Directing Technology/Network
Networking in Schools
[edit | edit source]
Networking is simply the act of connecting multiple computers together for the purpose of sharing information. A network also connects computers to printers, servers, other hardware, and to the Internet. There are different types of computer networks, such as Wide Area Networks (WAN) and Metropolitan Area Networks (MAN), but the type that is commonly used in a school setting is a Local Area Network (LAN). The types of networks are different because of their size and their reach. A LAN is suited for computers in close proximity to one another. While a LAN is among the smallest types of computer network, it can easily accommodate thousands of computers. The proximity of the computers is what differs among the different types of networks. Most LANs are wired but schools also use wireless networks frequently in conjunction with a wired LAN.
A school's computer network controls many functions of a school - e-mail, storage of private and public files, Internet access, human resources records, payroll, and student grades, to name a few. Because of this, it is vitally important that a school network is set up correctly and according to the school district's needs. A technology director should assess the needs of the people using the school network before designing and implementing the network infrastructure.
There are advantages and disadvantages to using computer networking in a school environment. It allows schools to cut costs because software licenses can be shared. It gives staff and students a central location to store files that can be accessed from any computer on the network. Also, as mentioned above, a network makes it easier to manage staff login accounts and integrate them into all password protected areas (like e-mail) - an example of this is Active Directory. Some disadvantages include cost of network implementation and maintenance, and the need for experienced IT staff to manage the network. There is also the risk of hardware or software failure that could disrupt network access across the school district.
Networking Terminology
[edit | edit source]Cables
A networking cable is what connects the various types of hardware on a computer network. Many various types of cable can be used in a computer network, including unshielded twisted pair (UTP, commonly known as CAT5) or shielded twisted pair (STP) cable, coaxial cable, and fiber optic cable. However, as mentioned above, some computer networks have gone wireless and may use less cables than before.
Ethernet
Ethernet is the networking technology most commonly used for LANs. It connects the different parts of a computer network with twisted-pair (CAT5) cables, hubs and/or switches. Many computers currently are pre-configured to support Ethernet, where once it was required to purchase a network card to use the technology.[1]
IP Address
An IP address is a unique identifier for a node in a computer network that uses the Internet Protocol to communicate (IP stands for Internet Protocol). An IP address looks like this: 167.76.48.1. There are billions of possible IP address combinations.
MAC Address
A MAC address is assigned to a piece of network hardware when it is manufactured. It identifies network ports on a computer network, so a computer can have more than one MAC address if it has multiple network ports - for example, a wireless card and a port for an Ethernet cable will each have a MAC address. A MAC address is a 12-digit hexadecimal number and looks like this: 00:B0:C9:17:C3:27.
Node
A node is anything that is connected to a network - a computer, printer, server, modem, etc. On a LAN, every node has a MAC address, which is a unique number used to identify each node on a computer network.
Proxy Servers
A proxy server allows a network administrator to filter what goes in and out of the network; it is a go-between between different servers. One example is a web proxy server, which allows schools to keep students from accessing unauthorized or inappropriate Web sites.[2] View more information about proxies below
Routers
A network router connects multiple networks to one another. It allows the computers to share information with each other, as well as share connections to other peripherals, such as printers. Routers also connect the computer network to the Internet, via a cable modem, broadband modem, or another similar device. For wireless networks, a wireless router or a regular router with a wireless access point connected will connect the devices to the network.
Servers
A server is a specific computer (or multiple computers) on a network designed to handle the different functions of a network. Servers are usually equipped with extra memory and processing capabilities. Different types of servers include file servers, which store files and allow users to upload and download; web servers, which host Web site content and mail servers, to house a network's e-mail activity
Switches and Hubs
A network switch connects the computers in a network together. A hub is similar, but in a network of four or more computers, it does not perform as well as a switch and it uses more bandwidth, especially in busy networks. Because of this, switches are used more often. The reason for the difference is that hubs pass network traffic through all of the computers connected to it, while switches are able to selectively route the traffic where it needs to go. Also, when there are many computers in a network, switches can be connected to each other if needed.
Wireless
A wireless network allows nodes to connect to the network without using cables. The node needs to be equipped with a wireless network card, and the network needs to have wireless routers. Wi-Fi is a widely used wireless network that allows people to connect to the Internet. One disadvantage of a wireless network is that the connection speed is slower than a wired network. However, it allows for easier expansion of the network using laptops and other wireless-enabled devices.
Network Configurations
[edit | edit source]
The configuration of a computer network is referred to as topology. It is the arrangement of the nodes in the network and how they are connected. Different types of network topology include bus, star, tree, line, mesh, and ring. They are depicted in the diagram at the right, and described below:
Bus
A bus topology is set up in a linear configuration, where all nodes are laid out in a line and are connected to a singular "backbone" cable. A failure in the backbone cable will bring down the whole network.
Star
A network using the star topology has a central hub to which all of the nodes are connected. It physically resembles the spokes of a bicycle tire. All of the nodes send their data to the central hub, but the nodes are not connected to each other, so if one node fails the others will not be affected. This topology is easy to set up, but requires more cable than the other configurations.
Tree
A tree topology configures the network in a hierarchy; combining characteristics of the bus and star topologies. One backbone cable (the top level of the hierarchy) connects multiple groups of nodes (the second level of the hierarchy). Each group of nodes is then arranged in a star topology configuration. This topology allows for more nodes to be added easily. But as in the bus topology, if the backbone cable fails, the whole network will go down.
Line
When a network is configured with the line topology, nodes are connected to each other as depicted in the diagram - a line of nodes connected to their two neighbors, with a node at each end only connected to one other node.
Mesh
A full mesh network has nodes that all connect to each other, so data can pass through the network in many ways. A partial mesh network may have some nodes that do not connect to others. It is a complex setup and may only be desired for small networks.
Ring
In a ring topology network configuration, each node is connected to two other nodes. The data sent from each node travels in a circular manner through the nodes, and any problems with a single node can bring down the whole network.
These topologies can be combined to create more complex networks.[3][4][5]
Monitoring Your Network
[edit | edit source]It is crucial to constantly monitor network activity to discover problems such as slow connections, outages, or security issues. Things to monitor include connection and response times across the network, availability of nodes/routers/switches/etc., or a successful test of a Web server or e-mail server.
A network can be monitored in many ways. A low-tech idea would be to manually time different network functions, such as how long it takes to open a document stored on the network. For large networks, many operating systems have built-in monitoring software. There are also many tools that can be purchased to monitor a network and notify the network administrator of any issues. MonitorTools.com is an example of a Web site that lists many of the different options for network monitoring tools. A tool should be chosen only after the monitoring needs of a network are identified by network administrators or other IT professionals or administrators in the school district.
When a tool is in place for network monitoring, a network administrator must then review performance logs generated by the monitoring software to identify any problems. Performance logs can be scheduled to run at any time of day and should be run at different times during the day to identify busy network times.[6]
For more information about network monitoring, maintenance, and backup, visit the Maintaining Technology section of this Wikibook.
Firewall
[edit | edit source]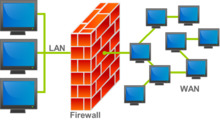
A network firewall is a system or a device that is designed to limit, control or prevent access to a network connection. A firewall is the first device that is encountered when the connection is made from outside of a network that firewall resides on. It is the last device that is being encountered when the connection is made from the inside the network that the firewall is located in. A firewall filters, enables, denies, encrypts, decrypts, or proxy all incoming our outgoing network traffic. The technology director will be responsible for purchasing or upgrading to an appropriate hardware of software that will operate the firewall. He will collaborate with a network administrator for installing and overseeing the functionality of the system. A firewall must be a solid and proven system that will withstand a high volume traffic, process and log the IP information, block and secure possible DDoS (Distributed Denial of Service) attacks. For more information about Firewall consider the following resources.
Wikipedia - [7]
HowStuffWorks - [8]
Barracudanetworks -[9]
Firewall Ports
A firewall typically operates by restricting TCP and UDP ports. For example a firewall may be set up let any communication ports to be transmitted to a specific IP address. This is called a DMZ (Demilitarized Zone)[10]forward. Instead of exposing entire network to incoming port requests, a DMZ is set up to establish connections directly with designated IP. A firewall is typically set up to allow requests through port 80. Port 80 is a default port for web service such as HTTP protocol. Below is the sample table listing of some other common protocol ports.
| Port | Description | Status |
|---|---|---|
| 20/TCP | FTP - data | Official |
| 21/TCP | FTP—control (command) | Official |
| 22/TCP,UDP | Secure Shell (SSH)—used for secure logins, file transfers (scp, sftp) and port forwarding | Official |
| 23/TCP | Telnet protocol—unencrypted text communications | Official |
| 25/TCP | Simple Mail Transfer Protocol (SMTP)—used for e-mail routing between mail servers | Official |
| 80/TCP,UDP | Hypertext Transfer Protocol (HTTP) | Official |
For a more comprehensive list of Firewall ports, visit the Wikipedia Port Table Listings.[11]
Firewall Structure
Hardware
There has been a long controversy of the software vs hardware firewall effectiveness. Most of the hardware firewalls provide a strong security protection from the Internet and require a minimal configuration or set up. A hardware firewall is a device that attaches between the incoming internet connection and the router that computers are connected to. It acts like a guard at the gate, checking every bit of data coming and going. If an unauthorized user or restricted type of data attempts to enter or exit the network, it is blocked. [12]A hardware firewall then controls the flow of network by packet filtering. A packet filtering is also referred to as static packet filtering. It controls access to a network by analyzing the incoming and outgoing packets and letting them pass or halting them based on the IP addresses of the source and destination. Packet filtering is one technique, among many, for implementing security firewalls.[13] A hardware firewall was originally designed for use on large corporate networks, hardware firewalls are made for networks of all types and sizes now. Large hardware firewalls designed for big business use can cost thousands of dollars, but many good hardware firewall products designed especially for home and small office use are very affordable.
Software
A software firewall, also known as a personal firewall, is a program that is installed on your computer. It protects only the computer it is installed on, so if a software firewall is the only type of firewall used on a network, each computer must have a personal firewall installed. There are many good software firewall products available, and all are reasonably priced for the degree of protection they provide. Some include the following:
Avanquest ZoneAlarm Pro 2006 - [14]
PC Cillin - [15]
Sygate Personal Firewall - [16]
Armor2net Personal Firewall - [17]
Sunbelt Personal Firewall - [18]
AVG - [19]
Anti-Malware
[edit | edit source]An antivirus is a software used to prevent, detect, and remove malware, including computer viruses, worms, and Trojan horses. Such programs may also prevent and remove adware, spyware, and other forms of malware.[20] The increasing demand on security and protection of personal computers has led to a massive development of antivirus software protection. Today there are hundreds of antivirus software manufactured. The most popular list includes:
- Norton Internet Security
- McAfee VirusScan
- AVG AntiVirus
- Avast Antivirus
- ESET NOD32
- Malwarebytes
- Panda Cloud Antivirus
- Microsoft Defender
There are no best and worst virus detection programs. It may depend on the network infrastructure or the size of business to choose appropriate virus protection. All products provide excellent detection and removal of malware infections. Some include a WebGuard add-on to protect against malicious or compromised websites, some include scanners that provide the ability to make an antivirus rescue CD for your system, some may include a real time scanning of computers and provide real time protection of email, Web browsing and so on.
Physical Security
[edit | edit source]
Restricted Access
Because of the high importance and valuable networking equipment in a control room, -- a restrictive access is installed. Only authorized people will have physical access to network systems. Why would a network control room be so important you might ask? Well, devices such as computers are unavoidably vulnerable to physical attack. Routers allow their passwords to be reset, server software-based security can be easily bypassed, and user passwords can be cracked and stolen. All of this is possible with a reasonable amount of physical access to the system. Therefore usually a password combination lock or card swipe access is the best solution. Only the technology director and selective IT staff such as network administrator would be allowed to access this room. Very commonly network administrator would perform a backup or copying of the sensitive data in the network room. Sometimes those who are gaining access to a system are just curious employees who want to learn more about the systems or perhaps play with some settings to see if they can allow themselves a greater ability to control their PCs. The room itself or outside may be monitored to ensure security of valuable equipment. [21]
Proxies
[edit | edit source]
A proxy is a bridge between a client and a server. A proxy takes incoming packets and reconfigures them in a requested manner governed by the set of filter policies. These set of policies can include file requests, web access, e-mail and so on. A proxy's main purpose is to allow accessibility to inaccessible (blocked or denied by a firewall) services. Its goal is to bypass the set rules and provide successful connection from the client to the server. A proxy can also provide anonymous connection to the server by hiding the true IP address of the client. For example if a client requests a connection with a specific server by using proxy, the only IP that is visible is the proxy's IP not the client's.
Caching proxy
[edit | edit source]A caching proxy is a server that collects requested data from servers and stores it for later requests. Most of the time the data collected is the most frequent accessed information. For example this information might include frequently accessed files that are large in size. The purpose of caching proxy is to eliminate the wait time and reduce stress on the bandwidth traffic. Common installations of a caching proxy are included with major ISP's, large corporations and search engines.
Web proxy
[edit | edit source]A web proxy is a server that provides filtering for World Wide Web services. The most common use of a web proxy is to enable access to denied services. Some public schools and corporations may deny access to selected web services. Sometimes it is possible to bypass these rules by using a web proxy that will fully enable access to those services.
Anonymizing proxy
[edit | edit source]An anonymizing proxy is a server that hides or disguises a client's IP with an IP of that proxy server. Its purpose is to provide cyber security and protect a client from being seen online. However the information that is transmitted to the server is not hidden to the proxy server. Thus a set of policies and rules may exist between a client and a proxy that will provide assurance of true anonymous identity.
Sources
[edit | edit source]- http://en.wikipedia.org/wiki/Firewall_(networking)
- http://en.wikipedia.org/wiki/Computer_network
- http://networkbits.net/lan-components/local-area-network-lan-basic-components/
- http://compnetworking.about.com/
- http://fcit.usf.edu/network/
- ↑ http://en.wikipedia.org/wiki/Ethernet
- ↑ http://en.wikipedia.org/wiki/Proxy_server
- ↑ http://en.wikipedia.org/wiki/Network_topology
- ↑ http://www.edrawsoft.com/Network-Topologies.php
- ↑ http://compnetworking.about.com/od/networkdesign/a/topologies.htm
- ↑ Lowe, D. (2007). Networking for Dummies. Hoboken, NJ: Wiley Publishing.
- ↑ http://en.wikipedia.org/wiki/Firewall_(networking)
- ↑ http://www.howstuffworks.com/firewall.htm
- ↑ http://www.howstuffworks.com/firewall.htm>
- ↑ http://en.wikipedia.org/wiki/Demilitarized_zone_(computing)
- ↑ http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
- ↑ http://www.antivirus-firewall-spyware.com/firewalls.html
- ↑ http://www.webopedia.com/TERM/P/packet_filtering.html
- ↑ http://www.avanquest.com
- ↑ http://www.pccillinsecurity.com
- ↑ http://www.symantec.com/norton/sygate/index.jsp
- ↑ http://www.armor2net.com/
- ↑ http://www.sunbeltsoftware.com/home-home-office/sunbelt-personal-firewall/
- ↑ http://www.avg.com
- ↑ http://en.wikipedia.org/wiki/Antivirus_software
- ↑ http://archive.is/20130102123047/http://articles.techrepublic.com.com/5100-10878_11-5054057.html