and Gibbs; 2006
- ↑ Sztompka 1999
- ↑ Sztompka 1999
- ↑ Mills 2007
- ↑ Steiger et al; 2007
- ↑ Toma et all ; 2008
- ↑ Suler; 2004
- ↑ Lucid; 2009
- ↑ Walther and Parks; 2002
- ↑ Stone; 1995
- ↑ Luxton, E. “4 billion people still don’t have internet access. Here’s how to connect them“. In: The World Economic Forum 11.05.2016
- ↑ Sagasti, A “The Knowledge Explosion and the Knowledge Divide”. 2001. p. 32
- ↑ Segev, Elad. “Google and the Digital Divide” edited by Elad Segev. Elsevier Science. 2010.
- ↑ Segev, Elad. “Google and the Digital Divide” edited by Elad Segev. Elsevier Science. 2010. p.22-23.
- ↑ Sagasti, A “The Knowledge Explosion and the Knowledge Divide”. 2001.
- ↑ McLuhan, Marshall. (1964) Understanding Media: The Extensions of Man.
- ↑ Grosswiler, P., 2010. Transforming McLuhan: Cultural, Critical, and Postmodern Perspectives. Peter Lang.
- ↑ Cultural determinism - Oxford Reference. (2017, January 15). Retrieved from http://www.oxfordreference.com/view/10.1093/oi/authority.20110803095652815
- ↑ Culture in Sociology topic. (n.d.). Retrieved from http://www.ldoceonline.com/Sociology-topic/culture
- ↑ Jacobi, Jolande. Jacobi, S, Jolande., 1999. Psychology of C G, Jung. Reprint, Revised edn. Psychology Press. p. 33.
- ↑ Erving Goffman in The Presentation of the Self In Everyday Life (1959). p. 31.
- ↑ Fry, Stephen. 2015. Erving Goffman and the Performed Self. BBC Radio 4. https://www.youtube.com/watch?v=6Z0XS-QLDWM.
- ↑ http://www.psychosocial-studies-association.org/
- ↑ Bailenson, J., Ducheneaut, N. Yee, N., (2009). The Proteus Effect Implications of Transformed Digital Self-Representation on Online and Offline Behaviour, Stanford University Department of Communication, Stanford, CA
- ↑ Kelliher, A G M (2007) Everyday Storytelling: supporting the mediated expression of online personal testimony. Massachuesetts Institute of Technology, USA
- ↑ Russell, J. & Norvig, P. (eds). Artificial Intelligence: A Modern Approach, Prentice Hall Inc, 1995. p. 1
- ↑ http://royal.pingdom.com/2010/01/08/how-google-collects-data-about-you-and-the-internet/
- ↑ https://securehomes.esat.kuleuven.be/~gacar/fb_tracking/fb_plugins.pdf
- ↑ https://www.theguardian.com/uk/2013/jun/21/gchq-cables-secret-world-communications-nsa
- ↑ http://www.huffingtonpost.com/james-canton/from-big-data-to-artifici_b_10817892.html
- ↑ http://isciencemag.co.uk/features/interviewing-murray-shanahan-ex-machinas-scientific-advisor/
- ↑ http://www.bbc.co.uk/news/technology-27762088
- ↑ Waldron, S., Wood, C., & Kemp, N. (2016). Use of predictive text in text messaging over the course of a year and its relationship with spelling, orthographic processing and grammar. Journal of Research in Reading. doi:10.1111/1467-9817.12073
- ↑ Dreyfus, H. (2001). On The internet. (2nd ed.). New York: Rutledge. pp. 101
- ↑ w:Humans (TV series)
- ↑ w:Robot & Frank
- ↑ Eagle Eye
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p26
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies" in A Private Sphere, p27
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p26
- ↑ http://www.encyclopedia.com/philosophy-and-religion/other-religious-beliefs-and-general-terms/miscellaneous-religion/public#3-1O88:pblcsphrvrssprvtsphrdstnc-full
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p28
- ↑ Fuchs, Christian. “Habermas’s Concept of the Public Sphere” in Social Media: a critical introduction, p181
- ↑ https://petition.parliament.uk/help
- ↑ https://infoscience.epfl.ch/record/146804/files/InformationSchool.pdf
- ↑ Burnett, Robet. Marshall, David. 2003. Web Theory, pg.1
- ↑ Levy, Pierre. Bononno, Robert. 1997. Collective Intelligence. p13
- ↑ Fuchs, Christan. 2014. Social Media, A Critical Introduction, p32-43
- ↑ Gauntlett, D. 2011. Making is Connecting: The Social Meaning of Creativity, from DIY and knitting to YouTube and Web 2.0
- ↑ http://www.danah.org/bio.html
- ↑ http://www.sheffield.ac.uk/socstudies/staff/staff-profiles/helen-kennedy
- ↑ Levison ,P. 1999. DIGITAL MCLUHAN, p2
- ↑ McLuhan, Marshall. 1962. The Gutenberg Galaxy, p32
- ↑ Levison ,P. 1999. DIGITAL MCLUHAN, p4
- ↑ http://zizi.people.uic.edu/Site/Thoughts/Entries/2010/11/23_A_Private_Sphere.html
- ↑ Fuchs, Christian. 2014. “Google: Good or Evil Search Engine?” in Social Media: a critical introduction, pg.132
- ↑ http://www.alexa.com/topsites/category/Computers/Internet/Searching/Search_Engines
- ↑ http://www.internetlivestats.com/google-search-statistics/
- ↑ Fuchs, Christian. 2014. “Google: Good or Evil Search Engine?” in Social Media: a critical introduction, pg.127
- ↑ https://www.usnews.com/opinion/articles/2013/05/10/15-ways-google-monitors-you
- ↑ https://www.google.com/intl/en/policies/privacy/#infouse
- ↑ Meikle, Graham. 2016. “TMI: Prism” in Social Media: Communication, Sharing and Visibility, pg. 106
- ↑ https://www.theguardian.com/technology/2013/aug/14/google-gmail-users-privacy-email-lawsuit
- ↑ http://www.bbc.co.uk/guides/z9x6bk7
- ↑ https://www.google.com/policies/terms/
- ↑ https://www.theguardian.com/technology/2013/aug/14/google-gmail-users-privacy-email-lawsuit
- ↑ https://investor.fb.com/home/default.aspx
- ↑ https://zephoria.com/top-15-valuable-facebook-statistics/
- ↑ http://bigthink.com/praxis/do-you-have-too-many-facebook-friends
- ↑ Miller, Daniel. 2011. Tales From Facebook, preface
- ↑ https://zephoria.com/top-15-valuable-facebook-statistics/
- ↑ https://www.statista.com/statistics/417295/facebook-messenger-monthly-active-users/
- ↑ https://www.theguardian.com/technology/2015/mar/31/facebook-tracks-all-visitors-breaching-eu-law-report
- ↑ http://newsroom.fb.com/news/2015/03/send-money-to-friends-in-messenger/
- ↑ https://twitter.com/privacy
- ↑ https://en.wikibooks.org/wiki/Living_in_a_Connected_World/The_Online_Real-Life_Divide#Snapchat
- ↑ http://www.independent.co.uk/life-style/gadgets-and-tech/news/snapchat-privacy-terms-of-service-legal-snaps-update-a6714686.html
- ↑ Papacharissi, Zizi. 2010. A Networked Self, edited by Zizi Papacharissi, Taylor and Francis, p315
- ↑ Rettberg, Jill Walker. 2014. Seeing ourselves through Technology, Written, Visual and Quantitative Self-Representations, p11-14
- ↑ boyd, danah. 2014. It’s Complicated: The Social Lives of Networked Teens, p32
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p27
- ↑ Dery, Mark. 2008. "The everyday posthuman: new media and identity", cited in New Media, p269
- ↑ https://support.apple.com/en-gb/HT207056
- ↑ http://searchcrm.techtarget.com/feature/Location-based-apps-bring-ease-and-privacy-concerns-to-consumers
- ↑ https://www.cnet.com/news/senate-bill-amounts-to-death-penalty-for-web-sites/
- ↑ Charlie Osborne, "Would a Wikipedia blackout be such a bad thing?", iGeneration on ZDNet, December 13, 2011, 11:04 am PST. Retrieved January 5, 2012.
- ↑ http://www.ispreview.co.uk/index.php/2016/11/uk-government-confirm-move-force-isps-blocking-adult-sites.html
- ↑ https://www.publications.parliament.uk/pa/bills/cbill/2016-2017/0087/amend/digital_rm_rep_1123.1-7.html
- ↑ Lanier, Jaron. 2010. You Are Not A Gadget, p48.
- ↑ https://opennet.net/research/profiles/burma
- ↑ https://opennet.net/blog/2008/07/burmese-regulations-cybercafes-stringent-expected
- ↑ http://www.internetlivestats.com/internet-users/china/
- ↑ Deibert, Ronald., Palfrey, John., Rohozinski., Zittrain, Jonathon. 2012. Access Contested : Security, Identity, and Resistance in Asian Cyberspace. p3
- ↑ Deibert, Ronald., Palfrey, John., Rohozinski., Zittrain, Jonathon. 2012. Access Contested : Security, Identity, and Resistance in Asian Cyberspace
- ↑ http://www.cnbc.com/2017/01/24/chinas-great-firewall-is-doubling-up-on-vpn-regulation.html
- ↑ http://influence-central.com/kids-tech-the-evolution-of-todays-digital-natives/
- ↑ https://freedomhouse.org/report/freedom-net/freedom-net-2016
- ↑ https://freedomhouse.org/report/freedom-net/freedom-net-2016
- ↑ http://www.newstatesman.com/politics/2014/07/deep-state-data-surveillance-about-power-not-safety
- ↑ https://www.aclu.org/report/bigger-monster-weaker-chains-growth-american-surveillance-society?redirect=technology-and-liberty/bigger-monster-weaker-chains-growth-american-surveillance-society
- ↑ http://www.newstatesman.com/science-tech/2016/10/everything-you-need-know-about-terrifying-investigatory-powers-bill
- ↑ https://www.theguardian.com/world/2016/nov/19/extreme-surveillance-becomes-uk-law-with-barely-a-whimper
- ↑ Rainie, Lee. et al, “Anonymity, Privacy, and Security Online”. http://www.pewinternet.org/2013/09/05/anonymity-privacy-and-security-online/
- ↑ Rainie, Lee. et al, “Anonymity, Privacy, and Security Online”. http://www.pewinternet.org/2013/09/05/anonymity-privacy-and-security-online/
- ↑ Rainie, Lee. et al, “Anonymity, Privacy, and Security Online”. http://www.pewinternet.org/2013/09/05/anonymity-privacy-and-security-online/
- ↑ https://www.instantssl.com/ssl-certificate-products/https.html
- ↑ Ess, Charles. 2009. Digital Media Ethics, p31
- ↑ Ess, Charles. 2009. Digital Media Ethics, p32
- ↑ Athique, Adrian. 2013. Digital Media and Society: An introduction (1st ed.). Oxford: Policity Press, page 492.
- ↑ [1], Sharp, J. C., 2007. A short history of Spyware.
- ↑ [2], Lavasoft. 2017. The history of Spyware.
- ↑ [3], the official Microsoft Blog (2013, April 17)
- ↑ [4], Keyloggers Explained: What You Need to Know. (2017). Howtogeek.com.
- ↑ [5], Identity Theft Statistics in 2016 - Should You Be Worried?. (2017). ID Theft Authority.
- ↑ [6], What are the consequences of spyware activity? (2017). Computer-security-review.org.
- ↑ Andrejevic, Mark. 2011. Surveillance and Alienation in the Online Economy. Surveillance And Society.
- ↑ [7], Benjamin Edelman - Biography. Benedelman.org.
- ↑ [8], Is Google to Blame for Spyware?. Archive.oreilly.com.
- ↑ Janet Jackson and Justin Timberlake’s in the 2004 Superbowl
- ↑ Queen of cynicism: No stunt's too shameless for Beyonce, who was once accused of trying to look white but this week posed as a heroine of black power
- ↑ I don't date people who are famous', admits Emma Watson... but wishes she could 'protect' her beaus from the public eye
- ↑ Inside the Kim Kardashian Robbery: Everything We Know So Far
- ↑ chip off the old block: Did Malia Obama smoke MARIJUANA at Lollapalooza? Video shows the president's eldest daughter puffing on a suspicious cigarette (just like dad did . . .)
- ↑ Macaulay Culkin: ‘No, I was not pounding six grand of heroin a month’
- ↑ Carl Greenwood, (12 SEP 2016) Celebrity death hoaxes: The stars killed over and over again on social media.
- ↑ "Edison Chen's blog". CLOT. Archived from the original on 6 February 2008. Retrieved 4 February 2008.
- ↑ "Sexy Photo Gate' Mesmerizes Hong Kong, China and Sparks Police Crackdown, Backlash". The Wall Street Journal, Fowler, Geoffrey; Jonathan Cheng (15 February 2008)
- ↑ "China arrests over HK sex scandal", BBC News. 20 February 2008.
- ↑ "China riveted by stolen sex photos of Hong Kong stars". The Guardian., Watts, Jonathan (13 February 2008).
- ↑ "Chinas nackte Superstars", Der Spiegel. 27 February 2008.
- ↑ NewYorkDailyNews, Eloise Parker, (October 13, 2008) Choi Jin Sil, Ahn Jae Hwan, more South Korean stars commit suicide after Internet rumors.
- ↑ NewYorkTimes, Choe Sang-Hun, (12 October 2008) South Korea links Web slander to celebrity suicides.
- ↑ Business Insider, Kovach (2014), We Still Don't Have Assurance From Apple That iCloud Is Safe
- ↑ Business Insider, Kovach (2014), We Still Don't Have Assurance From Apple That iCloud Is Safe
- ↑ The Verge, Kastrenakes (2014), Apple denies iCloud breach in celebrity nude photo hack
- ↑ The Verge, Kastrenakes (2014), Apple denies iCloud breach in celebrity nude photo hack
- ↑ The Guardian, Badham (2014), If you click on Jennifer Lawrence's naked pictures, you're perpetuating her abuse
- ↑ The Guardian, Badham (2014), If you click on Jennifer Lawrence's naked pictures, you're perpetuating her abuse
- ↑ The Independent, Selby (2014), Emma Watson on Jennifer Lawence nude pictures leak: 'Even worst than seeing women's privacy violated is reading the comments'
- ↑ The Washington Post, Lubitz (2014), More stars react to the massive celebrity-photo leak
- ↑ The Telegraph, Sanghani (2014), Jennifer Lawrence photo leak: Let's stop calling this hacking 'The Fappening'
- ↑ BBC News, Kellon (2014), Apple toughens iCloud security after celebrity breach
- ↑ Forbes, Rogowsky (2014), Yes, Celebs Had Their iCloud Accounts Hacked. No, You Shouldn't Shut Yours Off
- ↑ Ashley Madison® - Affairs & Discreet encounters - Life is short - Official Ashley Madison website
- ↑ Rachel Hosie. "Ashley Madison hacking: What happened when married man was exposed"
- ↑ The Guardian, Thielman (2016), Yahoo Hack: 1b accounts compromised by biggest data breach in history, 2016
- ↑ New York Times, Goel (2017), Yahoo's Top Layer Resigns and C.E.O. Marissa Mayer Loses Bonus in Wake of Hack
- ↑ New York Times, Goel (2017), Yahoo's Top Layer Resigns and C.E.O. Marissa Mayer Loses Bonus in Wake of Hack
- ↑ The Guardian, Thielman (2016), Yahoo Hack: 1b accounts compromised by biggest data breach in history, 2016
- ↑ The Guardian, Woolf (2016), Yahoo 'secretly monitored emails on behalf of the US Government
- ↑ The Guardian, Woolf (2016), Yahoo 'secretly monitored emails on behalf of the US Government
- ↑ The Guardian, Woolf (2016), Yahoo 'secretly monitored emails on behalf of the US Government
- ↑ The Guardian, Woolf (2016), Yahoo 'secretly monitored emails on behalf of the US Government
- ↑ Ess, Charles. 2009. Digital Media Ethics, p46
- ↑ Weber, Rolf H. 2012. "How Does Privacy Change in the Age of the Internet" in Fuchs, Boersma, Albrechtslund, and Sandoval (eds.) Internet and Surveillance: The Challenges of Web 2.0 and Social Media, p274
- ↑ [9], Stuart, K. & Arthur, C. 2011. PlayStation Network hack. the Guardian.
- ↑ [10], PlayStation outage caused by hacking attack - BBC News. (2011). BBC News.
- ↑ a b [11], Quinn, B. & Arthur, C. 2011. PlayStation Network hackers access data of 77 million users. the Guardian.
- ↑ Mogull, Rich. 2011. Protect your privacy: take control of social networking [[12]]
- ↑ Johnson, Sheree. 2014. New Research Sheds Light on Daily Ad Exposures [[13]]
- ↑ Baym, N. 2010. Personal connections in the digital age. Cambridge: Polity Press
- ↑ Miller, V. 2011. Understanding digital culture. London: Sage.
- ↑ https://www.sciencedaily.com/releases/2016/03/160330135623.htm
- ↑ Baym, N. 2010. Personal connections in the digital age. Cambridge: Polity Press
- ↑ Scheff, S. 2014. Are you oversharing on social media? Retrieved March 5, 2017, from http://www.huffingtonpost.com/sue-scheff/are-you-oversharing-on-so_b_5940996.html
- ↑ Lanier, J. 2010. You are not a gadget. New York: Alfred A. Knopf.
- ↑ Mayer-Schönberger, V. 2009. Delete : The virtue of forgetting in the digital age. Oxford: Princeton University Press.
- ↑ https://support.twitter.com/
- ↑ https://support.twitter.com/articles/77606
- ↑ (Mosco 2004)
- ↑ (Maxwell and Miller 2012)
- ↑ (Maxwell and Miller 2012)
- ↑ ( Allmer 2017)
- ↑ (Sandoval 2013)
- ↑ ( Dyer-Witheford 1999)
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p27
- ↑ https://www.techopedia.com/definition/28556/filter-bubble
- ↑ Pariser, Eli.; Helsper, Ellen. 2011.The Filter Bubble: What The Internet Is Hiding From you,
- ↑ Lanier, Jaron. 2010. "Missing Persons", in You Are Not A Gadget, p3-23
| This page or section is an undeveloped draft or outline. You can help to develop the work, or you can ask for assistance in the project room. |
Persistent Connectivity and the Fear of Missing Out
[edit | edit source]Introduction
[edit | edit source]his chapter aims to discuss the key academic concepts and theories behind the development of persistent connectivity and the fear of missing out respectively. To achieve this, we have split the chapter into key sections and within these further sub-headings which we feel will aid our investigation into this broad subject; there are many angles from which this subject can be approached and it is our aim to cover these angles by setting the chapter out in this way. The main focus areas can be found in our Main Concepts section from which one can navigate to their areas of interest.
Main Concepts
[edit | edit source]
In order to gain an understanding of this topic, it is important to first determine what is meant by The Fear of Missing Out (FoMO). The section regarding this will look into the history of this concept starting with when it was first introduced. It will discuss some of the previous studies that have been concerned with the fear of missing out including the motivational, emotional, and behavioral correlates of fear of missing out and additionally, the connection between alcohol and FoMO.
In regards to the persistent connectivity and the fear of missing out that is becoming more and more normalized in todays society, we will be talking about The Development of the Internet and technological advances that have happened throughout the past couple of decades. This allows us to see the changes not only to the ways in which we function socially but also the way that new technology and persistent connectivity has changed the ways in which our businesses function and go into depth about the Current Uses of the Internet.
We will then go on to talk about the Always on Culture that has come to light in the last decade, with the surge in mobile technology and ongoing access to the internet anywhere people go. This always on culture is then linked to the effects that our persistent connectivity may have on our internal and external selves.
We talk about the Internal Effects in which we discuss the ways in which our internal identity can be altered by the web through the creation of "mini performances" which means to say that we create a different version of ourselves for presentation purposes. We then go on to talk about "the google effect" which suggests that our brain has changed due to evolving technology in that we no longer store information in the way we used to. Also within the chapter we touch on the tethered self and the creation of identity through new media sites.
The External Effects of the Web are then discussed by talking about how our social interactions have been altered by the development of mobile technology and the ways in which persistent connectivity has changed our view of what is acceptable and what is not. In this section, we also discuss mobile privatization and the ways in which how much we share with people has changed largely since the introduction of social media.
In the final section we look at ideas from a key sociologist, Erving Goffman, as we explore his theory - Goffman's Mask - of using different personas and masks to portray ourselves depending on the circumstance. This is an important aspect to acknowledge when we consider the ways in which we connect with others on the internet. We will talk about how these personas create a range of meanings and attitudes in the topic of persistent connectivity online and also how these changes can be identified in regard to the fear of missing out.
The Development of the Internet
[edit | edit source]Before 1970
[edit | edit source]Before 1970, individual researchers developed the technologies, including queuing theory involving probabilities, packet switching, and routing. Leonard Kleinrock pioneers the packet-switching concept in his Massachusetts Institute of Technology.

In 1962, J.C.R. Licklider argued that, within a few years, computers would become sufficiently powerful to cooperate with humans in solving scientific and technical problems. He conceived the Intergalactic Network, a concept really close to what the Internet is today. In 1965, ARPA(Advanced Research Projects Agency) sponsored a study on « cooperative network of time-sharing computer ».
1970's
[edit | edit source]During the 1970s, experimental networks, notably the ARPANET, were constructed. Dr. David Clarck implements Internet protocols for the Multics systems, the Xerox PARC ALTO and the IBM PC. In 1972, the first email was sent by Ray Tomlinson. The « @ » sign was chosen to separate local from global emails: « user@host.com ».
1980's
[edit | edit source]The Internet protocol is introduced in 1984, it gives an address (IPV4) that provide us a IP number for each computer so we can connected. This protocol sends packets one after an other from transmitter’s IP number to the receptor’s IP number. The Transmission Control Protocol has the role of checking if the packet sent to the receptor arrived. Macintosh introduced some essential elements of the computer: the graphic interface, a design software and a word processing software. A new stage appear, the computer technology goes from a means of monitoring, and tracking (Big Brother) to a tool that can benefit to humans. The Internet became a tool and a way of express their liberty. The same year, Stewart brand, a journalist interested in informatics, created a virtual community named The WELL with the involvement of 600 persons. People discovered conversations online: they could express themselves through internet by sending messages and waiting answers.

William Gibson write a science fiction book, the Notion of cyberspace appeared in his book. He conceptualized data base, approach the notion of hackers. Researchers try to inspire from its book to make more researches. In the mid-1980s, hundreds of thousands of workers at IBM were using electronic networks for e-mail and file transfers, the banks were performing electronic funds transfer. The first network gateways between U.S. and Europe was established by Lawrence Landweber. First U.S developed the network to allow access to Education: Dr. Stephen Wolff leads the development of NSFNET (National Science Foundation Network) to support research and higher education.The global Internet extend, about 25 countries were connected to the NSFNET.
1990's
[edit | edit source]In the 1990s, the invention of the web made it much easier for users to access informations. Linux, the operating system is created with a graphical interface. In 1991, for the first time the World Wide Web is made available to the public thanks to Tim Berners-Lee and Robert Cailliau. Through this major step, a browser called Mosaic appear and helps popularize the WWW (World Wide Web) among the general public. The first blog was created in 1998, the web publishing tool are available for non-technical users to express themselves. Between 1995 and 2000, the Dotcom bubble[1], also known as the Internet bubble, referred to the period in which investors look to the market of Internet. Investors pumped their money into startups and Internet companies and hope those investments will turn into profit. The Dot Com bubble burst, investitures reduced or cut funding, some of the Internet companies failed. Amazon.com was launched in 1995 during the Dotcom bubble, but the company persevered and decide to chose a slow growth strategy to stay in business.[2]
2000's
[edit | edit source]The early 21st century was marked by the famous virus called I LOVE YOU[3] or LOVEBUG. It infected 15 million computers and caused damage estimated at $5 billion. This virus was sent by email to Outlook inboxes, the subject of this email was: « ILOVEYOU » to make people believe that the email was a love letter, in the email there was an attachment named « love-letter-for-you ». Victims of this virus lost their files and their usernames and passwords were sent to the virus’ s creator. In 2001, Microsoft launched the operating system Windows XP, increasing the ease of access to the Web for the general public.
The internet has grown substantially between 2000 and 2010, there were only 361 million Internet users in 2000 in the entire world, 10 years later, that number increased to 1,967 million in the world[4]. The internet became more spread out, with a user number increase of 444, 9 % in 10 years.
Which country's internet population has grown the most between 2000 an 2010?
| Country | New Internet users since 2000 | Relative growth |
|---|---|---|
| China | 397.5 million | 1767% |
| United States | 144.1 million | 152% |
| India | 76.0 million | 1520% |
| Brazil | 70.9 million | 1419% |
| Russia | 56.6 million | 1826% |
| Japan | 52.1 million | 111% |
| Nigeria | 43.8 million | 21891% |
| Germany | 41.1 million | 171% |
| France | 36.1 million | 425% |
| United Kingdom | 36.0 million | 234% |
Blogging and social media began to explode in popularity since the early 2000’s, Friendster was founded in 2002 and became known as the first modern general social network. In 2003 LinkedIn was founded, it was one of the first social networks devoted to business, MySpace started the same year and was followed by websites to facilitate photo sharing like Photobucket and Flickr. Facebook and Twitter both became available in 2006 to public users. Today, there are thousands of social media platforms, all serve a different interest: photography, dating, business, videos, and social communities. E-commerce has also been developed, companies now provide online food ordering, media streaming in a fully online marketplace.
Current Uses of the Internet
[edit | edit source]Business Uses
[edit | edit source]Nowadays, organisations are more likely to use some sort of social media in their marketing practices. With the coming of social media it means that companies now have a much farther reach in terms of raising awareness of their brand as well as identifying new potential customers.

According to this chart developed by Christine Moorman in “The CMO Survey”, the average percentage of firms using social media in their marketing activities is over 80%. [5] This information makes it clear that social media must be a very strong tool in regards to business success.
With collective monthly views of 2.8 billion on Facebook, Instagram and Twitter [6] it is understandable the appeal for organisations to use the platforms in increasing their success and profits. The development of targeted advertisements on platforms, such as Facebook and twitter, it is now easier to target specific customers based on their likes and dislikes on the platform. This ensures that the organisation is only targeting potential customers and not wasting time on advertising to people that simply wouldn't be interested in the products or services on offer. With targeted advertising now being easily accessible to the majority of businesses including small independently own companies it is a very cheap and effective way of advertising your products or services without breaking the bank. All Instagram users now have the option to transfer their profiles to business profiles making it easier for customers to get in contact or interact with their website, also on Facebook you have an option to create a page for your business which gives the option to completely cut out the need to have a website at all again cutting costs for smaller businesses that may not have the funds to afford running a website.
Along with targeted marketing and cutting costs social media can also act as a customer touchpoint, which is when the organisation is given the opportunity to interact with their customers on a personal level. It can be seen that a lot of companies now use their social accounts as a point of customer service, often aiding customers with problems and responding to complaints. However, this can have a negative affect on the business as as well as it’s upsides social media also allows for negative comments and complaints to spread a lot quicker than they would when social media wasn't around.
Social Uses
[edit | edit source]We have already established that the number of users on social media is now in the billions but why do people use these platforms? There are various social reasons that people tend to gravitate towards social platforms a study done by Anita Whiting and David Williams [7] which identified ten uses and gratification of using social media after carrying out 25 interviews. The ten uses and gratifications identified were:

- Social interaction
- Information Seeking
- Pass time
- Entertainment
- Relaxation
- Expression of opinions
- Communicatory utility
- Convenience utility
- Information sharing
- Knowledge about others
Social Interaction is one of the key current uses of social media, Melissa Leiter says “Social media comes down to a simple basic human desire: the need to connect with other humans, to be part of a group” [8] and since many social media sites accommodate for the forming of communities and allows people to find others with the same interests as a much larger scale than you could have before the development of the internet it is easy to see how the natural instinct to connect with others would be enhanced. A lot of the more well known social media sites are designed solely for the purpose of social interaction, hence the term "social networking sites". Facebook is primarily used to communicate with people, with being able to comment on status', pictures and on people's personal pages, it's all about being social. Facebook also has a private messaging service, making it even easier and more accessible to have constant communication with peers, following the Web 2.0 concept (which you can read more about in Internal Effects).
A social use that seems to becoming more and more popular in modern society and with the rise of the internet is that of online dating, which we wish to further explore here.

In the digital age, online dating has become more and more common with the invention of sites such as Tinder, Grindr (for LGBTQ+ people) and Match.com - to name just a few. Using such sites has a fair amount of appeal to individuals, of course they are easily accessible, involve little effort unless you pursue a relationship and move it to in-person dating, and for many people, the idea that they can be less honest about themselves than they may be when meeting in 'real life', as they can essentially create any type of personality that they like for themselves, even one that holds no similarity to their real self whatsoever by using different pictures, a different name and so on. This is not exactly moral however it is more common than one would think and even has a name - Catfishing. However Wagatwe Wanjuki (2005)[9] discusses the more positive aspects of social media in her article on online dating. She discusses some studies that she has researched which state that online dating is just as, if not more, successful than real life dating (as found by Stanford University, 2012). It is also beneficial to many as it widens the dating pool, so if they are from a small area they have a wider variety of people to connect with online. This shows how using the internet for social uses can be a helpful for many people in a variety of situations.
Information Seeking refers to people self-educating from the vast amounts of information available on the internet. The internet has allowed vast amounts of information readily available at our fingertips which was previously a trip to the library to get your hands on. This has encouraged people to take to the internet in order to find out any information they need whether that be for school, work or a simple piece of general knowledge, which is great in terms of easy access but could be making us too reliant on this form of research. The Kaspersky Lab states that, “we don't commit data to memory because of the "Google Effect" – we're safe in the knowledge that answers are just a click away, and are happy to treat the web like an extension to our own memory”. Like Web 2.0, you can read more about the “Google Effect” in Internal Effects.
Pass Time is an obvious reason to use social media and the internet in general as nowadays people find it hard to be doing nothing and in need for constant stimulation, Philip Karahassan, a psychologist says after looking at his own uses of smartphone technology he often found himself using his smartphone when he was “at a loss of things to do” and says that this results in to miss out on actual thoughts and experiences [10]
Entertainment is a huge factor of the internet as since the internet has revolutionised the way we play games and consume movies, TV and other forms of entertainment. The internet has allowed gaming to be collaborative as your gaming experiences can now be shared with others through “Live Gaming”. The amount of young boys that play games with others on the internet is around 50% [11] which shows the popularity of the internet for this use. Nowadays, most entertainment mediums are accessible to anyone with a computer, the ability to download and stream games, films and television programmes has allowed people to consume forms of entertainment at their leisure without having to go out and visit a game shop or DVD store which is a very common practice for internet users as can be seen in “Our Survey on Social Uses” where the majority of answerers, 64%, used the internet in this way.
Relaxation is a less common use of the internet scoring a mere 21% of our survey participants using it for this reason however, much like using the internet for entertainment it is the same types of activities that can also act as uses for relaxation. For example, winding down after a long day by watching a funny video could be seen as a reward of hard work and an aid in relaxation to get the stresses of the day out of mind. Watching a funny video clip, streaming relaxing musics or downloading a film to watch can offer that relaxing break that people need but this also combines with using the internet for entertainment.
Expression of Opinions can relate to the sharing of statuses about current events or even just something that you have an opinion about. Many people choose not to share too many opinions as it can often lead to backlash from other social users however their are some people that can get away with the sharing of opinions and it is encouraged that they do so. A key group who uses social media for social purposes (i.e. engagement with their fans) are celebrities, and they tend to have huge audiences. However there can be repercussions of this as things can often be misinterpreted online and this causes issues, adding more to the list of dangers that we can encounter when using these online platforms, most recently the Harry Potter star, Emma Watson received backlash on a recent photoshoot and her self proclaimed “feminist” status was questioned by many people online. Emma Watson then responded to the backlash with the statement, “Feminism is not a stick with which to beat other women with” [12], this is a key example of the power of opinions on social media.
Communicatory Utility involves using platforms like Facebook Messenger, WhatsApp and iMessage in order to communicate with friends. The main attraction of these services is that internet messaging systems allow you to contact someone for free (if at a free wi-fi hotspot) as well as being able to contact someone from all parts of the world. As previously discussed in the “Social Interaction” section, forming online communities on social media can often lead to meeting people from different countries which before the internet would include a cost at communicating to but using messaging systems allows you to communicate essentially for free.
An example of Convenience Utility in the Whiting & Williams research paper was the idea of the ‘convenience of online shopping’ which is a popular use of the internet nowadays. A staggering 41% of purchases are being made online [13] showing the popularity of the activity. The convenience lies in the fact that customers can access online shopping 24 hours a day and whenever suits them, as well as the ease of accessibility shoppers also have access to products from around the world which would not have been available before the internet [14].
Information Sharing refers to the act of posting information about you to others. This can include sharing pictures of your holiday or writing a status update about what you're doing, each day over 55 million status updates are made each day on Facebook [15] and an average of 52 million photos are posted to instagram [16]. Although information sharing is one of the least popular uses of the internet according to our social uses survey, a study done at the University of Arizona concluded that when people were posting statuses they essentially felt less lonely even if their statuses were not getting engaged with by their peers. However along side that was the sad truth that when seeing other friends statuses were being “liked” and responded to more caused the subjects to feel as if they didn't belong [17]. This is caused by the Fear of Missing Out.
Knowledge About Others is essentially being “nosey” and going through peoples profiles or keeping up to date with their statuses, etc. A blog written by Professor Laura Portwood-Stacer states that social media “has eradicated the geographical barriers of privacy” [18] making it so easy for us to find out a variety of information on someone just by scrolling though their social media profiles, you can find out what they had for lunch and where they had it or what movie they went to see and who with. The information on people that can be derived from social media is endless, of course that can be down to the problem with “Information Sharing” or again the Fear of Missing Out.
Our Survey on Social Uses
To aid our knowledge and research into this subject, we decided to carry out a survey to observe what social media sites were most commonly used, and the key reasons (based on Whiting and Williams'[19] uses of gratification) that they used said sites. The results were as follows (note, the results are based on the response of 100 people);
| What is Your Age? | Answer |
|---|---|
| 18-24 | 73% |
| 25-34 | 7% |
| 35-44 | 6% |
| 45-54 | 12% |
| 55-64 | 1% |
| 65-74 | 1% |
| 75 or older | 0% |
| Why Do You Use Social Media? | Answer |
|---|---|
| Social Interaction | 79% |
| Information Seeking (self educating) | 37% |
| Pass Time | 83% |
| Entertainment | 64% |
| Relaxation | 21% |
| Expression of Opinions | 18% |
| Communication (messenger etc) | 83% |
| Convenience (easily accessed) | 29% |
| Information Sharing | 35% |
| Surveillance/Knowledge | 43% |
| How Often Do You Use Social Media? | Answer |
|---|---|
| Extremely Often | 54% |
| Very Often | 38% |
| Moderately Often | 7% |
| Slightly Often | 1% |
| Not at All Often | 0% |
| Which of the Following Social Networking Sites do you Use Most Often? | Answer |
|---|---|
| 92% | |
| Google+ | 11% |
| Snapchat | 55% |
| 60% | |
| 33% | |
| Other | 12% |
There are quite a few points that we can consider from the retrieval of this information. Firstly, as one may expect we discovered that most people using social media are in the 18-24 demographic. The second largest areas of use were generated from the 45-54 category, which is rather intriguing. An article by Eleanor Doughty (2015)[20] suggests that the reasons for older people using sites such as Facebook (which we saw from the survey was the most used site) is related primarily to communication. She argues that as people get older they are aware that their mobility may be decreased and therefore Facebook and Facebook Messenger becomes an extremely useful tool for them. Doughty (2015) cites Martin Lock, CEO of Silversurfers.com[21] who states; "Being comfortable using Facebook will help older people stay connected to their families and friends, and may help alleviate loneliness in later years". Which is of course a very relevant and useful thing to keep in mind. It is often assumed that communication over online platforms is a negative thing, and some believe that it reduces personal value. However as seen here, sometimes it can greatly improve individuals lives.
Career Development Uses
[edit | edit source]The internet plays a major role in career development. The effect of persistent connectivity is discoverability, meaning a simple search of a potential employee's name yields thousands of results. This can either improve or damage a potential employee's chances of getting a job, as how one presents themselves online is an employer's best estimate of how said potential employee may represent their company. In fact, according to a study conducted by CareerBuilder, around 60% of employers look at social media profiles of potential hires. Furthermore, in the same study it was found that around a quarter of employers have actually admonished or fired current employee's due to their negative internet presence. [22]

An example of how social media has positive effects on career building is LinkedIn, a website aimed toward aiding in employment through the use of a social media platform. This medium allows users to make a functional, high tech resume that highlights their strengths. Social media allows the user to present a particular image, and LinkedIn utilizes this feature to assist users in presenting their employability.
Examples of the negative effects of social media use is outlined in Business Insider's article "13 People Who Got Fired for Tweeting". [23] Many people have gotten fired or forced to resign due to presenting controversial opinions on social media platforms. Increased discoverability online allows employers to see anything written on social media profiles or potential or current employees, therefore how someone presents themselves online must be constantly monitored in order to prevent these negative effects.

However there is a growing group of people that instead of depending on the internet to get them a job they have made a job out of their use of social media by turning themselves into social media influencers, this group of people consists of bloggers, you tubers and Instagram stars. Due to their large amount of filling on various platforms, businesses have seen this as a new marketing opportunity and sponsors an influencer that they feel best suits their brand to promote products to their many followers. A way to think about this is an update from celebrity endorsements and since the reign of social influencers is constantly expanding some industries have taken their involvement a step further as recently fashion haus Dolce & Gabana had social stars like Youtubers, Marcus Butler and Jim Chapman [24] with combined 7 million subscribers, walked their mens fashion show. The use of social influencers in, what used to be extremely exclusive, fashion shows has allowed the fashion industry to get a much bigger audience as consumers are now able to see the fashion real time due to the amount of coverage of the events due to influencer attendance [25].
However social influencers are breaking their way into many careers just by the use of their social accounts, music star Justin Bieber is another example of a success story as he was first discovered on Youtube and is now one of the youngest most successful musicians of the century so far. The most common success story is Youtube superstar Zoella (Zoe Sugg) who's first youtube video was her showing 50 things she had in her room, now she has over 10 million subscribers as well as three best selling books and a beauty and lifestyle range in cosmetic drug store, Superdrug. These are only some of the amazing career developments achieved by the use of the internet but really show the current power of discoverability online.
Surveillance Uses
[edit | edit source]The final use of the internet fall under a very controversial heading and that is the use of the internet for surveillance. This way of using the internet can be done for a variety of reasons, as Daniel Trotter Daniel Trottier discusses in his book ‘Social Media as Surveillance: Rethinking Visibility in a Converging World’ [26] there are four primary uses of social media surveillance:

- Interpersonal
- Institutional
- Market
- Policing
In this book he talks about the risks of social media surveillance and how although you may feel like you have your information and security setting under control that you cannot control your peers and the organisations that control the platforms you are posting on. Interpersonal Surveillance refers back to the Social Uses of the internet and using it for “Knowledge About Others” and how people can spy and find out a variety of information about you through these platforms. A less discussed surveillance use is Institutional uses which Trottier has taken the example of universities and schools and how they use social media in order to manage their students. He then refers to Danah Boyd’s idea of the ‘invisible audience’ [27] in relation to the fact that students allow this type of audience, in this case their institutions, to spy on their online activities. Market Uses again refer back to the previously discussed “Business Uses” that are based around the use of the internet and social media in order to find out information about certain customers and use that information in product development or advertisement targeting. The final use discussed by Trottier is Policing, a survey carried out in 2013 by the International Association of Chiefs of Police [28] concluded that over 95% of police departments that were surveyed use social media to come extent, the most popular use was in order to solve crimes said 80% of participants. The massive amounts of information available about individuals and the things we post that we assume no one will see can come in handy for law enforcement as police can often access this information and can identify suspects from crime from small clues that we leave online.
Always on Culture
[edit | edit source]
"Always-On" culture is a term coined by theorists which refers to the fact that we now live in an age where we are constantly connected to technology and the internet. Whether this be from constant notifications on your phone, to having new facets of technology continually available to us, it seems impossible to break away from our virtual lives these days. Sherry Turkle, a leading theorist in this area of studies, describes us being "tethered" to technology, with information and everything our lives have come to be at the touch of a finger tip.
A theorist who takes a more positive stance on the concept is danah boyd, who doesn't see this constant connection as a bad thing suggesting that it's not about being "on or off" anymore as we are always-on nowadays, it is a choice whether or not we allow ourselves to always be on - "technology doesn't simply break social conventions - it introduces new ones." Technology and social media allows us to not always be connected to a physical handset, but connected to the network, which according to boyd is the meaning of "always-on".[29]
"Tethered" to Technology
[edit | edit source]Sherry Turkle refers to the idea of always-on culture in a somewhat critical way. She talks about the idea that we now live in a world where "madmen and women" talk to themselves, unaware of what is actually happening around them. She also goes on to explain that today's generation of teenagers are our "first view of tethering in developmental terms".[30] What Turkle speaks about is the fact that we have a generation, in an important foundation-building time of life, using a technology which we are unable to identify any long-term disadvantages. However, Turkle's skepticism follows a trend more-or-less all new technologies face. From the first TV set in the domestic space, to the home computer, people have forever contested the way in which new technologies will effect society, and many also live in fear of these changes.
Availability
[edit | edit source]Permanent Connectivity
[edit | edit source]One major way in which technology has changed our lives over the past two decades is the immense range of tech available to us at affordable prices, and therefore reaching a larger audience. From the development of the laptop portable computer, to more recent developments such as the smart watch and tablets, the vast array of accessories that are on the market cement the idea of "always-on" - you don't even have to be carrying your phone anymore to be connected, instead it can be strapped around your wrist.

A 2015 study by UK survey company Ofcom reveals that 90% of 16-24 year olds now own a smartphone while the number of 55-64 year olds owning a smartphone device has more than doubled since 2012, rising from 19% to 50%. [31]

As Turkle explains it "it assumes the existence of separate worlds, plugged and unplugged." She also speaks about being "tethered to our "always-on/always-on-us" devices" which she describes as "animate and inanimate".[32] This is a bizarre yet extremely appropriate turn of phase to describe a mobile phone etc. is effective in hammering home the point that while the physical handset is just something to hold, it consumes so much of our lives that it cannot just be dismissed in such a nonchalant manner.
Notion of Availability
[edit | edit source]The notion of availability is the idea that we now live in a society where we expect to be able to reach someone instantly. We live in a society where we see no excuse not to be able to communicate at any time, and have an expectation of being constantly available. With the growth of instant messaging apps and, as mentioned previously, the growth in wearable technology, it becomes apparent that there genuinely seems to be no reason for us to not be always available. danah boyd is a social media scholar who talks about this issue and the blurring of the lines between "real-life" and "virtual-life" - "It's about living in a world where being networked to people and information wherever and whenever you need it is just assumed." boyd goes on to explain that Always-On Culture is "about creating an ecosystem in which people can stay peripherally connected to one another through a variety of microdata."[33]
The result of this blurred line between online/offline life means that many users feel the need to declare a social media "purge", or a "holiday". Users will often post to sites such a Twitter and Facebook publicly announcing their short-term departure from the site; professionals will often send out mass emails altering their contacts to the fact that they will not be available to answer and reply between certain times.
Online Disinhibition
[edit | edit source]Online disinhibition is the understanding that people posting online seem to have less of an awareness of consequence of their actions online. Gackenbach and von Stackleberg describe this as "the inability to control impulsive behaviours, thoughts or feelings and manifests online as people communicating in ways that they would not ordinarily do offline." [34] Another prominent theorist specialising in the topic of online dininhibition is John Suler. In his work "The Online Disinhibition Effect", he describes the way in which online disinhibition can work in two different ways - benign and toxic.
Benign Disinhibition is the term used by Suler to describe the pleasant way in which user will act anonymously and/or publicly online. "Sometimes people share very personal things about themselves. They reveal secret emotions, fears, wishes. They show unusual acts of kindness and generosity, sometimes going out of their way to help others." This maybe be why some people are more likely to participate in an online charity challenge, such as the Ice-Bucket Challenge, but may not be willing to give money to charity in the street - their inhibitions are lowered and therefore their sense of responsibility is too. However, this could also relate to the idea of "FOMO" - the fear of missing out - which is explain in detail below. Toxic Disinhibition is the term Suler uses to describe the darker side to the internet and the way way in which users create a "toxic" virutal environment. He explains "people may be rude, critical, angry, hateful, and threatening, or they visit places of perversion, crime, and violence – territory they would never explore in the “real” world."[35] In taking Suler's approach, there are evidently not just cons to the idea of online disinhibtion, but also pros too.
Perhaps the most notorious example of online disinhibtion, and more specifically toxic disinhibition, is the act of "trolling". This is the act in which someone purposefully seeks to cause offence or harm others verbally online. It is in this instance where the previous point of the blurring of online/offline lives becomes an issue. While some may see it a whimsical way to make fun of someone, new legislation has determined that online trolling is a serious crime. There have been many debates over the past five years or so as to whether trolling should be considered a real crime. This comes with the statistics that 52% of teenagers have experienced "cyberbullying". [36]
Social Context Cues
[edit | edit source]One of the main issues surrounding the way in which we speak online is the lack of social context cues in place to regulate the way in which we communicate with each other. As Suler explains "People don’t have to worry about how they look or sound when they type a message. They don’t have to worry about how others look or sound in response to what they say. Seeing a frown, a shaking head, a sigh, a bored expression, and many other subtle and not so subtle signs of disapproval or indifference can inhibit what people are willing to express." [37] Users lack interpersonal cues, and therefore feel a lower sense of responsibility when it comes to communicating with others online. To contrast, text-based communications usually indicate a low fidelity, whereas face-to-face communications usually indicate the highest level of fidelity.
Privacy Concerns
[edit | edit source]Another issue which causes concerns for a constantly connected user is the issue of privacy. Being constantly available and connected means that technology and the internet touches nearly every part of our lives - from our social relationships, to online banking, there may be a relatively justified cause for concern when it comes to keeping information safe. What seems worrying is the lack of awareness when it comes to "snooping" - people simply do not pay enough attention to terms and conditions etc. to realise just how open their information to the world is. What is even more worrying is that there are users who are aware, but simply accept it as part of the culture of having an online identity.
Data Mining
[edit | edit source]Data mining has become an issue in the past few years, and certainly became more apparent since the NSA snooping scandal and similar instances of tracking. It can be defined as the collection of information online, either through cookies or data trails etc., by an individual, company or organisation. Even the most inconspicuous sites are a treasure trove for companies looking to gain from user information - "Viewed through the lens of market research, platforms such as Facebook and Twitter are much more than sites of networked sociality: they are the world's biggest focus group. Generating more data than any market researcher could ever hope to read and analyse."[38]
More information on privacy issues concerning social media can be found in the Privacy in the Digital Age chapter of Living in a Connected World.
Changes to Interactions due to Technology
[edit | edit source]Technological innovation has dramatically changed the way humans interact and coexist. From the beginning of the digital age up until present day, human behavior has adapted to live in a world dominated by ever-changing machines. This technology-focused mindset not only affects connections with the outside world, but also impacts an individual's sense of themselves.
Internal Effects
[edit | edit source]We are living in a digital age. For some, this concept is terrifying and for others it is welcomed with open arms. But no matter what stance one takes, it would be naïve to assume that we are in no way affected by the fast growing network of social media sites, messaging/photo apps and video sharing sites that undoubtedly encourage the 'always-on culture'. Neil Tweedie (2010) talks in an article in The Telegraph [39] about how we are constantly being distracted on the Internet – describing it as an “electronic sweet shop”. The implications of this are quite dense, implying that the web is a negative force in our lives taking us away from the many things that we should be focusing on - work, education, socialising. It is these things that arguably have caused many people to see the internet as a negative thing in society (see Moral Panics. And of course, being distracted by a sweet shop isn’t however always a good thing and likewise it would not be unfair to say the same for the Internet. Though the web and social media sites can of course lend to positive things, Tweedie is referring to the more sinister effects. These sites, he argues have an immense power to influence our thought process and behaviours. Quite a bold implication, but one that holds truth nonetheless. The creation of the Internet has completely changed our world, and the way in which we do things. To explore this and the internal effects it has on individuals, this section will be split into key concepts with the intention to investigate and analyse these effects.
Web 2.0
[edit | edit source]Terry Flew (2008)[40] states that our modern Internet (named Web 2.0) is solely designed to promote persistent connectivity. We are more active on the Internet and social media sites now more than ever before as a result of this. Of course this 'always on culture' is one of the key things that has changed in our world.
Web 2.0 comes with the development of sites such as Facebook and Twitter, both of which allow for instant and constant communication. Web 2.0 wants the internet to be easy to use, in order to promote the use of social media to people of all ages. Sites are thus designed to be appealing to all in their design and function. Apps like Facebook Messenger have given us the power to be accessible at any given time, which is alluring to a lot of people as they may be too busy in their everyday lives to meet up with friends and family as much as they like, but instant messaging apps give them an alternative. Whereas before we would have had to travel to see someone in person to have a discussion, all we have to do now is pick up our phones. We can have a full conversation with little effort required, and engage in interaction without ever having to leave our house. Because of this, we are now engaging in less and less in person interaction which is argued by many to be bad for ones mental health. Donelan et al (2010: 237)[41] describe Web 2.0 as being primarily "user generated content" (237). Which means that the people are the key creators of what is out there. We can upload our own photos, customise a lot of the sites we use, create blogs and videos and even create our own websites. Is this why we are so driven towards it? The idea that we can do and say what we like, with far less regulation than in real life, and what are the internal repercussions of this?
Rosalyn Carson-DeWitt wrote an article on Everyday Health[42] and argues that being addicted to the internet is entirely possible, and is affecting more and more people as the internet develops. What Carson-DeWitt notes is that people with this addiction are likely to feel socially isolated; and while they may believe that being online will make them feel less alone, it often does the contrary. Looking at Facebook especially, people tend to use the web to show off their lives, primarily with photos. Undoubtedly this can make one feel jealous and unhappy with their own lives, yet they are missing out on things by spending such a huge portion of their time online. These are only some of the small effects that spending too much time on social media can have. Web 2.0 may be interpreted by some as a good thing, however is encouraging greater amounts of time spent online and making it more accessible for people truly the best thing for our society? Some may argue no.
Our 'Mini-Performances'
[edit | edit source]Erving Goffman (who you can read more about in our Goffman's Mask section) was a very influential sociologist who was fascinated with the everyday procedures of human life and furthermore the interactions that we partake in. He argued that the self is a social product. What he meant by this is that our personalities and sense of self are created as a result of the social interactions that we have. Different interactions develop different parts of ourselves and this is also transferred onto social media sites. Goffman proposed the idea that we display different parts of ourselves in different situations/company; we wear masks. Thus we are never fully showing our true self, we can pick and choose different masks to wear depending on how we wish certain people to see us. He referred to this as frontstage and backstage personalities, or the idea of 'I' and 'me'. Which is the concept that we have a true self or a backstage self but this is reserved for ourselves. Our frontstage self is the one that we put on show for others to see. But like any play we can change this, and it may be altered depending on differing audiences. Roberts (2006: 65)[43] comments on this, stating that "the individual presents themselves to others and tries to control the impression that others gain of him or her in acting in their presence". This concept is referred to as 'impression management'. This becomes important to our modern world, as it could be argued that this notion is extremely applicable to the internet and more specifically - social media sites. It is arguable easier to carry out this impression management online, which is perhaps why social media sites hold an appeal for many. The use of uploading photos onto Facebook and Instagram allows us to paint a certain picture of our lives; one that does not necessarily reflect the reality.
An article by Britney Fitzgerald (2013) on The Huffington[44] talks about the way we act on Facebook. She outlines how even though we display our real names (or at least the majority of people do) there is still an, even subconscious, element of anonymity and thus our behaviour changes.
Goffman argues that certain social situations expect different roles and 'faces' from us. There is an element of expectation linked to certain scenarios, we have predetermined ideas and understandings of how we should act. Whilst online, this expectation differs due to the uniqueness in the way that we communicate. Swingle (2016)[45] outlines how the reason for our differing behaviour is due to the fact that social media platforms thwart our ability to read emotions as we would in a face-to-face conversation. In Swingle's (2016: 164) words, "the medium directly promotes narcissism". This can of course be contested, as not everyone who uses social media platforms can be accused of being narcissistic, but it is interesting to consider nonetheless. And, inevitably, there is some truth to the claim as due to how different online communication is to real life communication, it would be ignorant to assume that we act entirely the same in both situations.
The Tethered-Self
[edit | edit source]More can be found on the tethered self in Always On Culture however it is useful to briefly discuss it in relation to internal effects also. The Tethered Self is a concept presented by Sherry Turkle (2011). She states that "each is tethered to a mobile device and to the people and places to which that device serves as a portal" (p.155). So, what Turkle is essentially saying is that we are addicted, or tethered to this online self that we have created. The implications of this are quite large indeed. Turkle (2011: 156) discusses how the creation of the internet and further this notion of the tethered self has changed the way in which we experience life. She relays an anecdote about how a director of a students exchange program explained to her that students were no longer appreciating travel in the way that they should. Instead of experiencing the new culture around them, they would spend their time on Facebook, talking to friends back home.
Rice (2009)[46] states that this notion of the tethered self goes further, claiming that we are so tethered to these social media sites that people are beginning more and more to turn to such sites to help us make decisions, or to ask for advice about our personal lives. Rice (2009 does note that this can be a positive thing, citing James Surowiecki from his book The Wisdom of Crowds (2004),[47] who argues that individuals tend to make better decisions when they are being informed by others, rather than doing so on their own. However Rice goes on to say that there are hugely negative implications from this also, as one may expect. Rice (2009: 145) states that the ""voices" of our invisible entourage can drown out the sound of our own hearts", and goes on to say that looking for others opinions on social media sites the way we do makes it increasingly difficult to know what thoughts actions and feelings belong to us. In other words, we begin to forget our own natural instincts and care more about the way in which others see us and how they think that we should be living our lives. Showing further just how deep the internal effects of the social networking cites can go.
The Google Effect
[edit | edit source]Genevieve Roberts (2015)[48] wrote an article for The Independent that is useful to discuss when looking at this topic. Essentially, she argues that the Google Effect is the idea that we are no longer storing information like we once would, because we feel safe in the knowledge that everything we require an answer to is only a Google search away, treating the Internet as an "extension of our own memory". Our brains are not working as hard to remember information any more as, somewhat subconsciously, we are aware that essentially we do not need to in this modern digital age of ours because we have machines to memorise and store things for us. Many academics are currently worried that this notion is actually making us less intelligent, something mentioned by Roberts (2015). Of course this is not to say that we all treat the internet in this way; but the general consensus by academics is that users of the internet are all affected in some way. Roberts cites Dr Maria Wimber, lecturer at the University of Birmingham's School of Psychology, who argues that the Internet has simply changed the way in which we deal with and store information.
“Google Effects on Memory: Cognitive Consequences of Having Information at Our Fingertips”
In 2011 researchers at Columbia University, University of Wisconsin-Madison and Harvard University published a study in the journal of science. The study “Google Effects on Memory: Cognitive Consequences of Having Information at Our Fingertips” used four different experiments to determine the impact that internet search engines, such as google, may have on our cognitive functions of memory.[49]
The study found that participants who were primed with trivia questions they did not know the answer to were faster in recognising computer based words than non-computer based words - thus showing a desire to fill gaps in knowledge with computerised resources. If participants thought that the computer would save information for them, then they were slightly less likely to remember this information. Moreover, believing that the computer had saved the information for them did not enhance the participants' memory of specific information but it did enhance their memory of where to find the information on the computer at a later date. Overall, the participants' would seem to remember which computer folder the information was stored in rather than the actual content of the folder.
The researchers concluded the study by saying “We are becoming symbiotic with our computer tools, growing into interconnected systems that remember less by knowing information than by knowing where the information can be found.”[50]
Identity and the Internet
[edit | edit source]Turkle talks about the influence of the Internet and social media on peoples identity. She touches on Erik Erikson's stages of development and specifically 'moratorium'. [51] She believes that "connectivity offers new possibilities for experimenting with identity and, particularly in adolescence, the sense of a free space, what w:Erik Erikson called the moratorium. He describes the moratorium as a "psychosocial stage between childhood and adulthood" when the person "re-examines his identity and tries to find out exactly who or she is." [52] Turkle talks about this notion of identity in relation to the internet and claims that "the internet provides new spaces in which we can [experiment with our identity.]" She goes on to say that with the introduction of the web it is not only adolescences that can do this but adults are now also able to experiment with their sense of who they are.
People are now able to do this with the introduction of social media sites with which people are able to create profiles with which they are able to express their interests that they might not feel comfortable expressing in public. These sites allow for the creation of anonymous accounts which allow people to experiment with their identity before they display it to their friends and family. It can be seen as a way of easing people into their new identity until the are certain that they want to commit to that identity.
Moral Panics
[edit | edit source]Not to go into too much detail, but to finish of this section we wish to mention briefly Stanley Cohen's [53] concept of a moral panic as it is arguably relevant here. The definition of moral panics by Cohen (1972: 9) is as follows; “a condition, episode, person or group of persons emerges to become defined as a threat to societal values and interests”. Though contested, many would and have argued that the internet is a threat to society (Krinskey, 2008)[54] The reasons for this have of course been previously outlined within the entirety of this chapter. As with many moral panics, one of the key things that people worry about in relation to the web is the way in which it will affect children, and this is not unjust. In relation to the internet, one of the key worrying points for many people - namely parents - is the thought of online grooming or the easiness for strangers to access information about these young individuals. A quick Google search of "what are the dangers for kids online" brings up a multitude of results a lot of which are tips for young people online. These tips include things like "keep privacy settings as high as possible", "don't post photos of yourself" and "do not talk to people you don't know [55]. Tim Newburn (2013)[56] discusses the moral panic surrounding Paedophiles in the 1990's. This concern has transferred over to the media, as some believe that it makes children more accessible for these people. There have been known cases where these awful things have occurred as a result of young people not being careful enough and ending up in unthinkable situations, Kayleigh Haywood being one of these poor victims[57]. And so we can see that certain moral panics surrounding the internet have credible reason to exist, and we can see from this some of the ways in which the desire to be online across all ages cannot always be a positive thing.
Social Comparison Theory
[edit | edit source]Presented by social psychologist Leon Festinger, Social comparison theory proposes that people obtain – what they understand to be – ‘accurate self-evaluations’ by comparing their opinions and abilities to others and thus gain an understanding of how to rank themselves in these areas. Downward social comparison is defined as looking to an individual or group of people, who you already perceive to be lacking in some regard, to boost your sense of self. In cases of upward social comparison, rather than observe the many differences that make you superior to another person or group of people, you draw the similarities between yourself and someone or a company of people, who you already perceive to be largely better than others. It has been suggested that while downward social comparisons are used to temporarily lift our self-image, upward social comparisons are far more powerful as motivators to achieve or fulfil the roles we deem desirable and successful.
In the context of social media, there is a rampant sense of self-evaluation and examples of both downward and upward social comparison are evident. A Reuters articles on Facebook envy found that:
‘Social interaction was the second most common cause of envy as users could compare how many birthday greetings they received to those of their Facebook friends and how many "likes" or comments were made on photos and postings. . . These feelings of envy were found to prompt some users to boast more about their achievements on the site run by Facebook Inc. to portray themselves in a better light.’ (Goldsmith, 2013) [58]
Facebook offers a unique opportunity to openly judge, critique and criticise – whether privately or in the company of friends – and use these downward social comparisons to deem yourself more popular and thus more successful. Conversely, it allows you to direct these judgements and criticisms at yourself. Either way, these negative emotions, directed at others or yourself, are harmful and detrimental on a deep mental level.
Self Image
[edit | edit source]Social media has become an unprecedented form of currency in the modern world. Perhaps the most valuable is Facebook, as it allows a window into your life that Twitter or Snapchat do not. On Facebook, you have your education and your work, which people use to determine your intelligence and financial standing; you have pictures from parties, holidays, birthdays and weddings, which people use to determine your attractiveness and the activeness and well-roundedness of your social life. The people making these determinations: your childhood friends, school friends, university friends, work friends, holiday friends, night-out friends, your family, potentially your partner’s family and friends, casual acquaintances and absolute strangers. A plethora of people, who sit as an attentive audience and casually judge the stage-show of your life, with no consideration for the time, the labour and consideration demanded to put on such a phenomenal event. What will entertain one section of the audience will not entertain another; what will impress your friends will not impress your family. At least, this is how it is understood to be.
Your sense of self – and most importantly, your sense of self-worth – comes from how you understand others to value you. Suddenly, fifty likes on a profile picture is more valuable to a person than a promotion – although ideally, there would be fifty likes on a status about the promotion as people congratulate you and celebrate how successful a Facebook profile you present, regardless of the reality.
A study revealed that: ‘Becoming self-aware by viewing one's own Facebook profile enhances self-esteem rather than diminishes it. Participants that updated their profiles and viewed their own profiles during the experiment also reported greater self-esteem, which lends additional support to the Hyperpersonal Model. These findings suggest that selective self-presentation in digital media, which leads to intensified relationship formation, also influences impressions of the self.’ [59]
While likes and comments are important to boosting your sense of self-worth, the simple act of maintaining a profile that you are proud of is enough to create positive emotions and thus improve your self-image. Although, is it a simple task to maintain a Facebook profile to be proud of and, consequently, is it a simple task to maintain your self-image on social media?
A separate study conducted among students it was noted that: ‘The multivariate analysis indicated that those who have used Facebook longer agreed more that others were happier, and agreed less that life is fair, and those spending more time on Facebook each week agreed more that others were happier and had better lives. Furthermore, those that included more people whom they did not personally know as their Facebook 'friends' agreed more that others had better lives.’ [60]
External Effects
[edit | edit source]Over the past decade, the development of mobile technology has changed the way in which we interact with people. Gitte Stald describes the changes that have occurred over the past 10 years: "Within a decade, the typical mobile available on the popular market has developed from being a portable telephone to being a handheld computer with enough data and speed capacity to facilitate mobile internet access, MP3 music, photography, video, advanced games and tools such as a calculator, diary, notebook, alarm, clock, GPS and more." [61] These new high quality functions that are now available on the majority of mobile phones may be the reason that most people constantly have their mobile with them. The option to always be connected to the internet is one that allows people to stay connected through not only text and phone calls (which are offline functions) but also through social networking sites even when they are out of the house. Stald describes the common mobile as a "Swiss Army Knife, which holds a number of useful tools - even if people almost always tend to use the same ones." It can be said, however, that there is a difference in the way in which different age groups may use their mobiles - which has been shown further up in this chapter in Social Uses of the internet. These statistics suggest that younger people use the internet on a more frequent basis and use more social media sites. This can be linked back to how each generation grew up. Younger people grew up with technology during their childhood and therefore have a better understanding of how it works and are more likely to use it extensively. Whereas slightly older people did not have the same access to technology as this and therefore are less likely to use it heavily.
A 2006 survey showed that 80% of informants never turned off their mobile phones. While the other 20% of people turned their phones off between 4 and 12 hours per day. I would suggest that since the development of the mobile phone has come so far in the past decade since this survey was conducted that those figures will have grown extensively. This constant connection, not only to other people, but to the Web means that we are never truly 'offline'. One 19 year old girl that had been interviewed during the process of this study talked about switching off her phone to de-stress but also commented "I can't be without it for too long. What if I miss something." Stald describes "missing something" as referring to the constant updating of the social network. This means that with this fear of missing out, young people today have no or few communication and information-free moments. People are often contactable right up until they go to sleep and as soon as they wake up in the morning which puts a continuing pressure of these people to reply and remain available throughout the day.
With this constant connectivity right up until we go to bed can have harmful effects on our sleeping pattern as well. "The blue light emitted by screens on cell phones, computers, tablets, and televisions restrain the production of melatonin, the hormone that controls your sleep/wake cycle or circadian rhythm. Reducing melatonin makes it harder to fall and stay asleep." [62] With the majority of people claiming that they never switch their phones off, it is concerning that our levels of sleep may be reducing as a generation due to our high levels of technology usage. This is something that can be can be linked to McLuhan's theory Technological Determinism which suggests that technology shapes the way society functions - which I talk about in more detail in the section "being 'Pausable'". I think this change in sleeping patterns throughout this generation, suggests that McLuhan's theories are credible in that some things about our society have changed due to technology. And the introduction of mobile technology is not the first time we see this. Technology shaping our society can be traced all the way back to the invention of the wheel or the light bulb. Significant changes such as these ones are what shape our society.
Being 'Pausable'
[edit | edit source]The fact that people nowadays always have their mobiles with them creates this notion that people are "pausable". [63] The ways in which our social interactions work now is that we pay more attention to our phones than the person talking to us - something that has changed since developed mobile phones have emerged. Turkle states that "our face to face conversations are routinely interrupted by incoming calls and text messages." The distraction of our phones constantly being with us means that people fade in and out of conversations only catching parts which means that our full attention is no longer on the person we are with but spilt between to modes of communication. This is an point that has been suggested by many media researchers but why is it that people now believe they can put the face to face interaction they are having on pause in order to answer their mobile. An 18 year old boy, that Turkle talked to, claimed that his friends are now "so used to giving their phones all the attention... they forget that people are still there to give attention to." This kind of interaction means that our face to face interactions no longer mean as much as they might have before.
There are a few ways that theorists look at this. Marshall McLuhan believes that technology is an extension of the human body, he believes that big cultural shifts are determined by the changes in technology which is a theory called Technological Determinism. He said that there are "personal and social consequences of any medium - that is, of any extension of ourselves - result from the new scale that is introduced into our affairs by each extension." [64] In this, we can link back to how we are now "pausable" due to the changes within technology as McLuhan suggests that new technology often changes the ways in which we interact with people and do every day tasks. With the constant fear of missing out and the need to be connected all the time are we then missing out on actual experiences? Due to these technological advances we now experience our lives in a different way than we would have before. The increase in photography with mobile devices is one way in which our experiences have changed majorly. For example, when people go to a concert nowadays, people feel the need to film every second of the concert and therefore does this mean that our experiences of the concert are no longer as meaningful as before as we are watching them through our phones or cameras and not experiencing it in full. We put our whole lives 'on pause' just so that we can keep up to date or perhaps even keep other people up to date.
This is then counterbalanced by the views of Raymond Williams who believes that technology is not an extension of ourselves but the social context in which we use technology actually determines what we make of it, he believes that our social interactions throughout history shape the ways in which we have used technology. This is called Cultural Determinism With this, Williams flips the idea that technology is actually shaped by the needs and wants of the society that we live in. Williams also delves into the fact that the intention of technology can often differ from the actual use of it. Mobile phones are a major development in technology that has changed the ways in which we function as a society which can be linked to both of Williams notions here. The extensive use of mobile phones in our every day life has changed our social interactions and demean the relationships that we have with one another due to a overwhelming use of technology instead of face-to-face interactions. It can also be said that mobiles are now used for things other than their intended use as they were created in order to boost communication which made it easier to be contacted but in contrast it can be said that mobiles often take away from our communication and often isolate us due to our overuse of our devices instead of real interactions.
New Boundaries
[edit | edit source]Papacharissi talks about the "uncoupling of space and time" within the changes of social interactions. [65] He means to say that we can live our lives in any time and space that we wish but all from the comfort of our own homes. We "no longer require the traversing of temporal and geographical boundaries." Which means to say that our use of the web has now extended not only for information gathering but to fully living our lives through the internet. This is something that can be seen through the introduction of not only social media sites which allow communication but also with the introduction of dating websites and apps such as Tinder. The introduction of this to our online environment means that even less face-to-face interactions are necessary in order to live a normal life with normal relationships - but they are now online relationships.
The ways in which we use the internet in our every day life "results in transforming the private sphere of the home into a space that is both public and private." Due to the widespread use of social media there appears to be a new norm in how much we share with people. On social media, it may be easy to forget how many people are able to access what we are posting which means that people are more likely to post more personal things. The line between our public and private lives is becoming more blurred in that the things that people would have shared only with their close family and friends, before the introduction of social media, is now shared with everyone on their friends list - and potentially more than this depending on privacy settings. This persistent connectivity that has been created by these platforms means that there appears to be no secrets about what people are doing.
Mobile Privatization
[edit | edit source]Raymond Williams came up with the term mobile privatization as a part of his "criticism of the failings of technological determinism and its role in the accounts of media history." [66] w:Mobile privatization is one way in which theorists describe the attachment that people have to their mobile devices. And although this term was made before modern mobile phones, it can be strongly linked to the uses of modern mobile phones. The theory suggests that people's mobile devices give them a feeling of security and being "at home". It can be said that because we are "always on" it means that we could travel anywhere and still feel comfortable due to the connectivity of their mobiles. This means to say that we do not need four walls and a roof over our heads to feel at home because we are now able to carry our homes with us. This is a notion that can be linked back to Stald's idea that "the meaning of the mobile goes beyond its practical function."
Online Presentation
[edit | edit source]
There are different reasons that we might post our lives online. The reasons can, of course, be linked to identity as I have talked about before with finding identity through online experiences and sharing in the internal effects section. But there are other reasons such as to preserve memories and therefore look back on. But is this idea still valid in this day and age? Mendelson and Papacharissi talk about the use of photos on social media and question "if photos are taken for the purpose of being displayed and tagged, does this render the experiences and the social relationships presented more real?" [67] This is a contentious question as it suggests that the snapshots we take now are more real, but does the selfie truly capture a memory in the same way that a photograph may have done before the introduction of the selfie craze. It can be said that the way that photos are taken now is too staged which takes away from the way in which it works as a time capsule. If someones social media site is full of pictures of only themselves (and their face only) then what purpose does this serve? Stald describes the "mobile as a personal log for activities networks, and the documentation of experiences" which means to say that we use our mobiles to capture moments and then relive them through the photographs and the memories that we have saved onto our mobile devices.
Mendelson and Papacharissi suggest that "people are able to post only that information which presents a desired image." The way in which we present ourself may not be in line with the way we are in reality and therefore we are able to construct a new identity that we present to the people online. The pair compare online presentation to the ways in which we present ourself in real life: "In everyday life, people consciously and unconsciously work to define the way they are perceived, hoping to engender positive impressions of themselves. This effort entails emphasizing certain characteristics, through dress, hairstyle, behavior and/or speech, while hiding or diminishing other characteristics perceived as flawed, depending on context." The way in which they describe the ways people try to present themselves in reality can be likened to the ways we try to present ourselves in the best light online as well. However, there is one key difference in that flaws are able to slip through in real life whereas online people are able to edit their flaws and delete anything that they do not want online (although this does not necessarily mean that the photos or status is gone forever as once they are online, they are often never truly offline.)
Fear of Missing Out
[edit | edit source]The 'Fear of Missing Out' or the FOMO can be defined as a feeling of uneasiness that a person might get with regards to the idea that they are missing out on social experiences that other people might be having. It is fueled by an eagerness to be constantly up to date with what others might be experiencing. In the current day, social media platforms provide us with unlimited methods of engaging with others online. People are scared that if they are not constantly active online then they will be missing out on vital social interactions. This causes them to experience a negative feelings when they see other people posting on social media. They believe that the other person is having more fulfilling life experiences than them and this can cause a feeling of low self-worth. Thus resulting in an overwhelming urge to stay socially connected to people via social media and technology. You can read more about the fear of missing out in relation to privacy in Living in a Connected World/Technology as an Extension of Self. of the book.
The history of FOMO
[edit | edit source]In June 2013 a Wikipedia page was created explaining the phenomenon of The Fear of Missing Out (FOMO). FOMO was described on the page as a form of social anxiety which was caused by being overly active on social media. The page also discussed a study by social psychologist Andrew Przybylski (2013). The study was concerned with why people used social media, and it found that some used it more due to unfulfilled psychological needs. This was the first time that FOMO was recognised by academic research - it had previously trended on social media and been referred to in news articles but this was seen as a lighthearted phrase.
Although 2013 was when FoMO was recognised as an academic term, it's origins date back to 2004. A Harvard Business student, Patrick McGinnis, wrote a comic story for the school newspaper in 2004 in which he spoke about the suffering of students. He identified that people would rather over fill their evenings with a variety of events that they couldn't possibly attend than feel like they were missing out on something. He wrote that this in turn led to a drunken email at three in the morning to an abandoned friend: “Sorry I missed your 80’s theme party at Felt—you know that you are totally in my top 15.” The concept managed to circle its way around Harvard until it gained momentum. [68]
After the term had been circulating for a while it's popularity increased. In 2007 a Business Week article addressed the term saying that the epidemic was 'catching on everywhere'. Then by March The Guardian had added the word into it's glossary of Youth internet slang. By this point it seemed like everyone was talking about FoMO and at a time where Facebook was rapidly growing the concept was getting more and more relatable. In April 2011,FoMO became the Urban Dictionary's most searched for word of the day(Dossey,2014) Finally, the following year FoMO became official with the Oxford Dictionary(2012) recognising the word as the “Anxiety that an exciting or interesting event may currently be happening elsewhere, often aroused by posts seen on a social media website.” [69]
The need to belong
[edit | edit source]The history in regards to FoMO and social media may only be traced back to 2004 but it is important to note that the concept of the fear of missing out has been around for a lot longer. We can see this from phrases such as 'keeping up with the joneses', people have been trying to fit in and out do each other so they don't feel like they are missing out for a long time. There are previous theories that deal with why humans experience certain emotions if they feel left out. FoMO can be understood as the need to belong somewhere whether it may be a social group, an online community or the wider world.
Mark Leary and Roy Baumeister wrote a paper on 'The need tɒ Belong' in 1995. The paper hypothesises that as human beings our fundamental motivation is to belong. The study speaks of our drive to form long lasting and successful relationships with our people - it is simply in our nature to attempt to bond with others. In order to for us to satisfy our need to bond, Leary and Baumeister say that there are two steps. First, we need to frequently interact with others but these interactions must be pleasant and around other people. Secondly, the interactions must be stable with a mutual concern for the others well being. The study also points out how easy it is to form social bonds and how we can form attachments with rivals or opponents because of our inclination to create relationships. Although it easy to form these relationships, it is much harder to break them. For example, when training groups are formed the group members know that the meeting will eventually stop. Even when the group purpose has been fulfilled members try their hardest to hold onto the social bond that they have formed with each other. They then promise to stay in touch and have reunions but the reality is that this barely happens. [70]
They found that when the relationships began to break down an individual's mental health as well as physical health and general well-being deteriorated. The effects of broken bonds were all negative and impacted poorly on the individual. The need to belong relates to the concept of FoMO as the need to feel like you belong somewhere relates to the same feeling people get in regards to social media. People want to belong to their social media platforms and form bonds with their 'friends' and 'followers'
The effects of FoMO are very similar to those experienced from the need to belong, both result in the individual experiencing negative emotions. These emotions amplify when the individual feels they are missing out on something others are partaking in - maybe a social gathering their friends. They then begin to fear that the have missed out by not being at this social gathering thus resulting in a surge of emotions that leads to the individual feeling like they do not 'belong' to their social cohort anymore.
Previous studies
[edit | edit source]Motivational, emotional, and behavioral correlates of fear of missing out.
An article which is concerned with the phenomenon of the fear of missing out is Motivational, emotional, and behavioral correlates of fear of missing out. In this, three studies are carried out in order to obtain a better understanding of the subject. The first study used an international sample to create a measure of individual uniqueness measure and introduces a FoMO scale. The second study investigated how motivational and well-being factors relate to the fear of missing out. Lastly, the third study suggested a correlation between behavior and emotional needs and the fear of missing out. The article considers FoMO from a psychological needs perspectives. The self-determination theory considers human motivation and it is a useful perspective in understanding FoMO. According to the self-determination theory mental health and self-regulation heavily depend on the three standard psychological needs. First is competence, one must be able to make changes to the world. Second is autonomy- one must be able to think for themselves and make independent decisions. Lastly, we have relatedness - a connection with other people is essential.
This theory is often referred to as basic need satisfaction and it can be related to the fear of missing out. In order to achieve high need satisfaction, an individual is inclined to use social media persistently as a way of connecting with others. Low levels of basic need satisfaction(BNS) can relate to FoMO and engagement on social media sites in two ways. Individuals who have low levels of BNS may use social media because it can be seen as a resource to communicate with people, a tool to develop social competence and an opportunity to create lasting social ties - this is a direct link. The link could also be indirect, this being that FoMO could serve as a mediator link in relation to psychological needs and social media engagement.
The study found that young people, particularly males, tended to report higher levels of FoMO - there was no gender difference among older participants. The results also indicated that those with a high FoMO reported more instances of negative moods and lower overall life satisfaction. Some of the research also focused on University students - it was found that those with high levels of FoMO were more likely to log into facebook during a university lecture. Furthermore, young adults who experienced high levels of FoMO were more likely to pay attention to emails, texts and their mobile phones while driving than those with lower levels of FoMO.[71]
The relationship between FoMO, alcohol use, and alcohol-related consequences in college students
In 2014 the Otago Department of Psychology, New Zealand, conducted a study on alcohol, university studnets and the fear of missing out. 432 students took part in two psychometric tests to measure their FoMO level and completed a brief Young Adult Alcohol Consequences Questionnaire. In the questionnaire the amount of negative alcohol-related experiences in the past 3 months were reported. In study one, alcohol was measured retrospectively and in study two it was measured prospectively using a 13-day internet diary.
In study one, the amount of drinks consumed per week was measured by the survey. Students were asked to "Think of a typical week in the last 30 days for you. Think of what you did, where you lived, what your weekly activities were. Try to accurately remember how much alcohol you typically drank." [72] From the results, 3 measures of alcohol use were measured: weekly drinking, drinking frequency and drinking quantity.
In the second study, the number of drinks that the participant consumed was measured by a daily diary. For 13 days participants had to report the number of alcoholic drinks they had the night before. The previous nights drinking was assessed as the diary was only available from 3 pm - 8 pm, this was a measure to reduce the risk of intoxication while completing the survey. This was then calculated against the three measures of alcohol use used in study one.
Across both studies it was found that FoMO was significantly related to an increase in negative alcohol related experiences. Participants who were more likely to experience the fear of missing out reported double the amount of negative alchohol relatd incidents than those who were less likely to experience the fear of missing out. There was also a significant link found between FoMO and the quantity of alcohol consumed by students.[73]
Facebook and FoMO
[edit | edit source]With 1.79 billion users, Facebook is one of the most popular social networking sites in the world. In the last decade, the popularity of social media surged and networking sites became pivotal in how we communicate. Facebook and other social media sites allow us to communicate frequently with other users at the touch of a button. Not only can we be in frequent contact with someone who is half the world away but we can check up on our friends 24/7 - this means we are always up to date on their lives.
Research conducted by Psychology Today found that there is a link between FoMO, Facebook and negative consequences. 76 Irish University students participated in the study which included four collective intelligence sessions. The study found that “Increased dissatisfaction with one's life" and a "Decrease in Privacy” was the primary consequence of FoMO in relation to Facebook. These consequences both contributed directly to a “Poorer self-image” at the second stage of the study and a “Decrease in concentration” at the fourth stage. Other consequences that they found were an increased dissatisfaction with ones life, feelings of jealousy in relation to friends and an increased tendency to neglect basic needs. [74]
Researchers at the University of Missouri also discovered that there is a link between Facebook and depression - this is caused by feelings of FoMO. They found that when others post about new cars/houses, happy relationships or expensive holidays, this evokes feelings of envy among other users. If users are envying the lifestyle and activities of their family and friends then they start to fear that their life is less meaningful, these users are much more likely to report feelings of depression. [75]
Another study also found that those who experienced high levels of FoMO tended to use Facebook as soon as they woke up, during meals and before going to sleep.[76] Further information on this study can be found in the above section "previous studies".
Goffman's Mask
[edit | edit source]Erving Goffman
[edit | edit source]Erving Goffman was a Canadian-American sociologist and was considered one of the most influential of the twentieth century. Many of his concepts relate to our topic of living in a connected world. When looking at the themes of persistent connectivity and the fear of missing out, it is important to regard some of Goffman's work, as he explains how society can act in a world reliant on the internet.
In 1959, Erving Goffman's book entitled 'The Presentation of Self in Everyday Life' was published. This focuses on how people can change the way they act, or want to appear in different scenarios. However, it is important today to use these theories to link with the online world as well as the 'real life' world.
Later on, Goffman wrote other books, which refer specifically to human interactions and the affect of these. His later work, including 'Stigma' [77] and 'Interaction Ritual' [78] showed how different types of people can be analysed to show the behaviour we tend to encounter. A high percentage of human interaction these days takes place online, on various platforms, and this could be a reason in which many of us have a 'fear of missing out'. While we can meet up with people in groups, we cannot predict the online interactions, which many people want to be a part of.
Erving Goffman has also written an article called 'Where The Action Is'[79], which describes occasions where people congregate to do something. In modern times, these places where many people can connect in one place is best found online. With the internet connecting people globally, many things are arranged, discussed and shared online and can result in a lot of persistent connectivity.
In the work Goffman produced, particularly 'The Presentation of Self in Everyday Life', he analyses interpersonal interactions- an important use of internet connectivity. While he was writing in a time where the internet was not a factor, the theories he discussed were comparatively unexplored areas of thought. One theory in particular, about the different 'masks' and personas we wear in different situations can be related to our online identities, and how this shows in our persistent connectivity. [80]
Goffman's Theory
[edit | edit source]Erving Goffman’s theory states that there are two personas when it comes to the persistent connectivity on the internet; the ‘I’ persona and the ‘Me’ persona.
The ‘I’ is always present in some way but is usually backstage, behind the mask in front. The mask shows the ‘Me’ persona and is influenced by the persona behind it. The ‘Me’ persona shows how the person wants to be seen and means that some parts of the ‘I’ persona can be hidden behind the mask. Only certain characteristics, or parts of their life, are shown. The ‘Me’ persona may be seen as the one engaging in persistent connectivity as people get to ‘know’ this persona based on online activities. Meanwhile, the ‘I’ persona may be the one related to the fear of missing out. This is more to do with the refreshing of pages, and looking at other profiles. This persona is not presented as much online but is often presented to.
“While in the presence of others, the individual typically infuses his activity with signs which dramatically highlight and portray confirmatory facts that might otherwise remain unapparent or obscure”

These types of strategies emerge depending on front and back stage settings and are determined by the anticipated mannerisms expected. While people acting on stage put on a character and are aware of the many people they are exposed to, that same person can change persona very quickly as soon as they go backstage. They no longer need to put on a show or present to anybody and they can simply be themselves. Goffman refers to this in his work and it helps to understand some of the reasons why our persistent connectivity is not always an 100% accurate representation of ourselves. [82]
The theory of Goffman’s mask leads to many questions about how the persistent connectivity and the fear of missing out can cause us create an image of what we ‘should’ be like online. If we connect too much and observe the way other people present themselves online, gradually a social norm is created and people try to impress others with pictures and comments that others would like. Often this is purely for the likes or the interest, to gain a feeling of self-worth. People can often use the acceptance of their ‘Me’ persona, to feel better about their ‘I’ persona, as they appreciate some sort of connection between the two. In some ways, the mask becomes a conception of the identity we have formed for ourselves online. We strive to become this persona, and if we believe this online persona looks good we can end up trying to live up to this character we have presented. “This mask is our truer self, the self we would like to be”. [83]
Fitting In Online
[edit | edit source]While Goffman speaks of these masks also being used in real life when we come across different situations and have to act accordingly, these masks are more easily used online. This may be due to the fact that people can look at us at any time when online, by simply searching our name into a search bar.
Although people can see images of others, and sometimes even live videos, when judging a person online you are never looking at them in real life.

Almost everything has been censored by the person, as they have uploaded these pictures, videos or text and know that they will be viewed by certain people on certain platforms. This makes it easier to create new masks and try to fit in, adapting the 'I' persona, to a newer one which is maybe deemed to be better in some way.
Goffman states that “When interactions migrate online, the interacting parties meet in time rather than in a place”. [84] This is an important factor to consider when debating the ability to adapt and fit in online. You are able to interact with people from anywhere, and you do not have to even make conversation with someone to get to know what they are like online. Many pages online are open to interaction and you are able to see what someone was doing without having to be in that place. With over half of the world's population using the internet today,[85] we are able to view many other profiles before deciding what ours "should" be like.
Masks for Different Platforms
[edit | edit source]On different platforms, we are able to put on different masks to enhance some of our characteristics, matching the general characteristics of users of the site we are on. An example may be that on Twitter, the majority of accounts seem to be open for anybody to come across, and so users may bear this in mind when deciding how to portray themselves through the words they use. More time will be taken to take into account the language used, with the word limit sometimes taking an effect on choices.
On platforms such as Snapchat, people filter their lives and broadcast what they think is the most exciting. These updates are available to a much smaller audience and they do not remain on the site, so the time taken to choose a mask is lessened. There is less thought about what is said and more thought about the kind of life people want to show their 'Me' persona to have.
A very different form of online identity is created when people engage in gaming online. While on other social media sites the images that represent people are usually photographs taken at a particular point in time, on Gaming sites, avatars are often made. It may be argued that this is not a direct representation of the person, but the argument still stands that this is the picture that goes with the character the individual has created. This is another of the masks which Goffman writes about. On some online games, the people become absorbed in the game and the adrenaline keeps people playing. As a form of escapism, gaming online often creates persistent connectivity but in a different sense. In this connectivity, the players often enjoy the life they have created virtually.[86] Connecting to this online provides an alternative life to live, and can show how life online and in real life (irl) are separate. It focuses the idea that we can be entirely different online and offline.
Goffman has often referred to the need to 'juggle' masks in life, and this is widely seen across the various online accounts of most users of the internet. No social media site is used for the same purpose, and so there are often different aspects of people's lives are scattered across a variety of pages. This means that when looking at someone on two different sites, it could appear to be like looking at two slightly different people; in actual fact they have just altered their mask.
References
[edit | edit source]
| This page or section is an undeveloped draft or outline. You can help to develop the work, or you can ask for assistance in the project room. |
Technology as an Extension of Self
[edit | edit source]Introduction
[edit | edit source]igital technology, as we have always known it, has been humanity’s outlet for communication. As the technology we have created, over time, has slowly started to replace the need for face-to-face communication, humanity has begun to live with digital technology beyond terms of mere association. We have entered a fixed relationship with it; whereby today, we are represented, judged, assessed and manipulated – by both ourselves and others – online, through the use of multiple platforms on multiple devices. We don’t go a day without checking our own personal screens for messages, notifications, texts – updates of all kinds. We are fixated, caught in a storm which has only just begun its journey and shows no sign of clearing up, or slowing down.
There has been much discussion and research into the complicated, intrinsic relationship between technology and humanity, specifically in terms of how we are becoming, as it were, part of the machine we originally created. This chapter will explore, in association with relevant theories, the discussion points surrounding the relationship between humanity and technology and will help to define the notions of past, present and future technologies and how they are becoming (if they have not become already) an extension of ourselves.
Theorists
[edit | edit source]Jaron Lanier
[edit | edit source]
Jaron Lanier is a computer and technology theorist. His philosophies are critical of humanity’s relationship with computers, as he demonstrates the ways in which technology has negatively affected certain elements of human experience and interaction. Lanier believes that technology is an extension of ourselves, but puts forward a further debate that technology is turning humans into machines. In Lanier’s Missing persons, IN: You are not a gadget: a manifesto, he warns that technology could become the self, rather than an extension of the self [87] Lanier proposes that there should be an effort among those with the power and money to change technology to enhance humanism over technology. He believes there is an opposition between technology and humankind, rather than a stable and healthy equilibrium.
In Jaron Lanier’s article, Digital Maoism : The Hazards of the New Online Collectivism[88], he highlights how dangerous online collectivism can be. An example of this is how he talks about how you necessarily aren’t in control of what you are known for online as he talks about the fact on his Wikipedia page he is classed as a filmmaker, despite only having made one film in the past – “… I made one experimental short film about a decade and a half ago.” “I have attempted to retire from directing films in the alternate universe that is the Wikipedia.” This is a good example how people are usually known online on a first impression basis. It doesn’t matter what you have done since then, no matter how different it is from what you have gained a reputation for. That one action defines you. This is reflected in how Lanier explains how the collective is basically one being – “Reading a Wikipedia entry is like reading the bible closely. There are faint traces of the voices of various anonymous authors and editors, though it is impossible to be sure.” Following this point Lanier talks about how new online collectivism and the band wagon effect relate to each other, “…nothing less than a resurgence of the idea that the collective is all-wise, that it is desirable to have influence…” This idea relates especially to how humans are social creatures that aspire to be part of a group, to belong. He also points out how that context is everything and that notoriety of the website in question can change the intention of information provided, “If an ironic web site devoted to destroying cinema claimed that I was a filmmaker, it would suddenly make sense.”

Marshall McLuhan
[edit | edit source]Herbert Marshall McLuhan was a Canadian philosopher and intellectual who wrote extensively on the topic of media technology. He was active in mostly in the 1960s and 70s so his work is entirely pre-internet as he passed away in 1980. Despite this, the views and ideas McLuhan put forward are relevant to discussions on digital media today. McLuhan wrote several books on the subject of media relating heavily to the way in which media works with technology as well as technological determinism. In his 1964 book Understanding Media: the extensions of man[89], McLuhan talks about various technologies and how they relate to both extending ourselves and society as a whole. McLuhan believed that technology has a direct role in defining and shaping the societal group of any time which is the main concept behind technological determinism. McLuhan's views have been seen as controversial as other views conflicting with his have been established, this includes cultural determinism which outlines the idea that society affects the technological changes rather than the technological explanation.
Jill Walker Rettberg
[edit | edit source]Jill Walker Rettberg is a professor of Digital Culture at the University of Bergen in Norway. She published Seeing Ourselves Through Technology, a book that explores self-representation through the use of technology. She studies the way we represent ourselves, looking at three modes of self representation (written, visual and quantitative), studying how various ways of self representation work along side digital technology. She discusses the 'pre-digital' history of each mode, how current methods of self-representation have evolved. In Rettberg's book "Seeing Ourselves Through Technology"[90], she discusses the use of selfies, and how the takers of these selfies have complete control over the finished image. She compares the modern day selfie to Suzanne Szuc's gallery of images which is comprised of 5475 photos, a photo each day for 15 years. These images followed Szuc through all aspects of her life, ranging from emotional turmoil, to light hearted images such as ones with her tongue sticking out. Rettberg comments on the similarities between Szuc's project, and modern-day photo sharing platforms such as Instagram.
Erika D'Amico
[edit | edit source]Erika D’Amico is a researcher at the University of Urbino, Italy. She specialises in the study of images within social media, looking particularly at the socio-economic structures of social media platforms. D’Amico wrote “The Elements of Libidinal Economy in Instagram: A New Ontological Status of Photography”. In this paper she explores the connotations of certain styles of photography, looking at aesthetic, relationships within images, and the impact of uploading certain types of images to online platforms. Instagram is the key focus of the paper, with D’Amico exploring the relationship between the creator and uploader of images, and the audiences that then view them.
She believes that Instagram and other photo sharing platforms are anchored by a three-step process. The first step is to let others “recognize the experience you are living through images”[91] meaning that it is your duty to create the most accurate portrayal of the experience as you can. The second step is to “use a hashtag as a sort of call to action and (to) get more visibility”.[92] She argues that the use of hashtags allows for images which would normally be swept under the digital rug, along with thousands of others, to be recognised for their merit. The third step involves “matching my shot to some specific filters”.[93] She states that in order to get the best audience for the image the uploader needs to upload it with appropriate tags and filters.
Zizi Papacharissi
[edit | edit source]Zizi Papacharissi is a communication scholar. She has a PHD in communication studies. Her works mainly concentrate on the consequences of new media and technologies on society. She edited the collection of A Networked Self: Identity, Community and Culture on Social Networks Sites, which we studied for this module. In it, she wrote a chapter with Andrew L. Mendelson about the narcissism that comes with posting pictures on social media especially for college students and young adults. She focuses on observing the different ways people posts pictures, their social meaning but also focuses on the differences in photos posted by men and women. In her books, she prefers to write about the changes brought by the use of technologies in our society. She writes about the consequences of those technologies and social medias on our social and political engagement. In A Networked Self, she examines how social connections are made in a time where everything is online. It explores the consequences of having an entire identity online and only online since nowadays people prefer to only present themselves online and use their social networks as an extension of their identities.
Sherry Turkle
[edit | edit source]Sherry Turkle is a professor of social psychology at the Massachusetts Institute of Technology. She is also a founder and the director of the MIT Initiative on Technology and Self. Sherry Turkle received a joint doctorate from Harvard University in sociology and personality psychology. Professor Turtle explores the relationship people have with technology and analyses how it affects human behaviour. She studies how human connection and communication is redefined by electronic devices and social networking. Since publishing her book The Second Self: Computers and The Human Spirit in 1984, Sherry Turkle has been exploring how technology changes our lives and how it affects our identity. In her work Alone Together (2011) and Life on the Screen, The Second Self (2005) she sets the questions about human isolation and connectivity in a technology dominated world. She also explores the notion of the ‘tethered self’ - the new human identity that has been built in close connection with technology. In academic environments professor Turkle is known as "the Margaret Mead of digital culture” and in her studies she mainly focuses on the technologies that she calls “the architects of our intimacy”, such as social media, chatbots, sociable robots and digital workplaces. She suggests that there is still time for humanity to analyse and rebuild our approach to digital technology as it is still relatively new. Sherry Turkle’s work allows readers to look at people’s relationships with technology from a new, fresh perspective.
Adrian Athique
[edit | edit source]Adrian Athique is an Associate Professor in Cultural Studies at the University of Queensland in Australia. He specialises in media studies and has written multiple articles and chapters as well as world leading textbooks on our association and relationship with online platforms. He is fascinated by psychosocial relations and defines in his own words - in his 2013 textbook [94] his theory of the "I" (the subject of ourselves) and the "Me" (our public persona) in relation to human interactions with Social Networking Sites (SNS). Athique has a specific interest not only in SNS but in the relationship between human interaction in real life and virtual interaction and sociologically, the impact that is having on society. His interest in so called, New Media, (and his criticism of the term) relating to the constant convergence of current media forms partnered with a look at how humanity came to not only accept digital technology but arguably thrive with it in use in their daily lives provides an interesting look at the social norms of present.

Raymond Williams
[edit | edit source]Raymond Williams was a theorist and critic who focused his interests and writings on culture, was an influential member of the New Leftand paved the way for the beginning of cultural studies. His book ‘Television, Technology and Cultural Form’ (1974) focused on the power relations between humans and technology [95] Williams discussed cultural determinism as a theory to counter technological determinism. He therefore proposed that humans had power over technology because technology was created, used and adapted according to pre-existing human desires in social groups. He further argued that different groups may use the same technology for different things, depending on their different needs and intentions.
History
[edit | edit source]Self-Representation
[edit | edit source]
Pre-Digital History
Self-representation is how we see each other, and ourselves. It allows us to make sense of the world we live in. How we use technology, as a form of self-representation, as an extension of self, is a concept not foreign but a universal practice that dates back thousands of years. Jill Walker Rettberg discusses the ‘pre-digital’ history in her paper, “Seeing Ourselves Through Technology”. She argues that past methods have evolved into the current digital methods of self-representation.[96]
Prehistoric cave paintings, discovered all over the world have given us a glimpse into the lives of early humans, showing us how they saw the world they lived in- depicting great animals like bison, lions and horses. Humans are rarely seen in the paintings, represented mainly as hands that have been stencilled. The meaning behind cave paintings is debated but it is argued that they could have played a role in religious ceremonies. Religion can be viewed as an extension of self; your beliefs and practices influence your actions, how you dress and speak and ultimately how people see you.
You could view Facebook profiles like a cave wall, ‘painted’ for religious purposes. Everyone decorates their Facebook wall with their interests and their beliefs. Their practices and aims influence what goes on their wall, to gain ‘likes’ or to connect with individuals who have similar beliefs and interests.
Figurines and statues are key examples of self-representation from a pre-digital time. If you look at the discovery of Venus of Hohle Fels, a figurine of a woman that dates back over 35,000 years ago, you can see how body image is portrayed. Researchers, Alan F. Dixson and Barnaby J. Dixson discuss ‘Venus figurines’ in great detail in their article, "Venus Figurines of European Paleolithic: Symbols of Fertility and Attractiveness?" The article states that the figurines could reflect the individual styles and preferences of those who made them. However, ‘it is challenged that they may have been crafted by women, who were making images of their own bodies.’ This idea of self-representation can be seen today, through the use of filters and other camera techniques- women and/or men can create images that reflect their own styles and preferences or create something that they believe depicts their own bodies.
Masks used in ancient Greek theatre displayed characteristics and exaggerated emotions in order to create a reaction in an audience. They also allowed an actor to take on many different roles without being recognised. These ancient masks could be compared to the modern day selfie because it shows only what the subject wants its audience to see (a certain characteristic or emotion).
Self-portraits are another example of self-representation that can be linked to selfies and visual social media platforms, like instagram. Frida Kahol (1907-1954) was a Mexican painter known for her self-portraits. Her painting, The Two Fridas (1939) shows two versions of herself, sitting side by side. Both versions have their hearts exposed; one dressed in white appears to have cut her heart open with scissors, blood spilling onto her dress. The other version is dressed in warm colours and her heart appears strong, a rich red. The Two Fridas is an extension of self, how Frida saw herself- it is said that the painting depicts the unloved and loved Frida. In comparison to how individuals represent themselves online, it could be argued that they are doing just the same thing as Frida: pictures on instagram accounts depict the reality that individuals want people to see. The same can be said for profile pictures (they represent the reality of the individual).
Technology
[edit | edit source]Ideas relating to technology and the extension on self, pre-date our digital world by many years. As far back as the 1960s, long before the development of the internet, Marshall McLuhan was writing about the extensions of man in his book Understanding media. McLuhan outlines several key ideas relating to technology and mankind being closely related to one another. McLuhan also outlines several aspects of technology that directly relate to our senses including film, motorcars and telephone as well as others.
Transport
[edit | edit source]Transportation relates heavily to elements of the extension of self. Transport gives the individual freedom by removing their restricted movement. In terms of extension, in a literal sense, it can be said that the wheel extends the leg so therefore does the car. It is evident even in contemporary society, and McLuhan’s in 1964, that the motorcar is a status symbol. The car is often seen as representative of self although today the focus seems to have shifted to the caliber of vehicle rather than simply owning one. McLuhan feels like the view of cars as status symbols is misplaced as he says it ignores the equal ability cars provide. In Understanding Media, he describes the idea that despite race, age or background, cars provide the same extension for each of us. This may have been applicable to the internet when internet enabled devices were hard to come by, however as such devices have become far more commonplace, the freedom it provides is far more noted than any status symbolic qualities.

Film
[edit | edit source]The development of film technology allows for illustrations of self-extension in various ways. In the UK, early cinemas were known as Bioscopes which derives from the Greek word bios meaning life. This relates to the idea that films capture life and allow audiences to connect with that. The mechanical technology provides content that is organic in appearance, allowing the connection to real life, organic experiences to be formed. On the side of the creator, the film allows for a portrayal of the mind or an extension of the self. To understand the way in which film falls in to the history of self-extension, we should look at the way in which print is very similar. According to McLuhan, Miguel de Cervantes (author of Don Quixote) would have seen print as we see film. The new technology usurps the old in providing new, easier, more interesting ways to further society. Marshal McLuhan uses the terms “Hot and Cool” when referring to media. Hot media are those which extend a single sense whilst conveying large quantities of information with little effort and cold media are those which convey little information. In the case of film, it is a hot medium as uses vision to provide a range of data easily interpreted by the viewer. A criticism of Mcluhan’s work on film is that he views film audiences as passive. In her 1997 book, Shocking Entertainment: viewer response to violent movies [97], Annette Hill paints a different picture when she talks about violence effects of media as she talks about the audience being active in the way they consume and interpret violence and by extension film in general.

Communication
[edit | edit source]Electrical communication has played a very extensive role in shaping the current way in which our society functions. Electric communications such as the telegraph and the telephone extend speech in a way which postage and non-electric communications could not with near instant speed. In turn the foundations upon which the internet is built can be said to have come from these types of communications as in the early days of online communication, dial-up internet used the phone lines to send information. The telegraph rose in popularity in 1910 as it led to the arrest of Dr Hawley H. Crippen who was a U.S. physician that had fled the country on a boat equipped with wireless communication and the telephone was famously invented by Alexander Graham Bell in 1876. The instant communication that these technologies allowed meant that multiple institutions in a society could work with and depend on one another, altering the way that society previously functioned. Therefore, supporting ideas of technological determinism. In 1964, when Marshall McLuhan was writing Understanding Media: The extensions of man, he talks about the extension of the voice communications devices allowed and how people would provide their own thoughts about the other person’s actions whilst only hearing speech. As this was over 50 years ago, we now know of services such as Skype which allow us to see and hear another individual at the same time. This ties in to earlier ideas of hot media as now technology requires less effort on the side of the user.
Forms of self-representation
[edit | edit source]Social Media
[edit | edit source]Social media is a very important part of many people’s lives. The varied social platforms, ranging from Facebook, Twitter, Instagram and many others give people the ability to post whatever they wish, sharing it with the world. Social media can be a very personal experience, offering up chances to share your everyday thoughts, pictures, and links to your friends and followers. These online profiles are similar to diaries, however online diaries are digital, and take their information from multiple different source rather than just one. The information a user posts on the internet is compiled together to create an overall impression of that person. This is especially the case if the user chooses to link their various social media profiles together. For example, Instagram is easily integrated into Facebook and offers an option to automatically repost any Instagram upload onto your Facebook profile.
This makes it easy to find and compile online data and uploads from individual users, giving a deeper and more developed look into the life of somebody that one would not typically find in a paper diary. However social media often does not always provide an accurate representation of somebody’s real life, and the ability to filter and edit what we upload can lead to a false portrayal of daily life.
Facebook is the largest social media network, giving a social media voice to over 1.8 billion people. The platform encourages the sharing of links, images and text between friends online. Due to the simplistic nature of uploading these, users “walls” are often filled with things they find interesting and wish to share with others. Facebook is the more prominent example of how regular posting on a social media site can build up a profile and extend a personality through technology. Every post made is timestamped, similarly to how a paper diary has dates written in. Although a user’s timeline is automated by Facebook, with the website taking your likes and displaying them on your feed, everything else on the platform is very hands-on. This includes the sharing of information with other users, and whilst this is essential from a privacy standpoint, it brings into question the authenticity of Facebook profiles.

The majority of Facebook users only want to share the good aspects of their life, such as nights out with their friends, exam success and positive family news. This ability therefore to only upload what they wish, gives them the opportunity to exclude the negative things in their life such as mental health issues or family struggles. This leads to a highly filtered representation of people on the platform, often driven by the ambition to get “likes” on a post, or follows on the platform. Human beings gravitate towards positivity, and would likely unfollow a user’s social media account if negative things were posted.
In comparison to a paper diary, Facebook is a far less realistic representation of real life. In a paper diary the writer is usually completely honest, as they do not intend for anybody else to read it unless under their supervision. Whereas Facebook, to a large degree, is an open platform, allowing for almost anybody to see what you post. The purified nature of what users post on Facebook also extends to the images they upload, their profile pictures in particular. A user’s profile picture is one of the first things seen on a Facebook account, it is visible in every post made, on profile pages and in any comments the user makes. Because of this, users often upload edited images of themselves, changing the pictures through applications such as Instagram in order to make themselves look more appealing. This practice of doctoring images to increase a user’s likeability on the internet is a perfect example of why social media, such as Facebook, cannot be trusted as a realistic representation of somebody’s personality in the non-digital life.

Twitter is a platform which allows users to post text up to 140 characters in length. This makes it ideal for sharing daily thoughts and posting hyperlinks to content you find interesting and want to share. On Twitter it is often more acceptable to update your profile daily with your current thoughts and feelings than on other sites such as Facebook. Because of this, Twitter tends to attract those who are more open with their online profiles and sharing their personalities with others. The acceptance of sharing minute details of your life on Twitter has led to it becoming the most diary-like social media platform to date, with photo and video uploading still present in the experience. The ability to look back on previous posts is another similarity Twitter has to the conventional diary format, allowing users to see their own personal growth over time. The regular nature of the posts on twitter allows the user’s personality to come through in more depth that typically found on other social media platforms such as Facebook.
One example of this is Donald Trump’s Twitter account, where he regularly posts about his political views and standpoints on issues. This is both a positive and negative way of portraying his views to the general public. It is positive as Twitter is an open platform, allowing anybody to find his profile and learn about his current agenda. However it is also a highly ineffective platform to use as the President of the United States as the 140 character limit severely limits the detail in which Trump is able to tweet. This often leads to Tweets with multiple interpretations, making it difficult to decipher Trump’s views. The immediacy of the platform and ease of use means that Trump is able to post whatever thoughts are in his mind at any given moment, and these digitised moments of bravado showcase how Twitter gives users a platform to extend their personalities into an online space.
Instagram is an image-centric social media platform which lets users post and edit photos. The platform acts as modern-day digital photo album, allowing users to categorise their photos by adding tags and locations to the images. The app itself also automatically adds information to an uploaded image such as the camera settings used. Although this information isn’t substantial, it provides another piece of the overall picture of online identity. A large part of the Instagram experience is the ability to edit the photos that are uploaded through a smartphone application. This editor offers many powerful functions such as adjusting the contrast and saturation of an image, however the editor’s main attraction is the option of adding filters. These filters change the overall tone of the image, often hiding flaws in the photo. This is the epitome of how many users use social media in general, opting to use both photo filters on the profile pictures and other images they upload, whilst also filtering out information that they do not wish to share with other people.
Erika D’Amico’s paper: “The Elements of Libidinal Economy in Instagram: A New Ontological Status of Photography”, provides insight into the way users represent their wealth through their online profiles and images. The paper argues that when you upload images to social media sites, it allows other people to experience the events you experience, albeit through a 2d, cherrypicked medium. In choosing to upload images to Instagram, you open your real life up to the scrutiny and judgement of others, which often leads to people posting expensive possessions that they own, or exciting events they have been involved in. The ability to post images of almost anything on Instagram has led to the phenomenon of “The Rich Kids of Instagram”, even leading to a Channel 4 documentary. For these people, Instagram is used as a bragging platform, with them regularly sharing images of their wealth. They choose to not only show off their wealth in a tangible manner, but also extend their exhibition to an online environment.

Distrust for AI Many technology companies are trying to develop ‘AI’ for their products, Microsoft and Apple respectively being the best examples out there. Although, (using Lanier’s Edge article[98] from 2006 as an example here) some theorists have suggested that true AI has existed on the internet because of the communities contained with each website. We can see this in the way that AI have been tested on social media sites, like twitter, to varying degrees of success. Examples from Lanier’s article[99] for people that think this are George Dyson- who hypothesises that an AI already exists on the internet- and Larry Page- who suggests that a true AI will appear on the internet within the next few years (from 2006).
Although Lanier also points out the danger in anticipating this, for example he says that [100]“how premature and dangerous it is to lower the expectations we hold for individual human intellects.” It could be argued that one could counter this with the fact that human intelligence is what is need for AI to be created.
Newspapers facing decline

It could be argued that the fact that newspapers are facing a decline is a natural evolution since the creation of personal computers. In fact, one could say that newspapers as we know them are a result of the invention of the printing press and that the spreading of information via text has been around for centuries before. It should be noted that ‘news’ websites, such as Google News, are said to be better funded and more secure compared to traditional websites for news outlets, thus bringing up the subject of “…question of new business models for content creators…”[101]
However, in the same section of his article, Lanier also says that blogging is not writing since writing takes time. This point could be agreed upon for the fact that information for blogs, vlogs, and any social media is readily available- this relates to the quote before from Lanier about how information exists in several places on the internet. Whereas ‘real’ writing requires some amount of research.
On one hand, it could be argued that if blogs ran how most news is reported then the World would be chaotic. Lanier explains that affairs, at the time, are reaching this because of an “…artificial elevation of all things Meta…profound influence on how decisions are made in America”[102]. An example of this would be how certain politicians now have their own official social media to ‘interact with the public better’ or how some are made into parts of pop-culture, for example memes. An example of the distinction between blogging and ‘real’ writing can be seen in the words of Jaron Lanier who states, “I’m saying and doing much less than I used to… I’m still being paid the same amount.”[103]
Future Technology
[edit | edit source]Technology has been developing for years now and continues to do so every single day, affecting our everyday lives whether we like it or not. For example, in the last couple of years the use of mobile phones and laptops have become more common than uncommon; a development like this has effects in different aspects of our lives too, like in Education for example, where laptops are relied on for teaching classes. One of the biggest changes that appears to be continuing with newer developments too is the age at which technology becomes a central part of someone's life. Most children nowadays will be growing up around technology as a key part of their life, and with all the continuing developments that are happening now, it doesn't seem like this will be changing anytime soon.
There are a lot of interesting new developments that have happened in the past few years that may also have major effects on how we are able to keep a sense of our 'self', whether that be in an 'online' sense or even within 'real life'.
Smart Watches
[edit | edit source]
Smart Watches have become the next logical step for a lot of companies when trying to innovate their mobile technology. Alongside consistently developing their mobile phones to keep up with the competitive market, most companies are now also simultaneously releasing smart watches to essentially function as an extension of the mobile phone.
Most of the features of a smart watch are essentially the same as the majority of smartphones nowadays. For example, the watch will also you to make calls, to view the weather, to view images you have saved (most likely transferred from another device), and to send messages to people. Even though most people take their phones with them almost everywhere, the smart watch brings technology and the human body even closer than before. People always talk about others being 'glued to their mobile phones', yet, with the smart watch, this phrase has never been closer to to the truth. The similarities between the two devices essentially show how the smart watch has became a smaller version of a phone that is always literally attached to you. It also appears to show just how much technology is becoming a bigger part of our everyday lives; that something such as a watch has now been 'modernised' in a way to act more like a phone highlights the rapid developments of technology.
VR (Virtual Reality)
[edit | edit source]
Whilst Virtual Reality has always been quite commonly known worldwide in theory, it has only been in the past few years that it has started properly integrating itself into the worldwide business market. Samsung are just one of the companies that are now shipping VR headsets with their phones (something that would have been unheard of just a few years back), and Sony has taken full advantage of the program by creating their own VR headset and shipping it alongside their newest model of the Playstation 4.
One of the most interesting things about Virtual Reality is how it can function in multiple different ways: it has the ability to bring us 'closer to life' in some ways, by creating situations (e.g. being attacked underwater by a shark) that would never rarely find ourselves in yet making them as 'realistic' as possible. However, the breadth of the technology's ability also enables it to go into the opposite direction in terms of realism: it can offer a way of escapism, essentially a gateway to worlds that don't exist, yet we are able to feel 'real' within them.
Key theorist Marshall McLuhan often spoke about how media has the ability to provide us with sensory extensions that had the ability to transform our experiences with ourselves and with each other. To put explain what he meant by this, he often used examples such as how vehicles can extend our feet, providing us with the ability to travel longer distances much quicker - he essentially thought that all new technology mirrored a specific part of the human body, and therefore somehow provided us with an improved version of that body part. Therefore, technology is intrinsically tied with human beings. Looking at Virtual Reality, it seems to extend the possibilities of the human body as a whole - it is perhaps the closest thing that the world currently has of extending the sensory experience of the body as a whole. The technology manages to take ourselves into an entirely new situation, therefore presenting the body with an entirely new 'world' to explore.
Personal Trackers
[edit | edit source]
Personal Trackers are another form of developing technology which extend our experience of the world. The main use of them is to be able to find where people are, or, if you were using one on yourself, then other people who were aware of the software would be able to find where you were at any point in time. Even though you can buy GPS trackers on their own, applications such as 'Find my Friends' on iOS enable users to see where their friends are as long as both have the correct settings turned on within their phone.
There are a lot of positives and negatives that come with this new technology: for example, people may choose to use this technology with their children, so that they can know where they are at all times in order to keep them safe. This allows the children to remain protected by the parents even though they are not physically with them. The downside of this is that people may use this type of software to stalk people, or to keep an eye on them when they have not provided consent to them doing so. Regardless of the impact of the technology, it essentially makes the space between people in the world smaller. We are no longer always able to hide away from people whenever we feel like it. Considering the implementation of this software into our mobile phones too, it is now easier than ever to know where someone is no matter how far away they are from you in a physical sense.
Blogs/Online Diaries
[edit | edit source]Another form of expressing your identity online are blogs and online diaries. People use these not so much to post pictures but more to express their feelings, thoughts, even day to day experiences. Some people just write about their lives. Nowadays, there are more and more blogs where people share their issues or health problems. There are blogs where people describe their struggle with depression, eating disorders even anxiety problems. These blogs are often made by people who decided to share their experience to help more people. There can always be the criticism that some people just do it to have attention or to feel important. Some people use blogs as an extension of themselves, to help go through personal issues, to analyse their thoughts, even though it is a public platform. People are also paid to have blogs and to advertise certain products if they have a large following and an important influence on people. Online diaries are a more personal form of writing as they involve people just sharing their intimate thoughts on the internet. People are attracted to the interactive notion of it, where people can comment and share if they've had similar experiences. The bloggers can have immediate responses. It can also be anonymous if people are unsure about sharing their identities but some people can show their identity if they are comfortable telling people who they are. However, nowadays people don't use blogs or online diaries as much. Instagram and Facebook have replaced them. It seems people are more inclined to share their lives in pictures than writing about it.
Wordpress
[edit | edit source]
Wordpress is a website used for creating websites. It is used by a lot of famous blogs, news websites like The New York Time's blog, music outlets and important companies.
People use it to create a website that will be useful to their businesses or even to make an impression on the internet and present themselves through their blogs.
Gaming
[edit | edit source]It is not uncommon today to be involved in some form of gaming platform. From playing small touch-based apps on our phones to partaking in international tournaments online and at conventions, gaming is an important aspect to many peoples’ interaction with technology. The possibility of escape, into another world, to play as a character for an indiscriminate amount of time in a virtual universe is both entertainment and often a form of relaxation for millions of players. The potential to become a part of a community is also an appealing aspect and allows users of video games to not only interact as humans with other players but helps to form a sense of unity amongst fellow gamers.
Platforms
[edit | edit source]Steam
The main gaming platform on the PC is Steam, a game client and store created by Valve. The platform allows for heavy customisation of both user profiles and the store itself, giving users the ability to extend their personalities into the gaming world. Steam offers the ability to upload profile pictures, ranging from pre-installed stock images provided by Valve, to user-uploaded images.This is extremely important as your profile image is one of the first things other users see when visiting your account page. Steam also allows users to upload images, videos and text to the profile, with many users opting to include their gaming setups and screenshots of their favourite games. This level of customisation allows for a user of Steam to extend their personality into the digital gaming world.
Another aspect of Steam is the communication available. In many games such as Counter Strike:Global Offensive players communicate through both voice chat and text chat. Steam allows users to privatise their profiles, meaning that other people cannot view the information they have uploaded to their account. This anonymity that Steam offers can breed very hostile interactions between players, especially when games become competitive. This voice chat platform often brings out the worst in people, with aggressive language and curse words at the forefront of the problems. However, it can also be very useful for team communication and can often increase the enjoyment of games, giving those who are pleasant in online interactions, voice communication. As with anything competitive, emotions often run high and this brings out a side of people not often seen. How people react when losing an online game is often a strong indicator of their real life attitudes and personality.
PSN (PlayStationNetwork)
One of the most popular video game consoles is Playstation. After many years of development and evolution - from the original Playstation all the way through to todays most recent version of the console, the Playstation 4 - this console now acts as not only a platform for individual gaming, but provides the user with a community. Like many other video game platforms, PSN allows the user to choose an avatar, a pseudonym and a background (on screen). All of these choices are customisable and conveys PSN as a platform which gives each user much space for self-representation. Each user can be as anonymous or as public as they would like, with the option to share information and gaming history (in the form of Trophies) - much like social media sites.
As mentioned, PSN's notable trait is that of its community. Many gamers who play regularly define themselves as part of the community, a group of like-minded individuals, who through their shared interest in video games can converse and feel a sense of unity. Through headphones and microphones, PSN allows users (when playing online) to communicate with those who are playing either the same game as them - and are thus in the same lobby - or if said individual is friends with another player. This form of self-representation allows for gamers to not be judged solely on their avatar and chosen screen name but by their voice also; this arguably lends video gaming to a more humanistic relationship with technology. The user face of PSN is incredibly easy to manage and keep private and allows each player to completely customise their personal space, and subsequently the space that is seen by others.
Xbox Live

Xbox is an example of an online platform growing into the mainstream and how quickly this notoriety fades in a short space of time. An example of this notoriety is how the term "xbox" can mean anything to a wide range of people and has become synonymous with gaming in mainstream culture today. However, the whole story behind Xbox Live as a business venture is a real world representation of what Lanier[104] has said "The illusion that what we already have is close to good enough..." as the platform has already faded into obscurity. This shows how gaming culture has become part of the mainstream, look to the example of Pewdiepie. The example of Xbox Live shows how internet culture as a whole has been assumed by mainstream culture today. To see how this is possible you don't have to look further than the example that Facebook has set in accordance with all of the separate groups that are contained within its structure and how it is essentially the place to be nowadays.
Identity and Identification
[edit | edit source]The enormous popularity of video games and the influence they have on player’s offline life suggests that they should be seen as more than just escapism and ways to kill time. According to McGonigal (2010), people all over the world spend three billion hours a week playing[105]. Therefore, an average player sacrifices 13 hours a week on video games, entering other worlds and taking different roles. The cyberspace provides the safe environment for experimenting and exploring a player’s identity. Hence, video games can be seen as important tools for identity formation as they help the gamer to re-conceptualise it. It is useful to explore the notion of ‘cyborgs’ in order to understand the process of constructing identity in video games and the character identification a player uses to perform that identity. A Cyborg is a person whose ability became increased by replacing body parts with mechanical parts. In the technology dominated world it is safe to say that we all became cyborgs with our omnipresent company of wireless technological devices that we carry everywhere. The line between human and machine is blurry. In video games, players literally become the machine, become avatars. Considering the ability to interact with people from around the world, the opportunities for experimenting with identities are endless. The player is able to take male or female perspective, can transform into someone much older or much younger, much more or less visually attractive, stronger, braver, more confident than he or she is offline. Interestingly, ‘by playing avatar we end up being ourselves in most revealing ways’ ([106]).
While building our avatar in Sims Online or Second Life we are able to choose desired physical features but also create different personalities. Being shy and socially awkward in real life, we can become a confident party animal and try this new notion of self in different situations. By doing this it is possible that we transfer these characteristics into our offline life. Creating ‘the new self’ in the game can also help the player to deal with fears, insecurities, anxieties and traumas. For example transgender people may be more confident about coming out after using a desired gender in the game. According to Sherry Turkle there are two ways of using online life to deal with real life problems. We can ‘act out’, taking conflicts from our real lives and expressing them again and again through virtual reality means ([107]). However we can choose more productive solutions, ‘work through’ and therefore use the online sphere to confront the conflicts from real world in order to find new solutions.
It is also important to mention Murphy’s theory ([108]) that states that identification with characters in video games is reinforced by a ‘cinematic-like state’. Therefore, even in the case of fighting games, such as Mortal Kombat, which lack a complex narrative, players still identify with the avatar due to their complete control over it.
In her essay ‘Cyberspace and Identity” Sherry Turkle writes about the notion of multiple identities and analyses how they have been increased by cyberspace communication. Quoting Sherry Turkle ([109]): “if traditionally, identity implied oneness, life on today's computer screen implies multiplicity and heterogeneity”. Video games can be seen as important tools for identity formation as they help the gamer to re - conceptualise reality.
Dating Sites
[edit | edit source]Online dating has become one of the fastest growing industries on the internet, worth over $2 billion [110], since its inception in 1995 [111] with the internet dating site Match.com. The common business model requires a small subscription fee in return for the space to create your own profile, and view the profiles of other users. Other users are often promoted by their compatibility using such parameters as common interests listed and location. There are many specialised online dating services that cater to those looking for a partner with a specific trait, such as Elite Singles, Uniform Dating and Christian Connections. The emergence of dating online has created an entirely new branch of social interaction and masspersonal communication, creating a new environment for people to sell themselves; online etiquette and signifiers are used to connote the users personality and try and make a connection with other users. Sites such as Zoosk and Match.com offer advice to users on how to make their profiles more attractive such as advising what words to use and not use, what sort of photo of themselves to use and how much information about themselves they should reveal. According to a study published by the Proceedings of the National Academy of Sciences last year, one third of U.S marriages start online. [112]. Whilst many accuse online dating as breeding a narcissistic, superficial, “hook-up” culture [113] others praise the advancement in technology for creating links between people that previously would have never been able to meet.
Match.com/Tinder etc.
[edit | edit source]
The variety of different online dating sites has created an online culture in which people are asked to specify what sort of person they are, and what sort of person they are looking for. As Papacharissi wrote, “[online dating] has particularly dynamic properties that facilitate selective self- presentation in the pursuit of relational goals…” (Papacharissi, Zizi, 2010).
Sites such as eHarmony and Match.com promote themselves for single men and women, young and old, looking to connect with other like-minded people. The huge success of online dating sites such as these have prompted many to praise the advancement in interconnectivity due to the internet, bringing together couples that without the technology would never have crossed past in the real world. The large success of online relationships proves its success. Theorists Parks and Floyds noticed in the infancy of online dating the amount of online communications that led to face-to-face interactions, 1/3 of all sustained communication. They summarised, “These findings imply that relationships that begin on line rarely stay there” (Parks and Floyds, 1996.) Sites such as Dattch have been praised for creating a space in which a smaller demographic of people, in this case lesbian women, can search actively online for a partner. [114]. Many praise this inclusion for addressing issues such as the difficulty of meeting people of the same orientation when they are out and using sites that are largely geared towards heterosexuals. 70% of homosexual couples in the UK begin online. [115] Early studies on the connectivity of online communication assumed that people online would often be linked by common interests. (Rheingold, 1993). Geographical location has become the dominant way of linking two users in internet dating and social media. Apps such as Tinder and Grindr exploit this, linking users by their distance from one another. Tinder began in 2012, and boasts over a billion “swipes” a day. The app functions by showing the user photos of men and women in their area, and allowing the user to either like or dislike the look of this person. If both users like each other’s photos and brief bio, they are connected and can message one another. Grindr works in a similar way, focussing on homosexual men. Both sites are deemed controversial for their shallow nature, and promotion of short, sometimes sexual meet ups. Others have deemed these apps a symptom of a larger issue, citing the Uses and Gratification theory alongside Maslow’s hierarchy of needs for millennials seeking of approval and acceptance. [116]
Criticism and Debate
[edit | edit source]
The nature of online dating is inherently judgemental, and many have criticised the use of such an interface to meet someone as being too superficial. How someone looks is the primary way in which most dating sites allow users to appraise one another, creating a divide between people that find this too shallow whilst others appreciate avoiding awkward first dates devoid of attraction. Papacharissi writes that networked technologies makes it easier for people ignore social etiquette often demanded face-to-face. [117]
In general, dating sites have become notorious for users lying and using false information to better promote themselves and gain attention. The competitive nature of online dating has created a community in which Toma compared the information social media such as Facebook and Twitter with the more, “…deceptive self- presentation sometimes found [on]… online dating sites…” (Toma, Hancock, & Ellison, 2008). In extreme cases, catfishing can take place, creating a sense of distrust and manipulation when dating online.
Online dating has been criticised for creating a culture in which narcissism and superficial judgement is promoted. CEO of Match.com Greg Blatt has admitted that online dating encourages greed, and that it is difficult for some to stop using the site once they’ve started as there is “always someone better”.. [118]. Studies have shown that with so much choice less and less people are finding the need to commit to their partner, and are often drawn to the instantly gratifying nature of the internet. A 2016 study by the Manchester Metropolitan University found that men using Tinder felt that they had a right to “use woman as they saw fit” if they were not attractive as their profile suggested, anchoring the sexist, one night stand culture apps such as these endorse. Those defending such findings adopt theorists like McLuhan’s belief that you cannot completely separate media platforms from attitudinal politics like this (McLuhan, 1964), however many still see these sites as unhealthy releases for this type of behaviour. 24% of Tinder users are already in a relationship. [119]
Video based representation
[edit | edit source]YouTube
[edit | edit source]
Youtube is created in 2005 website made for sharing videos free of charge. It became to be one of the most populates websites on the Internet with 100 hours of video uploaded every minute. Along with increasing popularity of YouTube, more users decided for vlogging, video blogging. They decided to mediate their everyday life by filming themselves and therefore, create stories, genres and narratives. The platform that allows its users develop, experiment and explore their identities as well as interact with each other and share opinion, views and experience. It is also a powerful tool for challenging social norms through displaying these various identities publicly. Although it more difficult to remain anonymous on YouTube due to the fact that its users display their image and share their voice, they can still re - create their identity and become someone different than they are in the real world. [120]
It is important to mention that the aesthetics of user - created content is especially focused on experimentation with the video form. Therefore, it allows the vloggers to break the rules, go against the stereotypes and encourage others to do the same.
Vloggs can be seen as the digital form of autobiography or diary that allows the users to express and present themselves but also construct the ‘new self’ on the camera. Every video blog contains the traits of self - disclosure even if its content is mainly focused on particular theme, specialisation or interests. For instance, make - up tutorial videos authors very often reveal information about their private life and actively engage with the dialogue with their fans by using audio - video components as well as written text.
Another aspect of vlogging is increasing popularity of 'YouTube stars'. YouTube allows common people who have passion, desire and charisma to transform their channel into commodity: product that allows them to make profit. Despite the benefits of it, there is also a danger that the identity of vloggers will be affected by this notion of popularity and their 'true self', the 'I' will be lost in the process.
Vimeo

Vimeo was created in 2004 video sharing platform that differs from YouTube mainly by its focus on art in the shared videos. It is considered as a website designed for more professional filmmakers and artists and its emphasises the quality of its content. It was also the first platform of its kind that supported HD videos. The YouTube community is much larger (800 million visitors per month), compared to less consistent Vimeo user base (70 million visitors per month). This emphasis on quality allows serious film-makers to be taken seriously on the platform, something not often seen on YouTube due to the amount of low-quality videos uploaded. Vimeo allows those who are passionate about video creation to extend their passion to an online environment which is far more revealing of high quality content than other sites.
False sense of representation/edited representation
[edit | edit source]Videos posted on various platforms like YouTube, Vimeo or Social Media can be considered as extensions of human eyes as they allow us to see ourselves, each other and our surroundings. They also play important role creation of our identity and enable self - expression. Video platforms work like the mirror that can distorted our image depending on the version of ourselves that we want to see. Through video we are able to create ourselves and reality.
It is important to mention that every mediated image or video is not the exact, objective version of reality. It is the representation that depends on the perspective of person who creates this image. In case of videos we are able to distorted the reality by the certain camera angles, editing techniques but also by recreating subject that we film. Hence, by posting a vlogg we can choose what clothes we wear, the hair style, we can change the way we speak and appropriately control our body language. What we do not show is also important. We can omit certain aspect of our physical and mental characteristics. We have this control through lack of bodily presence these videos. We are representing ourselves. Our choices depend on effects we want to make on our target audience. Therefore, we use the impression management by working on the backstage to achieve desirable effect on the front stage.
According to interactionist tradition, our self exists in relations to others. It is useful to bring into the discussion Goffman’s notion of public theatre, thus the way we adapt different social roles to suit different social context. Depending on who we want to watch the video we post, we put the different ‘masks’ on ([121]).
This performance we display in the videos can lead to collapsing of the distinction between personal and social identity. It is, therefore, important to cultivate the balance between private ‘I’ and social ‘ME’. There is the danger of ‘ME’ taking control over ‘I’. In this case our real sense of self can be transformed and lead to serious identity crisis ([122]).
It is also important to use our ‘digital eyes’ with the certain distance and awareness that everything we watch is representation. It is a story told from someone’s perspective and in certain context. Thus, we should be critical and (self) - reflecting in order to be able to perceive reality.
Demographics
[edit | edit source]In today’s digital age of technology all fabrics of society are present. From age groups and gender to sexual orientation and religion, we are all categorisable, and whether we like it or not, our representation as parts of these demographics and our own representations of ourselves greatly affect our relationship with technology.
Age
[edit | edit source]Digital technology is inevitable component of our everyday life. There is a pressure to use electronic devices is present almost every age group (maybe excluding babies and very small children) . People in every age use digital media for communication, interaction, self - expression. Quoting Shrery Turkle ([123]) ‘we are cyborgs’, older and younger - we are all tethered to out beloved electronic devices. The technologies are our extensions. Being online is often work requirement for adults. However, they often admit that the devotion for communication devices goes beyond employer’s expectations. Children and teenagers need to use Internet for schools and universities but obviously, they use for entertainment and communication with peers as well. Every age group experiment with the identity by creating multiple identities online. Overall, nobody can escape the demands of always on culture.
However, the approach to technology varies according to age.
Young people have grown up in the world already dominated by technology, on the network in a fully tethered life. They do not necessarily consider the online life to be the second best. They treated equally with the real life. The mixture of virtual and real world is what they know since they remember and they take it for granted. Also, young people live in the constant state of waiting for connection. Every text message is the beginning of the connection not interruption, even if it is sent during important meeting in real life.
What lacks in the life of the young people in digital era is the time for self - reflection, the time to be truly alone with own thoughts that is so important for shaping identity in adolescence. Sherry Turkle ([124]) uses Erik Erikson’s concept of ‘moratorium’ defined as realativelly consequence - free space for experimentation, the time out. It applies to adolescent need for autonomy, spent away from peers and adults. Today’s teenagers lack the ability to reflect on their emotions in private. Without connections they do not feel like themselves. This can be seen as positive cultivation of ‘collaborating self’, learning to be a part of collective intelligence. However, the alone time is crucial to find the sense of the ‘real self’. Without it it is extremely difficult to build ‘real’ relationships and function maturity in the world. The abilities that online life offers for experimentation with identity is important and highly beneficial. It provides practice at being different kind person, checking how various identities work in various situations. However it is important to remember that it is not enough to create a fully mature human being. Young people have often problems with dealing with anxieties of separation and loneliness. Behaviour of a teenager who phones home fifteen times a day would be considered as pathological a decade ago, whereas it is completely acceptable today. Young people send constantly send text messages and vast part of them is sent to parents.
In contrast, adult often overwhelmed when discover the power of social media and text messages. They often feel behind and need to rely on the help of their children in order to gain knowledge about using electronic devices. People who grew up in time free from always - on - ness sometimes feel lost in the digital world. However, as soon as they learn how to efficiently use new technologies they share with younger generation similar needs for communication, sharing etc. They often get equally drawn into online world as youngsters. They also not rarely forget about real communication with their own children who need to compete for their attention with technology.
As Danah Boyd ([125]) pointed out, the devotion for technology and always - on - ness ‘is defined more by values and lifestyle than by generation’. There are young people want to break free from the online world and are exhausted by the pressure of constant connection, whereas some adult are fully passionate about digital technologies. However, young people are considered to be more willing to explore digital world.
Different types of social media and modes of connection may have different uses, especially for younger generations depending upon who they connect to on that particular platform. For example, Facebook is a platform where people may be connected to family members and colleagues, and so a certain, perhaps more censored or conservative aspect of self is represented. In comparison, a platform like Snapchat may be used with less caution as a more casual form of self-representation due to older generations often not using this platform as it is targeted towards younger generations and is quite a new form of social media.
Gender
[edit | edit source]There is an obvious difference in the use of social medias as an extension of one's self between genders. It is addressed in Papacharissi's work A Networked Self. Women use social media differently than men and we can see that in the way they post pictures. Women are most likely to strike more 'sexy' poses than men. Whether posing alone or with friends, women are usually more forward about using their looks on pictures than men would. Women also are more comfortable posting where they kiss a person of the same sex on the cheek than men who rarely post that kind of picture. Men care less about the pictures they post while women seem to care more, they view social media as an extension of themselves and that is why it is necessary for them to keep posting pictures about 'perfect' moment. They take it more seriously whereas men act more casually towards their online presence. It has to do with the fact that even in real life, women are held to a much higher standard than men While men can just be themselves, women still have to work a lot harder to even be considered as equals. Also, women have beauty standards to live up to with the pressure from the society to constantly look beautiful and specifically feminine. Men are also sometimes less criticised for appearing in pictures where they are shirtless or showing off their bodies whereas women are more criticised for appearing sexualised. There was a recent controversy where pop singer Justin Bieber appeared naked on an Instagram photos and people praised him for it and complimented him. People compared his comments to the comments female singers like Demi Lovato got where people told them to have some decency and to cover themselves. This is a behaviour that men are praised for while women are reprimanded for it. Instagram was also criticised for allowing men to post pictures where you could see nipples whereas for women they had to blur them. Men have more freedom to use the internet and social networks as an extension of themselves whereas women need to be more careful in order to not receive criticism.
Sexual Orientation
[edit | edit source]Digital Technology has always predominantly been tailored not only to a male gaze, but to that of a heterosexual one too. Online, any page you come across, websites advertise heterosexual dating sites with photos of scantily clad women posing sexually or advertise products like perfume or hair products with a heterosexual couple holding each other. With advertising taking up a tremendous amount of both revenue and physical screen space in terms of digital technology, it is clear to see that there is a struggle for non-heterosexual people to feel represented.
It is only in the last decade that qualitative research into the self-representation of non-heterosexual users of digital technology has been studied. There has been a recent surge in the interest into how non-heterosexual members of society portray their online identities through the use of dating sites and chat rooms, as well as interview-style research into how these people balance their representations of themselves in real life and online.
In an attempt to not only feel more equally represented but to feel as part of a community whereby peoples’ representation of themselves comes under no stereotype of non-heterosexuality, those individuals have created LGBT social networking sites, in an attempt to remove themselves momentarily from their “predominantly heterosexual peer cultures”. These websites are a way of communicating in a safe space and provide relative to complete anonymity for users.[126] In 2013, after research on “non-heterosexual young people’s use of the internet”, theorist Gary Downing concluded that, “the relationship between online and offline relations is not a one-way ‘rehearsal’, but a multi-dimensional process that blurs the boundaries between virtual and material realities”. [127] This suggests that non-heterosexual people, through certain websites and chatrooms (teenchat.com, lgbtchat.net) are finding ways to successfully extend themselves through the technology they are using and present a version of themselves even though they find themselves in an online world dominated by forefront heterosexuality and advertising.
Religion
[edit | edit source]
Religious institutions have influenced life before the internet and now. People in the religious community are confused as to which they go to for guidance. On the other hand the internet is an asset that is used by other members of the religious persuasion that use the internet as a means to an end, a necessary end to some. Similar to how the bible is often described, [128]"Reading a Wikipedia entry is like reading the bible closely. There are faint traces of the voices of various anonymous authors and editors, though it is impossible to be sure." This is similar to the ideas expressed by one small subculture ([129]"...psychedelic luminaries of old.").
Although, the internet in general seems to be more of a secular landscape in which nobody is challenged on their beliefs, nor are they mocked for having these beliefs- unless they find themselves in the wrong community i.e message boards, meme pages, etc. Some in the religious community may only have problems with the fact that there is little to no human interaction on the web, [130]"...value always came from connecting with real humans." Those that are more less traditionalists might take issue with the fact that writing in the first person is a relatively new concept too; as is highlighted by Jill Walker Rettberg in her book from 2014[131], in which she says that for most of human history people rarely wrote about themselves.
Although in the same chapter [132]Rettberg also talks about how the use of the internet can be beneficial to religions, for example Vivian Serfaty is referenced as talking about how blogs now are like 18th Century diaries of the Puritans, which were [133]'a requirement of religious self-discipline.'
However, those in these communities may run into the same problems faced by academics and students alike, as [134]Lanier points out "...most technical or scientific information that is in the Wikipedia was already on the web before...".
Theories
[edit | edit source]Online/Real Life Divide
[edit | edit source]There are many factors that create the online versus real life divide. The first of which is the lack of personal connection to most of the people we encounter online. For example, I have no personal connection to the majority of people who I play games with online. They are my teammates for a short period of time and then the relationship ends. In comparison, the encounters we have in the real world often lead to developed relationships, typically leading to friendship, romance, or conflict. This lack of emotional investment in those we encounter online makes it easier to become frustrated with them, with people often using harsh language that they would not normally use in the real world.
The online world provides a level of anonymity not available in the real world, giving users the ability to post whatever they please without any repercussions. Sites such as 4chan and 7chan give users complete privacy and anonymity, leading to some truly horrific posts on these sites. Those on these sites (and others such as YouTube and Tumblr) are far more likely to be hostile towards others due to the lack of repercussions they would face for it. This often brings out the worst in people, allowing them to project their darkest thoughts onto the internet without any backlash. For example, in the real world, if you threatened to physically assault somebody, you would be arrested. Whereas if this same even occurred online, which is does on a daily basis, nothing could be done about it as there would be very little information about the user who made the threats.
It is undoubtedly true that a big part of our lives is lived in virtual places. As we became real life cyborgs, sleeping with our phones, constantly online: texting, messaging each other, making Skype and Face Time conversations, playing online games with people around the world. It is hard sometimes not to get the border between online and real life blurred. On - line we can be enhanced versions of ourselves, we can re - create ourselves in the way we want to. Some people describe life on Facebook as better than anything than they every experienced. Moreover, online we can deal with everyday activities: communicating, shopping, ordering food ( we cannot YET eat online but who knows what is going to happen in a decade…), paying bills, listening to the music, watching films, searching for information etc. There are also social, educational and work pressures to stay online. The clear line between virtual and real disappeared and all we, as society, can do is to use the online sphere to enhance the offline world. It is important not to let the real be completely dominated by virtual on collective and individual level.
Being online in the digital era gives us opportunity not only for multitasking but as Sherry Turkle put it for 'multi - lifing'. Sending and receiving text messages allows us to simultaneously continue another activity. We can can be on Facebook, deeply in digital world, while ordering a coffee. Ability to multitask is a requirement for being successful.
It is impossible to completely replace the value of real face - to - face communication with digital. The ability to physically spend time with someone, being able to hear the tone of the real voice of our companion (not digitally mutated like in FaceTime conversation), to read the body language or being able to touch each other is simply irreplaceable. There is this nuance and gesture that is missed from digital interactions, even if we connect through video displayed in 4K. The problem appears when even on a romantic date or important family meeting we are not really together but tethered to our phones, being with someone else, in different digital world.
Privacy
[edit | edit source]The use of technology as an extension of ourselves has increased the sharing of private information dramatically both in terms of people willingly sharing thoughts and aspects of their identity, and unwillingly through data trails for example. Always-on culture has led to a blurring of boundaries between public and private lives, as real lives are becoming increasingly connected to the online world at all times. This blurring of boundaries has created an online disinhibition, as being behind the screen means not being in proximity to other people, therefore physically locating us away from normal social cues and responsibilities. Users of technology have somewhat willingly traded in their privacy for the ability to share their lives and thoughts, which demonstrates how technology has become an extension of self. However, at times technology encourages users to share more personal information than they want to or feel comfortable with, and users are either unaware or become concerned about how and why this private information is used.
There is also a political aspect of online visibility. In the era of global terrorism, terrorists often use social media as a tool for communication. Isis famously used Twitter to plan their assassinations. There is obviously a need to control social media platform by institutions that deal with crime to prevent it. However, this is often used as an abuse of privacy of common people that have nothing to do with terrorism or any kind of criminal activity. It is the same case with the drug dealers, human traffickers etc. There is ongoing debate about the level of control that should exercise by governments to prevent the crimes. However, it is important to remember that excessive level of this online invigilation may lead to complete lack of privacy of Internet users. This brings on mind not only McLuhan’s notion of ‘global village’ but the Orwell’s super – state where everyone is constantly closely monitored by infamous Big Brother.
'Privacy has been defined either as the right to be left alone or as the right to determine for oneself which areas of life should be accessible to others –or as a combination of the two (Tavani, 2008)'. The concept of privacy is one that keeps coming up nowadays in relations to social media and the use of the internet. We are becoming aware of the fact that we are constantly watched no matter what website we are on. It is not even about sharing too many information on social networks like Facebook or Instagram, it is more about how any information is available. Nowadays, in order to visit most websites, we need to give out information, like our names or email address, sometimes giving out our age and gender. Sometimes this is necessary and can help certain companies that have websites to draw information about the kind of person who visits their websites and who should be their target audiences. It has now become necessary to give out information in order to be a part of a website. It can feel like we are also more 'encouraged' to be paranoid about technologies and social medias. There were reports from the news with the NSA files and Snowden who had access to every information and from everyone. When confronted, the NSA relied on the fact that if people have nothing to hide they have nothing to fear. This is a theme we can also see in pop culture with the rise of many TV shows addressing this privacy issue like Mr Robot and Black Mirror. In an episode of Black Mirror called Shut up and Dance, a young man is filmed doing something embarrassing in front of his webcam and is blackmailed into doing dangerous acts in order to stop people from leaking the video online. Many reviews have called this episode realistic has it was inspired by real life events of people who were blackmailed and threatened to have personal and potentially embarrassing information leaked. We are encouraged to share more and more information about ourselves sometimes even simply to build an identity online. It relates to the notion that we use the online as an extension of ourselves sometimes without caring about potential dangers. The more information is available online, the more we are at risk of being watched even if it's sometimes by organisations claiming to protect us.
Connectivity
[edit | edit source]Modern technology such as the internet and mobile phones have revolutionised the ways in which people are able to connect with one another. Connectivity is now instant and constant due to people often using more than one social media account and being connected to many people all at once, at any time. This technology has helped us to connect with one another more quickly and more often. However, it is debated that this constant online connectivity and the always-on culture as Danah Boyd discusses, has led to distractions from real world connections, and we must make an effort to balance online and offline connectivity by taking time away from online connection once in a while. [135] Similarly, Lanier describes that "this widespread practice of fragmentary, impersonal communication has demeaned interpersonal interaction", but believes that connectivity is a positive force as long as we use it in creative and personal ways to create real human connection [136] The widespread use and popularity of the internet as a means of connectivity shows how important human connection is to us. Groups with similar interests or things in common can now interact with one another no matter what their location. Connection with one another has allowed users to express their identities to others and to validate their identities to themselves. The online world of connection has become a community in it's own right, where people can interact with one another regardless of who they are and where they are in the world.
Hive Mind
[edit | edit source]Some would be inclined to say that the concept of a hive mind has been around for many years, but this concept becomes particularly dangerous when applied to technology today, fandoms and the internet.
The power of the hive mind can be seen clearly in Jaron Lanier’s article Digital Maoism : The Hazards of the New Online Collectivism[137]. In this Lanier talks about how it says on his Wikipedia page that he is a film director, which has some degree of truth to it. Lanier goes on to state how he tried to get this removed, “I have attempted to retire from directing films in the alternate universe that is the Wikipedia.” However, he also states that he is usually overruled on this by the next day. Therefore, this shows how powerful the collective can be when compared to the power that the individual has.

In the following section Lanier[138] displays how the collective can be stupid despite the number of individual minds attached to it as he speaks about the thought that many people have of misplacing trust in the fact that ‘someone will correct this’ and that all this information is readily available to anyone and everyone, “…it takes work to find the right authors to research and review a multitude of diverse topics.”
In the same article[139] Lanier also points out how every collective starts with the best intentions, an example of this would be how in the early days of this information age search engines like Yahoo were started as a simple directory, but then the race to see who could become the most Meta site began with the introduction of Google and its superior service. In early days, these companies only had to have one person in charge of it all, whereas now you have multiple different people doing essentially the same job, like community managers, social media managers, etc. and you have different algorithms in charge of sites like Reddit and such instead as the hive mind is too much for one person to handle.
One could say that these collectives are now helping their own and other businesses thrive as algorithms can cater to the individuals within the hive mind by gathering data on the collective to sell, advertise, etc. directly to the individual. This in turn contributes to the belief that the most Meta site has infinite funding. We are already seeing the beginning of this in terms of social media sites like Facebook, Twitter, etc. This then proves the contrary that [140]“the collective isn’t always stupid.” As [141]Lanier points out, “The reason the collective can be valuable is precisely that its peaks of intelligence and stupidity are not the same as the ones usually displayed by individuals.” Here he connects the idea that there is strength in numbers with the fact that message boards and such help connect those with the ideas and those that will execute those ideas. Showing the connection between independent projects and the mainstream, using Pewdiepie as an example; he started as an independent element on the internet and soon became mainstream when his channel was incorporated by Maker studios- a company owned by Disney.
[142]Lanier points out, however, how controversy can occur when power of the many is given to the one, “…when one is both given substantial power and insulated from the results of his or her actions.”
Censoring
[edit | edit source]
Although the internet is a much more free environment to express opinions that is often found in real life, it is still censored in certain ways. Particular sites such as YouTube, Twitch and Facebook will remove content that is flagged as inappropriate or illegal. This content can range from sexual images and videos, to offensive language, to other inappropriate content. Some internet sites do not censor whatsoever, including the 4chan network, which allows for completely anonymous posting of images, links and content. This therefore allows for a much free-er platform to express ideas and thoughts, and often allows for things that would be deemed inappropriate in real life, to be shared through the internet.
On sites such as Twitch, Facebook and Youtube there are multiple ways of censoring users. Users can be banned on Twitch for offensive content, and this prevents them from streaming and communicating with their audience. Twitch is generally quite relaxed with regards to content, allowing the majority of swear words and offensive content. In comparison Facebook is far less lenient, banning users who post violent and or sexual content. This is especially the case in countries where the government has more control over social media. Youtube is more lenient than Facebook, it still censors explicit sexual content, however it does allow some representations of violence and bad language
Technological Determinism
[edit | edit source]Technological Determinism is a theory which proposes that historical and cultural shifts throughout time have arisen due to technological and media innovations; and conveys the fact that technological innovation has a real transformative power on society, in revolutionising social roles and norms. Technology, in its broadest of terms can be defined as any tool which with the addition of physical and mental effort has come to resolve some (human) problem. Specifically, in terms of Technological Determinism, the technology in question has evolved over time and is now not only associated with the likes of physical machines, Gutenberg’s printing press (in 1439) for example, but with virtual technology also, modern day computer software, for example.
The most prominent theorist to voice their opinions on Technological Determinism was Marshall McLuhan. Through his 1964 work [143] he argued that through evolutions in technology, the way we live our lives, and interact with each other has dramatically changed. His view (coined originally by Thorstein Veblen) conveyed technology as the most powerful transformative factor in history and therefore, in society. McLuhan illustrated that through print, there was a cultural and societal shift from that of oral communication to written communication. From here it is clear to see the development to television (as a form of visual communication), and onwards to the internet (an all encompassing multi-platform of worldwide information).
Technology has been used to mark out major periods in time with names such as the stone age, bronze age, mechanical age and now the digital age, each relating to the major technological influence of the time. McLuhan describes the idea that technology and man are intertwined by saying: “Personal and social consequences of any medium (of any extensions of our self) result from the new scale that is introduced by each extension”. [144] Outlined here is that the way mankind is a result from the previous technological development and in turn the next development is the result of the society formed by that society. The relationship is painted as being symbiotic in nature as technology is an intrinsic part of mankind as a whole.
Many other critics and writers on technology and its relationship with humanity have commented on the theory of Technological Determinism, with Rosalind Williams describing it as “..a three-word logical proposition: "Technology determines history””. Another theorist, Lelia Green argues (from a Technological Determinist standpoint) that "'You can't stop progress', implying that we are unable to control technology". This notion of control has often been a discursive factor when understanding Technological Determinism, with more radical theorists believing that humanity has lost its control over technology – or more specifically, that humanity has greatly changed its attitude towards the acceptance of technology in our lives. In terms of technology as an extension of the self, Technological Determinist arguments can be seen to appeal to the notion of an ever-developing close relationship between man and machine; with technology acting as a version of ourselves, creating new norms and conventions that socially, we must oblige to (for example, the almost universal use of Social Media Sites, not only to present ourselves as active humans but as the primary form of online communication with others).
Cultural Determinism
[edit | edit source]Cultural determinism is a cultural theory that evaluates how society and history affects what technologies are created and what they are used for. Defining cultural determinism first requires a definition of culture. Culture can be described as the products and patterns of human thought that are shared within a society.
Raymond Williams’ theories on cultural determinism were critical of the previous writings of Marshall McLuhan’s thoughts on technological determinism. Cultural determinism somewhat rejected the ideas of technological determinism that technology affects or creates major changes or shifts in society. Instead, technology can be seen to be developed as a reaction to society’s needs, and so technology was just an adaption to patterns that already exist within society. Williams described that “all technologies have been developed and improved to help with known human practices or with foreseen and desired practices”, therefore technology follows society rather than society evolving due to technological changes [145] When considering cultural determinism theories through technology as an extension of self, it is arguable that humans are naturally social and use technology for an already present desire to share and communicate.
Cultural Determinism Theory states that the culture shapes ‘our behavioural and emotional patterns’. By applying this to the media effects on society, Raymond Williams claimed that social processes and structures influence developments in technology. Williams, in contrast to McLuhan, aimed to prove that technology cannot guarantee any social or cultural change. Media studies tend to favour Williams’ theory and ignore the similarities in McLuhan’s and Williams’ writings. The concept of ‘extension of man’ is important for Williams when he writes: ‘A technology, when it has been achieved, can be seen as general human property, extension of human capacity’([146]) . However, he is more interested than McLuhan in exploring the question about reasons for development of technology . For Williams the technologies were invented to help the society and they ‘involve precisely’ ([147]) . His argument is sociological and the technological development is dependent on specific social groups. Different social groups with different needs and agendas adapt, shape or reject the uses of technologies. Moreover, Williams claims that the final effect and impact and social effects of technologies is sometimes impossible to foreseen. His full concept of technology takes into consideration the knowledge and skills needed to use particular tool or machine.
Therefore, Cultural Determinism Theory also considers technology as ‘an extension of man’. However, it is the man who decides what technology needs to be developed in order to be useful for society. This can be political and economically problematic considering that average user of technology devices, without power and skills to decide on technological innovations is being manipulated by more influential groups. For instance, social mentality is affected by images transmitted mass media which are heavily influenced by political and economic dominant ideologies.
The other influential thinkers whose work relates to Cultural Determinism are: Goethe, Fichte, August, Schlegel, Patrick Buchanan and Robert Barro. [148]
The Future
[edit | edit source]It is difficult to tell exactly where technology will take mankind in the future. When looking at the past, academic figures such as McLuhan were successful in predicting certain technologies as his writings on future mediums appears to have predicted the internet around thirty years before it was invented. Whatever the next medium may be, past predictions seem to suggest technology will continue to extend more and more of our senses. Advances such as VR (virtual reality) are now aiming to immerse players within other worlds, far more than the world of film could before that and in turn print media before that. Immersion in stories and games have been achieved then its possible the next step would be to immerse ourselves in worlds of communication. The internet allowed for instantaneous communication across the globe and continues to change the way in which we interact with others, combining this communication with high levels of immersion would extend ourselves further than previously possible. If communication shifted from manual and mechanical means to electrical with email and instant messengers, then perhaps the next medium of extending communication is imminent.
Glossary
[edit | edit source]- AI - [149] a branch of computer science dealing with the simulation of intelligent behavior in computers. The capability of a machine to imitate intelligent human behavior.
- App - [150]an application, typically a small, specialized program downloaded onto mobile devices.
- Avatar - An icon or figure representing a particular person in a video game, Internet forum, etc. [151]
- Cyborg (short for "cybernetic organism") is a being with both organic and biomechatronic body parts. [152]
- Gamer - [153] a person who plays games; especially : a person who regularly plays computer or video games.
- Global Village - A term developed by McLuhan to explain how the world has been boxed into a small physical framework by technology.
- Hive mind - A notional entity consisting of a large number of people who share their knowledge or opinions with one another, regarded as producing either uncritical conformity or collective intelligence. [154]
- Impression Management - a conscious or subconscious process in which people attempt to influence the perceptions of other people about a person, object or event. [155]
- Mass Personal Communication - Term used to describe the online sharing of personal information with a wide audience.
- Media Convergence -[156] phenomenon involving the interconnection of information and communications technologies, computer networks, and media content. It brings together the “three C’s”—computing, communication, and content—and is a direct consequence of the digitization of media content and the popularization of the Internet.
- Meta - [157] (of a creative work) referring to itself or to the conventions of its genre; self-referential.
- Online Collectivism -[158] a political or economic theory advocating collective control especially over production and distribution; also : a system marked by such control, emphasis on collective rather than individual action or identity.
- Persona - the aspect of someone's character that is presented to or perceived by others. [159]
- Pseudonym - An alias, fake/false/different name used by one to represent an identity other than their own.[160] A fictitious name, especially one used by an author.
- Social Media - Websites and applications that enable users to create and share content or to participate in social networking. [161]
- The Machine - The term used to define technology (often used when referred to as, in opposition to humanity)
- Wikipedia - Wikipedia is a free, open content online encyclopedia created through the collaborative effort of a community of users known as Wikipedians. Anyone registered on the site can create an article for publication; registration is not required to edit articles. [162]
References
[edit | edit source]
| This page or section is an undeveloped draft or outline. You can help to develop the work, or you can ask for assistance in the project room. |
The Hive Mind and Collective Intelligence
[edit | edit source]
ollective intelligence is where the intelligence of a group out-weighs the intelligence of an individual. There are various types of collective intelligence, as is indicated in the visual to the right. In his book 'Collective Intelligence: Mankind's Emerging World in Cyberspace',[163] Pierre Lévy introduces the concept that collective intelligence can be broken down into five components:
- Ethics
- Economics
- Technologies
- Politics
- Aesthetics
The Hive Mind is an entity of multiple people who openly share their knowledge and opinions, which may lead to collective intelligence or uncritical conformity.
History and Origins
[edit | edit source]

The first investigation into the concept of collective intelligence can be traced back to the philosopher Nicolas de Condorcet, whose jury theorem in 1785 deduced that there was link between group sizes and their overall correctness. Then in 1911 though his study of ants becoming superorganisms, William Morton Wheeler determined that collaboration between species leads to an otherwise unattainable success. Various other writers such as Douglas Hofstadter, Tom Atlee, Pierre Lévy, Howard Bloom, Francis Heylighen, Douglas Engelbart, Cliff Joslyn and Ron Dembo went on to continue to investigate and observe collective intelligence, forming the current understanding of this group intelligence.
The concept of a hive mind is often used as a trope in various sci-fi books, tracing back to Olaf Stapledon's science fiction novel Last and First Men (1930). Non-fiction wise, Kevin Kelly's book Out of Control: The New Biology of Machines, Social Systems, and the Economic World (1994) heavily featured the concept of a hive mind, with the writer directly linking the beehive nature to human group intelligence.
Main Concepts of Collective Intelligence
[edit | edit source]The main concepts of collective intelligence are ethics, economics, technologies, politics, aesthetics and sociology.
Ethics
[edit | edit source]The moral principle of ethics is brought into consideration whilst discussing the concept of collective intelligence. As collective intelligence consists of a wide range of multiple individuals, this allows for a wide range of both ethical advantages as well as ethically problematic practices.
Ethical Advantages of Collective Intelligence
[edit | edit source]Tom Atlee, an American social, peace and environmental activist, feels that collective intelligence can be encouraged "to overcome 'groupthink' and individual cognitive bias in order to allow a collective to cooperate on one process – while achieving enhanced intellectual performance." [164] A lack of personal bias in results from collective intelligence proves as a advantage as it eliminates the ethical problem of biased results that a singular entity may provide.
'Smart mobs' is a term coined by Howard Rheingold to describe groups of collective intelligence. In his article he affirms that cooperation causes civilizations to advance as well as the general lives of civilians to improve. He notes that "Language, the alphabet, cities, the printing press did not eliminate poverty or injustice, but they did make it possible for groups of people to create cooperative enterprises such as science and democracy that increased the health, welfare, and liberty of many", displaying the positives of a collective intelligence. [165]
Advantageous Examples
[edit | edit source]

The internet is the perfect place for collective intelligence to blossom as it is accessible to millions across nearly every country. Geert Lovink expresses an advantage of this collective intelligence in his book 'Zero Comments: Blogging and Critical Internet Culture', where he cites the Buncefield fire as an instance where collective intelligence helped shape the news, noting that "The BBC received 6500 e-mailed mobile images and video clips showing the fires at the Buncefield oil depot [...] Media started to look more participatory and inclusive". [166]
Another advantage of collective intelligence is the wide spread coverage Amber alerts on missing people receive. By using methods such a sharing articles and re tweeting posts from official police sources, thousands of people are alerted to news they might otherwise be oblivious to. Also in relation to crime, the collective intelligence of social media users on Reddit and Facebook helped to track down the identity of a car crash victim allowing his family to be notified and given the closure they were waiting for. [167]
Ethical Problems of Collective Intelligence
[edit | edit source]Whilst the aforementioned smart mobs can prove a positive, Howard Rheingold also discusses the negatives that the collective intelligence can cause. He notes that "There are the dangers as well as opportunities concerning smart mobs. I used the word "mob" deliberately because of its dark resonances. Humans have used our talents for cooperation to organize atrocities. Technologies that enable cooperation are not inherently pathological: unlike nuclear bombs or land mines, smart mob technologies have the potential for being used for good as well as evil." [168]
Problematic Examples
[edit | edit source]
The collective intelligence of smart mobs can be used to commit harmful actions, such as mass hacking of private accounts. An example of this is the infamous Yahoo hack where over one billion accounts were compromised. This hacked data included users' names, email addresses, telephone numbers, dates of birth, passwords and encrypted or unencrypted security questions and answers. This illegal and invasive use of collective intelligence reveals the disregards of ethics that such a system can provide. [169]
Ethical Problems In Relation to The Hive Mind
[edit | edit source]Ethics are also in need to be taken into consideration whilst analyzing the hive mind. The group mentality of the hive mind can lead to deindividuation, which is the loss of self-awareness in a group. This can lead to cyberbullying as groups are easily swayed and targeted without realizing the damage they are causing, using the group dynamic as a guise to hide behind. A more in-depth discussion of the problems of the hive mind can be found in the Problems of the Hive Mind section.
Economics
[edit | edit source]
The US is known as having the largest economy. They are 7 trillion dollars ahead of China. The UK ends up in 5th place with a 2.9 trillion dollar economy. The digital economy has a great deal to do with it. Tiziana Terranova describes the Collective Intelligence as a form of universally distributed intelligence, constantly enhanced, coordinated in real time, and resulting in the effective mobilization of skills… The basis and goal of collective intelligence is the mutual recognition and enrichment of individuals. Knowledge labour is inherently collective, we create content from one peer to another. Collective knowledge work, then, is not about those who work in the knowledge industry. But it is also not about employment. The mass layoffs in the digital media industry have not hindered the internet content or technology from growing. One battle the collective knowledge faces is government agencies and the like, are trying to “reimpose the regime of the broadcast era in which the customers of technology will be deprived of the power to create and left only with the power to consume.” The other industries such as film and music industries want you to “pay to play.”
The Digital Economy
[edit | edit source]The digital economy is an easy way to copy or share information with little to no cost. Terranova explains the digital economy as specific forms of production, such as web design, multimedia production, digital services etc.

Distributing value by its likelihood of profit is the processes of ‘channelling’ according to Terranova. “Music, fashion, and information are all produced collectively but are selectively compensated. It is a form of collective cultural labour which makes these products possible even though the profit is disproportionately appropriated by established corporations.” Knowledge work, according to Terranova, is an essential quality to innovation and achieving goals. Human intelligence adds value to the economic health of the organization but it can’t be managed the same way as more common types of labour. Knowledge workers need open gateways in order to create, due to their process being rooted in collaboration.
Labour
[edit | edit source]The collective Intelligence of the digital age has created a unique conundrum in the way of labour. The problem being most labour is not returned in wage because it is possible with so many people collectively producing content, for someone to work for free. Terrranova explains the “society-factory” describes a process whereby ‘work processes have shifted from the factory to society.’ Which in turn creates voluntarily given and unwaged, enjoyed and exploited, free labour. This activity on the Net includes building web sites, modifying software packages reading a participating in mailing lists and building virtual spaces. Many have discussed the draw backs of this particular situation being, as Terranova would say, the death of the middle man, from bookshops to travel agencies and Blockbusters a like.

The Recording/Film Industry
[edit | edit source]The same economic pickle is shared between both the recording industry and the film industry. The pickle being file-sharing. These industries both have problems with illegally downloaded content and are trying to back “protection devices” that will prevent smaller users from distributing or creating content online and only allow larger players to do so. The industries get robbed of millions of dollars due to web sites dedicated to file sharing. It’s so easy for users to google a song or a movie and find a free version on the internet due to the peer-to-peer communication on the internet. Web sites such as Napster, and Lime wire have been handled legally in courts but the damage was still done.
Napster
[edit | edit source]
Napster was a UK file sharing web site for mostly MP3s that was created in 1999. It’s ease with peer-to-peer interaction ushered its success. The web site got millions of hits and downloads. Until artists like Dr. Dre and Metallica started to find their unreleased music on the website. They sued the web site and the suits were settled in 2001 after being shut down.
Radiohead had a more enjoyable experience with Napster. Radiohead was never known for their top hits. They never made it on the radio and never released singles. So when their album was leaked early the production crew was extremely worried about sales. All of a sudden their songs were being downloaded by the millions. Their song jumped to #1 on the charts and everyone was buzzing about it. The interaction on the site created the buzz and in turn Radiohead was more popular than they had ever been before.
Technologies
[edit | edit source]Advantages of Technologies within Collective Intelligence
[edit | edit source]Collective intelligence is the collaboration of information of everything that we use in our everyday lives. Thousands of people have collaborated specialist information, but no one with a full understanding, to create an overall accepted idea. Pierre Levy suggests, “No one knows everything, everyone knows something.” [170] This is why technology has become one of the most groundbreaking resources that people can use as it allows them to gain knowledge on topics that are discussed all over the world.
This quotation from David Guantlett, supports this statement. “The internet is the most extraordinary of these external storage systems, offering access to a vast array of information, text and audio-visual material, and giving people a platform to share and exchange ideas, and to collaborate on projects together.” [171]
This is exactly what we are using this Wikipedia Project for, it allows groups of students, like us, to collaborate out ideas and portray them in a way that the rest of the world can see. It is an update of an essay, that aids everyones learning.
It is easier to keep in contact with friends and family, it is easier to research, keep up to date on breaking news and experience things as the are happening live. This has allowed society to speed up and be active online 24/7. Nowadays all the information that is needed to anyone is available at the touch of a button.
Advantage - Examples
[edit | edit source]The development of Collective Intelligence has allowed the web to become more widespread and evolve from Web 1.0 to Web 2.0. You can see from this table that the development of websites and applications has allowed society to have more access to online information.

| Web 2.0 | Development | Web 2.0 |
|---|---|---|
| Double Click | —> | Google AdSense |
| Ofoto | —> | Flickr |
| Akamai | —> | BitTorrent |
| mp3.com | —> | Napster |
| Britannica Online | —> | Wikipedia |
| Personal Websites | —> | Blogging |
| Evite | —> | upcoming.org and EVDB |
| Domain Name Speculation | —> | Search Engine Optimisation |
| Page Views | —> | Cost Per Link |
| Screen Scraping | —> | Web Services |
| Publishing | —> | Participation |
| Content Management Systems | —> | Wikis |
| Directories (Taxonomy) | —> | Tagging (“Folksonomy”) |
| Stickiness | —> | Syndication |
These developments have aided a positive growth of the internet and allowed Collective Intelligence to increase as Web 2.0 created a space for a blooming platform where individuals could portray their own ideas. This is where the specialist information was shared and consumed to create the ideas that society has today.
The ability to ‘subscribe’ to a website and receive notifications on it’s updates every day was another huge stepping stone in the web becoming ‘live’. This addition to web viewing was vital in the development of Collective Intelligence as it allowed society to have constant access and connection to other people’s views and ideas. Richard Skrenta, a Silicon Valley entrepreneur called it the ‘incremental web’.
Tim O’Reilly (2005) has shaped Web 2.0 into 9 different topics, it is based on user generated content and relates to things covered within this chapter. The idea of 'subscribing' relates to user generated content. This shows that the internet is becoming what we make it.
- Participation
- Collective Intelligence
- Better software by more users
- Control of one one’s data
- Rich user experience
- Remixing data
- Radical decentralization
- Radical trust
- Users as contributors

The Massachusetts Institute of Technology is one of the main research Universities in the world and has played a key role in the development of Collective Intelligence, the CI research centre at MIT is headed by Professor Thomas Malone. “The MIT Center for Collective Intelligence brings together faculty from across MIT to conduct research on how people and computers can work together more intelligently and on the underlying scientific questions that help make this possible.” MIT’s goal is to further discover ways in which people can use technologies to communicate ideas and ripen this idea. This research centre shows the magnitude of Collective Intelligence and this research centre is collecting examples and case studies of Collective Intelligence applications. [173]
There are many advantages of Technologies within Collective Intelligence, they have allowed the world to grow together and share ideas, information and discoveries in seconds. It is now possible to know what is happening a million miles away. A recent example of this is the 2016/17 presidential elections. 30.6 million people watched Donald Trump's inauguration on 12 different networks. 2.3 million of these people watched on one of the 16.9 million livestreams. This is an example of the advantages of collective intelligence, as it allowed the viewers to be right there in Washington DC that day. [174]
Disadvantages of Technologies within Collective Intelligence
[edit | edit source]Is all this information available to us via the internet and technology making us smarter? The answer seems to be no. Society is getting more selfish, and users take everything at face value. They don’t ask questions and their attention spans have shrunk. As a society, it is expected that because these technologies are on hand that everything should be fast, efficient and reliable. Within Collective Intelligence, it has been seen that people do not think for themselves and ‘steal’ others' ideas and this is what creates a hive mind. These technologies have allowed the web to become a place of consumption and less contribution, and as Guantlett says “creativity will become an industrial tool and it’s positive potential will be destroyed.” [175] MIT professor Thomas Malone believes that technologies have not been used in a productive way to fix our global problems like climate change and the third world problems. It has been used to create entertainment, and a sociable platform for users. He believes it has gotten to the point where it is difficult to stop this evolution of the Web and start to use it for its original purpose. [176] This over-populated space of information “feeds resentment and hostility, the humiliation and frustration from which violence is born.” [177] In Pierre Levy’s reading What is Collective Intelligence he suggests that if we do not accept and acknowledge other people’s intelligences when reading information we can become selfish and start only thinking about ourselves and we do not gain a full view of the information and topic at hand.
Disadvantage - Examples
[edit | edit source]
Have you ever noticed when you are online an advert comes up for a dress, book or gadget you had looked at a week before online comes up? This is because the use of the internet everyday is tracked and then produces adverts on your screen specifically by what you have previously clicked. This is a claustrophobic form of advertising that is referred to as Filter Bubbles. It has stopped the ability to view things by choice. It starts to show you content you are already aware of and starts to narrow the way you think, as you do not have a clear idea of the whole topic. This is when Collective Intelligence becomes a Hive Mind. It is believed that The Hive Mind is the negative effect of an over populated Collective Intelligence - also known as Artificial Intelligence. [178]
Hive Mind
[edit | edit source]
“Even if one individual is not capable of much, collectively a swarm of insects can solve difficult problems.” [179] This is what is meant by a hive mind. The information that has been gathered and became a Collective Intelligence has now been overused and shared and not allowed anyone else to form their own opinions. Due to technologies, everyone else's opinion is available 24/7 and it then makes it hard to create our own. This difficulty has created what is considered a negative of Collective Intelligence, The Hive Mind.
Collective Intelligence allows flow for the development of ideas and opinions wheres the Hive Mind does not. It is as it suggests, a fixed, rigged structure that contains the animals. Although the animals inside the Hive help each other and share opinions on decisions, it does not allow growth for new ideas. The risk of technologies is that it will start to enclose the options of society in with Filter Bubbles and therefore causing no space to grow and to develop opinions.
Thomas Malone wrote “The most intelligent person is not the one who's best at doing any specific task, but it's the one who's best at picking up new things quickly.” [180] This ties in the idea that the members of society who are allowing their mind to accept new ideas are more intelligent. They can be part of Collective Intelligence, but not actually be intelligent as they have a limited range of options and ideas, and therefore can be put in the Hive Mind category.
Social Networking Sites
[edit | edit source]
Social Networking Sites (SNS) such as Facebook and Twitter are starting to hinder societies' abilities to formulate their own ideas. Everyone is using these sites to vent their opinions and are very raw and uncut. If you follow users and accounts online this is the only content you see and it starts to become very biased as you click on what you want to see. Unlike newspapers, social media sites give you the side of the argument you follow. This has become much more of a problem in recent years. During the 2014 Scottish Referendum it was thought that the Yes Campaign would win as they were the louder voices on social media, but it was actually the Better Together Campaign that won the Referendum. The vote was 2,001,926 (55.3%) to 1,617,989 (44.7%). The ability to place a banner of ‘Yes’ or ‘Better Together’ on top of profile pictures during the Referendum shows how much of an impact SNS had on people’s political views. Seeing other people’s opinions can quickly change other users opinions as you read into what the people you are following are saying. Glasgow University analysed 2.8 million tweets in the lead up to the vote and claimed that the ‘Better together’ campaign lost the social media battle. The statistics below support this statement. [181]
| Social Media Site | Yes Followers | No Followers |
|---|---|---|
| Official Twitter Campaigns | 103,000 | 42,000 |
| Nicola Sturgeon | 66,000 | xxx |
| Alex Salmond | 95,000 | xxx |
| Alastair Darling | xxx | 21,000 |
| Official Facebook Campaigns | 320,000 | 218,000 |
This is a strong example of Collective Intelligence and The Hive Mind. Not everything on the internet is true. Just because an opinion is expressed it does not mean that it is the final decision or correct one. It can be seen here that the ‘Yes’ campaign has more social media support, allowing society to believe that it was going to win the Historic Vote. This is why users online should question all the information they read, and ask themselves if they are reading information on the whole topic or if they are getting stuck in the Hive Mind of society.
Politics
[edit | edit source]Pierre Lévy and the fall of Communism
[edit | edit source]Pierre Levy believes that power lies in the careful management of knowledge, and governments must identify where that knowledge lies and organise it accordingly taking full advantage of people’s skills thus creating a collective intelligence. Levy suggests therefore the communist governments began to decline in the seventies and then finally collapsed in the early nineties because they were unable to follow the transformation of labour to technological and organized structure. “Totalitarianism collapsed in the fate of new forms of mobile and cooperative labour. It was incapable of collective intelligence”. [183]
Democracy and Collective Intelligence
[edit | edit source]Hélène Landemore is a professor of political science who is interested in democratic theory. In her article The Mechanisms of collective Intelligence in politics, Landemore discusses the argument for democracy stating "that many heads are better than one". It has been suggested, especially in politics that a select few of the most intelligent people among us ought to beat the rule of regular people. However, Landemore does not agree with this stating that “Even the best and brightest need not be generally smarter than the rule of the many because of the crucial role of one component of collective wisdom, namely ‘cognitive diversity’ or the existence within the group of multiple ways to see the world and interpret it”. Different races, cultures, sex, sexuality etc can group their collection of experiences and skills to come together as one, creating a vast amount of knowledge. [184]
John Stuart Mill's truth and fallibility argument
[edit | edit source]
John Stuart Mill was an advocate for democracy and believed everyone should be able to express their own opinions. “If all mankind minus one, were of one opinion, and only one person were of the contrary opinion, mankind would be no more justified in silencing that one person, than he, if he had the power, would be justified in silencing mankind.” What Mill means in this quotation is that everyone is entitled to expressing their own opinion without it being censored, even if it is one person’s belief against the majority. Humans have been wrong in the past and governments have censored people that have tried to share their own beliefs. Often these beliefs held by one person which have been censored later become the common beliefs throughout humanity after they have been proven correct through discussion. [185]
It is therefore important to acknowledged someone as an an intelligent being as highlighted by Pierre Lévy in his writings of "What is collective intelligence?" Levy makes the point that not identifying someone as an intelligent being to deny them a social identity. We therefore must identify skills and put them to use. " Not only does it lead to improved skills administration in business and community environments, it also possesses an ethical and political dimension". [186]
Social Media and Politics
[edit | edit source]Through online platforms individuals can come together and express their political views through discussion and hopefully come to a better understanding and conclusion by sharing their ideas. Through platforms such as Facebook, young people can become politically active as it gives them a place to share their ideas and political views. “young people who are involved in online communities become more engaged in politics. Even when these groups involve shared interests like fashion or gaming that are not explicitly political, they encourage political engagement". Through social media young people learn skills which can be applied to a political cause. "When they see online discussions spill over into social issues, they come to pay closer attention to politics. They are more likely to be encouraged to vote or to take some other political action". [187]
Clicktivism
[edit | edit source]
However there are acts carried out online which are sometimes describes as low-threshold such as “clicktivism”. By clicking a mouse can we really say that we are being active and participating in political discourse. “Are they simply meaningless, or are they a valid new form of participation that challenge normative notions of democracy and participation”. By liking a comment or sharing a video will enable other people on social media to view the information that has been shared, so perhaps this is a new form of democracy. “Are they simply meaningless, or are they a valid new form of participation that challenge normative notions of democracy and participation”. Clicktivism does not only take place on social media, it can also be used to organise protests, sign petitions and facilitate boycotting thus help spread awareness to a specific cause. So perhaps "clicktivism" can lead to people participating and becoming active in political discourse.[188]
Aesthetics
[edit | edit source]Pierre Lévy describes collective intelligence as a form of ‘universally distributed intelligence, constantly enhanced, coordinated in real time, and resulting in the effective mobilization of skills’[189], and notes that one of its indispensable characteristics is ‘the basis and goal of collective intelligence is the mutual recognition and enrichment of individuals rather than the cult of fetishized or hypostatized communities'. In essence, individual knowledge utilized to enhance the knowledge of the masses; without stratification of its worth based on social factors such as class, race, etc. An awareness of this exists beyond academic analysis of collective intelligence, but also in the consciousness of real people producing online texts in an online climate. One of these real people is Neil Beloufa, a 31-year-old video artist and sculptor whose work deals with hyper reality and human relations, who said “We don’t have hierarchy of knowledge any more, [according to YouTube] Keyboard Cat is more famous than Barack Obama, and a 14-year-old can write an article on Wikipedia. I grew up with that loss of hierarchy of imagery: anyone can say anything about anything."[190]
The Distribution and Consumption of Art, Pre-Cyberspace
[edit | edit source]
In describing how aesthetics function as a component of collective intelligence, Lévy noted that cyberspace 'brings with it methods of collective perception'. This method of collective perception is a subversion of centuries of Western artistic phenomenon, which can roughly be accounted as a person signs an object or individual message, which other persons consume with appreciation, interpretation, etc. The short hand way of conveying this would be to say that ‘the artist signs their work, then recipients consume it'; and examples would include conventional media such as films, television shows, and books. Again, this is articulated by Lévy, who wrote that ‘transmitter and receiver are clearly differentiated and their roles uniquely assigned’.
The Distribution and Consumption of Art, Post-Cyberspace
[edit | edit source]An intrinsic part of technology is that it is constantly evolving; and it is not simply not realistic to attempt to predict a finite impact that cyberspace, and the collective intelligence it aids, will have on various art forms. As Lévy rather dramatically suggests, cyberspace could as easily 'presage, or even incarnate, the terrifying, often inhuman future revealed to us by science fiction' as it could engage with collective intelligence and become 'replete with culture, beauty, intellect, and knowledge'. He heavily emphasizes that the masses are in control of our technological future, and have the ability to progressively interconnect and provide an interface for the various methods of creation, recording, communication, and simulation.
The Hive Mind
[edit | edit source]The term 'hive mind' is usually associated with insects such as ants or bees. Individually, these insects are not considered to be intelligent. However, when they act as a collective and access the 'hive mind' (the collective knowledge of all the insects in the hive), they are able to do extraordinary things. However, with the coming of Web 2.0, media turned social and 'Hive mind' is now a term that can be applied to the Internet and how humans interact with the Internet. Web 2.0 promotes many-to-many connectivity, decentralised forms and control and is user-focused and user-friendly. For example, collaborative content production such as Wikipedia and social networking sites like Facebook or Twitter.
There is now an infrastructure in place to support these global social networks and people from all over the world are able to share their knowledge and learn from others through the Internet:
"When we are online, we are essentially linked to a vast hive mind, known in psychology as a transactive memory system, which allows us to access the collective knowledge of anyone and everyone." [191]
However, as good as this idea of the 'hive mind' sounds, there are many problems associated with it. As Jaron Lanier (2006) says: "The hive mind for the most part is boring and stupid. Why pay attention to it?" [192]
Problems of the Hive Mind
[edit | edit source]Lower Standards
[edit | edit source]As the amount of information available on the Internet continues to expand, our ability to navigate this information becomes ever more important or we could be swamped with Information Overload. One way to achieve this is to use distributed moderation and filtering systems which aggregate information (such as likes or up-votes) and this information is used to rank and sort items, with the most popular items being placed in positions of greater importance, such as the on the "home page" or "front page" of websites. [193] However, the problem associated with this method of information sorting is that there is no person in charge of deciding what is important or interesting, only an algorithm.
This is a problem that Jaron Lanier identifies when discussing what he calls "Meta-aggregator sites", such as social news sites reddit or Digg. These sites use algorithms rather than people to determine what the most relevant news is but Lanier believes that this method is not as effective. Despite this, people are willing to overlook its deficiencies because it is new and something which resembles Artificial Intelligence:
in "the race to erase personality and be most Meta... there's a presumption that something like a distinct kin to individual human intelligence is either about to appear any minute, or has already appeared. The problem with that presumption is that people are all too willing to lower standards in order to make the purported newcomer appear smart. Just as people are willing to bend over backwards and make themselves stupid in order to make an AI interface appear smart so they are willing to become uncritical and dim in order to make Meta-aggregator sites appear to be coherent."[192]
There is also a concern that people may become over-reliant on the Internet to provide them with information. Rather than simply try to remember the information themselves, in time, people may find it easier to access the "hive mind" of the Internet to find any information they need. This is why Lanier believes that it is essential that people continue to see the Internet as a tool for connecting people and sharing information rather than as an all-knowing entity that can provide them with information. "The beauty of the Internet is that it connects people. The value is in the other people. If we start to believe the Internet is an entity that has something to say, we're devaluing those people and making ourselves into idiots." [192]
Deindividuation/Invisibility in Crowds
[edit | edit source]One of the main theories behind Collective Intelligence is that working as a collective will enhance individuals. As Pierre Lévy (1999) says: "The basis and goal of collective intelligence is the mutual recognition and enrichment of individuals rather than the cult of fetishized or hypostatized communities." [194] However, this is not always the end result of Collective Intelligence. Often, people find it easier to remain anonymous in a large group and prefer to go along with the general consensus rather than put forward their own ideas. This is something Jaron Lanier has observed in the online world of wikis and meta-aggregation:
"I've participated in a number of elite, well-paid wikis and Meta-surveys lately and have had a chance to observe the results. What I've seen is a loss of insight and subtlety, a disregard for the nuances of considered opinion, and an increased tendency to enshrine the official or normative beliefs of an organisation"[192]
There is less risk associated with going along with the most popular idea, it is safer not to voice your own opinion which may go against the general consensus.
In its most extreme form, this can potentially lead to something called "deindividuation" which is basically a loss of self-awareness when in a group. Deindividuation is mostly unconscious and more likely to lead to mischief. [195] Psychologist David G. Myers describes it as "doing together what you would not do alone." It can potentially have some very negative outcomes, such as cyberbullying.
Cyberbullying
[edit | edit source]Most of us like to believe that we are individuals and unique in some way or another. But this individuality can often be wiped away when we are part of a large group. We lose ourselves to a group mentality and often do or say things that we would not if we were alone. A little encouragement from one member of the group is sometimes all it takes for a person to lose themselves in the group and do things they would not normally do, such as verbally abuse someone online.[196]
Anne R. Allen discusses cyberbullying at length in one of her blog posts and she believes that the hive mind mentality that can develop due to deindividuation is one of the main issues that contributes to cyberbullying. "I think the most egregious abuses spring from something far more dangerous than the lone anonymous troll: 'groupthink' aka the 'hive mind'". [197] She also discusses a quote attributed to psychology pioneer William James: "there's nothing so absurd that if you repeat it often enough, people will believe it." With social media sites such as Facebook or Twitter, this kind of mass repetition is more dangerous than ever. People are able to globally spread falsehoods or abusive posts that contribute to cyberbullying in just a few minutes. Anne R. Allen also believes that once someone has entered into this "hive", they feel a compulsion to repeat themselves as if to prove that they are right. This hive mentality also makes it almost impossible to reason with individual members of the hive because they have lost their individuality.
"Members of a 'hive' that has perpetuated a falsehood or misinterpretation of facts fuel a narcissistic compulsion to keep repeating it - to 'prove' their own righteousness... Once an individual joins in an attack on a designated victim, s/he becomes assimilated into the collective hive mind and seems to lose the ability to behave as an individual." [197]
Lack of Real Engagement
[edit | edit source]
It has become a concern for some people that it is now too easy to sign a petition, support a charity, or show solidarity for a cause online. People follow whatever is popular or trending at the time, whether it is doing the Ice Bucket Challenge for ALS or changing your profile picture to include the French flag after the terrorist attacks in Paris 2015, without giving any real thought to the issues. A couple of clicks to show your support and it is done, never to cross your mind again.
"In our social media age, we demonstrate empathy in the easiest way possible - a few mouse clicks - much like the knee-jerk dropping of a few coins into a peddler's can, without much reflection whether such act of sympathy would make a difference, as long as the gut-felt emotion is relieved." [198]
The days when political action required careful planning and serious thought appears to be disappearing and replaced by a few mouse clicks. But do the mouse clicks actually amount to anything other than making yourself feel better?
Social News
[edit | edit source]Social news (e.g. reddit) provides an alternative to conventional news media in determining what 'the news' should be. Rather than having an editor deciding which stories to publish and where to place them as happens in traditional news media, the role of an editor is fulfilled by the users in social media. The placement of items is decided by an algorithm which accounts for the up-votes and down-votes of the users and places the most popular posts in the most visible locations, with users hoping to reach the "front page" of the site.
This method of deciding what is 'newsworthy' has its flaws. As increased visibility ultimately leads to increased voting activity, it is possible that content which goes against the majority view of users could be suppressed. "The 'rich get richer' mechanisms which these websites are built on would suggest that for any controversial issue opinions which are opposed to that of the majority will potentially be excluded from prominent locations."[193]
Another problem associated with social news sites is the repetition of content. Rather than try to come up with their own individual, original content, many users conform to the hive mind of the site and attempt to replicate content that has proven to be successful.
"Reddit's penchant for up-voting certain types of post is often discussed by users. The tendency for users to submit posts of a type which have previously been received well is known in the community as 'circlejerking' - and a sub-reddit exists for the purpose of highlighting and satirising these trends (the 'circlejerk' sub-reddit). This, and the perception that posts which go against commonly held beliefs or movements are always down-voted, are two of the main characteristics of what reddit users often refer to as the 'reddit hive mind.'" [193]
Potential of the Hive Mind
[edit | edit source]Despite the potential problems associated with the hive mind, it can be a useful tool in certain situations. As Jaron Lanier, a critic of the hive mind, says:
"The collective is more likely to be smart when it isn't defining its own questions, when the goodness of an answer can be evaluated by a simple result (such as a single numeric value,) and when the information system which informs the collective is filtered by a quality control mechanism that relies on individuals to a high degree. Under these circumstances, a collective can be smarter than a person. Break any one of these conditions and the collective becomes unreliable or worse... Every authentic example of collective knowledge that I am aware of also shows how that collective was guided or inspired by well-meaning individuals. These people focused and in some cases also corrected for some of the common hive mind failure modes." [192]
An example of this could be Wikipedia. Often considered to be one of the champions of the Web 2.0 movement, praised for the collaborative nature of its knowledge production. In fact, as Niederer & van Dijck (2010) show, much of Wikipedia's content has been produced by a small core of dedicated individuals rather than a horde of anonymous users particularly during the first five years of its existence. [199] These well-meaning individuals have helped to guide the production of Wikipedia content rather than allow it to be overwhelmed by a hive of anonymous users.
The Sociology of the Collective Intelligence and Hive Mind
[edit | edit source]
Human societies have distinctly evolved and advanced alongside each progressive shift in technology. As both the minority and majority worlds are in the midst of the informational revolution, the technology utilised by human conscious is a matter of sociological investigation. It is necessary to understand technology’s place in relation to how society is structured, and how Web 2.0 has socialised individuals across cultures.
The Socio-Technological Paradigm Shift
[edit | edit source]The improvement of technology used by humans throughout our history, has resulted in societal-revolutions found within the collective conscious. The overlaps with each development from these socio-technological advancements results in paradigm-shifts. These shifts occur within the collective intelligence and correspond to the advancement of technology. The progressions observed are results of human beings collaborating with one another.
These shifts are highlighted below:

- from foraging
- to hunting & gathering
- to horticulture (hand-used tools)
- to agrarian (using animal drawn plough)
- to industrial
- to informational (currently the paradigm we are living in) [200]
These shifts in lifestyle innovation and information progression, display how human societies are constantly striving and moving forward into a more structurally sound future.
Lanier reaffirms that human beings are worth cherishing because of their rich, distinctive, individual, natures, not because of they are simple and predictable [201]. He gives the example that YouTube and Flickr work exceptionally well because they enable users to create content, with each unit of collaboration being relatively substantial there in of itself. Unlike Marx’s understanding of the product of labour under capitalisms (which is when the individual feels alienated from their work), this perspective contests that classical understanding. It is difficult to determine if that means the internet exists in a post-capitalist bubble, or Marx’s writings regarding the work produced by an individual social agent can not be applied to the technology of the internet.
Hive-Mind Enthusiasts
[edit | edit source]There are many sociological pioneers who, in recent years, who enthusiastically praise the Hive-Mind structure that Web 2.0 possesses. They mainly consider the way we very rapidly have been socialised to interact with and comprehend digital media in a new way, fundamentally groundbreaking. They argue that nothing like this societal shift in communication has happened before. Thoman and Joss could be considered Hive-Mind enthusiasts, they explain that our adoption of New Media literacy is incredibly complex: “To be a functioning adult in a mediated society, one needs to be able to distinguish between different media forms and know how to ask basic questions about everything we watch, read, or hear,” [202]. This ability that now many people have is unlike anything seen before, and it purely a result from the way structure of society and how technology has permeated culture to promote this New Media literacy. Other hive-mind enthusiasts such as Clay Shirky and Charles Leadbeater, are enthusiastic about pragmatic, rational collaborations. These scientific and qualitative collaborations to study information work wholly more effectively than more expressive and creative endeavours; "challenging the traditional view that intelligence is an attribute of individuals, the distributed cognition perspective holds that intelligence is distributed across “brain, body, and world", [to achieve] high-quality mush – full collaborations at a fine grain level”[203].
Marx's Notion of Alienation
[edit | edit source]
Technological Estrangement
[edit | edit source]When Marx was writing about alienation during the industrial revolution, he observed workers carrying out monotonous tasks on the production line which alienated them, not only from the product of their labour, but also each other. This separation and exclusion can perhaps still be seen today, as technology in the workplace has evolved. In the mid 20th century alienation was observed predominantly in bureaucracies and the service industry as they regulated autonomy. In the book Labour and Monopoly Capital, Braverman spoke about how the degradation of the jobs available to the working class resulted in a mass “deskilling”[204] millions of workers across the contemporary capitalist economy. Many other thinkers in the field argue that as a result of the proliferation of the technological Collective Intelligence, it has resulted in the population being dumbed down [205]. These ideas address the capability of technology as society progresses, but also the Marx’s notion of alienation. Through transformations like automation, fragmentation of companies, and outsourced processing; alienation is said to be felt be many across the contemporary working world.
In Marx’s wider understanding of alienation, he addresses estrangement from other people, ourselves, the external world, and “human essence” [206]. This idea in relation to the internet is particularly controversial. On the one had Web 2.0 has constructed an open, unregulated institution which comprises of peer collaboration, communication and comprises of a decentralised leadership. The internet has the ability to inspire the “phenomenon of individual intelligence” within a hive-minded structure [207]. The internet can be seen as a tool to democratise information and communication. This is something that Marx almost prophesised; the "accumulation of knowledge and of skill, [which materialises through the] productive forces of the social brain"[208]. This statement can be viewed in a way to outline the collective conscious, and how it has merely migrated to a more accessible plane – the internet. Therefore, the perhaps the opposite of alienation has emerged; unity across cultures has been accomplished.
Novel Alienation
[edit | edit source]Many voices, however, dispute this viewpoint and consider the technology in a contemporary context to be alienating to the user. There is a claim that the individual is alienated from “real life” when they participate in “cyber life” [209]. This novel form on alienation, can be said to only further isolate individuals. Isolation from; others (through decreased social interaction), and the human-essence (through lack of meaningful, creative stimulation). The sort of paradigm the internet exists as should be seen as a tool rather than a product in itself. With this perspective, perhaps it can be viewed more objectively, as a pragmatic system containing vast information and data – with the power to transform the planet into a global village [210].
Societal Impact of the Hive-Mind
[edit | edit source]Real World Examples
[edit | edit source]There are many examples where the Collective Intelligence is employed by society in reaction to real-world problems. The case study and examples below are observed by contemporary sociologists as outstanding examples which highlight the constructive power of the collective intelligence and hive mind.
Hurricane Katrina
[edit | edit source]In 2005 citizens affected by the hurricane and flooding proactively shared their own self-produced media and began sharing information in order to trend online, to draw attention to the situation. In Confronting the Challenges of Participatory Culture Jenkins speaks comprehensively about the disaster.
"After Jonathan Mendez’s parents evacuated from Louisiana to his home in Austin, Texas, he was eager to find out if the floods had destroyed their home in Louisiana. Unfortunately for him, media coverage of the event was focused exclusively on the most devastated parts of "New Orleans, with little information about the neighbourhood where his parents had lived. With some help from his coworker, they were able, within a matter of hours, to modify the popular Google Maps Web service to allow users to overlay any information they had about the devastation directly onto a satellite map of New Orleans. Shortly after making their modification public, more than 14,000 submissions covered their map." [211]

As a result of this many of the victims, and families of those affected by the hurricane and the damage it wrecked on the community were able to reach out into a relatively new domain to appeal for help - the internet. The lack of mainstream media's attention to help assist with the floods etc. meaning thousands of lives were saved. The amalgamation of people and minds from all around the globe was one of the first examples to support the constructive societal process, carried out by the hive mind. This democratised pursuit to help as many people as possible was unimaginable 15 years ago, but now so many other socio-political movements would have not been possible were it not for the online community and collective intelligence.
These include:
- The Black Lives Matters protests - held in the US as a direct response to police brutality and murder of many innocent, African American citizens. These were made possible through the persistent trending of victims names, and the wide spread, online talk surrounding the issue.
- The Arab Spring - many governments throughout the Arab world, were democratically overthrown by its citizens. Due to the censorship of information online and in the mass media, the only way for these recent revolutions to have had occurred was through the utilisation of the Collective Intelligence online.
Glossary
[edit | edit source]- Aesthetics
- The principles underlying the work of a particular artistic movement.
- Artificial Intelligence
- The theory and development of computer systems able to perform tasks normally requiring human intelligence, such as visual perception, speech recognition, decision-making, and translation between languages.
- Cognitive Diversity
- The power of having cognitive diversity in the workplace is the same power that companies try to attain through strong leadership and great communication. It's a more inclusive, collaborative, and open space where people feel empowered to create and implement ideas.
- Collective Intelligence
- A group intelligence which is formed by contributions from a wide range of people.
- Cyberbullying
- The use of electronic communication to bully a person, typically by sending messages of an intimidating or threatening nature.
- Cyberspace
- A perceived environment in which communication occurs over a computer network.
- Deindividuation
- The loss of self-awareness in groups.
- Filter Bubbles
- A filter bubble is a result of a personalized search in which a website algorithm selectively guesses what information a user would like to see based on information about the use.
- Hive Mind
- A collective consciousness, analogous to the behaviour of social insects, in which a group of people become aware of their commonality and think and act as a community, sharing their knowledge, thoughts and resources.
- Such a group mentality characterised by uncritical conformity and loss of a sense of individuality and personal accountability.
- A distributed memory that both perceives and remembers.
- Information Overload
- Exposure to or provision of too much information or data.
- Interface
- A device or program which enables users to communicate with others.
- Knowledge Labour
- Labour based on learning knowledge rather than capital
- Meta-aggregation
- A method of systematic review that mirrors the processes of a quantitative review whilst holding to the traditions and requirements of qualitative research (it aggregates findings into a combined whole that is more than the sum of the individual findings in a way that is analogous with meta-analysis).
- Smart Mob
- A group that uses modern technology to coordinate and communicate.
- Social Media
- Websites and applications that enable users to create and share content or to participate in social networking.
- The collective of online communications channels dedicated to community-based input, interaction, content-sharing and collaboration (e.g. forums, microblogging, social networking, social bookmarking, social curation, and wikis).
- Social Networking Sites
- A place online where users can create accounts and share options and follow content
they agree with and like.
- Social News
- A much more personalised form of news consumption, delivered on a central platform (like Facebook, Twitter, Reddit, etc.) according to how users engage with news stories from various sources.
- Subscription
- An arrangement to receive something, typically a publication, regularly by paying in advance or an arrangement by which access is granted to an online service.
- Web 1.0
- Web 1.0 refers to the first stage in the World Wide Web, which was entirely made up of Web pages connected by hyperlinks
- Web 2.0
- The second stage of development of the Internet, characterised especially by the change from static web pages to dynamic or user-generated content and the growth of social media.
- Wiki
- A website or database developed collaboratively by a community of users, allowing any user to add and edit content.
References
[edit | edit source]- ↑ https://books.google.co.uk/books/about/Rise_and_Burst_of_the_Dotcom_Bubble.html?id=7UOykx3ntYMC&redir_esc=y
- ↑ https://books.google.co.uk/books?id=4eICEV1uN7gC&dq=inauthor:%22Mats+Lindgren%22&hl=fr
- ↑ https://books.google.co.uk/books?id=cd9vBAAAQBAJ&pg=PT66&lpg=PT66&dq=i+love+you+virus+academic&source=bl&ots=U3TeMOo2Pg&sig=YUBvvxCbdVQFkjNVQToOuFvbWhE&hl=fr&sa=X&ved=0ahUKEwiU1JvdmsDSAhViLcAKHaURCk0Q6AEIQjAF#v=onepage&q=i%20love%20you%20virus%20academic&f=false
- ↑ http://www.internetworldstats.com/emarketing.htm
- ↑ http://bootcampdigital.com/81-of-firms-are-using-social-media-for-marketing-cmo-survey/ Percentage of Firms Using Social Media in their Marketing Activities
- ↑ https://www.statista.com/statistics/272014/global-social-networks-ranked-by-number-of-users/ Statistics of monthly users on Social Platforms
- ↑ http://www.emeraldinsight.com/doi/abs/10.1108/QMR-06-2013-0041 Why People Use Social Media: Uses and Gratifications
- ↑ http://www.socialmediatoday.com/content/why-do-people-use-social-media Why do People Use Social Media?
- ↑ http://www.upworthy.com/researchers-studied-the-impact-of-online-dating-on-relationships-heres-what-they-found
- ↑ http://www.therapyin.london/constant-stimulation/ Is the Physical World not Enough?
- ↑ https://www.internetmatters.org/parental-controls/entertainment/ Entertainment and Search Engines
- ↑ https://www.aol.com/article/entertainment/2017/03/06/emma-watson-vanity-fair-topless-photo-shoot-controversy/21874456/ Emma Watson Vanity Fair Controversy
- ↑ http://fortune.com/2016/06/08/online-shopping-increases/ Online Shopping Increases
- ↑ http://recursostic.educacion.es/secundaria/edad/3esoingles/3quincena9/impresos/shopping_trends.pdf Benefits of Online Shopping
- ↑ https://blog.kissmetrics.com/facebook-statistics/ Facebook Statistics
- ↑ http://www.statisticbrain.com/instagram-company-statistics/ Instagram Statistics
- ↑ https://blog.bufferapp.com/psychology-of-facebook Psychology of Facebook
- ↑ https://csmt12.wordpress.com/tag/voyeuristic-tendencies/ Voyeuristic Tendencies
- ↑ http://www.emeraldinsight.com/doi/abs/10.1108/QMR-06-2013-0041 Why People Use Social Media: Uses and Gratifications
- ↑ http://www.telegraph.co.uk/goodlife/11751851/Facebook-is-the-most-popular-social-network-for-the-over-50s.html/ Facebook is the Most Popular Social Network for the Over 50's.
- ↑ https://www.silversurfers.com/
- ↑ http://www.careerbuilder.co.uk/share/aboutus/pressreleasesdetail.aspx?sd=4%2F28%2F2016&id=pr945&ed=12%2F31%2F2016
- ↑ http://www.businessinsider.com/twitter-fired-2011-5?IR=T
- ↑ http://www.elle.com/fashion/news/a42120/dolce-gabbana-fall-2017-mens-show-millennials/ Dolce Gabbana Fall 2017
- ↑ http://os-fashion.com/magazine/impact-of-digitial-influencers/ Impact of Social Influencers
- ↑ Trottier, D. (2012) ‘'Social Media as Surveillance: Rethinking Visibility in a Converging World’' (1st ed.). Routledge
- ↑ http://www.danah.org/papers/2010/SNSasNetworkedPublics.pdf Danah Boyd SNS as Networked Publics
- ↑ http://www.berkeleyside.com/wp-content/uploads/2014/02/2013SurveyResults.pdf Police Survey Results
- ↑ Participation in the Always-On Lifestyle, danah boyd, featured in The Social Media Reader, Mandiberg, 2012
- ↑ Turkle, S., The Tethered Self, p.2, 2006 featured in Handbook of Mobile Communications and Social Change, Kats, J.
- ↑ https://www.ofcom.org.uk/about-ofcom/latest/media/media-releases/2015/cmr-uk-2015
- ↑ Turkle, S., The Tethered Self, p.2, 2006 featured in Handbook of Mobile Communications and Social Change, Kats, J.
- ↑ Participation in the Always-On Lifestyle, danah boyd, featured in The Social Media Reader, Mandiberg, 2012
- ↑ Psychology and the Internet: Intrapersonal, Interpersonal, and Transpersonal Implications, Jayne Gackenbach & Heather von Stackleberg, 2011
- ↑ The Online Disinhibiton Effect, John Suler, Cyber Psychology & Behaviour, Vol 7, No. 3, 2004
- ↑ https://nobullying.com/cyber-bullying-statistics-2014/
- ↑ The Online Disinhibiton Effect, John Suler, Cyber Psychology & Behaviour, Vol 7, No. 3, 2004
- ↑ Infoglut: How too much information is changing the way we think and know, Mark Andrejevic, 2013
- ↑ http://www.telegraph.co.uk/technology/7858189/Are-Twitter-and-Facebook-affecting-how-we-think.html
- ↑ Flew, T. (2008) New Media: An Introduction (3rd ed.). Oxford: Oxford University Press
- ↑ Donelan, H., Kear, K., and Ramage, M. (eds), (2010) Online Communication and Collaboration: a Reader. London: Routledge
- ↑ http://www.everydayhealth.com/internet-addiction/guide/
- ↑ Roberts, (2006). Micro Social Theory. London: Dalgrave
- ↑ http://www.huffingtonpost.com/2012/10/11/facebook-psychology-7-reasons_n_1951856.html/ Facebook Psychology: 7 Reasons We Act Differently Online
- ↑ Swingle, M, K. (2016). i-Minds: How Cell Phones, Computers, Gaming and Social Media are Changing Our Brains, Our Behavior and the Evolution of Our Species. Canada: New Society Publishers
- ↑ Rice, J. (2009). The Church of Facebook. 1st ed. Colorado Springs, CO: David C. Cook.
- ↑ Surowiecki, J. (2004). The Wisdom of Crowds. New York: Doubleday
- ↑ http://www.independent.co.uk/life-style/gadgets-and-tech/features/google-effect-is-technology-making-us-stupid-10391564.html/ Google Effect: Is Technology Making Us Stupid?
- ↑ http://science.sciencemag.org/content/early/2011/07/13/science.1207745
- ↑ https://journalistsresource.org/studies/society/internet/google-effects-memory-cognitive-consequences
- ↑ http://resourcelists.stir.ac.uk/link?url=http%3A%2F%2Fstir.eblib.com%2Fpatron%2FFullRecord.aspx%3Fp%3D684281&sig=23bd45212245e7eddbe334594a9b77ad3f0fc8a6b1cdf5ac8f02a6bb52401ff3 Alone Together: why we expect more from technology and less from each other.
- ↑ http://www.simplypsychology.org/Erik-Erikson.html Erik Erikson
- ↑ Cohen, S. (2002). Folk Devils and Moral Panics: The Creation of Mods and Rockers (3rd ed). New York: Routledge
- ↑ Krinskey, C. (eds). (2008). Moral Panics over Contemporary Children and Youth. New York: Routledge
- ↑ http://www.safetynetkids.org.uk/personal-safety/staying-safe-online/
- ↑ Newburn, T. (2013). Criminology. 1st Ed. London: Routledge
- ↑ http://www.mirror.co.uk/news/uk-news/distressing-video-reveals-how-facebook-9560118
- ↑ Belinda Goldsmith. "RPT-Is Facebook envy making you miserable?"
- ↑ Gonzales, A. L., & Hancock, J. T. (2011). Mirror, mirror on my Facebook wall: Effects of exposure to Facebook on self-esteem. Cyberpsychology, Behavior, and Social Networking, 14(1-2), 79-83.
- ↑ Chou, H. T. G., & Edge, N. (2012). “They are happier and having better lives than I am”: the impact of using Facebook on perceptions of others’ lives. Cyberpsychology, Behavior, and Social Networking, 15(2), 117-121.
- ↑ http://digimed-jhi.pbworks.com/f/Stald%20Mobile%20Identity.pdf Mobile Identity: Youth, Identity and Mobile Communication
- ↑ https://sleep.org/articles/ways-technology-affects-sleep/ Scary Ways Technology Affects Your Sleep
- ↑ http://resourcelists.stir.ac.uk/link?url=http%3A%2F%2Fstir.eblib.com%2Fpatron%2FFullRecord.aspx%3Fp%3D684281&sig=23bd45212245e7eddbe334594a9b77ad3f0fc8a6b1cdf5ac8f02a6bb52401ff3 Alone Together: why we expect more from technology and less from each other.
- ↑ https://books.google.co.uk/books?hl=en&lr=&id=I8dPhB88Sx4C&oi=fnd&pg=PA107&dq=McLuhan&ots=CD3Gry9BbN&sig=osR20L0w3D7XHpjTpyHOtRMgHSE#v=onepage&q=McLuhan&f=false The Medium is the Message.
- ↑ https://ebookcentral.proquest.com/lib/stir/reader.action?docID=1180919 A Private Sphere
- ↑ http://sk.sagepub.com/books/key-concepts-in-media-and-communications/n30.xml Mobile Privatization.
- ↑ http://zizi.people.uic.edu/Site/Research_files/Look%20at%20meAMZP.pdf The Networked Self: Identity, Community on Social Network Sites.
- ↑ http://reagle.org/joseph/2014/fomo/fomo.htm
- ↑ http://www.bostonmagazine.com/news/article/2014/07/29/fomo-history/
- ↑ http://persweb.wabash.edu/facstaff/hortonr/articles%20for%20class/baumeister%20and%20leary.pdf
- ↑ http://www.sciencedirect.com/science/article/pii/S0747563213000800
- ↑ http://www.vipoa.org/neuropsychol/2/7
- ↑ http://www.vipoa.org/neuropsychol/2/7
- ↑ https://www.psychologytoday.com/blog/in-one-lifespan/201510/facebook-and-the-fear-missing-out-fomo
- ↑ http://www.independent.co.uk/life-style/gadgets-and-tech/news/fomo-we-really-do-hate-it-when-our-friends-on-facebook-become-successful-10023900.html
- ↑ http://time.com/4358140/overcome-fomo/
- ↑ Goffman, E. (2009). Stigma: Notes on the management of spoiled identity. Simon and Schuster.
- ↑ Goffman, E. (2005). Interaction ritual: Essays in face to face behavior. AldineTransaction.
- ↑ Goffman, E. (1969). Where the action is. Lane, Penguin Press
- ↑ http://web.pdx.edu/~tothm/theory/Presentation%20of%20Self.htm
- ↑ Goffman, E. (1978). The presentation of self in everyday life (p. 56). Harmondsworth.
- ↑ http://imaginingjustice.org/classroom/goffmans-ghost-art-acting-101-articulated/
- ↑ Bial, H. (2004). The performance studies reader. Psychology Press.
- ↑ https://www.slideshare.net/dchapple/goffman-and-the-online-world
- ↑ http://wearesocial.com/uk/blog/2017/01/digital-in-2017-global-overview
- ↑ http://llinsw.hypotheses.org/30
- ↑ Lanier, Jaron. (2010). Missing Persons. In You Are Not a Gadget: A Manifesto. (pp. 3-23). New York: Vintage.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ McLuhan, M. (1964). Understanding media: The extensions of man. New York: McGraw-Hill
- ↑ Walker Rettberg, Jill. "Seeing Ourselves Through Technology", 2014.
- ↑ D'Amico, Erika. "Why Instagram" in "The Elements of Libidinal Economy in Instagram", page 1, 2015.
- ↑ D'Amico, Erika. "Why Instagram" in "The Elements of Libidinal Economy in Instagram", page 1, 2015.
- ↑ D'Amico, Erika. "Why Instagram" in "The Elements of Libidinal Economy in Instagram", page 1, 2015.
- ↑ Digital Media and Society: An Introduction |Athique= |Adrian= |February 2013= |Digital Media and Society: An Introduction= |Polity= |978-0-7456-6228-2
- ↑ Williams, R. (1990 [1974]) Television: Technology and Cultural Form. London: Routledge.
- ↑ Walker Rettberg, Jill. "Seeing Ourselves Through Technology", 2014
- ↑ Hill, A. (1997). Shocking entertainment: Viewer response to violent movies. Luton, Bedfordshire, U.K: University of Luton Press.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ http://fansconf.a-kon.com/dRuZ33A/wp-content/uploads/2013/07/Who-You-Want-to-Be-Video-Games-as-Identity-Reflexive-Texts-by-James-Bales.pdf
- ↑ Turkle, S. Alone together: why we expect more from technology and less from each other, 2011, p.154
- ↑ Turkle, S. Alone together: why we expect more from technology and less from each other, 2011, p.214
- ↑ Brooks, David. “Overstiumlated Suburbia.” Picturing Texts. Ed Lester Faigley, Diana George, Anna Palchick, and Cynthia Selfe. New York: W.W. Norton & Company. 2004. 366- 373
- ↑ Turkle, S. Alone together: why we expect more from technology and less from each other, 2011
- ↑ http://waitbutwhy.com/table/online-dating-good-thing-bad-thing
- ↑ http://pegasus.cc.ucf.edu/~smathews/history.html
- ↑ http://www.nydailynews.com/life-style/one-third-u-s-marriages-start-online-dating-study-article-1.1362743
- ↑ http://www.vanityfair.com/culture/2015/08/tinder-hook-up-culture-end-of-dating
- ↑ https://www.theguardian.com/lifeandstyle/womens-blog/2014/mar/24/online-dating-lesbians-app-dattch-women
- ↑ http://www.telegraph.co.uk/science/2016/03/15/the-science-of-dating-why-we-should-stop-dating-online/
- ↑ https://medium.com/media-theory-and-criticism/tinder-ya-or-nah-1b0b02c2c9e1#.kl77wy7o1
- ↑ Papacharissi, Zizi. A Networked Self, edited by Zizi Papacharissi, Taylor and Francis, 2010
- ↑ http://www.telegraph.co.uk/science/2016/03/15/the-science-of-dating-why-we-should-stop-dating-online/
- ↑ http://www.buryfreepress.co.uk/news/opinion/shallow-pitfalls-of-online-dating-1-7357235
- ↑ https://books.google.co.uk/books?id=8erNPbPQdDoC&pg=PA33&lpg=PA33&dq=youtube+and+creation+of+identity&source=bl&ots=qWiT45CyxN&sig=ewP2f-EtSjY8ziHpmsemETUGGOM&hl=en&sa=X&ved=0ahUKEwj9jaCT2MLSAhUmKcAKHTWuCK04ChDoAQgfMAE#v=onepage&q=youtube%20and%20creation%20of%20identity&f=false
- ↑ Athique, A. Digital media and society: an introduction, 2013, Hoboken, NJ, p. 224 - 244
- ↑ Athique, A. Digital media and society: an introduction, 2013, Hoboken, NJ, p. 224 - 244
- ↑ Turkle, S. Alone together: why we expect more from technology and less from each other, 2011, p.265
- ↑ Turkle, S. Alone together: why we expect more from technology and less from each other, 2011
- ↑ Michael Mandiberg, American Council of Learned Societies, The social media reader, 2001, p.71
- ↑ |Downing= |Gary= |2013= |Virtual youth: non-heterosexual young people's use of the internet to negotiate their identities and socio-sexual relations= |http://www.tandfonline.com/doi/pdf/10.1080/14733285.2013.743280?needAccess=true= |Routledge= |10.1080/14733285.2013.743280
- ↑ |Downing= |Gary= |2013= |Virtual youth: non-heterosexual young people's use of the internet to negotiate their identities and socio-sexual relations= |http://www.tandfonline.com/doi/pdf/10.1080/14733285.2013.743280?needAccess=true= |Routledge= |10.1080/14733285.2013.743280
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Walker Rettberg, Jill. "Seeing Ourselves Through Technology", 2014.
- ↑ Walker Rettberg, Jill. "Seeing Ourselves Through Technology", 2014.
- ↑ Walker Rettberg, Jill. "Seeing Ourselves Through Technology", 2014.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Boyd, D. (2012). Participating in the always-on culture. In M. Mandiberg (Ed.), The Social Media Reader (pp. 71-76). New York: NYU Press
- ↑ Lanier, Jaron. (2010). Missing Persons. In You Are Not a Gadget: A Manifesto. (pp. 3-23). New York: Vintage.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Lanier, Jaron. "Digital Maoism : The Hazards of the New Online Collectivism", 2006.
- ↑ Understanding Media: The Extensions of Man= |McLuhan= |Marshall= |1964= |Understanding Media: The Extensions of Man= |Canada= |McGraw-Hill= |81-14-67535-7=
- ↑ Understanding Media: The Extensions of Man= |McLuhan= |Marshall= |1964= |Understanding Media: The Extensions of Man= |Canada= |McGraw-Hill= |81-14-67535-7=
- ↑ Williams, R. (1990 [1974]) Television: Technology and Cultural Form. London: Routledge.
- ↑ Williams, R. (1990 [1974]) Television: Technology and Cultural Form. London: Routledge.
- ↑ Lister, Martin, Dovey, Jon, Giddings, Seth New media: a critical introduction, Haboken, 2008 p. 77 - 75
- ↑ https://en.wikipedia.org/wiki/Cultural_determinism
- ↑ https://www.merriam-webster.com/dictionary/artificial%20intelligence
- ↑ http://www.dictionary.com/browse/app
- ↑ https://en.oxforddictionaries.com/definition/avatar
- ↑ https://en.wikipedia.org/wiki/Cyborg
- ↑ https://www.merriam-webster.com/dictionary/gamer
- ↑ http://www.dictionary.com/browse/hive-mind
- ↑ https://en.wikipedia.org/wiki/Impression_management
- ↑ https://www.britannica.com/topic/media-convergence
- ↑ https://www.google.co.uk/webhp?sourceid=chrome-instant&ion=1&espv=2&ie=UTF-8#q=definition+of+Meta&*
- ↑ https://www.merriam-webster.com/dictionary/collectivism
- ↑ https://en.wikipedia.org/wiki/Persona
- ↑ https://en.oxforddictionaries.com/definition/pseudonym
- ↑ https://en.oxforddictionaries.com/definition/social_media
- ↑ https://www.google.co.uk/webhp?sourceid=chrome-instant&ion=1&espv=2&ie=UTF-8#q=wikipedia+definition&*
- ↑ Lévy, Pierre (1997-08-21). Collective Intelligence. Basic Books. ISBN 9780306456350.
- ↑ Tom Atlee, The Universal Mind: The Evolution of Machine Intelligence and Human Psychology
- ↑ Howard Rheingold, Smart Mobs
- ↑ Geert Lovink, Zero Comments: Blogging and Critical Internet Culture
- ↑ Caitlin Dewey, How Internet sleuths on Facebook and Reddit solved the 20-year-old mystery of a missing teenager
- ↑ Howard Rheingold, Smart Mobs
- ↑ Sam Thielman, Yahoo hack: 1bn accounts compromised by biggest data breach in history
- ↑ Pierre Levy, [https://is.cuni.cz/studium/predmety/index.php? do=download&did=29658&kod=JJM085]
- ↑ David Gauntlett, [http://davidgauntlett.com/creativity/lego-cultures-of-creativity- report/]
- ↑ Tim O’Reilly, [https://books.google.co.uk/books? hl=en&lr=&id=DDI_XTmXI3MC&oi=fnd&pg=PA225&dq=web+2.0&ots=3FDbWzc3od&sig= 7PhCBERGbV6OMriBVAYee_qJObc#v=onepage&q=web%202.0&f=false]
- ↑ MIT: Collective Intelligence Research Centre, [14]
- ↑ Democracy Now, [https://www.democracynow.org/live/ inauguration_2017_live_coverage]
- ↑ David Gauntlett, [https://books.google.co.uk/books? id=DGW0tLoxqUsC&pg=PA184&lpg=PA184&dq=creativity+will+become+an+industrial+to ol+and+it’s+positive+potential+will+be+destroyed+david+gauntlett&source=bl&ots=YuJoda Nvog&sig=pZBQQuA5VMlDfhaoX6ZBPsdK_Eo&hl=en&sa=X&ved=0ahUKEwii9tfp9MTSA hWqCcAKHbRrBeoQ6AEIGjAA#v=onepage&q=creativity%20will%20become%20an%20in dustrial%20tool%20and%20it’s%20positive%20potential%20will%20be%20destroyed%20 david%20gauntlett&f=false]
- ↑ Thomas Malone, [https://www.edge.org/conversation/thomas_w__malone-collective- intelligence]
- ↑ Pierre Levy, [https://is.cuni.cz/studium/predmety/index.php? do=download&did=29658&kod=JJM085]
- ↑ Eli Pariser, [https://books.google.co.uk/books?hl=en&lr=&id=- FWO0puw3nYC&oi=fnd&pg=PT3&dq=filter+bubble&ots=g3OuIvtOUY&sig=i04jQUMuirl3q OF2-xhSAGrmO3Y#v=onepage&q=filter%20bubble&f=false]
- ↑ Pierre Levy, [https://is.cuni.cz/studium/predmety/index.php? do=download&did=29658&kod=JJM085]
- ↑ Thomas Malone, [https://www.edge.org/conversation/thomas_w__malone-collective- intelligence]
- ↑ Iain McLean, Jim Gallagher and Guy Lodge, [https://books.google.co.uk/books? hl=en&lr=&id=zm0FBAAAQBAJ&oi=fnd&pg=PR3&dq=scottish+referendum+vote+2014&ot s=Djz7ZlxD8x&sig=_e0d0aHzyC0NO_snmrYeh9ClY1g#v=onepage&q=scottish%20refere ndum%20vote%202014&f=false]
- ↑ Iain McLean, Jim Gallagher and Guy Lodge, [https://books.google.co.uk/books? hl=en&lr=&id=zm0FBAAAQBAJ&oi=fnd&pg=PR3&dq=scottish+referendum+vote+2014&ot s=Djz7ZlxD8x&sig=_e0d0aHzyC0NO_snmrYeh9ClY1g#v=onepage&q=scottish%20refere ndum%20vote%202014&f=false]
- ↑ ,Pierre Lévy[https://is.cuni.cz/studium/predmety/index.php?do=download&did=29658&kod=JJM085 ]
- ↑ ,Hélène Landemore[http://www.sas.upenn.edu/ppe/documents/Landemore_DemocraticReason_Article_Version_for_UPenn.pdf ]
- ↑ , John Stuart Mill [http://www.bartleby.com/130/2.html ]
- ↑ , Pierre Levy [15]
- ↑ ,Benjamin Bowyer and Joseph Kahne [16]
- ↑ , Simon Lindgren [https://www.researchgate.net/publication/284715731_The_Work_of_Audiences_in_the_Age_of_Clicktivism_On_the_Ins_and_Outs_of_Distributed_Participation ]
- ↑ Lévy, Pierre (1999). "What is Collective Intelligence?". in Lévy, Pierre. Collective intelligence: mankind's emerging world in cyberspace. Perseus Books. pp.117-129
- ↑ Alive Vincent, http://www.telegraph.co.uk/culture/art/art-features/11130492/How-has-the-internet-changed-art.html, 2014 [accessed 7 March 2017]
- ↑ Jones, Orion. "The Internet as Hive Mind". bigthink. bigthink. Retrieved 04/03/2017.
{{cite web}}: Check date values in:|access-date=(help) - ↑ a b c d e Lanier, Jaron (29/05/2006). "DIGITAL MAOISM: The Hazards of the New Online Collectivism". Edge. John Brockman. Retrieved 28/02/2017.
{{cite web}}: Check date values in:|access-date=and|date=(help) - ↑ a b c Mills, Richard (2011). "Researching Social News: Is reddit.com a mouthpiece for the 'Hive Mind', or a Collective Intelligence approach to Information Overload?". In Bissett, Andy; Ward Bynum, Terrell; Light, Ann; Lauener, Angela; Rogerson, Simon (eds.). ETHICOMP 2011 Conference Proceedings: The Social Impact of Social Computing. Sheffield Hallam University. pp. 300–311.
- ↑ Lévy, Pierre (1999). "What is Collective Intelligence?". In Lévy, Pierre (ed.). Collective intelligence: mankind's emerging world in cyberspace. Perseus Books. pp. 13–19.
- ↑ McRaney, David (10/02/2011). "Deindividuation". You Are Not So Smart. You Are Not So Smart. Retrieved 01/03/2017.
{{cite web}}: Check date values in:|access-date=and|date=(help) - ↑ Dachis, Adam (02/11/2011). "How a Hive Mind Mentality Can Make You Capable of Anything Good, Evil, and Bizarre". Lifehacker. Lifehacker. Retrieved 01/03/2017.
{{cite web}}: Check date values in:|access-date=and|date=(help) - ↑ a b Allen, Anne R. (05/07/2015). "Public Shaming, Cyberbullies, and the Hive Mind: Fighting 'Censorship by Troll'". Anne R. Allen's Blog. Anne R. Allen. Retrieved 04/03/2017.
{{cite web}}: Check date values in:|access-date=and|date=(help) - ↑ Realuyo, Bino A. "Dear Hive Mind of Social Media Empathy Fads". Huffington Post. Huffington Post. Retrieved 28/02/2017.
{{cite web}}: Check date values in:|access-date=(help) - ↑ Niederer, S; van Dijck, J (2010). "Wisdom of the crowd or technicity of content? Wikipedia as a sociotechnical system" (PDF). New Media & Society. 12 (8): 1368–1387. doi:10.1177/1461444810365297. Retrieved 07/03/2017.
{{cite journal}}: Check date values in:|access-date=(help) - ↑ Grenier, Dr. Guillermo J. (2002). "Paradigm Shifts".
- ↑ Lanier, Jason (2010). You Are Not A Gadget: A Manifesto. London: Penguin Books. p. 5.
- ↑ Thoman, Elizabeth. "Media Literacy Education: Lessons from the Center for Media Literacy" (PDF).
{{cite web}}: line feed character in|title=at position 54 (help) - ↑ Leadbeater, Charles (2008). We Think: Mass Innovation Not Mass Production. London: Profile Books.
- ↑ Braverman, Harry (1998). Labour and monopoly capital: the degradation of work in the twentieth century. 25th anniversary. New York: NY Monthly Review Press. p. xix.
- ↑ "TEDxManitoba - TJ Dawe: An Experiment in Collective Intelligence". YouTube. TED. 1 Mar 2012. Retrieved 8/3/16.
{{cite web}}: Check date values in:|access-date=(help) - ↑ McLellan, David (1995). The Thought of Karl Marx. London: Papermac. p. 117. ISBN 0333281225.
- ↑ Lanier, Jaron (2011). You Are Not A Gadget. London: Penguin Books. p. 5.
- ↑ Marx, Karl (1978). The Marx-Engels Reader, second edition, ed. Robert C. Tucker. New York: Norton. p. 280.
- ↑ Kellner, Douglas (2006). New Technologies and Alienation: Some Critical Reflections. The evolution of alienation: Trauma, promise, and the millennium (PDF). Rowman & Littlefield Publishers. p. 10.
- ↑ McLuhan, Marshall (1962). The Guetenburg Galaxy. Routledge & K Paul.
- ↑ Jenkins, Henry (2009). Confronting the Challenges of Participatory Culture. MIT Press. p. 75.
Digital Labour on Social Media Platforms
[edit | edit source]Introduction
[edit | edit source]n their article What is Digital Labour, Christian Fuchs and Sebastian Sevignani assert that the concept of digital labour relates to how the “dominant capital accumulation model of contemporary corporate Internet platforms is based on the exploitation of users’ unpaid labour”. Social media users engage in the creation of original content on platforms such as Facebook, Twitter, Instagram, YouTube, and this content, in turn, is appropriated by social media websites for profit.
As Fuchs sees it, the emergence of social media and its increasing popularity has resulted in a digitalised form of exploitation that is similar to theorist Karl Marx’s view of the everyday worker being exploited and oppressed under capitalist society. An extension of capitalism in the digital realm, concepts of digital labour examine the ways in which a user’s contribution and participation online, referred to as “digital work”, is appropriated by capital to make money. The individual’s time spent online, Fuchs argues, results in digital labour that is, for the most part, usually unpaid.
Perspectives on digital labour begin with explanations of digital work and the reasons for user participation on these exploitative social media platforms. Sevignani uses Facebook as an example, highlighting its use for maintaining personal relationships which fosters a sense of belonging among its users. Cooperating together, a collaboration emerges as social networking users engage in the creation and exchange of content, producing a specific type of sociality that is meaningful. Described as “cognitive digital work”, Fuchs notes that much like humans use their brains, mouths, and hands to translate their experiences, the individual uses the Internet and websites like Facebook and Twitter as instruments to organise and present their life experiences in the online sphere (e.g. a user profile, a blog post). Digital work, therefore, is the organisation of human experiences that creates a product of information. Interaction between users becomes routinized on social media websites which results in a consistent and reliable flow of data. According to digital labour theorists, this is central to the exploitation process. While this chapter will examine digital labour through the lens of social media use, theorists argue that any type of participation online can result in a form of labour exploitation. [1]
Facebook, Twitter, Instagram, Snapchat, YouTube, Pinterest – all of these platforms offer Internet users different ways of engaging in the digital world; maintaining social relationships, watching user generated videos, microblogging, etc. What they all have in common, however, is that they are owned by corporate Internet companies that use a targeted advertising business model that appropriates a user’s data (e.g. activity on social networking accounts, user patterns) and turs it into a commodity. [2]
History: Capitalism and Karl Marx
[edit | edit source]
Explanations of digital labour have long been tied to the workings of theorist Karl Marx. Identifying struggles within the class system, Marx highlights the imbalance of wealth and power between the ruling class and working class, arguing that wage labour is a form of exploitation. Ideas of “labour” have evolved in the wake of the digital age compared to the more conventional definitions of labour in Marxist theory. Still, Marx’s view of economic class conflict can be applied to the concept of digital labour to better understand the exploitation of social media users; a process in which people’s interactions with digital communication devices and social networking websites are appropriated for profit by the capitalist framework that Marx argued is embedded in society.
Capitalism is a social-economic system based on the private ownership of the means of production (e.g. factories, land, technology) and distribution of goods. Karl Marx argued that class divide in society is based on the individual’s relationship to the means of production. A structural perspective, Marxist theory asserts that the capitalist society is divided into two key classes; the property-owning bourgeoisie (the ruling class) and the wage-working proletariat (the working class), the latter considered the bottom tier of society. Under the capitalist mode of production, the relationship between the bourgeoisie and the proletariat is exploitative in nature as the worker’s pay is considerably disproportionate to the value of the goods that they produce (known as surplus value), with the ruling class deriving the profits from the production process at the expense of the proletariat. Owning solely their capacity to work, the working class become alienated due to their inability to control the conditions of their labour or the products that they produce.
Marx predicted that the proletariat would inevitably grow conscious of their oppression and overthrow the capitalist system, which has yet to occur in modern day society. Marx argued that this is due to the proletariat being unaware of their exploitation, commonly referred to as false consciousness. The working class have been socialised into believing that the unequal distribution of power is a fair and natural component of society due to the ruling class controlling the institutions responsible for socialising individuals (e.g. media, education). Ideologies of the ruling class are ingrained in the proletariat through this socialisation process. [3]
Work and Labour in Society
[edit | edit source]Establishing concepts of work and labour is essential to understanding theories of digital labour and its relationship to capitalism. In his book Digital Labour and Karl Marx, author Christian Fuchs adopts Marx’s characterisation of work and labour to break down these key distinctions.
According to Marx, work is a “conscious productive activity that transforms and organizes nature so that humans produce their means of subsistence in order to satisfy human needs, which constitutes the production of material life itself”. Work is defined as a creative, artistic, meaningful activity that is a necessary component of all societies, a process by which individuals make use of their surrounding resources and technology to elevate nature, culture and society. Under the social-political sphere, Marx argued that economies of all societies involve the process of production, distribution and consumption and therefore the concept of work becomes embedded into this system, resulting in an uneven distribution of power, class conflict and exploitation.
In isolation of capitalism, Marx defined labour as being a natural condition of human existence, an interchange between individual and nature. Under the capitalist system, however, it becomes a specific form of labour that is inherently exploitative. The worker submits to the capitalist authority by selling their labour in exchange for a salary that is unequal to the value of the goods that they produce. A product of human labour is referred to by Marx as a commodity, which has both a use value and exchange value. [4]
Digital Labour
[edit | edit source]The digital labour theory argues that the capitalist economy has resulted in the corporate exploitation of social media users for profit. In his book The Internet as Playground and Factory, author Trebor Scholz applies Karl Marx’s theory of labour exploitation to the online sphere, asserting that the activities of social media users and the content that they produce is a digitalised form of commodity because it is appropriated by the platform to generate profit. Popular use of modern technology (e.g. laptops, iPhones, tablets) and social media websites has led to a shift in labour markets. Currently, users on the Internet create most of the content online; they search, link, tweet, share photos. Accumulating an exposed data trail, this information is tracked, analysed, used to predict users’ habits and interests, and ultimately seized for financial profit by Internet corporations. “The divide between leisure time and work has vanished so that every aspect of our life drives the digital economy”, argues Scholz. Alexander Galloway shares similar concerns, adding that it is now impossible to precisely differentiate between non-productive leisure “play” activity and digital labour within the sphere of online exploitation. Whether it’s an image posted to Instagram or a series of reflective Tweets, the entire fabric of our participation on social media websites has become the core material used for capital profit.[5]
"We get all the culture; they get all the revenue."
Discussing the capital accumulation model of social media websites that focus on targeted advertisement, Sevignani suggests that the defining aim is to generate more users and encourage users to spend as much time on the platform as possible. The content of the ads is specifically focused on promoting related commodities. Fuchs argues that the advertisements are ideological in nature because they make bold claims about the commodity in relation to the user; it’s something that they must engage with if they wish to have a meaningful experience online. [6]
Mies draws an analogy between digital labour and housework, arguing that they are both a “source of unchecked, unlimited exploitation.” Houseworkers are often coerced by feelings of love, commitment or family responsibility. A platform like Facebook, which boasts over a billion users, monopolises the supply of a social networking service to its users which allows them too, almost invisibly, exercise a form of coercion through which users are chained to commercial platforms. Social media users place tremendous importance on websites like Facebook to maintain social relationships and they therefore cannot disengage from the service or, consequently, the exploitation process. [7]
Similar to Marx’s claim of the proletariat’s false consciousness, active users on Facebook and similar platforms are unaware of their exploitation because they do not see their time spent online as a form of labour. Discussing this disconnect, Trebor Scholz says, “It does not feel, look, or smell like labour at all. Joining Facebook and social media is optional”. Scholz argues that because participation on these platforms is optional and not obligatory, it portrays users as free agents who can opt out at any time. This aura of autonomy, according to Scholz, is the central reason why online exploitation is so effective. Scholz uses Marx’s concepts of work and labour to highlight the exploitation process, arguing that the content produced by a user is a form of creative work, a meaningful activity, which is subsequently exploited by the platform on which it is produced and shared. [8]
Corporate Social Media and Free Labour
[edit | edit source]In her chapter “Free Labour,” Tiziana Terranova defines free labour as work that is not a result of employment, rather it is work that is unpaid and given for free. “It is unwaged, enjoyed and exploited.” Free labour comes in many different forms, including social media interaction, building websites, participating in mailing lists, or modifying software packages. It is becoming more apparent than ever, however, that corporate social media websites know the number one source of value is user participation. Tracing back to 1996, Terranova notes that at the peak of free labour in AOL chat room moderation, over 30,000 “community leaders” were helping AOL generate an estimated 7 million a month. [9]
According to Christian Fuchs, a user’s activity creates profile data, social relations, user-generated content and transaction data (also known as browsing behaviour) which is the defining commodity offered for sale to advertising companies by social media corporations. In doing so, this creates a pathway for advertisers to select specific user groups that they wish to target.

Fuchs notes in his discussion of digital labour that there are three key elements of online exploitation.
- Coercion: Users are ideologically coerced to use social media platforms to create and share content, exchange information and engage in communication. Using social networking websites (e.g. Facebook, Twitter) has become integral to how we maintain social relationships, an important part of our lives. Without such communication, Fuchs argues our lives would be less meaningful.
- Alienation: Companies, not users, own the platforms and generated profit.
- Appropriation: Social media users spend considerable amounts of time on these corporate platforms that are funded by advertising capital accumulation models. A user’s time is the value created by their unpaid digital labour. From a Marxist perspective, social media users are unconsciously engaging in their own exploitation which ultimately benefits the ruling class.
The process of exploitation, Fuchs argues, is established when a user creates the data commodity. Having no control or agency over this data, a user’s time spent online is therefore objectified. Through terms of service and privacy policies, corporate social media platforms acquire ownership of this user data which is then offered as data commodity to advertisers. The act of turning data into profit, known as the value realization process, occurs when targeted users click on or view an advertisement. Fuchs notes that not all data commodities are sold and some are more popular than others. Still, the act of exploitation always occurs at the point of the production and appropriation of the commodity, as well as the commodity’s sale. [10]
Fan Labour
[edit | edit source]Investigating the work of fan writers and artists who post their content on Twitter, Facebook, and other social media websites, author Abigail De Kosnik notes that these online activities are contributing massively to corporate revenues. The abundance of fan contributions to the Internet can be regarded as a type of unpaid labour, Kosnik says. Fan labour generates a tremendous amount of buzz and hype for the product. Enthusiastic fans dedicate large portions of their time to discussing or posting about their favourite types of media, often creating Twitter or Facebook pages dedicated to providing a continuous stream of updates on their favourite artist, movie, or television show. It’s essentially free promotion for the product, a new form of publicity and advertising.
Advertising revenue has proven to be a stable source of income for YouTubers and bloggers, and Kosnik notes that while most contributions by fans are largely unpaid, they could potentially receive compensation from Google AdSense or the YouTube Partner Program if companies would allow them to use copyrighted images, text, sound, and video. Fans are routinely sued or served with cease-and-desist letters for infringing copyright violations, while their unpaid promotion of the product on platforms like Twitter is exploited for profit.
According to Scholz, any possibility for fans to earn compensation for their labour would largely depend on both fans and corporations acknowledging that fandom activity is a form of labour. “It contributes value to the commodity itself and is therefore worthy of compensation." [11]
Alienation in Digital Labour
[edit | edit source]Digital labour results in various forms of user alienation on social networking websites. Grounded in theorist Karl Marx’s “Alienation theory”, Marx argues that there are four distinct forms of alienation under capitalism. Included in Economic and Philosophic Manuscripts [12], these are (1) Alienation from oneself. (2) Alienation from the objects of labour. (3) Alienation from the products of labour. (4) Alienation from others and society.
Applying Marx’s ideas of alienation to digital labour on social media platforms, Mark Andrejevic makes the following claim:
Each form of intentional user-generated content – a blog post, a Facebook update, a Tweet, is redoubled in the form of ‘cybernetic commodities’. While they are created by users, they are not controlled by users, who have little choice over how and when this data is generated, and little say in how it is used. In this sense, we might describe the generation and use of this data as the alienated or estranged dimension of their activity. To the extent that this information can be used to predict and influence user behaviour it is an activity that returns to users in an unrecognizable form as means of fulfilling the imperatives of others.
—Mark Andrejevic, Surveillance and Alienation in the Online Economy, 2011
Andrejevic expands on the coercion process of social networking websites, citing it as a main source of alienation threat. Individuals are social beings that crave communication and meaningful connection with others. In an information society, this means that digital media has become the essential tool for interacting with other people and sustaining meaningful relationships. If people do not interact with social media websites to engage with their peers, their lives, according to Andrejevic, will become less meaningful. This is particularly true for young people who are the most active users on platforms like Facebook. Andrejevic suggests that the coercion process involves the user being threatened by the idea of isolation and the social disadvantages that will follow if they disengage from social media use. The threat of alienation encourages the user to participate and, as a result, locks them in the exploitation process. [13]
Fuchs notes that the average time a user spends on social media relates to its level of profit value. The more time a particular group of users spend on the platform, the more valuable the data commodity is. 15-25 year olds spend a considerable number of minutes per day on Facebook and Twitter compared to 75-85 year olds. 15-25 year olds therefore constitute a more valuable commodity because they provide a higher average of labour per day which generates more data to be sold. Andrejevic considers this a form of alienation and estrangement as the user is completely disconnected from their free labour. [14]
Authorship and Ownership
[edit | edit source]Users are alienated from the instruments of their labour because they do not have power over their own content or the handling of their data, nor do they control the social media platform itself. Analysing the corporate and user divide, Fuchs notes that 61.1% of Facebook’s class B stock is directly controlled by 12 executive officers and directors, with partner companies acting as shareholders. There is an exploitive relationship between stockholders and users at the heart of Facebook; the users, classed as economically poor, do not control ownership of the platform, yet they create the wealth that is controlled and owned by stockholders. Users do not hold the power to influence the rules or conditions of Facebook, including the content, terms of service, the privacy policy, or the advertisements – which are emboldened by the commodification of user data. [15]
Examining the practices of data mining for intellectual property on social media platforms, Jessica Reyman states that although these websites give off the impression that they are spaces in which online users are encouraged to create, share, and connect with other users, the underlying practices at work transform a user's activity into data that is to be used for privatized and commercial gain, arguing that each social, creative, or intellectual activity a user engages in online is ultimately compromised in the data commodification process. Reyman goes on to suggest that data is not merely a by-product of technology that is to be bought and sold but it also forms a dynamic narrative about the paths we have chosen to take as users navigating the digital world. Everything relating to a user’s activity, from the technologies they have used, how they have composed themselves in particular online spaces, to whom they have participated with, is made vulnerable and exposed.
Debates surrounding the use of user data are largely focused on the ownership status of information on social media platforms. Corporate Internet websites know that user information is a valuable business asset because not only does it generate profit but it promotes a continuous flow of information that is specifically designed to encourage more user activity. User data, Reyman argues, is not created by an author-user, but rather is a by-product of technological algorithms. This means that the conditions of user contributions are not controlled by the original authors of those contributions, social media users, but by the platforms that appropriate the content for commercial gain. [16]
Inverse Fetishism
[edit | edit source]Fuchs' concept of “inverse fetishism” involves the social media user denying claims that they are being exploited by highlighting the social advantages they receive from using the service. The inverse fetish of a platform like Facebook, Fuchs suggests, includes statements like: “Facebook does not exploit me because I benefit from it by connecting to other users." The reality of the user being merely an object that serves the profit interests of Facebook is concealed behind the perceived advantages of user interaction.
Kruger notes the psychological reason for this, stating that the threatening realisation of the user being coerced, exploited and alienated must be fended off on a mental plane. In contrast to Fuchs example of denial (i.e. “I am not exploited because there are benefits to using social media”), Kruger’s research found different responses to the exploitation process, such as: “Facebook exploits me, but that’s not so bad as long as I can benefit from it by connecting to other users.” This reasoning is categorized under John Steiner’s “turning a blind eye” concept, a term he used to describe the various ways the individual will defend themselves against the knowledge or realisation that they are being exploited.
Steiner notes that it's a specific kind of response that is disengaged and does not consider the extent to which one is being exploited. "It conveys the right degree of ambiguity as to how conscious or unconscious the knowledge [of exploitation] is." Sevignani writes, "Users are kind of aware that people who own and control social networking platforms are appropriating societally produced surplus." Sevigani's use of "kind of" highlights the ambiguity Steiner is referring to when discussing the user's view of the exploitation process. From a Marxist perspective, it's a position that is similar in nature to the ambiguous perspective of the working class (i.e. "It's just the way things are"). [17]
Information Society
[edit | edit source]Information Society is a term that has long been debated over it's exact definition. It is generally believed to describe a society in which the creation, distribution and manipulation of information has become the most important economic and cultural activity. It is seen that digital information and new communications technologies have led to a information explosion and in turn, has caused all forms of social organisation to change. People who take part in an information society are referred to as digital citizens. The concept of an information society argues that we are now in a totally new stage in our society. [18]
Today, in an information society, there is an argument that there is no longer a distinction between our private life and our work life. Mobile phones, laptops and networked computers have meant that we are far more mobile and no longer need to be at an office desk or workspace. We can now get an e-mail about something like a report at any time of the day, there is a pressure for workers to be 'always on' and ready to receive information. To be successful in the current work climate, you need to be willing to be a 'node' in a networked economy. [19]
Computers are everywhere we look now, they take us into an information ecology that consists of networks, systems, processes, technologies and people. We live in a society where interaction and use of computers is prominent and that is something that is not likely to change anytime soon. Ten year olds, teenagers and adults all inhabit information society and inhabits everything we do.[20] Our jobs and our education have drastically changed since computerisation, millions of jobs now exist in technology that years ago never would have. The way we receive information in the current age changes how we are at work or school. [21]
In 'Theories of the Information Society' by Frank Webster, John B. Goddard identifies four elements which indicate the transition to an 'information society':[22]
- 1. Information has become a key strategic resource on which the very organisation of the world economy is dependent. Our modern world demands the co-ordination of globally distributed manufacture, planning between sovereign states and marketing throughout continents. Information is essential in our contemporary world.
- 2. Computer and communications technologies provide the infrastructure that enables information to be processed and distributed, new technology means information can be handled on a historically unprecedented scale and monitor economic, social and political affairs on a global scale.
- 3. The rapid growth of the 'tradable information sector' of the economy. This means the explosive growth of services such as new media (satellite broadcasting, cable, video) and online databases (cloud based systems) providing information on a host of subjects ranging from stock-market dealings, commodity prices, patent listings and currency fluctuations, to scientific and technological journal articles. These developments have seen radical re-organisation of the world's financial system.
- 4. The growing 'informatisation' of the economy is facilitating the integrating of national and regional economies. Immediate and effective information processing and exchange, economies have become truly global. Companies can now develop global strategies for production, storage and distribution of goods and services. Boundaries made by geographical locations are now being pushed back further and further.
Frank Webster has spent much of his work looking at the five different definitions of 'information society'; technological, economic, occupational, spatial and cultural.
Technological
[edit | edit source]The key idea of this concept is that breakthroughs in information processing, storage and transmission have led to the application of information have led to the application of information and communication technology (ICT) in virtually all corners of society. Cheap information processing and storage technologies, such as computers, leads to the development of better telecommunications that in turn can dramatically improve management and distribution of information.
Economic
[edit | edit source]Sometimes referred to as information economy, it highlights the fact that the economy in our society is based on the effective acquisition, dissemination, and use of information, rather than on the means of production. Austrian economist Fritz Machlup devoted a lot of his life looking at the size/growth of information industries such as education, the media, information machines and information services. He claimed that is is possible to add economic value to each of these and that they contribute to the gross national product (GNP) of a country. Many people argue that currently our economy is reliant on the information we are now able to access, and since information is in theory infinite, we are currently living in a society where the economy is based around an infinite resource. [23]
Occupational
[edit | edit source]One way of looking at the emergence of an 'information society' is by focusing on occupational change. We have only achieved an 'information society' when most of jobs in our society are in information work. Webster argues that this concept means we are only in an information society when "clerks, teachers, lawyers and entertainers outnumber coalminers, steelworkers, dockers and builders." [24]
Spatial
[edit | edit source]Here there is a major emphasis is put on information networks which connect locations and in consequence have dramatic effects on the organisation of time and space. This emphasises the importance of information networks linking together locations within and between towns, religions, nations, continents and the entire world.
Cultural
[edit | edit source]This is the most acknowledged conception of an 'information society'. Each of us is aware, from the pattern of our everyday lives, that there has been a massive amount of increase in information in our social circulation. There is more information in our everyday lives than ever before. Television programming is on 24 hours a day and now we can access all the films/TV shows we want at the click of a button due to streaming services such as Netflix or Now TV. Even our phones, something we fit in our pocket, holds a vast amount of information. According to Webster, "we inhabit a media-laden society." [25]
Flaws in an Information Society
[edit | edit source]Although highlighting these different forms of information society, Webster himself is skeptical over "whether it is a technological, economic, occupational, spatial or cultural conception, we are left with highly problematic notions of what constitutes, and how to distinguish, an 'information society'." [26]Webster states there is a variety of criteria which purport to measure the emergence of an information society but there are many scholars who, using different indicators, argue that we are yet to actually enter an information society. [27]
Philosopher Gordon Graham has made the point that when the term 'information' is applied to an online context it only refers to the ability to access digital data from a device. This causes a problem because it makes no reference to the quality or usefulness of information. [28] Graham claims that digital information can lead to misinformation and that information posted on the web can be wholly misleading and incorrect rather than knowledgable. [29] If this is the case and the information that people are getting is misleading, then it will lead to people in society being misled and taking in information that is potentially wrong.
The Network Effect
[edit | edit source]A network effect is the effect that one user of a good/service has on the value of that particular product to other people. When looking at a network effect it come down to how many people are using the product, the more people use it, the more value it holds in society. The network effect plays a key role in the popularity in the like of social media sites such as Facebook and Twitter. The more people join as users of the site, then the more likely other people are willing to join. If there are a lot of their friends on social media sites, then it is a way for people to stay connected with who they know and find out information regarding what people or up to or just chat to the in general.
Robert Hassan argues that we live in a society where digital information is "at its root, ideological."[30] He believes that digital information spreads the ideas of our culture and society. Hassan goes on to relate the fact that the idea of an information society itself has become a concept which falls to the network effect. If countries start to rely on an 'information society' then other countries will soon follow. [31] So many countries now rely on the value of information that "connectivity and access to networks is simply a part of what life is."[32]
The network effect means that old media, the traditional form of communication and expression, now speeds up. Communication in general speeds up, economies speed up and life speeds up.[33]
Network Society
[edit | edit source]The concept of a network society is an expression that looks at how the spread of networked, digital information and communication technologies has impacted the economy, politics and culture of our society. The network society accelerated at a rapid state, new technologies mean that our ability to communicate with each other is getting faster and easier.
The network society now is a form of social structure which relies on the information and communications technologies building a network that generates and distributes the information via points in the network. Nowadays, in our society, we are linked by networks in some way and this is a basic function of a network society.
Networks are seen a a key concept in looking a new media from the angle of social theory. Sociologist Manuel Castells defines the network society "as being the outcome of a historical trend where dominant functions and processes in the information age are increasingly organised around networks."[34]
Information Overload
[edit | edit source]In today's day and age are surrounded by information, we can find answers to just about any question we have by simply typing it into Google or even just asking your phone. The internet has given us unprecedented access to a vast amount of information that is available to millions of users. [35] There is now over 1 billion websites currently active on the web. [36] The availability of all this information and the speed at which we can get it, creates a problem of information overload.
Robert Hassan claims that "the problem we face is that we have nothing to measure this network to measure this network society against and so we are everyday stepping into an unknown and unpredictable future" [37] We now live in a society where information is all around us, when you consider how much information we can access "there is already too much information for us ever to ever be able to consume." [38]
Social Networks in the Network Society
[edit | edit source]The rise of social networking sites such as Facebook and Twitter contain a massive amount of information that is created through users communicating, sharing and liking posts. Instant messaging on these sites allow for free and rapid communication between users, demonstrating that in the modern age we can share all we need with people, without ever meeting face-to-face. The development of a network society in modern day allows for a great deal of information to be traded on these social networking sites. Through the use of these sort of sites, network society is always altering the "cultural production in a hyper-connected world."[39] We are constantly producing and creating information when on social media by posting. We go on these sites to seek some form of information, whether it be get the news, see what friends have been up to or make arrangements with friends.
It is argued that social media is now seen as how most people socialise, Terry Flew claims it is "since it has only been with the technological advances associated with new media that the capacity of networks to operate at a scale, speed and level of complexity" [40] has allowed the social media to become the "dominant mode of social organisation."[41]
Globalisation
[edit | edit source]Globalisation is the process of international integration arising from the interchange of world views, products, ideas, and other aspects of culture.
We, as a society, are constantly getting new information. We seek information everyday and use information to connect with one another, a network society helps us to connect with others the other side of the world and is credited as being a major factor in helping with the concept of globalisation. Robert Hassan believes that "the networking of society, the interconnecting of people, processes, applications and leisure pursuits has led to a globalised society." [42] With this idea of globalisation, it means that if we are a network on a global scale then we can share and access information to people all over the world, as long as they have access to the internet. Every piece of information we know can be posted on the web if we wanted it to be, people can expand their knowledge quickly and engage with anyone. There is an argument that proposes globalisation has marked a fundamental shift in social relations and they way people interact with one another. [43]Yet others argue that there is no evidence to support this claim and that many developments associated with globalisation and its affect on social relations are no historically new. [44]
Castells Five Central Elements
[edit | edit source]Manuel Castells proposes that the rapid expansion of a network society is due to five central elements.
- Information is the raw material that is necessary for any economic activity, its acts as both the input and output of new technologies.
- ICTs have world wide effects through all forms of social activity.
- Networking applies to all social processes and organisational forms, knowledge resides in a number of sources and therefore needs to be collectively kept in order to be effectively applied.
- Processes, organisational structures and institutional forms need to be flexible, in order that such activities and entities can be readily altered and transformed due to possible changes.
- The growth of specific technologies into highly integrated systems means that all industries can take on the characteristics of 'pioneer' ICT-based network enterprises such as Apple and Cisco. This includes look at the size and growth of partnerships and relations, interactivity with suppliers and consumers, management of flexibility , growing customisation of products and services, and accumulation of brand-based market value. [45]
Castells believes we have gone through an information technological revolution and that the 'network society' and information we all now can get in part of an all "encompassing worldwide phenomenon."[46]
Critical Theory
[edit | edit source]Critical Theory refers to the critique of society and culture through the application of knowledge of the social sciences and humanities.
Critical theory is a social theory with a basis in neo-Marxist philosophy. The theory provides a specific interpretation of Marxist philosophy and reinterprets some of its central economic and political notions such as commodification, reification, fetishization and critique of mass culture.[47] The therory aims to observe and understand underlying ideologies within society and culture in order to highlight inequality. Unlike other theories however, critical theory does not only seek to understand society and culture but to change it by human emancipation though consciousness and reflection. Max Horkheimer, who played a central role in the development of critical theory said: "The goal of critical theory is the transformation of society as a whole" and that the ultimate goal was to achieve a society free from injustice[48].Critical theory is opposed to all forms of human exploitation, domination and oppression.
History
[edit | edit source]Critical theory was developed by the Frankfurt School in Germany in the 1930s by a group of theoreticians brought together under Max Horkheimer at the Institute for Social Research.
The Institute of Social Research
[edit | edit source]The Institute for Social Research is a research organisation for sociology and philosophy in Frankfurt, Germany. It was founded in 1923 by Felix J. Weil, a young student of Marxist philosopher Karl Korsch. Weil funded the institution with an endowment from his father Hermann Weil which allowed him to create and maintain the institution until it achieved financial independence. Financial and intellectual independence was the ultimate goal of the institution. Weil firmly believed that independence was a necessary prerequisite for theoretical innovation and unrestrained social research. The Ministry of Education had initially suggested the institution be named the 'Felix Weil Institute of Social Research but Weil declined as he wanted the institute to be know for its "contributions to Marxism as a scientific discipline, not due to the founders money".[49]
The Frankfurt School
[edit | edit source]
In 1930, Max Horkheimer took over as director of the Institution for Social Research and it was under his supervision that a group of thinkers emerged with a similar sociological and philosophical interest. This group of theorists and their ideologies became known as the Frankfurt School. The term refers to a number of theorists associated with the work of the institute. Although only loosely affiliated, Frankfurt School theoreticians share similar Marxist premises and approach similar issues relatIting to society and culture.[50] The Frankfurt School was influenced by the works of Karl Marx, Sigmund Freud and Györy Lukács. They were focused on social change and research and sought to address the perceived omissions of classic Marxism.
The Origin of Critical Theory
[edit | edit source]Critical theory was established by five Frankfurt School theoreticians: Max Horkheimer, Walter Benjamin, Herbert Marcuse, Theodor Adorno, and Erich Fromm. The theory emerged as a result of their efforts to overcome limits imposed by previous philosophy. They returned to the ideas of Immanuel Kant, who believed that the primary task of philosophy was criticism rather than justification of knowledge, he argued that all philosophy should be subject to critical review. Under this influence their work took on a more critical element which resulted in a series of open-ended, probing and critical works rather than systematic philosophical statements.
The Foundations of Critical Theory
[edit | edit source]Ben Agger (2006) argued that Critical theory was based on seven foundations;
- It is a critique of positivism and of the assumption that theory is value free.
- It argues for the possibility of a better future without domination and exploitation.
- It sees domination as a structural phenomenon.
- It shows how humans, who live in structures of domination, tend to reproduce these structures in false consciousness.
- It is interested in everyday life such as the workplace and the family.
- It perceives structure and agency as dialectical.
- It sees liberation as a process that must be accomplished by the oppressed and exploited themselves.[51]
Fuchs simplified this further by considering these foundations in relation to aspects of Marxism, to define the key fields of study in Critical theory;
- Critical ethics
- Critique of domination and exploitation
- Dialectical reason
- Struggles and political practice
- Ideology critique
- Critique of the political economy
Critical Theory and Social Media
[edit | edit source]Critical theory is a useful tool in the critique of social media as it considers the role of social media within the commons. Social media has now entered our daily lives and plays a pivotal role in our economy and communications structure meaning that it has an impact on society and mass culture which is open to critical review. In Christian Fuchs' "Social Media:A Critical Introductions" he suggested that: "Understanding social media critically means, among other things, to engage with the different forms of sociality on the internet in the context of society.".[52] Fuchs stressed that just asking questions was not necessarily a 'critical' approach, that typical questions had a tendency to miss the underlying issues at hand and only sought positive answers from those in power without consideration for the affect of this on those not in power.
"They do not ask the question, who benefits and who has disadvantages from the use of social media ... and how the benefits of some are based on the disadvantages of others...they are concerned with how certain groups, especially companies and politicians, can benefit from social media and ignore the question of how this use benefits or harms others and society at large."
Fuchs argued that Critical theory was vital in the analysis of communication and technologies. He pointed out that, although many of us benefit from telephones, televisions, radio and the internet, etc. , the history of these technologies is deeply rooted in capitalism, colonialism, warfare, exploitation and inequality. He pointed out that Marxist thought was relevant to the analysis of these technologies and in particular the internet and social media.
"Marx described a global information network, in which "everyone attempts to inform himself" about others and "connections are introduced" (Marx 1857/1858, 161). Such a description not only sounds like an anticipation of the concept of the Internet, it is also an indication that Marx's thought is relevant for Media/Communications Studies and the study of the Internet and social media."
Critical theory looks at the power struggles within the commons. The internet and social media are power structures in their own right but also facilitate power struggle. The media is a tool for exerting power, domination and counter-power meaning it can equally be seen as a source of liberation. Media can support the expansion and commodification of the commons. Given social media's role as a potential source of domination or inequality, critical theory is an appropriate model for it's analysis and critique.[53]
Social Media
[edit | edit source]Social media can be described as “the collective of online communication channels dedicated to community-based input, interaction, content-sharing and collaboration” [54]. Social media can be the term used to describe all platforms available on the World Wide Web, and the most dominant examples of social media are Facebook, Twitter, Instagram, Snapchat and Wikipedia.
History of Social Media
[edit | edit source]We may think that social media is a new concept but it is really a further development in our social interaction with each other. When we look at the history of social media, we should look at the overall development in human communication throughout the years. Technology has continued to advance and social media is just the most recent trend and form of communication that we have developed.[55]
The telegraph, an early form of long distance communication, was invented in 1844 by Samuel Morse. It was the first form of using electricity to communicate through long-distance. With the development of the telegraph also came the development of Morse code (developed by Samuel Morse) which was an equivalent of the alphabet and numbers with different taps and clicks on the telegraph. The first message, “What hath God wrought?” was sent from Washington to Baltimore on May 24, 1844. [56]
Not long after the telegraph was being used, the telephone was invented. In 1876 Alexander Graham Bell was the first to obtain a patent from the U.S. for the telephone, the first device that allowed people to talk directly with one another over long distances. The invention of the telephone would forever change the way that humans communicate with each other. [57]
With these two early inventions as well as important others like the postal service and the radio, it is clear that human desire for sharing of information and connecting with one another was necessary. Through many adaptions and changes throughout time, the telephone and the radio are still being used today. These were some of the first inventions that allowed people to instantly reach and communicate with others across a long distance. These inventions in the 1800s were just the start to how humans would begin and learn to communicate with one another. They were the first things that led us to the forms of communication that we use today. [58]
Fast forward to the 1960s where the first form of the internet was getting started. CompuServe was one of the first forms of the internet and was originally used as a support network for an insurance company, and then was later used as an early form of email and file sharing. This allowed for true interaction with others online in the form of email and discussion forums. Shortly after that, AOL was invented and used by many. AOL allowed users to create “member profiles” which is much like the kind of social media sites we know today. [59]
Not long after this, in 1997 the first social media site was created. With the invention of computers, the internet, emailing, and user profiles, the rise of social media started. Through the following social media sites and other forms of messaging and interacting online, our technology and the way that we are able to communicate with people around the world has reached new levels.
Rise of Social Media
[edit | edit source]The first social media site was a website called Six Degrees and it lasted from 1997 to 2001. The name Six Degrees comes from the Six degrees of separation theory. This theory is the idea that all living things in the world are six or fewer steps away from each other in a way that their is a "friend to friend" chain that can be made to connect any two people in a maximum of six steps.[60] This website allowed users to create a personal profile and then friend other users whether you were a registered user or not. Before its end in 2001, the site reached 3.5 million registered users at its peak. It was also during this time that instant messaging and blogging started to rise.[61]
The use of instant messaging on AOL really changed the way that we are able to connect with others. While AOL messaging technically ended in 2010, the introduction of it in the late 90s allowed us to still use instant messaging through texting and on other social media sites like Facebook and Twitter. Blogging was also a new way for users to gain and connect with other users and readers and is a social form that is still being used online today. After Six Degrees and AOL's AIM started to establish itself, the late 90s and early 2000s saw an increase in social media websites.
Early 2000s Social Media
[edit | edit source]- Napster Unlike earlier social media sites, instead of file sharing and text-based communication, Napster allowed users to share music. It quickly became a very large electronic music distribution platform. It was even named the fasted growing business ever and remained so up until 2013 even though they went bankrupt in 2002. Although Napster was a very popular site at the time, it eventually filed for bankruptcy after copyright controversy.
- Friendster Friendster was invented in 2002 and was very similar to Facebook as it included Friendster college and a newsfeed. Unfortunately, due to continuous technical difficulties, Friendster never gained popularity and it soon lost to Myspace and Facebook. It was later used by a Malaysian company in 2009 and reinvented as a social gaming site in 2011. However, Friendster came to an official end in 2015.
- Myspace Myspace was founded in 2003 and was launched in January 2004. Myspace allowed users to create their own "space" including a friends list, status updates, photos, personal page decor, and music. It was thought and hoped to redefine music, politics, dating, and pop culture. In its first month, 1 million people had signed up for Myspace. It was valued at tens of billions of dollars as of 2007. However, due to mismanagement, strategic blunders, and an overall loss to the rising Facebook, Myspace struggled to remain relevant around 2011. The website itself is still active, but there is a massive loss in popularity and it is now used more for entertainment and music purposes.
- Second Life Second Life relaunched in 2003 after the original version, Linden World made some major upgrades. This was as social networking site that allowed users to create avatars and interact with other users or 'avatars' in this virtual world. The upgraded Second Life allowed avatars in this virtual world to have an in-game economy, a building interface, and messaging between users. It also allowed avatars to have relationships, sex, have their own religion, and gamble. By 2006 Second Life acquired over one million users and the attention of mainstream media. Second Life is still very much active today as there were 900,000 monthly users in 2015. Now, the creators are looking to transform second life into the new technology of virtual reality.[62]
Audience Engagement on Social Media
[edit | edit source]"Audience engagement is providing an outlet for audiences to interact with, be it through an empowered presenter or a physical stimulus. It is making sure you don’t presume the attention of your attendees for the duration of your event – they’re only human and their concentration will waver without a reason to focus."
As social media platforms continue to grow every day, networks and business must think about how to increase their engagement on their profiles to increase customers. As users are constantly one their accounts whether using the computer or through apps on their cellphones, they are constantly consuming content. This gives businesses the opportunity to market and advertise their business. Here are some ways that they can increase their audience engagement.
- Create a Strong Social Media Presence
Find ways to keep content compelling.
- Enable Audience Participation
Find ways to include your audience by creating more ways for comments. Use trending content and create polls for the audience.
- Deliver Choice
Make sure that your content is available on multiple devices.
- The 80/20 Rule
This rule says that 20% of your content should be promotional and 80% should be added value to your followers.[63]
Most Popular Types of Social Media in 2017
[edit | edit source]Instagram is a free app that allows users to post pictures, videos, and short "stories" that last 24 hours. Kevin Systrom is the CEO and co-founder along with Mike Krieger the CTO and co-founder. [64] Instagram was launched in 2010, now the global community shares over 95 million photos everyday. [65]
The founders created the app with the simple purpose to make sharing photos more "fun", by adding filters and making the quality and speed a top priority. [66] Instagram also allows users to "like", "share", and "comment" on other users posts. Thus making the app interactive between users. In 2012 Facebook bought Instagram for $1 billion in cash and stock when Instagram had only 12 emplloyees. [67] By the end of 2016 Instagram had 300 million daily active users. [68] Instagram offers access on the web and in the Apple App Store and Google Play Store. [69]
Instagram's income is mainly generated from ads. Although Facebook does not relsease the financials of Instagram, they reported earnings of over $6 billion and certainly a portion of that is from Instagram. [70]
Facebook was launched in 2004. Facebook's mission statement as presented on their own Facebook page is "to give people the power to share and make the world more open and connected". [71] Currently it is free to all users. The founder, Mark Zuckerberg, started Facebook at the age of 23 at Harvard University, where it was only for the use of students. [72] Now Facebook has 757 million daily users of all ages and backgrounds.[73] Facebook can be used to share videos, photos, status updates, direct messaging, online calling, video chatting, etc; whether they are personal or business related. According to Facebook's Wikipedia page the company employees over 17,000 people.
Facebook makes 97% of its profit from advertisements in 2016 Facebook grossed over $6 billion dollars. [74] This includes the income generated from Instagram and WhatsApp. [75] Through the use of cookies the advertisements that show up on each users pages are tailored to what they have been searching. This way advertising is more effective and directed at the audiences more likely to buy.
According to Twitters on Wikipedia page Twitter's revenue in 2016 was $2.52 billion although their net income was -$456 million.
Twitter was launched in 2006 by founders Jack Dorsey, Noah Glass, Biz Stone, and Evan Williams.[76] Twitters mission statement is "To give everyone the power to create and share ideas and information instantly, without barriers." [77] Twitter has 313 million monthly users, 82% of which are active by mobile, and employee over 3,500 people around the world.[78]
Twitter allows users to "tweet" 140 character posts or "tweets" for anyone to see unless the users account is set to private. There are over 500 million tweets sent each day, this number usually increases depending on the major current events for the day. [79] For example Twitter exploded with tweets on the 2016 U.S. election day amounting in over 40 million just pertaining to the election. [80] Twitter is the ideal form of social media to express ones opinions and spread others.
According to Twitters own Wikipedia page their revenue amounted in over $2 billion but their net income was -$456 million. Needless to say Twitter is losing popularity in a sense. Twitter has been known lately to be a social media platform used by users to cyberbully, leading to the decline of users. [81]
Snapchat was launched in 2011, originally called Picaboo, by the co-founder and now CEO Evan Spiegel and co-founder and now CTO Bobby Murphy. Snapchat Inc. believes "Our products empower people to express themselves, live in the moment, learn about the world, and have fun together."[82] In 2011 Snapchat's features only allowed users to send "disappearing" pictures.[83] Now Snapchat allows users to send up to 10 second "snaps", snapchats with filters, videos, direct disappearing messages, viewing of 24 hour "stories", also Snapchat has over 10 business "stories" allowing users to stay connected on news, current events, celebrity gossip, technology, etc. Snapchat is recognized for the idea of "stories", Instagram recently came out with a similar concept.
Snapchat earned over $1 billion in advertising revenue in 2016.[84] In 2015 Snapchat had over 150 million active daily users.[85]
Youtube was launched in 2005 by former Paypal employees, Chad Hurley, Steve Chen, and Jawed Karim.They initially made Youtube as a way to share videos in one place rather than searching the internet for a specific video. In 2006 Youtube was bought by Google. Youtube allows users to browse millions of videos, upload videos, comment or like videos, etc. Youtube has a huge diversity of videos. Also Youtube has derived the word "Youtube Famous", typically people who are Youtube Famous have received thousands of views and continue to make videos like their original. For example there are fashion "youtubbers", comedy, stunts, etc. Youtube employee over 2,500 people. [86]
According to Investopedia Youtube makes a majority of its income through advertisements. Depending on the amount of views the video receives is the amount of money determined. Also the amount of ads that the video has. "In 2013, the average cost per thousand (CPM) for YouTube was $7.60. CPM (cost per thousand) is an industry term that represents revenue per thousand views. In 2013, the average income for each YouTube content creator was $7.60 per every thousand views. A video with 500 views would have earned roughly $3.80. A video like Gangnam Style with a billion views would earn $7.8 million. Some videos earn a higher or lower than average rate depending on the video content. Videos containing copyrighted music do not earn revenue for the video creator, and some topics may not attract advertisers. Others have a strong draw from advertisers and drive up the CPM."[87]
Pinterest was launched in 2010 by Co-founders CEO Ben Silbermann, Evan Sharp, and Paul Sciarra. Pinterest employees over 500 people. [88] Pinterest allows users to share ideas (pins) such as recipes, fashion, travel, interior design, etc. Pinterest offers "buyable" pins on websites other than Pinterest, and to pin a website to Pinterest to share it to a personalized pin board of the user. Pinterest allows the users to pin and make pin boards of different categories. Pinterest's main theme is "discover, pin, and buy". In September of 2015 Pinterest reached an average of 100 million monthly active users. [89]
Pinterest doesn't actually make revenue. Although Pinterest is valued at $11 billion in 2016. Pinterest is free to users and has become a third party website, because users go directly to the website of the product to purchase the item pinned. Pinterest's goal is to make $2.8 billion by 2018. "It's not as if Pinterest is sitting still - it has released a slew of ad products in recent months and restructured its sales organization to focus on its biggest advertisers in a bid to achieve that goal." [90]
Pros and Cons of Social Media
[edit | edit source]Pros[91]
[edit | edit source]- Social media allows users to spread information quickly such as breaking news.
- Law enforcement can use social media platforms to catch criminals through video posting and more.
- According to the Journal of Applied Developmental Psychology college students can use social media websites to create a network of new friends, which in turn helps students do better in school.
- Social Networking allows users to create more friends.
- Social media helps empower and give a voice to minorities such as business women.
- Through the use of social media employers can narrow their search for the right employee and vice versa.
- Social media has been known to have a "contagion effect" with dieting and exercise which can in turn make users more healthy.
- Face-to-face interaction can be promoted through social networking.
- Voting is promoted on social media cites.
- Political change is promoted on social media cites.
- The economy is stimulated by social media by providing thousands of jobs, etc.
- Community involvement is promoted through social media and empowers users to do social good.
- Senior citizens feel more connected to society through social media according to a Pew Internet & American Life Project study.
- People who are social introverted or isolated can reach out to people more easily through social media platforms.
- The government can quickly relay information to the public about health and safety information through social media.
- Social stigmas can be disarmed through the use of social media.
- Users can easily "crowdsource" and "crowd fund" for various needs through social media.
- Educational resources are more accessible with the use of social media.
- Small businesses and corporations can use social media as a form of free advertising.
- Teachers can use social media as a platform to collaborate with one another and communicate with students outside of the classroom.
- Musicians and artists can build their following through social media without any type of contract.
- Four year institutions use social media to recruit students.
Cons[92]
[edit | edit source]- Social enables the spread of "fake news".
- Through the use of social media users take the risk of allowing the government into their private lives.
- According to the American Journal of Family Therapy students who heavily used social media tend to have lower grades.
- According to A University of Edinburgh Business School study users with more friends on Facebook tend to have a higher stress level and relationship problems offline.
- Social media can cause people to waste time.
- Using social media can effect job stability for users in the future through negative use.
- The 2013 Diagnostic and Statistical Manual of Mental Disorders correlates social media use with personality and brain disorders.
- Digital Future at the USC Annenberg School found that people spend less time communicating face-to-face because of increased use on social media.
- Social media can be accessed by anyone including criminals who promote violence and crime and recruit gang members.
- Location services promoted by social media can endanger the military and journalists by using it.
- Productivity is stunted by the use of social media.
- Cyberbullying is committed on every form of social media.
- Social media allows users to produce "pornography" which can lead to criminal charges.
- Social isolation can happen while using social media.
- Users who use social networking tend to fall for amateur advice and self diagnosis health problems which can cause negative effects.
- Social media can spread hate groups more easily.
- Younger users may not understand the public and viral nature of social networking sites.
- Through the use of social media students can cheat more easily on school assignments.
- Social media can subject users to an invasion of privacy.
- Student-teacher relationships can become inappropriate through the use of social media.
- Anyone using social media are subject to unauthorized sharing more easily.
- Students using social media can harm their chances at getting into college through negative use.
- Everything that users put on the internet, social media, is forever, and may have future consequences.
- Users of social media are subject to hacks, identity theft, and viruses.
Social Media Advertising
[edit | edit source]
The high usage of social media networks on mobile phones makes them an ideal platform for advertising [93]. According to Sprout Social “The average person clocks in more than six hours online daily” [94]. Now. Market Land depicts this further by stating: “With total activity on smartphones and tablets accounting for 60% of digital media time spent in the U.S., there’s no denying that reaching users while on mobile devices is the next big wave in advertising — and social media advertising is the best native option.” Businesses have a direct link to the consumer’s interests as they have the potential to find new clients by what the user shares on their social media account. [95]
Advertising on social media can directly promote a product to the user without disturbing them as they are already constantly on these social networking sites on their mobile phones [96]. With word-of-mouth advertising being the most trusted form of advertising in the eyes of the consumer, money is now being given influential users to spread the word about brands. [97].
By 2010, the amount of users using Facebook totalled to more than the populations of most countries and this is why it was the second most popular visited website, only falling behind the search engine, Google. [98]
Facebook brought in $8.4 billion in advertising in the 10 years since May 2005, when it instigated its first advertising option [99]. Sprout Social explains how Facebook has managed to generate this revenue by stating “Not only does it have the largest audience with 1.49 billion monthly active users, but 92% of social marketers use the social network for advertising” [100]. Market Land furthers this point by stating: “mobile advertising was on course to comprise 68% of Facebook’s revenue and 84% of Twitter’s in 2014, and two-thirds of social media advertising spend is forecasted to go towards mobile ads in 2018, creating a $9.1 billion market on mobile. [101]. This highlights how big an industry social media advertising is and the amount of revenue that can be produced on popular social media sites such as facebook.
These days, customers are trusting the advertising that is shared through social media and this is one of the main reasons why powerful social media users are being paid to advertise businesses on their social media platforms [102]. Seopremiers explains the benefits that viral social media users can get as they get “sent out samples, write reviews, pose for photographic collaborations, are provided free return airfare and luxury hotel stays, get invited to exclusive parties and events, and partner with brands for exciting giveaways and competitions.” [103]. The mirror explains this further by stating that: “Instagrammers with more than 1,000 followers could earn £40 or more a post, according to the app Takumi, while bigger users could make up to £2,000.” [104]. This depicts that Instagram is actually providing jobs and a stable income for “Instagram famous” users.
Zoella, a Vlogger and Global Beauty Entrepreneur is making millions through her social media platforms. Zoe Elizabeth Sugg is an English fashion and beauty vlogger, and is best known for her Youtube channel 'Zoella'. She currently has 11,638,935 subscribers on Youtube and has had 938,027,686 views since she joined 2 Feb 2007. [105]
Tammy Hembrow, is an Instagram famous woman who lives in Australia. She currently has over 5.7m Instagram followers and receives hundreds of thousands of likes on each post. Because of the fame she has gained from her Instagram account she has managed to manufacture a successful fitness company, as one of the things she is most famous for is her figure. According to seopremier she earns an outstanding $2000 AUD, minimum, per picture she posts advertising a brand. [106]. The image to the right shows Tammy Hembrow using social media advertising. She is modelling a dress and has tagged the clothing company in the post in order to further promote the brand. Tammy received over 300,000 likes on the post, highlighting the high level of publicity she has given to the business.
However social media users can often feel overwhelmed and bombarded by the amount of online advertising and on the networks. Most platforms have the ability to disable certain adverts so users are feeling the need to do this to stop themselves being swamped by social media marketing [107].
Social Media Marketing
[edit | edit source]
In the present day society social media is a big part of our everyday lives. Companies and business are taking in upon themselves to use social media to expand their businesses and maximise their profits. An article posted by business insider in 2016 depicts the gross amount of revenue generated by social media advertising- “Social ad revenue in the U.S. will surpass $30 billion by 2021, according to new estimates from BI Intelligence, Business Insider's premium research service, based on historical data from IAB, PwC, and IHS. This figure is up from an estimated $15.5 billion in social ad revenue in 2016 and represents a five-year compound annual growth rate (CAGR) of 15%.” The explanation given for the extreme income produced by social media is down to how often people are on their phones, and on social media sites. [108]. Companies are using social media marketing as a platform to directly showcase their products to consumers and investors, whilst using social media the company has the opportunity to go “viral” and attract lots of new customers. [109]. There is a good opportunity to make a mass amount of revenue from social media marketing particularly on platforms such as Instagram.
Prosumers
[edit | edit source]Cisco states that “Alvin Toffler defined the prosumer as someone who blurs the distinction between a “consumer” and a “producer.” The term has since come to mean a variety of things, but here we define it as someone who makes little distinction between his or her home and work lives. The prosumer engages in activities belonging to either sphere, regardless of time or location.” [110]. Forbes Magazine tries to define the term further. They state: “The term “prosumer” has transformed from meaning “professional consumer” to meaning “product and brand advocate.” Rather than simply “consuming” products, people are becoming the voices of those products and significantly impacting the success or failure of companies, products, and brands, particularly through their involvement on the social web.” [111]. In the present digital age consumers have the power in how a company is perceived online. People have the ability to promote a business through platforms such as social media sites and blogs. People can gain a high amount of followers on these sites and have the ability to change their follower’s opinions on a business. Businesses have to take a precise approach to prosumers. They have to seek for and approach prosumers that could best promote their brand. Often prosumers will be sent free samples in return for promoting the businesses brand online. The businesses have to keep a firm relationship with the prosumers in order to gain the best promotion for their business [112].
Surveillance on Social Media
[edit | edit source]Surveillance
[edit | edit source]Surveillance is generally described as the mass collection and processing of data personal data, often justified as being for the safety of the Public. Traditionally, surveillance is often carried out by large government organisations in the interests of security, although increasingly private organisations are exploiting personal information that can be gathered online for corporate interests.[113]
Online surveillance is relatively new concept, that has developed significantly over the early 21st century. With the advent of the internet social media platforms, Government agencies, and indeed private organisations now have personal information that is easily accessible and easy to exploit. Due to the architecture of the internet, data is shunted through multiple servers and machines when being sent from one location to another. This involves copying the data many times over, resulting in data trails. These data trails, coupled with the rise of social media mean personal information can be easily gathered and traced.
Online surveillance is a great example of an ‘industry’ that has been made possible by digital labour, specifically the automation of data collection and complex algorithms used to sort through any relevant information that can be exploited. In contrast to traditional surveillance techniques, online surveillance is completely invisible, and requires far less effort and infrastructure such as camera’s and microphones, due to its computerised nature.
PRISM
[edit | edit source]Concerns of surveillance were recently renewed after Edward Snowden shed light on the clandestine gathering of personal information from both telephone logs and website data by the American National Security Agency (NSA).
One of the revelations to come from this scandal was the discovery of an online surveillance program known as PRISM that had access to nine large internet firms including Facebook and Google, that was operated by the NSA.[114] The leaked documents contained slides form a presentation given by the NSA detailing information on how PRISM operated, as well as implicating other intelligence agencies such as the GCHQ, the British equivalent to the NSA. PRISM allowed agencies such as the GCHQ to avoid the normal legal process in gaining personal information such as photographs and emails.[115]
Third-party Surveillance On Social Media
[edit | edit source]Challenging the traditional understanding of surveillance, many private companies now exploit personal data for financial gain.
One of the ways private organisations can track their users is through the use of Tracking cookies. These small data packets are often used by websites to save personal preferences when using said site, but they can also be exploited to monitor internet browsing habits. [116] Many cookies are now also accessed by websites for targeted personal advertising.
Facebook was also revealed to monitor their users browsing habits, even when those users were currently logged off of their accounts. Tracking cookies that were used by Facebook were still stored on their users' devices when they logged off, and thus were still active. This allowed Facebook to continue to monitor their users' activities regardless of whether they were currently on the site.[117]
Much of this surveillance is beginning to concern the public, much like PRISM and government surveillance had a surge of public awareness. Documents containing large amounts of personal information and tracking data have been recently revealed after being released through due to European data protection laws. Facebook was revealed to have stored up to 880 pages of personal information on a single user. [118]
Facebook Beacon
[edit | edit source]Implemented in November 6th, 2007, Facebook Beacon was a program that recorded information on its users and sent them to third party companies for advertising purposes. Third part companies who were members of Facebook Beacon, known as ‘Affiliates’, recorded information carried out on their site such as buying a product or rating a video, and then sent this information to Facebook. Through embedded code on the webpage, Beacon also posted on the users Facebook page information on the actions carried out on the site. The users were given a 10-second popup in which to decline the information being posted on their profile, but any data collected was still sent to Facebook which the user had no control over. [119]
Controversially, Facebook Beacon was automatically enabled for users, who had to turn it off manually if they did not want to participate in the service. Furthermore, ‘Friends’ of users who had disabled Beacon still had their information recorded if their Facebook ‘Friends’ still had the feature enabled, meaning information was being wrongly recoded and sent to Facebook without their consent. The opt-out process was also critiqued for being overly complex.[120]
Although Facebook Beacon was a commercial program, as opposed to a government security measure, it ties in well with the concepts of Digital Labour and Online Surveillance. Facebook Beacon also highlights the many ethical issues brought on by the gathering of personal data online.
Always On Culture
[edit | edit source]With instant communication available between all users of mobile phones, modern society has become reliant on mobile technology. ‘Always on Culture’ describes the blurred lines between users, and their ‘online selves’, as people become more connected to their online identities. [121] The constant connectivity Always on culture shouldn’t be confused with phone addiction.
Related heavily to Always On Culture, Web 2.0 describes the ways in which the interactions through the internet have developed and changed. The internet is now far more collaborative, and based around sharing rather than simply consuming. [122]. This could be witnessed in early websites like Napster and Bit-torrent, which focused on sharing files between users. This developed in Social Media platforms like Facebook and Twitter, which focus on the sharing of thoughts and opinions. The interactions described by Web 2.0, in addition to the ubiquity of mobile devices and internet connectivity, have enabled Always On Culture.
Always on culture essentially enables the widespread surveillance on the internet we see today, by having users always connected to a device which stores their location data, web browsing habits, and logs of who they spoken too. The revelation that Facebook tracks its users, regardless of whether they are online, mirrors Always On Culture.[123] Facebook users, and indeed Internet users in general, are intrinsically linked to their accounts and online identities, even when not actively connected. This means that their activities are also available to be exploited through surveillance at any time.
Glossary
[edit | edit source]- Capitalism
Capitalism refers to an economic system based on the private ownership of the means of production and their operation for profit.
- Critical Theory
Critical theory refers to the critique of society and culture through the application of knowledge of the Social sciences and humanities.
- Crowdfunding
A means of raising a large sum of money through small contributions from a large amount of people, typically through the internet.
- Cyber Bulling
Refers to a way that users online emotional torment another user through any means of social media.
- Dialectical Reasoning
A philosophical method for understanding the world which focuses on identifying contradictions. Dialectics argues that society is shaped by contradictions (eg. being and nothingness, life and death).
- Digital Labour
The term used to describe how corporate Internet platforms exploit user activity for profit.
- Frankfurt school
The term used to describe a group of neo-Marxist theoreticians, and their respective theories, brought together at the Institute for Social Research under the direction of Max Horkheimer.
- Social Media
The collective of online communication channels dedicated to community-based input, interaction, content-sharing and collaboration
- Globalisation
The process of international integration arising from the interchange of world views, products, ideas, and other aspects of culture.
- Information Ecology
This is the connection between ecological ideas with the dynamics and properties of the increasingly dense, complex and important digital informational environment and has been gaining acceptance in a growing number of disciplines.
- Instant Messaging
a type of online chat that offers real-time text transmission over the Internet.
- Information Explosion
Is the rapid increase of the amount of published data and as the amount of information published grows, can lead to difficulties managing the data and lead to an information overload.
- Information Overload
The exposure of too much information or data at one time.
- ICT
Stands for Information and Communications Technologies. It is an extended term for information technologies that puts emphasis on the importance of unified communications and the integration of telecommunications.
- Information Age
This is a time in history where there has been a shift from the traditional industry, characterised by the industrial revolution, to an economy that is based on the amount of information available on technologies such as computers.
- Network Effect
A network effect is the effect that one user of a good/service has on the value of that particular product to other people.
- Old Media
The traditional means of communication that existed before the creation of new mediums such as the internet.
- Radio
The technology of using radio waves to carry information, such as sound, by systematically modulating properties of electromagnetic energy waves transmitted through space.
- Surveillance
The observation, and mass process of personal data. Although traditionally understood as being undertook by governments, private organistions are starting to proccess personal data on an industrial scale.
- Telegraph
The long-distance transmission of textual or symbolic messages without the physical exchange of an object bearing the message.
- Telephone
A telecommunications device that permits two or more users to conduct a conversation when they are too far apart to be heard directly.
- Tracking Cookie
These are small packets of data which are stored on users computer by websites they have visited. They are often exploited by Third Party’s for targeted advertising. They can be used to monitor internet browsing habits.
- Web 2.0
How interactions on the internet have developed, resulting in more user created content and collaboration. Linked in part to the rise of Social Media.
References
[edit | edit source]- ↑ Seviigani, Sebastian. Fuchs, Christian. “What is Digital Labour? What is Digital Work? What’s their Difference? And Why Do These Questions Matter for Understanding Social Media?“, Triple C, January 2013. Retrieved on 22 February 2017.
- ↑ Frayssé, Olivier. “Digital Labour and Prosumer Capitalism“, AIAA, July 2015. Retrieved on 6 March 2017.
- ↑ Mandel, Ernest. “An Introduction to Marxist Economic Theory“. Retrieved on 2 March 2017.
- ↑ Fuchs, Christian. “Digital Labour and Karl Marx“, Routledge, March 2014. Retrieved on 4 March 2017.
- ↑ Scholz, Trebor. “Digital Labor: The Internet as Playground and Factory“, Routledge, 2012. Retrieved on 4 March 2017.
- ↑ Scholz, Trebor. “Digital Labor: The Internet as Playground and Factory“, Routledge, 2012. Retrieved on 4 March 2017.
- ↑ Fuchs, Christian. “Theorising and analysing digital labour: From global value chains to modes of production“, The Political Economy of Communication, 2, 2014. Retrieved on 5 March 2017.
- ↑ Seviigani, Sebastian. Fuchs, Christian. “What is Digital Labour? What is Digital Work? What’s their Difference? And Why Do These Questions Matter for Understanding Social Media?“, Triple C, January 2013. Retrieved on 22 February 2017.
- ↑ Fuchs, Christian. “Free Labor: Producing Culture for the Digital Economy“, Duke University Press, 2000. Retrieved on 6 March 2017.
- ↑ Fuchs, Christian. “Digital Labour and Karl Marx“, Routledge, March 2014. Retrieved on 4 March 2017.
- ↑ Scholz, Trebor. “Digital Labor: The Internet as Playground and Factory“, Routledge, 2012. Retrieved on 4 March 2017.
- ↑ Marx, Karl. “Economic and Philosophic Manuscripts“, Progress Publishers, 1959. Retrieved on 3 March 2017.
- ↑ Andrejevic, Mark. “Surveillance and Alienation in the Online Economy“, Surveillance Studies Network, January 2011. Retrieved on 3 March 2017.
- ↑ Fuchs, Christian. “Digital Labour and Karl Marx“, Routledge, March 2014. Retrieved on 4 March 2017.
- ↑ Fuchs, Christian. “Theorising and analysing digital labour: From global value chains to modes of production“, The Political Economy of Communication, 2, 2014. Retrieved on 5 March 2017.
- ↑ Reyman, Jessica. “User Data on the Social Web: Authorship, Agency, and Appropriation“, The National Council of Teachers of English, May 2013. Retrieved on 7 March 2017.
- ↑ Kruger, Steffen. “Alienation and Digital Labour“, TripleC, 2014. Retrieved on 6 March 2017.
- ↑ Theories of The Information Society, First Edition, Frank Webster, 1995.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ Theories of The Information Society, First Edition, Frank Webster, 1995.
- ↑ Media, Politics and the Network Society, First Edition, Robert Haasan, 2004.
- ↑ Theories of The Information Society, First Edition, Frank Webster, 1995.
- ↑ Theories of The Information Society, First Edition, Frank Webster, 1995.
- ↑ Theories of The Information Society, First Edition, Frank Webster, 1995.
- ↑ Theories of The Information Society, First Edition, Frank Webster, 1995.
- ↑ New Media: An Introduction, Third Edition, Terry Flew, 2008.
- ↑ New Media: An Introduction, Third Edition, Terry Flew, 2008.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ New Media : An Introduction , Third Edition , Terry Flews , 2008.
- ↑ How Many Websites are There? The Atlantic, 2015, Date Accessed 7th March 2017, https://www.theatlantic.com/technology/archive/2015/09/how-many-websites-are-there/408151/
- ↑ Media, Politics and the Network Society, First Edition, Robert Haasan, 2004.
- ↑ Media, Politics and the Network Society, First Edition, Robert Haasan, 2004.
- ↑ Media, Politics and the Network Society, First Edition, Robert Hassan, 2004.
- ↑ New Media: An Introduction, Third Edition, Terry Flew, 2008.
- ↑ New Media: An Introduction, Third Edition, Terry Flew, 2008.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ New Media: An Introduction, Third Edition, Terry Flew, 2008.
- ↑ New Media: An Introduction, Third Edition, Terry Flew, 2008.
- ↑ New Media: An Introduction, Third Edition, Terry Flew, 2008.
- ↑ The Information Society, First Edition, Robert Hassan, 2008.
- ↑ Claudio Corradetti. "The Frankfurt School and Critical Theory" Retrieved 5th March 2017. http://www.iep.utm.edu/frankfur/
- ↑ Horkheimer, M. , Adorno, T. , Noeri, G. 2002. "Dialectic of enlightenment" Stanford University Press.
- ↑ Martin, J. 1996. "The dialectical imagination: A history of the Frankfurt School and the Institute of Social Research, 1923 - 1950" https://www.ucpress.edu/book.php?isbn=9780520204232
- ↑ Finlayson, J. G. 2005 Habermas a very short introduction. Oxford. Oxford University Press.
- ↑ Agger, B. 2006. "Critical Social Theories An Introduction 2nd Edition" Oxford University Press
- ↑ Fuchs, C. Social Media: A Critical Introduction. 2014. Sage Publications
- ↑ Allmer, Thomas. "Critical Theory and Social Media", edited by Thomas Allmer, Taylor and Francis. 2015. Retrieved 5th March 2017. https://ebookcentral.proquest.com/lib/stir/detail.action?docID=2011264.
- ↑ Whatis.Techtarget (2016). Social Media. Retrieved 28/02,2017, from [17]
- ↑ Riese, Monica. “The Definitive History of Social Media“, The Daily Dot, February 2017. Retrieved on 3 March 2017.
- ↑ Library of Congress. “Invention of the Telegraph“, Retrieved on 3 March 2017.
- ↑ https://en.wikipedia.org/wiki/Invention_of_the_telephone
- ↑ Hendricks, Drew. "Complete History of Social Media: Then and Now", 8 May 2013. Retrieved on 7 March 2017.
- ↑ Digital Trends Staff. "The History of Social Networking", 14 May 2016. Retrieved on 3 March 2017.
- ↑ https://en.wikipedia.org/wiki/Six_degrees_of_separation
- ↑ Hale, Benjamin. "The History of Social Media:Social Networking Evolution!". 16 June 2015. Retrieved on 3 March 2017.
- ↑ Riese, Monica. “The Definitive History of Social Media“, The Daily Dot, February 2017. Retrieved on 3 March 2017.
- ↑ Peschau,Matt. "Using Social Media to Increase Audience Engagement" Retrieved on 8 March 2017.
- ↑ "About Us." About Us • Instagram. N.p., 2017. Web. 01 Mar. 2017
- ↑ "About Us." About Us • Instagram. N.p., 2017. Web. 01 Mar. 2017
- ↑ "FAQ." FAQ • Instagram. N.p., 2017. Web. 01 Mar. 2017
- ↑ Weber, Tim. "Facebook Buys Instagram Photo Sharing Network for $1bn." BBC News. BBC, 10 Apr. 2012. Web. 01 Mar. 2017.
- ↑ "Instagram: Active Users 2016." Statista. N.p., n.d. Web. 01 Mar. 2017.
- ↑ "About Us." About Us • Instagram. N.p., 2017. Web. 01 Mar. 2017
- ↑ Simon, Ellen. "How Instagram Makes Money." Investopedia. N.p., 27 Nov. 2016. Web. 01 Mar. 2017.
- ↑ "Facebook - About | Facebook." Facebook - About | Facebook. N.p., n.d. Web. 01 Mar. 2017.
- ↑ Phillips, Sarah. "A Brief History of Facebook." The Guardian. Guardian News and Media, 25 July 2007. Web. 01 Mar. 2017.
- ↑ Protalinski, Emil. "Facebook Passes 1.23 Billion Monthly Active Users." The Next Web. N.p., 29 Jan. 2014. Web. 01 Mar. 2017.
- ↑ Simon, Ellen. "How Instagram Makes Money." Investopedia. N.p., 27 Nov. 2016. Web. 01 Mar. 2017.
- ↑ Simon, Ellen. "How Instagram Makes Money." Investopedia. N.p., 27 Nov. 2016. Web. 01 Mar. 2017.
- ↑ "Company | About." Twitter. Twitter, 30 June 2016. Web. 01 Mar. 2017.
- ↑ "Company | About." Twitter. Twitter, 30 June 2016. Web. 01 Mar. 2017.
- ↑ "Company | About." Twitter. Twitter, 30 June 2016. Web. 01 Mar. 2017.
- ↑ "Twitter Usage Statistics." Twitter Usage Statistics - Internet Live Stats. N.p., n.d. Web. 01 Mar. 2017.
- ↑ Levy, Gabrielle. "Twitter Wins Big in 2016 Campaign." N.p., n.d. Web.
- ↑ Haque, Umair. "The Reason Twitter's Losing Active Users." Harvard Business Review. N.p., 12 Feb. 2016. Web. 02 Mar. 2017.
- ↑ "Snap Inc." Snap Inc. N.p., n.d. Web. 02 Mar. 2017.
- ↑ Bernazzani, Sophia. "A Brief History of Snapchat." HubSpot. N.p., n.d. Web. 02 Mar. 2017.
- ↑ Bernazzani, Sophia. "A Brief History of Snapchat." HubSpot. N.p., n.d. Web. 02 Mar. 2017.
- ↑ Bernazzani, Sophia. "A Brief History of Snapchat." HubSpot. N.p., n.d. Web. 02 Mar. 2017.
- ↑ Fitzpatrick, Laura. "Brief History YouTube." Time. Time Inc., 31 May 2010. Web. 08 Mar. 2017.
- ↑ Rosenberg, Eric. "How Youtube Ad Revenue Works." Investopedia. N.p., 26 Mar. 2015. Web. 08 Mar. 2017.
- ↑ "Press." About Pinterest. N.p., n.d. Web. 07 Mar. 2017.
- ↑ Savchuk, Katia. "Pinterest Founders Are Among The World's Youngest New Billionaires." Forbes. N.p., 03 Mar. 2016. Web. 07 Mar. 2017.
- ↑ O'Reilly, Lara. Business Insider, 8 Jan. 2016. Web. 07 Mar. 2017.
- ↑ "Social Networking ProCon.org." Are Social Networking Sites Good for Our Society? N.p., n.d. Web. 08 Mar. 2017.
- ↑ "Social Networking ProCon.org." Are Social Networking Sites Good for Our Society? N.p., n.d. Web. 08 Mar. 2017.
- ↑ Why Social Media Advertising Is Set To Explode In The Next 3 Years (2015), Marketing Land. Retrieved 06,03,2017 from [18]
- ↑ Starter Kit: Your Guide to Social Media Advertising (2015), Sprout Social. Retrieved 06,03,2017 from [19].
- ↑ Why Social Media Advertising Is Set To Explode In The Next 3 Years (2015), Marketing Land. Retrieved 06,03,2017 from [20]
- ↑ Why Social Media Advertising Is Set To Explode In The Next 3 Years (2015), Marketing Land. Retrieved 06,03,2017 from [21]
- ↑ They Make How Much?!, Seopremier. Retrieved 06,03,2017 from [22]
- ↑ Close, A. (2012) Online Consumer Behaviour, Taylor and Francis: England.
- ↑ Why Social Media Advertising Is Set To Explode In The Next 3 Years (2015), Marketing Land. Retrieved 06,03,2017 from [23]
- ↑ Starter Kit: Your Guide to Social Media Advertising (2015), Sprout Social. Retrieved 06,03,2017 from [24].
- ↑ Why Social Media Advertising Is Set To Explode In The Next 3 Years (2015), Marketing Land. Retrieved 06,03,2017 from [25]
- ↑ They Make How Much?!, Seopremier. Retrieved 06,03,2017 from [26]
- ↑ They Make How Much?!, Seopremier. Retrieved 06,03,2017 from [27]
- ↑ These Instagram users earn THOUSANDS for a single post - how much could your pics be worth? (2015) The Mirror. Retrieved 06,03,2017 from [28]
- ↑ Zoella: About (2017), Youtube. Retrieved 08,03,2017 from [29]
- ↑ They Make How Much?!, Seopremier. Retrieved 06,03,2017 from [30]
- ↑ Social media advertising and brand posts: four lessons to live by (2016), Telegraph Connect: Better Business. Retrieved 06,02,2017 from [31]
- ↑ Social ad revenue is set to double by 2021 (2016) Business Insider. Retrieved, 02,03,2017, from [32]
- ↑ Evans, D., Bratton, S., McKee, J. (2010) Social Media Marketing: The Next Generation of Business Engagement, John Wiley & Sons, Incorporated: England.
- ↑ Prosumers: A New Growth Opportunity (2008) Cisco. Retrieved, 03,03,2017 from [33].
- ↑ The Shift from CONsumers to PROsumers (2010), Forbes. Retrieved 06,03,2017 from [34]
- ↑ The Shift from CONsumers to PROsumers (2010), Forbes. Retrieved 06,03,2017 from [35]
- ↑ Lyon, David. Computers, Surveillance, and Privacy. 1996. Retrieved 2017.
- ↑ 4 BBC News. “Edward Snowden: Leaks that exposed US spy programme”. 2014. Retrieved 2017.
- ↑ Gellman, Barton. “U.S., British intelligence mining data from nine U.S. Internet companies in broad secret program” June 7, 2013. Retrieved March 1, 2017.
- ↑ Humphries, Matthew. https://www.geek.com/geek-pick/facebook-explains-why-it-tracks-you-even-when-youre-logged-out-1424083/ “Facebook explains why it tracks you even when you’re logged out”. 2011. Retrieved 5 March, 2017.
- ↑ Humphries, Matthew. https://www.geek.com/geek-pick/facebook-explains-why-it-tracks-you-even-when-youre-logged-out-1424083/ “Facebook explains why it tracks you even when you’re logged out”. 2011. Retrieved 5 March, 2017.
- ↑ Humphries, Matthew. https://www.geek.com/geek-pick/facebook-stores-up-to-800-pages-of-personal-data-per-user-account-1424807/. “Facebook stores up to 800 pages of personal data per user account”. 2011. Retrieved 5 March, 2017.
- ↑ Blizard, Katherine. http://true-reality.net/csc300/resources/Resources/Reference/Term-Papers/termpaper_blizard.pdf. “Facebook, Beacon and Your Privacy”. 2011. Retrieved February 28, 2017.
- ↑ Blizard, Katherine. http://true-reality.net/csc300/resources/Resources/Reference/Term-Papers/termpaper_blizard.pdf. “Facebook, Beacon and Your Privacy”. 2011. Retrieved February 28, 2017.
- ↑ Mandiberg, Micheal. “The Soccial Media Reader“, New York University Press, 2012. Retrieved on 5 March 2017.
- ↑ Mandiberg, Micheal. “The Soccial Media Reader“, New York University Press, 2012. Retrieved on 5 March 2017.
- ↑ Humphries, Matthew. https://www.geek.com/geek-pick/facebook-explains-why-it-tracks-you-even-when-youre-logged-out-1424083/. “Facebook explains why it tracks you even when you’re logged out”. 2011. Retrieved 5 March, 2017.
| This page or section is an undeveloped draft or outline. You can help to develop the work, or you can ask for assistance in the project room. |
Filter Bubbles and the Flow of Information
[edit | edit source]Introduction
[edit | edit source]
You are now aware of your breathing
pon reading this remark one might wish they hadn’t done so for, in drawing attention to an unconscious, automatic process we are encouraged to acknowledge the purely machine-like essence of our own internal body. When we think about breathing we invariably disturb its normal rhythm; our thoughts slow the machine and make it inefficient; our lungs have gone rogue and the staggering number of muscles used in breathing or blinking are rebelling. When our attention is cast on them they ebb then falter. This machine isn’t contingent on our active engagement and yet it is fundamentally tied to us, our habits, our environments – it is, indelibly: us!
Whereas our internal machinery was manufactured over many millions of years of evolution, to whom or to what process do we owe the internal machinery of the internet which operates as persistently as a heartbeat or the flexing of the diaphragm?
As we will see, beneath the internet lies its own mathematical language which directs our online activities in ways we might not have anticipated and, in understanding the most basic of concepts that breathing is vital to life, so too will we reveal how the internet’s underlying digital apparatus is now inexorably tied to our entire online experience.
Manufacturing Consent
[edit | edit source]"The past few years have witnessed a rapid penetration of the internet by the leading newspapers and media conglomerates, all fearful of being outflanked by small pioneer users of the new technology, and willing (and able) to accept loses for years while testing out these new waters. Anxious to reduce these losses, however , and with advertisers leery of the value of spending in a medium characterised by excessive audience control and rapid surfing, the large media entrants into the internet have gravitated to making familiar compromises – more attention to selling goods, cutting back on news, and providing features immediately attractive to audiences and advertisers."
|
In Noam Chomsky’s and Edward S. Herman’s essential work on the engrained modus operandi of mass communications media, we find a critical basis from which to continue. Manufacturing Consent delivers to us a critique that must pervade all our subsequent findings should we wish to truly scrutinise the situation at hand. Although it is beyond our reach to add to the propaganda model proposed by Chomsky and Herman, it stands nonetheless not only as a focal point for reflection but as an aide in going forward. Indeed, what Chomsky and Herman demonstrated is still as salient today and there will be interesting contrasts and comparisons to be made.
A Propaganda Model: Five Filters
[edit | edit source]"The elements interact with and reinforce each other. The raw material of news must pass through successive filters, leaving only the cleansed residue fit to print. They fix the premise of discourse and interpretation, and the definition of what is newsworthy in the first place, and they explain the basis and operations of what amount to propaganda campaigns."
|

The "Filter Bubble" was a term coined in a work of 2011 by Eli Pariser [3] . Before we expand on what precisely Pariser means, for our pursuit let us first suggest that Pariser’s filter bubble owes its primary conception to the Five Filters to which the “raw material of news must pass through”. In doing so, we will see how the invisible bubble that filters – and then constructs – our internet habits first emerged in the essential ingredients of a system-supportive, propaganda model. The Five Filters of this model are:
- 1) Size [4] ; (concentrated ownership, owner wealth, and profit orientation of the dominant mass media firms). The growth of a select few media giants has been astounding; in the US, the wealth and control is so concentrated that 6 media giants hold domain over 90% of what Americans choose to either read, watch or listen to. “Choose” is contradictory here for whatever one ‘chooses’ one invariably gets only the choice decreed from the media barons above.
- 2) Advertising [5]; (as the primary income source of the mass media). Shining an investigative spotlight on Social Media platforms we see that Facebook in short, makes its money from advertising. How is it that advertisements have become so ubiquitous? What is an editorial piece and what is a piece specially crafted for the purpose of selling a product, service, idea? The profit motive exists at every stage to which we have been inducted not as conscious actors but as mere consumers.
- 3) Sourcing [6] ; (The reliance of the media on information provided by government, business, and “experts” funded and approved by these primary sources and agents of power). How this has evolved with the now widespread popularity of technology that allows instantaneous video capture is of course remarkable but it would be too simple to characterise this as ‘progress’ and ignore the material forces at play.
- 4) Flak [7] ; (as a means of disciplining the media). ‘Bad press’ that is, the spread of unfavourable views of a media outlet encourages advertisers to withdraw patronage – a severe and costly punishment. This emboldens the advertisers with a great and powerful energy: they can either “make” or “break” you depending on how supple you are to their message.
- 5) Ideology [8] ; (Exactly meant is the ideology of anti-communism. This is the state religion of America). Communism as the ultimate evil has always been the spectre haunting property owners, as it threatened the very root of their class positions and superior status. If it threatens property interests call it Communism and mobilize the populace against the enemy! Today, there might not be some encroaching Red-Terror from the East but, how has the media-sanctioned ideology shaped our views with regards to terrorism, austerity measures, illegal immigration? Can a person even be illegal? Is what we do to them also terrorism?
Concurrent with time of writing, Al Jazeera English have released an animated short film giving an accessible, easy to understand account of the five filters model.
What the ‘filter bubble’ proposes is that what has passed through these five filters is in turn, re-filtered by the end user in a process that suggests a horrible circularity. This is a personalised process that only guarantees to return to the user what they already ‘like’, of course what they like to begin with is a contrivance manufactured by the dominant media interests to foster our role as a pliant consumers.
The Culture Industry: Give us again only what we had once before!
[edit | edit source]"The culture industry piously claims to be guided by its customers and to supply them with what they ask for. But while assiduously dismissing any thought of its own autonomy and proclaiming its victims its judges, it outdoes, in its veiled autocracy, all the excesses of autonomous art. The culture industry not so much adapts to the reactions of its customers as it counterfeits them. It drills them in their attitudes by behaving as if it were itself a customer. […] The culture industry is geared to mimetic regression, to the manipulation of repressed impulses to copy. Its method is to anticipate the spectator’s imitation of itself, so making it appear as if the agreement already exists which it intends to create. It can do so all the better because in a stabilized system it can indeed count on such agreement, having rather to reiterate it ritualistically than actually produce it. Its product is not stimulus at all, but a model for reactions to non-existent stimuli."
|
What Adorno is talking about here is exactly the notion we're seeking to explore. This will become increasingly apparent when we delve into the systems which 'personalise' our experience; giving us "what we want whether we like it not!" This rings true most evidently in the examples of Netflix and Amazon where recommendation is translated as "because you watched..." and "people also bought..." We are the victims of a mechanism in these examples which we will subject to further analysis. These filtered products of the Culture Industry are so ubiquitous and yet (or, because thereof) their thoughtful exposition might conjure feelings of dread and anxiety. It is as it were our very character was under threat; so closely tied the relationship is between a concept of the self and our consumption habits. Indeed, In a neo-liberal system that emphasises 'the market' above all else, all that is required of the individual is to consume - that is the extent of our responsibility and nothing more. Should we "pop" the matrix of the filter bubble with the sharpened tools of our analytical set we might uncover a new route to a culture that doesn't diminish but expands the democratic potential of our technological systems. And perhaps, just as these filtering processes have been designed-in so too can they be designed-out and replaced with something better suited to our needs.
"Just as the factory farming system that produces and delivers our food shapes what we eat, the dynamics of our media shape what information we consume. [...] We are predisposed to respond to a pretty narrow set of stimuli - if a piece of news is about sex, power, gossip, violence, celebrity, or humour, we are likely to read it first. This is the content that most easily makes it into the filter bubble.
|
The Power of Algorithms
[edit | edit source]This ties in to the idea of filter bubbles and the flow of information through the impact it has on organizations and consumers of said organizations. To set an example we will look at the impact that an algorithm would have on an online shopper. Every time the online shopper makes a purchase, or even so much as searches a product on a website, this information is recorded and held onto their account, so every time they use the account more and more data is added and a database on this person's shopping pattern is built. [11]
A real life example of this happening occurred in the US. A mathematical genius, Andrew Pole that worked on the algorithm system for the superstore franchise Target, was approached by collegues who asked him if he could use the algorithm system to figure out whether or not one of their customers was pregnant. The reason he was asked to carry out this somewhat bizarre task is because new parents always shop big in superstores like Target, as they have such a wide range of products, so figuring out when female customers were pregnant could end up being very money efficient.
Pole ended up taking up the challenge and in short; he was successful and the algorithm worked out that a customer was pregnant, before some of her immediate family even knew. (For the full article- [12]This just shows the power that an algorithm can possess when used correctly- it can go as far as working out personal information about you such as pregnancy, even determining what stage of pregnancy you are it. This is a very strong tool, which if it isn't blocked can reveal a lot about a person's character and could even be a security risk.

Algorithm has a direct impact on creating a 'Filter bubble' through the ability algorithm has on recording a users search data. One interesting finding was a comparison between two people's search of the organisation BP (British Petroleum). One user who had searched it found several articles and webpages discussing the investment news related to BP whilst another user found several articles about an oil spill that had occurred. So despite searching the exact same thing the filter bubble of each individual impacts on what data actually comes up.
This can be looked at positively and negatively. As a positive; whatever you search is tailored towards you previous searches, in theory meaning you have to put in less effort to find what you are actually looking for. However, from a negative viewpoint, does this mean that one's search is restricted to what they have done in the past? Due to being in a filter bubble certain information will not get through, or it will take a long time to try and obtain. So in spite of the positive impact algorithm can have, it can be perceived as a tool that restricts the user from fresh information, and it does so without the user being aware of what is actually happening.
From the Five Filters to Five Data Points
[edit | edit source]"The basic code at the heart of the new internet is pretty simple. The new generation of internet filters looks at the things you seem to like – the actual things you’ve done, or the things people like you like – and tries to extrapolate. They are prediction engines, constantly creating and refining a theory of who you are and what you’ll do and want next. Together, these engines create a unique universe of information for each of us – what I’ve come to call the filter bubble – which fundamentally alters the way we encounter ideas and information."
|
For the purposes of illustration and to give us a conceptual notion of this new personalized Internet that extrapolates even from our most innocuous actions a "theory of you" that in turn, moderates our subsequent activity, let us draw a comparison with the Soap Bubble hypothesis of the multiverse. From the inside of the filter bubble looking out the world comes to imbue (in the words of Pariser) the qualities of the Ptolemaic universe where everything revolves around us. The Internet itself could be described as a multiverse of these individual 'bubbles' each home to a personalized set of rules or laws of nature which are the filtered offerings derived from our constructed data points. Our bubble in this multiverse of bubbles is full of the products filtered for our convenience: it's a "custom-tailored world". We can make it as self-lobotomizing as we wish; if we want to exclude uncomfortable items on reality TV or foreign wars, they're gone! If we don't follow links on the topics happening out with our national borders then they are deemed irrelevant and simply filtered out. This universe can be warm and welcoming, full of bright colors and soft fabrics where you need only occupy yourself with the things individual to you. Everything you see is a reflection of your interest and desires. You are never bored. You are never annoyed. You are never Challenged.
Your filter bubble is individual paradise; a digital North Korea where you are the Supreme Leader. [14]
"Five Data Points" - They do more surveillance than the NSA!
[edit | edit source]"[T]he top fifty Internet sites, from CNN to Yahoo to MSN, install an average of 64 data-laden cookies and personal tracking beacons each. Search for a word like 'depression' on Dictionary.com, and the site installs up to 223 tracking cookies and beacons on your computer so that other Web sites can target you with antidepressants."
|
In the above example, a search for "depression" would count as a data point and this search would then determine what you see next. Pariser notes that the company Hunch claims they can predict your consumer preferences correctly a staggering 80% of the time with only five such data points. More so, even without your five data points if 2 people you are connected with have disclosed five data points Hunch can still predict your future preferences accurately. What that means is that even if you are not giving data away about yourself, an interpretation of you can be formed from the data of your friends. However, doesn't this suggest a rather crude approximation of who a person is? Could five pieces of information really be so telling? Are we really so one-dimensional in our habits and in the company we keep? And, even if we are to what pleasure do we owe a company to trade as a commodity this information about ourselves? The predictions made on our consumer preferences might have come from the data points of friends concerning information they'd rather choose to not share personally but to which an algorithm has relieved them of control.
Proposed hypothetically, could we with an imagining of the cumulative effect of successively known data points arrive at a predetermined point based solely on this information? This could take the form of:
- data point 1) You are a frequent visitor to the twitter feed of Israeli news outlet Haaretz.
- data point 2) You made a Google search for "correct pronunciation of quinoa"
- data point 3) You bought "Islam for Dummies" on Amazon.
- data point 4) You have a friend on facebook who only posts about West Ham United.
- data point 5) You use Firefox Web Browser, being most active between the hours of 18:00 and 22:00.
With 5 data points what can we deduce about this fictional 'you'? The question seems utterly futile but it is the infinitely branching possibilities offered by this data which is crunched by the algorithms into results which might prove relevant, only incidental or completely random. An attempt to mine backwards through the data is the inverse of the processes at play; vague connections arise from the data and not the other way around. We can postulate on the troubling issues that would surface should one seek to get the measure of another's actions by way of data collection alone. Edward Snowden brought many of these issues of light and spoke at TED2014:
"People should be able to pick up the phone and call their family, people should be able to send text messages to their loved ones. People should be able to buy a book online, they should be able to travel by train, they should be able to buy an airline ticket without wondering how these events are going to look to an agent of the government years in the future; how they’re going to be misinterpreted and how they’re going to think what your intentions were."
|
While Snowden's revelations might seem frightening in the context of intelligence agency over-reach into our private lives, let us also point out that a private company such as Acxiom alone has accumulated an average of 1,500 pieces of data on each person in its database - which includes 96% of all Americans [16]. The signals we send out while online are commodities to be bought and sold. The 'individual' experience is the marketization of 'You' now realized as a product. What better testament to the success of a market-system where consumers are likewise products - and yet still profess their own exalted individualism! What's good for the customer is not what is good for the citizen and, if we should retain a disposition for democracy and seek to improve our material conditions, we should actively embrace the role of participating, conscious citizen.
The Private Sphere and Democracy
[edit | edit source]
The mobility of the private sphere
[edit | edit source]The Private sphere has changed as a result of technology. Once resigning in family homes and secluded areas, the private sphere existed as something that was somewhat static. It was very difficult to communicate with a group of people who were not in the same space as you. However, due to advancements in technology and the natural development of Web 2.0, people can now communicate and partake in discourse through online social networks. The easy accessibility of these networks means that one can tweet their opinion on a political matter during a work break or participate in online polls while watching the news. As a result, “Social network sites extend the connecting and mobility of the private sphere by providing online spaces that host offline and online networks of social relations”. [17]This meaning that we can connect with friends, family, and acquaintances privately online through computers and mobile phones located in private domestic spaces.This new mobility certainly changes individual civic habits. However, do these online social networks within the private sphere actually enhance democracy?
The Personalisation of Newsfeeds
[edit | edit source]The most common form of online communication is through social media sites such as Facebook. As social media profiles are based on identity users can “like” or “follow” institutions, businesses, organisations, and entertainment profiles in order to stay up to date with their own personal interests as well as staying in touch with friends, family and acquaintances.
However, this becomes problematic when individuals only subscribe to profiles that hold the same opinions and beliefs as their own. More specifically, Facebook gives users the option to filter out the information they do not wish to see by allowing individuals to delete or mute friends, or pages whose political or ethical viewpoints do not coincide with their own.
Moreover, the platform itself also holds a responsibility in the filtering out of information. Much like the customised search results of Google, Facebook filters out information which they believe to not suit an individual’s personal beliefs based on what they have liked and what their friends have liked.
These filter bubbles become incredibly problematic when we consider that 51% [18] of people with online access use social media as a news source, with 44% [19]using Facebook as their top social network for news. A further 61% of millennials use Facebook as their primary source for news about politics and government. [20] Therefore, it is clear that Facebook is not just a space were we connect with friends, but a space in which many obtain their news. As a result, through the creation of filter bubbles both for us and by us we create personalised newsfeeds, which show us the news that we want to see, rather than news that we should be seeing. In turn, this may make us blind to the issues and struggles that face other communities that we are not apart of.
Problems with personalised newsfeeds
[edit | edit source]- It segregates: Even though available to everyone, some argue that Facebook contains a built-in demographic bias as you need internet access and literacy skills in order to use the site. Moreover, its initial interface was structured around privileged educational institutions, hence the site carries an American bourgeois element [21]. Furthermore, “The networked nexus of the private sphere is vulnerable to the inequalities present in the public sphere” [22]Online social networks make the private sphere more mobile, however, they also replicate the pre-existing elites, inequalities and divides that exist within the public sphere. By separating communities within the private sphere, echo chambers are created whereby mutual opinions are shared and not debate. Thus, leaving the question, how will we progress if as a society we continue to be segregated into different social divides? If social and political issues, especially those affecting minorities are only fought by those in which they effect, then progress and solutions will prove harder to obtain.
- The self becomes the reference point: Social networks help autonomy, control, and expression. However, “social networks of the private sphere present ego-centred needs and reflect practices structured around the self: This would present liberating practices for the user, but not necessarily democratising practices for the greater society”[23]. By only subscribing to information we wish to see, we become focused on our own self-interests, our civic habits shift from a focus on the greater good, to a focus on the greater good surrounding ourselves. The private sphere proves hard to be democratic when the opposing side of the discourse is consistently silenced through filter bubbles. Thus, although social networks have a social and political place within a democracy, they don’t necessarily make democracy better. They are democratic, but not democratising.
Solutions to personalised newsfeeds
[edit | edit source]- Flip feed: This is the idea of Facebook installing a link which will allow the user to see an alternative newsfeed, one which is free from algorithms, and personalisation, thus showing the user a newsfeed which differs in opinion from their own.
- Taking control of your online content: Instead of only “liking” the pages of news outlets that you agree with, try to create a balanced feed for yourself by “liking” multiple news outlets who offer a different opinion from your own. [24]
- Review Options: Much like sites such as rotten tomatoes whereby users leave ratings on how good a film was, a review option on Facebook, may act as a tool for users to vote on how trustworthy a source is and thus may be a good way to avoid the growing spread of fake news on the site.[25]
- Facebook accepting its role as a news source: This is quite a complicated solution. Facebook at current, has no desire to accept its role as a new source. Rather, it continues to focus on boosting ad serving volume and engagement rates. [26] However, if it did, it could take on the responsibility of a news outlet and present a more balanced display of information to individual newsfeeds. The problem here is, do we really want Facebook to have more power over what we do and do not see?
Citizen journalism and the flow of information
[edit | edit source]Our interaction with news sources has evidently changed; reading the news is no longer a passive activity as citizens can now choose whether or not to endorse stories. Peer-to-peer news sharing engines such as Digg and Reddit allow users to vote on news stories that they deem to be the most important –thus possibly upsetting the hierarchy of news making and pluralising news agendas. [27]. The flow of information has completely shifted, instead of news flowing in a one to many format, it now flows from many to many. There is no longer a top to bottom flow of information where news outlets and editors are at the top deciding what is newsworthy. Therefore, mainstream news agendas are being contradicted by readers acting as news gatekeepers.

The role of citizen as gatekeeper is also a result of more and more journalism online being created by “the people formerly known as the audience” [28]. Citizen journalism has taken form in news outlets requesting and using live video footage, photographs and first-hand accounts from members of the public, for example the BBC introduced a user-generated content hub (UGC) in 2005. However, it is in the form of blogging that offers considerable democratic potential as blogging allows media consumers the opportunity to become media producers. This new power to report allows citizens to present stories beyond mainstream media’s set agendas, thus encouraging the plurality of voices and the expansion of public agenda. Citizens also have more time to invest in investigative work due to a lack of deadline constraints, thus they can produce in-depth follow-up stories which many journalists do not have time to do. Many citizen journalists also hold professional knowledge in a specific field, hence they can explore and discuss certain stories in greater depth than that of a professional journalist. However, many of these blogs created by citizens begin to regress into self-confessional posts that resemble diaries. Thus, sparking a debate around whether citizen journalism is about comment, evaluation and subjectivity rather than the objectivity traditionally presented by professional journalism organisations and reporters. However, Lasch[29] argues that narcissistic behaviour is motivated by the desire to be connected to society, the personal reference in blogs adds a human touch to their reports. It also must be noted that citizens are allowed to express their opinions, unlike most mainstream media outlets. Narcissism in blogging allows citizens to self-reflect, to analyse, and, to simply “get a lot of things off their chest”[30] Put simply, narcissism in citizen journalism aligns with the core ideas of democracy.
Furthermore, instead of citizens taking control over what is newsworthy, a few popular blogs or persons may determine news agendas on social networking sites, hence proving counteractive as it replaces the traditional agenda setter with that of an inexperienced popular figure. Therefore, news agendas are still being set, but instead of by a qualified editor, or the masses, they are being set by the online popular elite –which may be equal to or worse than the traditional system. Moreover, the idea of being under qualified is a major argument against citizen journalists, with many holding the belief that the public need trained journalists who can interrogate, collect information and use contacts in a way that citizens simply cannot.
Nevertheless, by citizen journalists and professional journalists working together, the private and the public sphere overlap in order to make something democratising. Citizen journalism does not replace professional journalism but enhances it.
The creation of a new space
[edit | edit source]The private sphere does not so much oppose the public sphere but works somewhat collaboratively beside it. Through social networks, the private sphere can be accessed by two parties at opposite sides of the globe, completely reinventing the domain. Although the private sphere is mobile, it faces a considerable amount of issues regarding the flow and balance of information. Social networks provide users with more control, autonomy and expression. However, despite these being key elements in a democratic society, they do not necessarily enhance democracy, thus as Zizi Papacharissi argues: [31]
“Far from a recipe for democracy the private sphere is an attempt at new space and a new sociality”—Zizi Parachrissi, A private sphere: Democracy in a digital age
Control over Flow of Information
[edit | edit source]Ramifications of Information Sharing
[edit | edit source]The information we share online has implications for us which reach further than simply our connections list on our social medias. If we, firstly, take the sharing of our personal information on social media we are enabled some form of control through privacy settings and decision making in relation to our interactions and friends lists which allows us to seemingly regulate which content of our own we share and with whom we share it. It is here where factors such as “impression management” and the forming of an online identity come into play which aid us when faced with these decisions. However, the flow of our information online reachers further than we imagine and there are implications which arise from the information we choose to share as it flows knowingly or unknowingly online in the creation of filter bubbles as well as in aiding surveillance.
The Role of Information in the Creation of Filter Bubbles
[edit | edit source]Google as a surveillance machine: surveillance of user’s data is vital to the way in which google operates, and under googles own policy guidelines they themselves can define how they process and utilise user data.Google works to create individualised filter bubbles whether a user is signed up or not, by recording information about our online activity specifically in cataloguing keywords. Google, by defining its privacy policies and user terms of service carry out a large-scale surveillance of users in order to create filter bubbles to flood a user with relevant advertising and thus for economic benefit. Issues of privacy over owns own personal content arise and in 2012 the EU data protection was proposed to protect the rights of users, it states that online users must consent to their data being used in order to create personalised filter bubbles, however again this consent only needs to be in the form of accepting users terms of service which many do mindlessly to begin with. [32]
And thus, though this can limit the creation of filter bubbles to some extent by reducing the information that google is able to store it would be near impossible to carry out completely.
Google as a Surveillance Machine
[edit | edit source]Google can only work as Google by surveilling user data in order to gather information about user interests and activities which will work to target advertising. Here, it is almost impossible for a user to maintain control over the content they share and still be able to engage with the internet. This applies to both passive users of Google, as well as those who decide to sign up for a google account.[33]. In signing up for a Gmail or Google+ account, google are able to monitor user activity, even collecting information about us from our friends. According to Google themselves, this is in an attempt to create a better and more individualised user experience on any google related site, there are issues over invasions of privacy as well the plain fact that the creation of filter bubbles allows targeted advertising and the commodification of users for Google’s financial benefit. In owning a Gmail account you are enabling Google to comb through everything we send and receive we are enabling Google to store our information in databases.[34].
Information Sharing on Social Medias
[edit | edit source]The NSA monitors our use of Google and Facebook.[35] Facebook can be considered as a threat to privacy if we take into the account the wealth of information that millions of facebook users upload and update about their own lives and the lives of their friends regularly online. The use of privacy settings on such social medias can give slight control and even more so an illusion of further control over the information we share online. Helen Nissenbaum argues that “the right to privacy is neither a right to secrecy nor a right to control but a right to appropriate flow of personal information.”[36] Utilisation of privacy settings on SNSs can allow a user, such as that as a Facebook user, to control the flow of the information that they allow online. However, these privacy settings are often not enough and are undermined by online surveillance done by corporations wishing to gain financial benefit from their users. Information gathering, as carried out by google and any site that uses cookies in order to give a “better experience” does so as a means which undermines privacy of a user unknowingly as well as gaining profit by creating filter bubbles which allow targeted advertising.
From Privacy to Surveillance
[edit | edit source]
Any person willing to engage in social media, any site powered by google or any site that functions with the uses of cookies and much more, will have information about them stored in databases, possibly monitored and even possibly used for surveillance. Privacy settings can provide some protection for a user who wishes to control the flow of their information to whomever they choose. However, these do not protect users from the investigatory powers of the corporations themselves, or in fact anyone who knows their way around these measures. Fuchs states that “In modern society, privacy is inherently linked to surveillance.” [37]. Our online visibility, for many, is something that we consider somewhat out of our own control if we consider especially what our friends and institutions may share about us online. However, this also goes deeper. The investigatory powers bill introduced in the UK [38] now also allows many credible organisations to view and comb through the search and internet history by forcing internet service providers to keep a log of sites visited by their users.Our information flows to companies often without us even realising and goes on to be stored, compromising privacy. Users are also unknowingly profiled with their stored data in the creation of filter bubbles, arguably an intrusion of privacy. There are ways around this such as deleting internet history or joining other services which promise an anonymous relationship, but for the vast majority of internet users their information already flows through the internet.
“In modern society, privacy is inherently linked to surveillance.”—Christian Fuchs, Social Media: A Critical Introduction
Different Data Trails lead to Different Experiences
[edit | edit source]Our experiences on the Internet are different varying on who we are and our personal interests. Through the function of filter bubbles explained previously, a person's experience on the internet influenced by their own agendas, can vary when looked upon a different user who will use the internet in a different way for different things. Each person's likes and dislike are exclusively unique. When looking at Raymond Williams Cultural determinism views, it is conveyed that his work was very centred around the basis of new media and the way in which it was used as a device and how it was controlled. Williams believed the true potential of new media could only be exploited by social norms and ideals that were already present in a culture- and therefore traditional power relations would be sustained and many of the same things a social group is used to being presented will continue to be reproduced and exist. [40] These ideas are relevant when focusing on 'data trails' and how different individuals' data trails lead to them experiencing different things while on the web.
Williams believes technology is political and people's views are influenced by set algorithms on different web pages and power relations in a society. [41] This is a down side to the power of "new media" and account for why many people are only being able to view a selected section of a mass of information available to them because of people in higher power having control over what is available to them to view based on their interests. Facebook founder Mark Zuckerberg, said Facebook's main function was to manage impressions and develop relationships with other people the way you would as if you were in a face to face conversation.[42] However critiques are worried about the invasion of privacy Facebook undertakes without full explanation and hence how it goes from encouraging people to share "Whats on their mind" to their close relations to a more Web 2.0 view point where posts and likes made my users help satisfy several cooperatives who benefit from a vast information overload of peoples interests for economic satisfaction in the form of advertisements.[43]
Worries over privacy on the internet have been on going with the knowledge of data trails. As the power of the internet continuously grows stronger, many fear that an individual's control over what they post and who sees it is beginning to weaken. The so called protective framework that runs on different online platforms to ensure some sort of privacy has been dismissed. This is because, many corporate and government executives have highlighted several problems in it suggesting that the concept of 'privacy' is non-existent these days. The suggest that the wealth of knowledge online now available in this modern society and the vast amount of benefits they receive comes at a cost- that cost being their personal information and data trails being easily accessible to different organisations. There are debates over whether privacy is a "moral or a legal right". [44] Morally it seems wrong and invasive that many organisations can access your personal data trails to use at their own disposal. However legally this can seem to benefit the user themselves by providing them with a more enjoyable experience online as a result of different organisations filtering things they know the user will like.
Despite being on their own private platform, at the end of the day an individual is still operating on a public platform in a political and public sphere. Therefore, this results in a conflict between what's public and private because the overall content being produced by an individual is on such a public domain. For example interacting with people on your social media in public and posting comments on Youtube is ways users of the internet interact publicly and therefore (maybe without willingly knowing), expose themselves and their data trails to be looked at by different people and organisations giving them an overall different online experience. [45]
Advertising and Monetisation: Filter Bubbles in Consumer Culture
[edit | edit source]Founder of Facebook, Mark Zuckerberg, is worth roughly $60 billion, yet the site he created over a decade ago is free for its users. Likewise, Twitter founder, Jack Dorsey is worth nearly $2 billion, but it costs you nothing to send a tweet. This is possible through the marketisation and monetisation of the products these men have created, to them every move of the mouse is an opportunity to make money.
Advertising
[edit | edit source]Advertising revenue is one of the main ways Social Media makes its money. Facebook reported massive revenue jumps in Q1 of 2016 by selling mobile ads, pushing its total revenue to $5.5bn from $3bn. Mobile ads counted for four fifths of this growth[46]. The reason for this is that they sell for more than desktop ads and that more people are seeing them. The Facebook app has been downloaded by over 85% of the smartphones over worldwide, an estimated active mobile audience at around 1.6 Billion[47]. This is not including the entire eco-system built into Facebook’s messenger application which launched in 2015. In terms of revenue, there is no better social media business model than Zuckerberg’s whose just advertisement segment reached a value of US$ 13,539 Million by Q3 2018 excluding the revenue from other segments like payments and other fees[48]

.
That’s not to say its younger cousin, Dorsey’s Twitter, is a slow mover. In fact, Twitter’s Q2 earnings for 2016 hit $610 million. While this was less than expected for the company, they too seem to be embracing the shift from desktop to mobile, particularly when it comes to video sharing and playback, looking to create what they call ‘premium viewing environments’[49]. Since this statement towards the end of 2016 there has been a spike of video sharing on Twitter, which is usually accompanied by a pre-video ad, especially in the case of sports’ or TV highlights. Businesses also see Twitter as a space to share their content, and if done correctly, the audience do most of the work for them. An example of this could be the immensely popular trailer for Netflix’s Stranger Things’ second season which garnered 150k retweets, with little effort from the show’s Twitter account. Likewise, the famous selfie of assorted stars at the Academy Awards in 2015, which was a guerrilla ad for Samsung’s Galaxy Note, got almost 4 million retweets. Social media advertising matters and companies are very aware of that.
Tech upstarts Snapchat have also branched into the world of big business, by incorporating advertising into their Discover tab. Snapchat does not have a desktop component to worry about, so all of the premium advertising space that they have to offer comes in the form of those aforementioned, expensive mobile ads. A thirty second ‘Brand Story’ will run a company $750,000 whereas a space on the discover page will cost closer to $250,000[50]. They now play between your friends’ stories and companies will pay huge sums of money to appear first on the Discover tab. One such company who seems to have a permanent slot here is the Daily Mail, who appear first almost every day. The aim of these companies is to gain a subscriber base by offering some free content that leads you towards the premium content they offer. Two who do this very well are Sky Sports and ESPN, who give highlights of football and basketball not long after the games have finished in the vast majority of cases.
While there is a definite perceived shift from desktop to mobile, there is not necessarily a need to kill off desktop advertising, or even cross platform advertising. This is something companies still use to their advantage frequently, sometimes without you even knowing.
Cookies
[edit | edit source]In short, apart from the delicious biscuits, a cookie can be defined as: A small text file (up to 4KB) created by a website that is stored in the user's computer either temporarily for that session only or permanently on the hard disk (persistent cookie). Cookies provide a way for the website to recognize you and keep track of your preferences.[51] Naturally, this is big business for the websites trying to sell advertising space, as they can tailor ads directly to the consumer, and as has been mentioned in previous sections of the Wikibook, created an online profile for users. This allows the likes of Facebook and Twitter to more effectively market the space on their desktop sites especially, and create individual ‘filter bubbles’ for specific users but instead of filling the bubble with content, it is filled with advertising.
Following a revision of the UK’s laws surrounding online consent, websites are now required to make it clear that they are using them and that by interacting with the site you are implying your consent to having them build a virtual profile of you[52]. This has been cleverly dealt with by the vast majority of websites, storing extra information with regards to ‘cookie policy’ away behind a few more clicks. Much like the terms and conditions of almost every online form, these are easily brushed over by users who would rather access a site’s content than wade through the quagmire of complex, legal jargon.

While there are arguments against cookies to be made from the stand points of online privacy and opportunistic advertising, from a flow of information point of view, they are a helpful resource. For example, while the idea of expanding our filter bubble may make sense when it comes to incorporating different points of view, or new things we have not tried before, from an advertising point of view that makes almost no sense. If we take Facebook as an example, it’s billion or so users are not going to all be interested in the same things, in fact there’s a huge chance that their only common interest may well be Facebook. Cookie software means these people do not see the same ads, but instead see a tailor-made set of adverts, specific to their likes and dislikes. If the advertising is going to exist, and it will, then there is little point in seeing things we are likely to have no interest in.
Premium Filter Bubbles
[edit | edit source]Another way that companies have found to utilise filter bubbles is through the production of premium content for users. Often these will have a free component to them, for example Spotify or YouTube, but will hide the best content or experience behind a pay-wall. News outlets have been doing this with varying degrees of success for a great number of years, fairly safe in the knowledge that the content they create is premium enough to warrant a fee, as it had done in print format hundreds of years before the internet even existed. For free sites, it was a leap in the dark to branch out into the world of premium content, but in some cases it has worked exceptionally.
YouTube Red
[edit | edit source]Here we will look at YouTube’s ‘YouTube Red’ premium program as a case study. Launching in 2014, YouTube Red is a premium service for YouTube users which exists within the free YouTube ecosystem. It allows users to watch YouTube videos ad free, save them for offline viewing, and creates original content in partnership with already successful YouTubers such as Casey Neistat. The platform, much like Netflix, has integrated these original series with a catalogue of films and TV shows available to view on demand. If we remember Twitter’s comments regarding premium video streaming content at the end of 2016, we can see just how ahead of the curve YouTube was, realising how to grow their already successful platform almost two years prior.

YouTube Red allows YouTube, or parent-company Google, to take the idea of filter bubbles to an even higher level than can be achieved by any free site. By paying their monthly subscription, people are already giving a deeper insight into their likes and dislikes than people accessing free content. There are millions of videos on YouTube, many of which aren’t worth the time it takes to load them, but you can’t complain if you paid nothing to watch grainy, mobile-phone footage of a concert or sporting event. YouTube Red puts more onus on the content creators to deliver to a paying audience. This gives a clear idea of what content users will be interested in, and therefore allows YouTube to commission more content in that mould.
Control Over What We See
[edit | edit source]Reality is a scarce resource[53]. An idea that the media uses the news to fabricate a reality for us.
Who is in Control?
[edit | edit source]To what extent are we, as users, in control over what we see online? Who is it that regulates content that we consume and connect with every day? Well it is fair to suggest that there is a lot of control over what we view online. The internet shapes our opinions of events, ideas and issues which are displayed and reported online and can be far from objective. Media platforms pick and choose what to show to the consumer. Media power can effectively control, to an extent, the minds of readers or viewer[54]. We give into an endless stream of suggested content that is specific to us that we become completely bias in our opinions and what we use on the internet. Not just social media but people's opinions create filter bubbles for us to influence our own.
Filter Bubbles
[edit | edit source]Filter bubbles are constantly controlling what we view online. We like pages that have bias opinions and are selective in their production of content to fit this bias. That is why we like them because they fit our own opinions and we like being reassured that someone else feels the same as we do. Filter bubbles the produce more of this bias content that fits our ideal and we are surrounded by it. It effectively isolates people in their own ideological reality. We become part of an opinion that expands and grows the power we give in to it. Advertisements are another way in which we are effectively distracted from mainstream content along with Google's algorithm which is specifically tailored to produce content that is specific to the individual.
The issue of filter bubbles has been recognised as a growing concern by internet giants such as Bill Gates and Mark Zuckerberg. In a recent interview, Gates points out that “Technology such as social media lets you go off with like-minded people, so you’re not mixing and sharing and understanding other points of view”. Zuckerberg (the CEO of Facebook) has mentioned filter bubbles as one of the most discussed concerns of the year in his 2017 manifesto ‘Building Global Community’. In this manifesto he highlights the risk of filter bubbles causing “sensationalism and polarization leading to a loss of common understanding” and makes it a goal to create an informed, inclusive community that will help people see a “more complete picture.”
Filter bubbles are not specific to social media and the internet but can be due to public opinion through lobbying, protesting and through activism.
'Existing research has suggested several means by which social media can influence collective action, such as providing mobilizing information and news not available in other media, facilitating the coordination of demonstrations, allowing users to join political causes, and creating opportunities to exchange opinions with other people'[55] 'Consumption of hard news, particularly newspaper and online news, has been found to be a consistent predictor of various forms of political participation'[56]
The Trump Campaign
[edit | edit source]During election time social media users were bombarded with video after video on Facebook and sometimes other platforms, each one highlighting a new flaw in Donald Trump’s campaign which included promises made and not kept, his derogative language, his lies and past career and painting him as a misogynist which worked to Hilary Clinton, his opponent’s, advantage. The internet played a huge role in showing the election to the world and provided a platform for discussion and opinion. However objective news reporting was cast aside and in many instances, newspapers had even turned away from the rule of objectivity, with writers using what Howard Portnoy, in his article describes as “snark”[57] to report on the campaign. Especially in well established newspapers like The New York Times, bias reporting can cause people to change their own views to suit what they believe to be the general consensus.

Facebook and Media Outlets
[edit | edit source]Facebook played a huge role in shaping people’s opinions on Donald Trump. So much so that people overlooked the many positive and negative of opposing candidate Hilary Clinton. Even though Trump was portrayed as ruthless and cruel he was victorious in his rise to Presidency. An example of how the internet forms our opinions and is partly to blame for its outcome. This idea is especially prevalent in countries that were outside of the US whose only insight into the election was through the internet. People were therefore held at the will of the internet which held all power in controlling people’s thoughts and opinions on the election. There is no doubt that the footage shown was real however media outlets such as Facebook twisted it and manipulated things with captions and clips cut together to give very strong messages to encourage people agree with them.
Alternatively, a lot of people blamed the press for Donald Trump's victory. This is a valid argument as people were bombarded with hundreds of news stories of Trump during the election making him better known among voters.
' No one wakes up on June 17 and randomly decides on their own that Donald Trump should be the Republican nominee for president. People’s minds change because they are hearing information that they haven’t heard before'[58]
It was this non-stop coverage that arguably boosted Trump into the lead. Even those who were not voting, from other counties etc could not get away from the news articles. It was Barack Obama that had used the internet greatly during his campaign when he ran for President and no one had seen this before. Donald Trump did the same during his campaign and it was obviously working to his advantage, therefore you could say that internet has much to account for in this sense.
Symbolic Power and News Stories
[edit | edit source]The news nowadays seems to exploit the notion of ‘power to the people’, often considered as positive, letting society voice their opinions, however this has been proven to go both ways for those under scrutiny.
'Everyone in a democracy is a certified media critic'
- Michael Schudson, News and Symbolic Power[59]
This supports the idea that the news and the media have right to give out this power to the public and that symbolic power should not be only given to journalists. It could be argued, however, that the media hold a lot of these powers themselves in that they pick and choose their content. If individuals can use their social media for entertainment and personal then, as Gil de Zúñiga, Jung, & Valenzuela put it: 'there is no reason to think that people who are motivated to follow public affairs will not use their accounts in, say, Facebook or Google Plus to consume hard news and public-oriented information'[60]
Meikle argues that symbolic power is used to those who have greater Symbolic Capital:
‘not everyone is able to exercise this power in the same kinds of way or with the same kinds of success’[61]
So does that mean that the more powerful you are, the more power you have over what content is created? It seems to be widely accepted that the biggest news platforms are considered the most reliable so it is those people in that power have the greatest influence over the consumers. It could be argued that a news article is not the event itself but a story of an event through the someone else's word choice, someone else's eyes. This highlights the idea that it is the journalists and content creators that decide what society receives and how they receive it. These stories are what people accept as truth and do not seem to question to what extent or realise that what they read or watch online is the truth written or produced by someone else and that person or group of people are the ones decided how you receive it.
Outside the Screen
[edit | edit source]Of course media and the internet have control over what we see, their influence doesn't just affect our lives on the internet but our lives in general. It controls what we see outside of our screens, controls how we look at things and our opinions. Media affects everything and we participate, involve and surround ourselves with it. It changes the outcomes of events and shapes us as people. News is too important to be left only to journalists[62]
Filter Bubbles And Data Mining
[edit | edit source]Anything and everything we look at online is monitored. Vast and powerful programs lurk behind the scenes, keeping track of everything we say and do on social media, shopping sites like Amazon, video hosting sites like YouTube, and even search engines. These algorithms use our past experiences to create advertisements we might be interested in based on terms searched, comments posted, links followed. Certain social sites even employ an algorithm that shows content pages similar to what we have seen in the past. This construction of patterns based on past data is called Data Mining, and it is used all over the net. Contrary to popular belief, data mining is not the extraction of data itself, but the extrapolation of strings of data in order to create patterns that relate to the person whose data is being mined. Advertising and most of the content on the rest of this page have much to do with data mining, and the creation of filter bubbles merely speeds up the extrapolation process. By only exposing oneself to certain pages and products on social media or online in general, the mining algorithms are able to feed the advertising algorithms a stream of data about what they think you’ll like to see next. “Personalization and customization of web content by the user is not a new trend, and has always presented an alluring, yet not an inherently democratizing, aspect of web use. It does, however, allow users to select and promote a personalized news feed.” [63]. Such personalization is all because of data mining and the trails of data every internet user leaves behind.
Filter Bubbles And Data Trails
[edit | edit source]
A filter bubble is generally defined as "the space created when algorithms dictate the content a user sees." Instead of getting the uninhibited experience, the user is shown content similar to what they have seen before. The way the content shown is decided upon is based on the user's data trails, which as stated earlier on this page are tracked by massively powerful algorithms. A very good example of how data trails effect what people see online is a story told by Eli Parisher. He asked two of his friends to Google "Egypt," and to inform him of the results. The two men took pictures of their search results and discovered that despite searching for the same term their results were very different. One man was shown story after story of the Arab Spring, while the other got no results about that at all. Mr. Parisher went on to say that a filter bubble "is your own personal, unique universe of information that you live in online. And what's in your filter bubble depends on who you are, and it depends on what you do. But the thing is that you don't decide what gets in. And more importantly, you don't actually see what gets edited out."[64]
Data Mining And Advertising
[edit | edit source]Data-trail-tracking algorithms are used not just for adjusting our Google search results, but for adjusting the sorts of advertisements we see around the net every day. These algorithms can alter the advertisements we are shown online even as we browse, causing just a few clicks to completely change what we see. As the Cookies section above states, a vast amount of websites use very small text files to keep track of our movements online and tailor our advertising based on what we prefer to look at. While the effects of Data-Mined advertising can be averted by deleting the cookies from a hard drive, as soon as the user logs back onto the internet they will begin leaving another data trail. This makes it very easy for algorithms to create and maintain Filter Bubbles through the use of Data Mining.
Glossary
[edit | edit source]- Algorithm: a process or a set of rules to be followed in calculations or other problem-solving situations. These tend to be very complex formula so often require a computer system to work them out.
- Citizen journalism: News stories and information being collected, analysed, posted and written by members of the general public, most commonly by the means of the internet.
- Civic Habits: The duties or actions that people in a country, city, town, or local area part-take in, in order to better the community.
- Data trails: An electronic record of the transactions or activities of a particular person, organization, etc. [65]
- Data Mining: The process by which algorithms extract knowledge and patterns from data trails and use them to create a profile of a person based on their digital footprint.
- Echo Chamber: An echo chamber is where ideas, beliefs and opinions are consistently reinforced, repeated and "echoed" within a designated space.
- Filter bubble: "A filter bubble is a result of a personalised search in which a website algorithm selectively guesses what information a user would like to see based on information about the user (such as location, past click behaviour and search history) and as a result, users become separated from information that disagrees with their viewpoints, effectively isolating them in their own cultural or ideological bubbles" [66]
- Gatekeeper: A gatekeeper is someone who controls what information gets through to the public.
- Lobbying:Attempts by individuals or private interest groups to influence government decision making.
- Newsfeed: In terms of social media, a newsfeed is the central interface where users post and share infortmation, photos, videos, ideas and news stories with each other.
- New Media: Means of mass communication using digital technologies such as the Internet. [67]
- Power Dynamics: The more powerful, the more persuasive. Those who hold power in the media especially have a great deal of power over those who consume it.
- Protesting: Media provides a source of information and opinion which creates platform for users to discuss and participate in. The content displayed by those with opinion creates a basis for argument.
- The Private Sphere: The private sphere is the complement or opposite to the public sphere. The private sphere is a certain sector of societal life in which an individual enjoys a degree of authority, unhampered by interventions from governmental or other institutions. Examples of the private sphere are family and home. [68]
- Social networks: a group of websites or applications which allow users to communicate with each other through posting information, comments, messages and images, etc
- "Snark": Slang Phrase using a combination of the words snide and remark.
- User-generated content: Any form of content such as blogs, wikis, discussion forums, posts, chats, tweets, podcasts, digital images, video, audio files, advertisements and other forms of media that is created by users of an online system or service, often made available via social media websites. User-generated_content
- Web 2.0: The second stage of development of the Internet, where there was a shift from static web pages to interactive, user-generated content accompanied by the growth of social media.
References
[edit | edit source]Evidence and Memory in Online Communications
[edit | edit source]Living in a Connected World/Evidence and Memory in Online Communications
Glossary
[edit | edit source]Please format in alphabetic order.
- Always-on
- A term relating to the notion of persistent connectivity to a shared global network.
- Artificial Intelligence
- The theory and development of computer systems able to perform tasks normally requiring human intelligence, such as visual perception, speech recognition, decision-making, and translation between languages.
- Authentication
- Where an entity is proved to be valid or a user provides information to prove their identity.
- Collective Intelligence
- A term to describe the sharing of knowledge and information in a collaborative for.
- Cultural Determinism
- The notion that the culture in which we are raised determines who we are at emotional and behavioral levels.
- Cyberbullying
- The use of electronic communication to bully a person, typically by sending messages of an intimidating or threatening nature.
- Data Mining
- The practice of sorting through data to identify patterns and establish relationships, in relation to online privacy, data mining collects data from users of social media to examine trends and target adverts.
- Deindividuation
- The loss of self-awareness in groups.
- Digital Age
- Also known as the information age that is considered to have started in 1970 with the development of technology such as television and computers.
- Digital Labour
- The term used to describe how corporate Internet platforms exploit user activity for profit.
- Digital Media
- A form of electronic media where data are stored in digital (as opposed to analog) form.
- Encrypted Messages
- Relating to Facebook's secret messaging service, encrypted messages allow end-to-end conversations to occur where only the communicating users can receive the messages.
- Filter Bubbles
- The use of algorithms to display information which appeals to the specific user's interests.
- Fear of Missing Out (FoMO)
- A form of anxiety aroused by the fact that an exciting or interesting event may currently be happening from posts on social media.
- Global Village
- Coined by Marshall McLuhan, a social organisation when society can easily transfer and share information as a collective.
- Hacking
- Unethical activity, which exploits weaknesses in computer security.
- Hive Mind
- A collective consciousness, analogous to the behaviour of social insects, in which a group of people become aware of their commonality and think and act as a community, sharing their knowledge, thoughts and resources.
- Such a group mentality characterised by uncritical conformity and loss of a sense of individuality and personal accountability.
- A distributed memory that both perceives and remembers.
- Identity theft
- The deliberate use of someone else's identity, usually as a method to gain a financial advantage or obtain credit and other benefits in the other person's name.
- Information Age
- The period beginning around 1970, in which large amounts of information are widely available to many people, largely through computers and computer newtorks.
- Information Overload
- Exposure to or provision of too much information or data.
- Internet cookies
- Small pieces of information in text format that are downloaded to your computer when you visit many Web sites. The cookie may come from the Web site itself or from the providers of the advertising banners or other graphics that make up a Web page.
- Keylogging
- The act of tracking what the user is typing.
- Leaks
- The public release and circulation of private information against the owner of the information’s will.
- Margin of error
- A statistic expressing the amount of random sampling error in a survey's results. It asserts a likelihood (not a certainty) that the result from a sample is close to the number one would get if the whole population had been queried
- Meta-aggregation
- A method of systematic review that mirrors the processes of a quantitative review whilst holding to the traditions and requirements of qualitative research (it aggregates findings into a combined whole that is more than the sum of the individual findings in a way that is analogous with meta-analysis).
- New Media
- The means of mass communication using digital technologies such as the Internet and social media platforms.
- Oversharing
- The act of revealing too much personal information about oneself online
- Privacy Policy
- A privacy policy is that which states the ways a company gathers, uses, discloses, and manages a customer or client's data. It fulfills a legal requirement to protect a customer or client's privacy.
- Private Sphere
- Often defined in opposition or parallel to the Public Sphere. The Private Sphere is a section of societal life in which an individual has a degree of seclusion from the public. The concept has become blurred since the advent of social networking as "private messaging" communications are often stored on databases.
- Public Sphere
- Often defined in opposition or parallel to the Private Sphere. The Public Sphere is the section of societal life where private individuals come together to form a public entity. The ideology of the Public Sphere is that private people come together to discuss matters involving the greater good of the public.
- Retweet
- A function on the social media platform Twitter that allows users to repost or forward a Tweet.
- Smart Mob
- A group whose coordination and communication abilities have been empowered by digital communication technologies.
- Social Media
- Websites and applications that enable users to create and share content or to participate in social networking.
- The collective of online communications channels dedicated to community-based input, interaction, content-sharing and collaboration (e.g. forums, microblogging, social networking, social bookmarking, social curation, and wikis).
- Social News
- A much more personalised form of news consumption, delivered on a central platform (like Facebook, Twitter, Reddit, etc.) according to how users engage with news stories from various sources.
- Spyware
- Software designed to give unauthorised access to a system.
- Surveillance
- The observation, and mass process of personal data. Although traditionally understood as being undertook by governments, private organistions are starting to proccess personal data on an industrial scale.
- Technological Determinism
- The notion that technology is a social structure or force, autonomous inventions, that have direct effects on social life
- Virtual Community
- A social network of individuals who interact through specific social media, potentially crossing geographical and political boundaries in order to pursue mutual interests or goals.
- Vlog
- A blog in which the postings are primarily in video form.
- Web 2.0
- The second stage of development of the Internet, characterised especially by the change from static web pages to dynamic or user-generated content and the growth of social media.
- Wiki
- A website or database developed collaboratively by a community of users, allowing any user to add and edit content.
- ↑ Chomsky, Noam & Herman, S., Edward, Manufacturing Consent: The Political Economy of The Mass Media - with a new introduction by the authors [Pantheon Books, New York 1988] (Introduction p.xvi)
- ↑ Chomsky, Noam & Herman, S., Edward, Manufacturing Consent: The Political Economy of The Mass Media - with a new introduction by the authors [Pantheon Books, New York 1988] (p.2)
- ↑ Pariser, Eli, The Filter Bubble: What the Internet is Hiding From You [Penguin Books, New York 2011]
- ↑ Chomsky, Noam & Herman, S., Edward, Manufacturing Consent: The Political Economy of The Mass Media - with a new introduction by the authors [Pantheon Books, New York 1988](pp.3-14)
- ↑ Ibid (pp.14-18)
- ↑ Ibid (pp.18-26)
- ↑ Ibid (pp.26-31)
- ↑ Ibid (pp.31-35)
- ↑ Adorno, Theodor, Minima Moralia: Reflections From Damaged Life [Verso Books Edition 2005] (pp.200-201)
- ↑ Pariser, Eli, The Filter Bubble: What the Internet is Hiding From You [Penguin Books, New York 2011] (Introduction)
- ↑ [42]
- ↑ [43])
- ↑ Ibid
- ↑ This idea is borrowed From Christopher Hitchens who memorably referred to Heaven as a "celestial North Korea[...] Who but a slave desires such a ghastly fate?". We have forwarded this here as "Digital North Korea".
- ↑ Pariser, Eli, The Filter Bubble: What the Internet is Hiding From You [Penguin Books, New York 2011] (Introduction)
- ↑ Ibid
- ↑ Papacharissi, A., Zizi. (2013). A private sphere. In Papacharissi (Ed.), A private sphere: Democracy in a digital age (1st ed., pp. 131). Hoboken, NJ: Wiley.
- ↑ Reuters Institute for the Study of Journalism, University of Oxford. (2016). Digital news report 2016. Retrieved from http://www.digitalnewsreport.org/
- ↑ Reuters Institute for the Study of Journalism, University of Oxford. (2016). Digital news report 2016. Retrieved from http://www.digitalnewsreport.org/
- ↑ https://www.wired.com/2016/11/filter-bubble-destroying-democracy/>
- ↑ (boyd, 2007, Harg, Hai, 2007 as cited in Papacharissi, A., Zizi. (2013). A private sphere. In Papacharissi (Ed.), A private sphere: Democracy in a digital age (1st ed., pp. 131). Hoboken, NJ: Wiley.)
- ↑ Papacharissi, A., Zizi. (2013). A private sphere. In Papacharissi (Ed.), A private sphere: Democracy in a digital age (1st ed., pp. 131). Hoboken, NJ: Wiley.
- ↑ Papacharissi, A., Zizi. (2013). A private sphere. In Papacharissi (Ed.), A private sphere: Democracy in a digital age (1st ed., pp. 131). Hoboken, NJ: Wiley.
- ↑ Adee, S. (2016). How can facebook and its users burst the ‘filter bubble’?. Retrieved from https://www.newscientist.com/article/2113246-how-can-facebook-and-its-users-burst-the-filter-bubble/
- ↑ Adee, S. (2016). How can facebook and its users burst the ‘filter bubble’?. Retrieved from https://www.newscientist.com/article/2113246-how-can-facebook-and-its-users-burst-the-filter-bubble/
- ↑ EL-BERMAW, M. M. (2016, Your filter bubble is destroying democracy. doi:11/08/2016 https://www.wired.com/2016/11/filter-bubble-destroying-democracy/
- ↑ Papacharissi, A., Zizi. (2013). A private sphere. In Papacharissi (Ed.), A private sphere: Democracy in a digital age (1st ed., pp. 131). Hoboken, NJ: Wiley.
- ↑ Rosen, J. (2006, JUNE 27, 2006). The people formerly known as the audience. Retrieved from http://archive.pressthink.org/2006/06/27/ppl_frmr.html
- ↑ Papacharissi, A., Zizi. (2013). A private sphere. In Papacharissi (Ed.), A private sphere: Democracy in a digital age (1st ed., pp. 131). Hoboken, NJ: Wiley.
- ↑ Papacharissi, A., Zizi. (2013). A private sphere. In Papacharissi (Ed.), A private sphere: Democracy in a digital age (1st ed., pp. 131). Hoboken, NJ: Wiley.
- ↑ Papacharissi, A., Zizi. (2013). A private sphere. In Papacharissi (Ed.), A private sphere: Democracy in a digital age (1st ed., pp. 131). Hoboken, NJ: Wiley.
- ↑ Fuchs, Christian (2013). accId=10153&cite=1&isbn=9781446296868&maxCopy=29&maxPrint=29&mmLimit=0¬es=1&pageLimit=0&shareLink=%2F%2FWWW.VLEBOOKS.COM%2FVLEWEB%2FPRODUCT%2FINDEX%2F388356&startPage=0×tamp=2017-03-06T20%3A40%3A30&userId=789293&watermark=++++++++++++++++++++++++++++++STIRLING%2FMMJZAZRQUE1CEWQ2CEXXUJFDZKVDRLY2RZDVPQ++++++++++++++++++++++++++++++&token=J5SNl6qAvTPcD1uIA7C5UZ95Fjo%3d Social Media: a critical introduction. Los Angeles,CA: SAGE. ISBN 9781446296868.
{{cite book}}: Check|url=value (help) - ↑ Fuchs, Christian (2013). Social Media: a critical introduction. Los Angeles,CA: SAGE. pp. 126–178. ISBN 9781446296868.
- ↑ https://www.youtube.com/watch?v=Va07q3HFEZQ&feature=youtu.be
- ↑ Fuchs, Christian (30 September 2015). "Surveillance and Critical Theory" (PDF). Media and Communication. 3 (2): 6–9. doi:10.17645/mac.v3i2.207.
- ↑ Fuchs, Christian (2013). Social Media: a critical introduction. Los Angeles,CA: SAGE. pp. 126–178. ISBN 9781446296868.
- ↑ Fuchs, Christian (2013). Social Media: a critical introduction. Los Angeles,CA: SAGE. p. 158. ISBN 9781446296868.
- ↑ http://www.independent.co.uk/life-style/gadgets-and-tech/news/investigatory-powers-bill-act-snoopers-charter-browsing-history-what-does-it-mean-a7436251.html
- ↑ Fuchs, Christian (2013). Social Media: a critical introduction. Los Angeles,CA: SAGE. ISBN 9781446296868.
- ↑ “New Media:determining or determined”—Jon Dovey, Seth Giddlings, Martin Lister, New Media: A Critical Introduction
- ↑ “New Media:determining or determined”—Jon Dovey, Seth Giddlings, Martin Lister, New Media: A Critical Introduction
- ↑ “Networks Without a Cause”—Geert Lovink, New Media: A Critique of Social Media
- ↑ “Networks Without a Cause”—Geert Lovink, New Media: A Critique of Social Media
- ↑ “Internet privacy concerns confirm the case for intervention”—Roger Clark, Magazine Communications of the ACM CACM Homepage archive Volume 42 Issue 2, Feb. 1999 Pages 60-67
- ↑ “A Private Sphere”—Zizi Papachrissi, Democracy in the Digital Age
- ↑ https://www.wsj.com/articles/facebook-revenue-soars-on-ad-growth-1461787856
- ↑ https://market.us/statistics/facebook/
- ↑ https://market.us/statistics/facebook/
- ↑ http://www.cnbc.com/2016/07/26/twitter-reporting-second-quarter-2016-earnings.html
- ↑ http://www.cnbc.com/2016/02/18/snapchats-ad-rates-drop-as-brands-find-problems.html
- ↑ http://www.pcmag.com/encyclopedia/term/40334/cookie
- ↑ https://ico.org.uk/for-organisations/guide-to-pecr/cookies-and-similar-technologies/
- ↑ Carey, James (1989) Communication as Culture, New York: Routledge
- ↑ Van Dijk, T. A. Power and the news media, University of Amseterdam
- ↑ Bennett, W. L., & Segerberg, A. (2011). Digital media and the personalization of collective action: Social technology and the organization of protests against the global economic crisis. Information, Communication & Society, 14, 770-799
- ↑ Norris, P. (2000). A virtuous circle: Political communications in postindustrial societies. Cambridge, UK: Cambridge University Press.
- ↑ http://libertyunyielding.com/2017/03/06/mainstream-megaliths-losing-sense-objectivity-writing-trump/
- ↑ Why is Trump surging? Blame the media. - The Washington Post
- ↑ Schudson, Michael News and Symbolic Power (1995, pp3)(https://dspace.stir.ac.uk/bitstream/1893/8781/1/Interpreting%20News%20Introduction.pdf
- ↑ Gil de Zúñiga, H., & Valenzuela, S. (2011). The mediating path to a stronger citizenship: Online and offline networks, weak ties, and civic engagement. Communication Research, 38, 397-421
- ↑ Meikle, G. (2008). Naming and shaming: News satire and symbolic power. Volume 18 Numbers 2, 3, & 4,
- ↑ Meikle, G. (2008). Naming and shaming: News satire and symbolic power. Volume 18 Numbers 2, 3, & 4,
- ↑ Papacharissi, A., Zizi. (2013). A private sphere. In Papacharissi (Ed.), A private sphere: Democracy in a digital age (1st ed., pp. 152). Hoboken, NJ: Wiley.
- ↑ Parisher, Eli. Beware online "filter bubbles". Ted Talk, 2011. Accessed at https://www.ted.com/talks/eli_pariser_beware_online_filter_bubbles/transcript?language=en
- ↑ https://en.oxforddictionaries.com/definition/data_trail
- ↑ Filter Bubble
- ↑ https://www.google.co.uk/webhp?sourceid=chrome-instant&ion=1&espv=2&ie=UTF-8#safe=active&q=new+media+meaning&*
- ↑ Private sphere