Information Technology and Ethics/Cyber-Crimes
Overview of Cybercrime
[edit | edit source]Computer and internet crime refers to criminal activities carried out using digital technologies. These crimes exploit vulnerabilities in computer systems and internet infrastructure. Cybercriminals usually target businesses with the primary goal of making money, but they can also target individuals with the goals of extortion and blackmailing, as well as governments for geopolitical objectives, including espionage and sabotage. [1]
Cybercrime aims at targeting the fundamental principles of the CIA triad: confidentiality, integrity, and availability of computer systems. The first principle, confidentiality, refers to the protection of sensitive information from unauthorized access. Cybercriminals target confidentiality by illegally accessing data, such as personal information, through hacking or phishing.
Integrity, the second pillar, revolves around ensuring that data remains accurate, consistent, and reliable. Cybercriminals compromise integrity by tampering with data to cause data corruption or system malfunctions.
Lastly, accessibility ensures that unauthorized users can access data and systems when needed. Cybercriminals disrupt accessibility by launching denial-of-service attacks or other forms of system interference to prevent legitimate users from accessing essential services or resources. [2]
The modern history of cybercrime traces back to the pivotal events in the 1960s and 1980s.
In 1962, Allen Scherr launched a cyber attack against MIT computer networks. He used a punch card to steal passwords from the database. Scherr then shared these passwords with friends, which led to unauthorized access.
In 1981, Ian Murphy hacked the AT&T phone system by altering its internal clocks to charge daytime calls at night time rates. This cybercrime act, known as “phreaking”, led to Murphy’s first hacking conviction. He then was known as the first person to be charged with a cybercrime. [3]
Building upon the exploits of figures such as Allen Scherr and Ian Murphy, cybercriminals have continued to exploit vulnerabilities in computer systems for personal gain or malicious intent. [4]
Over the years, and as technology developed, cybercriminals have improved their methods by using new technologies and taking advantage of trends to commit illegal acts. They started spreading malware and phishing scams, carrying out cyber espionage, and launching ransomware attacks. As a result, cybercrime has become more intricate.
As we rely more on digital technology for communication and business, cybercrime’s effects are increasing. This creates significant challenges for individuals, businesses and governments. Therefore, a multifaceted approach is needed to mitigate these risks, including education, awareness, robust security measures, and effective law enforcement. [5]
Categories of Cybercrime
[edit | edit source]Cybercrimes can be categorized into the following:
- Cybercrime against the people: these are attacks against human personality, For instance kidnapping, cyberharassment, extortion, credit card theft, romance scam, phishing, cyber bullying, identity theft and cyberstalking are all in this category.
- Cybercrime against the government/organization: these are attacks against the government or organization. For instance, network intrusion, phishing, cyber terrorism, an act of war, or software piracy, are grouped in this category.
- Cybercrime against property: these are attacks against individual properties, Denial of Service (DOS) and Distributed Denial of Service (DDOS), copyright, and intellectual property right (IPR) are grouped in this category.
Cyber Laws and Regulations
[edit | edit source]In the United States, a variety of federal laws have been established to combat and govern cybercrime and related digital activities. These laws span from dealing with hacking and digital fraud to tackling online harassment and theft of intellectual property. Notable statutes include:
Computer Fraud and Abuse Act (CFAA) (18 U.S.C. § 1030) [6]
[edit | edit source]Introduced in 1986 to amend existing computer fraud legislation, the CFAA initially targeted hacking and was later expanded to cover a wider array of activities. It outlaws accessing a computer without or beyond authorization, though its broad definition of unauthorized access has raised concerns about its potential to overly criminalize common online behaviors.
Identity Theft and Assumption Deterrence Act (18 U.S.C. § 1028) [7]
[edit | edit source]This 1998 Act prohibits the misuse of someone else's identification details, such as Social Security and credit card numbers, among others. It was amended in 2004 to include aggravated identity theft, applying to the use of another's identity in committing certain federal crimes or acts of terrorism.
Digital Millennium Copyright Act (DMCA) [8]
[edit | edit source]Passed in 1998, the DMCA updates U.S. copyright laws for the digital age, protecting online service providers from liability for copyright infringement by users, while safeguarding copyright holders against unauthorized access and misuse of their works online.
Child Online Privacy Protection Act (COPPA) [9]
[edit | edit source]COPPA safeguards children's online privacy under 13 by mandating websites to outline their data collection practices, obtain verifiable parental consent before collecting data from children, allow parents to opt-out, and maintain the security of the collected data.
International Cyber Law Initiatives
[edit | edit source]The regulation of cyber activities extends beyond U.S. borders, with international treaties and conventions aiming for global cooperation against cybercrime. Key international frameworks include:
- The Budapest Convention on Cybercrime: A pivotal treaty by the Council of Europe, opened in 2001 to both European and non-European states, facilitating international collaboration in combating cybercrime.[10]
- African Union Convention on Cybersecurity and Personal Data Protection: Adopted in 2014, this Convention seeks to boost cybersecurity and data protection across Africa through inter-state cooperation.[11]
- Commonwealth Model Law on Computer and Computer-Related Crime: Drafted by the Commonwealth Secretariat, this Model Law serves as a template for member states to align their cybercrime legislation.[12][13]
- Organization of American States (OAS) Cybercrime Convention: Although not a binding treaty, the OAS framework promotes collaborative efforts to tackle cybercrime in the Americas.[14]
These laws and international agreements reflect the evolving landscape of cyber legislation, aiming to address the complex challenges posed by digital technology and cybercrime.
Types of Cybercrime
[edit | edit source]Crime has evolved with the advancements of the internet and social media. The parallel between technology and the types of crimes that are committed is astonishing. As technology became more readily available to the masses, the types of crimes committed shifted over time. A clear distinction has been formed based on the involvement of cybertechnology in crime. Crimes that would not exist or be possible without the existence of cybertechnology are true Cybercrimes. To be most accurate, these crimes can be classified as cyberspecific crimes. Crimes that can be committed that do not necessarily need cybertechnology to be possible, but are made easier by its existence, are known as cyber-related crimes. Of Cyber-related crimes, there are two distinct categories that can be identified. The first are Cyber-assisted crimes. These are crimes in which cybertechnology is simply used to aid a crime, such as committing tax fraud or being assaulted with a computer. The other category is known as Cyberexacerbated crimes, which are crimes that have increased significantly due to cybertechnology. [15]
Cyber-assisted Crimes
[edit | edit source]Cyber-assisted crime entails any crime where cyberspace or computing technology is used, but only plays a non-critical supporting role. Put simply, these are essentially normal crimes that have occurred throughout time on a regular basis. Income tax cheating is one example of a cyber assisted crime. While the actual crime involves improper tax filings and has traditionally been done ‘offline’; however, with the widespread availability of computing devices, criminals have begun using these computing devices to facilitate their illegal actions
The most common type of cyber-assisted crime that you will see is fraud. Fraud typically is a crime that does not require much thought to actually commit. As a crime, it has always been relatively easy to commit. With the use of cybertechnology, it only becomes much easier to actually carry out from start to finish.
Cyberexacerbated Crimes
[edit | edit source]Cyber-exacerbated crimes are crimes in which the actual offense does not occur in cyberspace. Rather, these crimes were made easier, or enabled, by cyberspace and tend to have a larger impact than if limited to the physical world. For instance, there are numerous cases of stalkers tracking their victims using cyberspace. The actual crime, in this case the stalking and harassment, occurs in the real world. The activities performed in cyberspace, though, certainly assist and exacerbate these crimes like never before. Cyberbullying, internet pedophilia and pornography may involve cyber technologies; however, the fundamental crimes themselves can be performed in the physical realm. However, these crimes have increased significantly due to adoption of cybertechnology. Most crimes have evolved to maintain their own categories due to the sheer volume of crimes and their slight uniqueness due to their ease with the use of cybertechnology.
Cyberspecific Crimes
[edit | edit source]Cyberspecific crimes don’t exist without the internet as we know it. Because of that, these are the most unique cybercrimes and could be considered as the only “true” cybercrimes. Cybertrespassing is one of these crimes. At its core, cybertrespassing takes its roots from actual trespassing. Essentially, perpetrators gain access to stores of information that they otherwise should not have access to because of the lack of permissions. The reason why this is so dangerous is because it opens the door for cybertrespassing to easily become a data breach if information is taken.
Cybervandalism is another form cyberspecific crime. Taking its roots from actual vandalism, cybervandalism began harmlessly with the defacing of websites on the internet. While annoying, it didn’t necessarily present any damage. It wasn’t until cyberattacks with the intent of harming computers were created that cybervandalism became a huge issue.
Types of Cyber Criminals
[edit | edit source]Who are cyber criminals?
[edit | edit source]Cybercriminals are people who use technology to perform activities that involve attacking a network or digital system to illegally obtain private information belonging to a company or individual. The intent set by a cybercriminal is financial gain. There are many different types of cyber criminals. Cybercriminals could be a group of people working as a team or an individual who commit unlawful cyber crimes. Contrary to popular belief, not all hackers are cybercriminals. The term “hacking” does leave the impression that illegal activity is involved. Because of this, many people think that all hackers are criminals, which is not the case. There are two general types of hackers: good hackers and malicious hackers. Good hackers, such as Ethical Hackers, work with originations in order to detect vulnerabilities that exist in their systems and improve their protection. Good hackers are considered White Hat hackers. Malicious hackers are individuals who hack or break into a computer or other digital devices without any permission from the owner with the intent to cause harm. Malicious hackers are considered Black Hat hackers. The following outlines many different types of cybercriminals and their roles.
Black Hat
[edit | edit source]Cybercriminals are people who use technology to perform activities that involve attacking a network or digital system to illegally obtain private information belonging to a company or individual. The intent set by a cybercriminal is financial gain. There are many different types of cyber criminals. Cybercriminals could be a group of people working as a team or an individual who commit unlawful cyber crimes. Contrary to popular belief, not all hackers are cybercriminals. The term “hacking” does leave the impression that illegal activity is involved. Because of this, many people think that all hackers are criminals, which is not the case. There are two general types of hackers: good hackers and malicious hackers. Good hackers, such as Ethical Hackers, work with originations in order to detect vulnerabilities that exist in their systems and improve their protection. Good hackers are considered White Hat hackers. Malicious hackers are individuals who hack or break into a computer or other digital devices without any permission from the owner with the intent to cause harm. Malicious hackers are considered Black Hat hackers. The following outlines many different types of cybercriminals and their roles.
Identity Thieves
[edit | edit source]Identity thieves are individuals or groups of people who steal personal information such as addresses, phone numbers, social security numbers, and credit card numbers. Identity thieves use the stolen data to impersonate their victims and in turn receive financial gain. Identity thieves have been identified as one of the oldest cybercriminals [16].
Cyber Terrorism
[edit | edit source]According to Google, cyber terrorism is defined as “the politically motivated use of computers and information technology to cause severe disruption or widespread fear in society”. Cyber Terrorism is a form of a cyberattack, developed for political reasons, in order to steal or/and corrupt government or corporate computers and network data. Cyber terrorists are responsible for cyber terrorism attacks. Cyber terrorism attacks could cause damage to businesses, countries, and organizations. A fundamental difference between a cyber-attack and cyber terrorism is that cyber terrorism is politically supported, whereas, a cyber-attack is performed by a group of people who are looking to gain money illegally by stealing confidential information [16].
Internet Stalkers
[edit | edit source]Internet Stalkers are cybercriminals who monitor their victims’ activities on the internet. By keeping track of their victim’s habits, they are able to terrorize and/or acquire personal information from their victims. This kind of cybercriminal heavily utilizes social networking platforms and malware to perform their attacks. There are many different reasons for doing this kind of cybercrime, however, the main two reasons internet stalkers perform their attacks are for bribery or slander, and sometimes both [16].
Script kiddies
[edit | edit source]These kinds of hackers can be anyone who is encouraged by the urge of immaturity to become a wannabe hacker. They have less technical knowledge and urge to run the scripts which have been pre-compiled so that there will be disturbances in the software. [17]They lack the technical expertise to even understand what the software was meant to work for which lets them hack the systems which are very weakly secured.
Scammers
[edit | edit source]These are the daily scamming emails that we come across. Whenever we have to login to our email inbox we receive probably more emails from the scammers which offer different proposals for discounted trips or medicines, timeshares or personal ads.
Spammers
[edit | edit source]They are not direct criminals but commit the crime of wasting one's time. Spammers flood the email inbox with ads and everything gibberish possible. They are not dangerous in any particular way but they are always considered to be annoying and time-consuming. [17]Spammers are even responsible for bringing in a real financial cost by bringing in the necessity to install expensive and unstable anti-spam technologies.
Hacker activist groups
[edit | edit source]They are often called as the 'Hacktivists'. They can be considered as petty criminals who always are on the try to prove their destructive behavior wherein they steal confidential information and release it publicly. They generally work anonymously and are responsible for creating tools that makes the hacking easier.[17]
Phishers
[edit | edit source]The most prominent example of such activities are when we receive notification about our account expiring and where we have to update our information. This is not really the case. It's all the activities of the phisher to extract personal information or the identity. There has been survey about this which says that there are around 20,000 to 30,000 phishing websites found every month.
Political/Religious/Commercial groups
[edit | edit source]These groups can be categorized into the ones which do not aim at financial gain. They generally aim at developing malware for political success. One of the finest examples of such a malware is Stuxnet! This malware was found in Iran’s atomic program but it was believed to be originated from some foreign government.[17] These can not be thought as harmless as they can have losses on the political, religion or commercial level.
Professional Cybercriminals
[edit | edit source]These kind of people are the most dangerous ones as they have the proper technical expertise and know what they want to harm and how to harm. These are a group which can consist of technologists who have turned themselves into cybercriminals. They do the most damage to government, financial institutions or e-commerce businesses. They can be responsible for the most number of crimes than the rest combined.
Examples of Cybercrime
[edit | edit source]Fore each of the above types of cyber crime there are a number of pertinent examples of cybercrime that should be mentioned, as follows:
Cyber-assisted Crimes
[edit | edit source]Cyber-assisted crimes can be some of the scariest once experienced in the real world, and some people have already seen them in action. For example, back in 2015, it was reported that a german steel mill was compromised in a cyber-attack which resulted in destruction and severe physical damage to industrial equipment. The hackers were able to escalate privileges using a simple phishing attack that they carried out against the company’s employees. It was also reported that this was not the only cyber-assisted crime of this nature. In 2008, the well known US and Israel cyber weapon, Stuxnet, have already carried out attacks against Iranian’s uranium enrichment plants to sabotage centrifuge operations. Although this last one might not be an actual cyber-crime, it is still a cyber-assisted operation because cyber tools were used in order to affect or control physical equipment.[18]
Cyberstalking
[edit | edit source]Cyberstalking is the practice of stalking or harassing someone over the internet. It can be directed towards individuals, groups, or even organizations, and can include slander, defamation, and threats. The goal could be to control or threaten the victim, or to obtain information for other crimes such as identity theft or online stalking. Cyberstalkers may scare their victims by sending them negative messages on a regular basis, possibly many times a day. It's even more unsettling when the messages come from multiple accounts controlled by the same person. It typically includes explicit or implied physical threats, instilling fear in the victim and potentially leading to stalking and aggressive action in the real world.[19]
Cyberstalking isn't limited to the wealthy and well-known. According to a 2014 Pew Research Center survey (Duggan, 2014), 18% of those interviewed said they had watched someone being stalked, while 8% said they had been stalked themselves. It was also observed that women are more likely than men to be the victims of cyberstalking or online sexual harassment. Women between the ages of 18 and 24 reported a disproportionately high number of incidents, with 26% having been cyberstalked and 25% having been sexually harassed.[20] This isn't to say that men aren't affected by this type of behavior. According to the report, 7% of men between the ages of 18 and 24 have been stalked online, and 13% have been sexually harassed.
Revenge pornography
[edit | edit source]In the age of the Internet, there is a new and dangerous development, a nasty and potent offspring of the chaos. This is what is known as "revenge porn."Revenge porn is one of the most evil features of the Internet. Invasion of privacy on the Internet is inexpensive for the intruder, quick, damaging to a large number of people, and practically impossible to stop.This term has a wide range of meanings; in general, it refers to sexually explicit or naked images or films of a person that have been broadcast or circulated online without his or her consent and have a high risk of causing harm. The name "revenge" stems from the context: former partners frequently publish photographs or films to humiliate, degrade, or ridicule an ex-lover. Not only images, but also identifying information about the victim, such as his or her name, address, and social media profiles, is aired in the most horrible way possible. Websites dedicated to exchange such photographs and information were formed particularly to make revenge porn possible.
Revenge porn's ramifications differ from victim to victim and can be severe. When a victim comes upon the content, it has almost definitely already been shared by a huge number of others. Aside from the obvious humiliation, victims have described extreme emotional distress, social impairment, and suicidal ideation, with some even committing suicide. Victims often claim that others who have seen their nonconsensual pornography online have threatened them with violence and stalked or tormented them. Victims have reportedly claimed to have lost their jobs, been expelled from school, and had their names changed.
The COVID-19 pandemic outbreak appears to have exacerbated the problem. Experts in this field in the United States have reported an "onslaught" of persons seeking their assistance, saying that the "environment is ripe for digital abuse." When it comes to nonconsensual porn, New York Attorney General Eric Schneiderman has declared that the COVID-19 pandemic poses a significant threat to the state's residents, citing a 70% increase in the number of messages posted on dating apps.[21]
According to research, victims of nonconsensual pornography suffer from similar suffering to survivors of sexual assault. Meanwhile, Section 230 of the Communications Decency Act of 1996 shields message boards and other platforms that are regularly used to distribute revenge porn from legal liability for information posted by users. Victims are left with their entire trauma, which abusers are fully aware of."[22]
Young women are the most frequently targeted, with 90 percent of nonconsensual pornography victims being female, according to the Cyber Civil Rights Initiative.
Sextortion
[edit | edit source]Sextortion is sexual exploitation and extortion in which the victim is controlled by the abuse of power, such as in sex-trafficking situations, is common. It's also used when someone is blackmailed into doing something by threatening to release pornographic images if they refuse. It's challenging since the perpetrator is frequently anonymous or assumes the identity of someone else, and may be located on the other side of the world. It's possible that they're using TOR or hiding their IP address. When the offender is unknown, attracting law enforcement's attention is more difficult. Victims who encounter a stranger in a chatroom or on social media are common cases. Over time, the stranger gains the victim's trust and convinces them to transmit naked photographs or strip on webcams. The stranger then exposes himself to be malicious, threatening to distribute the naked photographs to the victim's friends, families, and employers unless the victim provides more, pays money, or performs sexual favors. Sextortion scams frequently target underage victims. When a pimp threatens to distribute naked photographs when a sex trafficking victim seeks to leave the business, the criminal is sometimes known to the victim. Sextorts have a knack for instilling fear in their victims. They could show images or a snapshot of an especially raunchy conversation.[23] They also regularly search the victim's social media accounts for information about their family and friends. To put it another way, they'll convince the victim that they can ruin their reputation at any time, even if this is typically untrue.
Most sextortion scams begin with catfishing. Many cases of sextortion start with a type of internet attack known as catfishing. When catfishing, the attacker takes on the persona of someone else, usually someone who is extremely attractive, such as a stunning young woman or a handsome and affluent businessman, or someone relatable, such as someone who shares the victim's interests. Sextorts who are skilled at catfishing are quite astute. They create realistic phony social media profiles using stolen photos and comprehensive personal information.[24]
The perpetrator would often approach a huge number of people on various social media and dating platforms after creating such profiles. They'll friend them, like their profiles, or send them a message. The attacker will begin communicating with the victim as soon as they react in order to gain their trust and gather information. The next step is to gather sexually explicit images of their victim in order to utilize them in a sextortion scheme.
Sextorts may also use email campaigns related to sextortion. Because anyone can become a victim, these strategies are often used. Attackers will send out a fear-inducing email to hundreds of people.
In most cases, the perpetrator will say in the email that he or she has access to the victim's camera. They'll argue that they exploited that access to video the victim while having sexual intercourse with her. The attacker could even threaten to expose a list of the victim's sexual websites visited. The criminal will demand payment using a (almost) untraceable method such as Bitcoin.
Bullying
[edit | edit source]There are different reasons why cyberbullying happens, and from my research I found five of them relevant to this topic. Majority of the incidents in cyberbullying happens where the perpetrator and victim know or met each other. Firstly, cyberbullies believe they won’t suffer any consequences. The perpetrator believes that if they post or send something that is harassing another anonymously, no one will find out. Cyberbullies do not see the reaction of the victim and that is what makes it easier for them to cyberbully.
Secondly, the perpetrator lacks empathy. Studies show that kids who cyberbully do not feel empathetic towards the other person. Furthermore, kids who cyberbully feel that it makes them funny, and popular among their peers. They want to look important in front of others, and they find bullying to be an effective way to achieve popularity.
Next, cyberbullies assume that everyone else is doing the same thing as them. Once they get into the habit of harassing others, they will find other individuals who are doing it. After a while it becomes normal for children to cyberbully. When kids do it together, they have a false sense of security in the numbers of people they see in their teams.
Lastly, the reason cyberbullying happens is to seek revenge. They want to make the person feel bad for what they went through. Usually, it is not the fault of the victim for what the cyberbully went through, but this is not the logic they listen to. For example, if they get a bad score in math or hate math, they will also dislike and bully the person who is good at math. Essentially, it is happening because the perpetrator is jealous of the other person’s success.
Cyberbullies Think Everyone Is Doing It
When teens believe lots of people are bullying online, they are more likely to engage in the behavior themselves. In their minds, it doesn’t seem like a significant problem because their peer group accepts the behavior. What’s more, kids will cyberbully others to fit in with a group that regularly harasses people online
(reference to other cyber bullying chapter )
Cyberexacerbated Crimes
[edit | edit source]To further expand on this topic, the internet and cyber realm has exacerbated the ability of pedophiles to view and circulate child pornography (CP). To analyze how this has come to be, it is important to analyze the different modes of communication and commerce made possible by the internet or the information superhighway. Today, it is reported that offenders typically partake in this heinous crime in one of the two main categories:
- pedophiles who use cyber technology to buy or sell children for sexual purposes
- those that exploit the web for viewing and disseminating CP.
While these crimes have existed long before the existence of the internet and computers, the rise of cyber technology has allowed offenders to grow their illegal businesses (in this realm) and proliferate the existence of CP. Previously, individuals had limited interactions from others outside of their immediate vicinity and this helped keep the supply of CP low. However, the rise in cyber technologies has enabled for communication with people across the world, creation of massive online groups, and ability to share massive files in matter of minutes which in turn has enabled pedophiles to conduct their crimes at ease and reach other evil minded people and potential victims with relative ease.[25]
Cyberspecific Crimes
[edit | edit source]To begin understanding cyber-specific crimes, it is best to look at a real world example of cybervandalism. Back in August 2019, an unidentified group of hackers were able to identify some vulnerabilities across different Minnesota government websites and exploit them. With the obtained access, the hackers proceed to change the website's content into anti-government rhetoric. It was revealed after that no serious private information was leaked during the process. Furthermore, officials determined that the hacker’s motive was unknown but certainly not with any financial gains in mind. Given that the motive was purely to irk, it was considered cybervandalism, and thus, a cyber-specific crime.[26]
Cyber Attacks
[edit | edit source]Arrested in June 2020 by the Dubai police and transferred to the United States to face justice is Ramon Abbas, aka Hush Puppy. Ramon Abbas is a cyber criminal who started his cybercrime attacks in Nigeria before moving to Malaysia. After he was caught, a total of $41 million and 13 luxury cars worth $6.8 million were seized from Hushpuppy by the United States FBI. Hush Puppy, also known as the Billionaire Gucci Master bought Gucci designer clothes, rented helicopters for launch, private jets, and luxury cars to tour the world. He spent most of his time in Dubai and Malaysia. Abbas Ramon was born on October 11, 1982, in Oworonshoki Lagos Nigeria and claimed the occupation of an Instagram influencer. He had a total amount of 2.5 million Instagram followers.
Furthermore, HushPuppy attack tactics include computer intrusions, business email
compromise schemes, and money laundering. A total of 2 million victims were recovered after the raid by the Dubai police. Successful deals by HushPuppy were the illegal transfer of $40 million after he defrauded a US law firm, defrauding U.S citizens of their pandemic payments, illegal transfer of $14.7 million from a financial institution, stealing $1.1 million from an individual to fund a school in Qatar, and he targeted other multiple victims. His last deal before his arrest was to steal $124 million from an undisclosed English football club. He is awaiting sentencing and might be charged up to 20 years in jail because he pleaded guilty to money laundering in 2021.
Viruses are pieces of computer programming code that causes a computer to behave in an undesirable way. Viruses can be attached to files or stored in the computer’s memory. Viruses may be programmed to different things such when they are downloaded or activated by a specific action for example viruses attached to file will infect that computer and any file created or modified on that machine. Viruses may also have programmed to display a message when certain activities are performed to execute the virus. Worms like viruses bury themselves in the memory of a machine and then duplicates itself with help from any help. It can send itself through emails and other connections. Phishing is when hackers try to obtain financial or other confidential information from Internet users, typically by sending an e-mail that looks as if it is from a legitimate organization, usually a financial institution, but contains a link to a fake Web site that replicates the real one. These con - artists urge the recipient of such emails to take action for rewards or avoid consequences. Hackers may use a backdoor within a computer system that is vulnerable, this allows them to remain undetected while they access important information. Key-logger programs allow attackers to view information that has been logged into a particular machine undetected. Botnets are a collection of computers that could be spread around the world they are connected to the internet, they are controlled by one single computer.
Malware
[edit | edit source]Malware is a term denoted for malicious software that spreads from computers and interferes with computer operations. Malware may be destructive, for example, deleting files or causing system ‘crashes’, but may also be used to steal personal data. Below is an outline of the most common forms of malware.
Viruses
[edit | edit source]Viruses are a standout amongst the most surely understood sorts of malware. A computer virus is like a flu virus designed to spread from host to host by replicating itself. [1]They require a host, (for example, a document, file or spreadsheet) in a computer to go about as a 'carrier', yet they can't contaminate a computer without human activity to run or open the tainted record. In more technical term, a computer virus is a malicious code programmed to alter the way the computer operates and designed to spread from one system to another. A virus operates by inserting or attaching itself to a legitimate program or document that supports macros in orders to execute the code. In this process, virus can cause damaging effects and cripple the host entirely after it made copies of itself.
Once a virus has successfully attached to a program, file, or document, the virus will lie dormant until circumstances cause the computer or device to execute its code. For a virus to infect your computer, you have to run the infected program, which in turn causes the virus code to be executed. This means that a virus can remain dormant on your computer, without showing major signs or symptoms. However, once the virus infects your computer, the virus can infect other computers on the same network. Stealing passwords or data, logging keystrokes, corrupting files, spamming your email contacts, and even taking over your machine are just some of the devastating and irritating things a virus can do.
Worms
[edit | edit source]Worms are also self-replicating programs, yet they can spread independently, inside and between computers, without requiring a host or any human activity. The effect of worms can therefore be more extreme than viruses, creating destruction across entire networks. Worms can also be utilized to drop trojans into the network. Before the widespread use of networks, computer worms were spread through infected storage media, such as floppy diskettes. When mounted on a system, these floppies would infect other storage devices connected to the victim system. USB drives are still a common vector for computer worms.[27] Computer worms often rely on the actions of, and vulnerabilities in, networking protocols to propagate. For example, the WannaCry ransomware worm exploited a vulnerability in the first version of the Server Message Block (SMBv1) resource sharing protocol implemented in the Windows operating system. Once active on a newly infected computer, the WannaCry malware initiates a network search for new potential victims: systems that respond to SMBv1 requests made by the worm. The worm can continue to propagate within an organization in this way. When a bring your own device is infected, the worm can spread to other networks.
Difference between Worms and Viruses: As defined in the "Security of the Internet" report, released in 1996 by the CERT Division of the Software Engineering Institute at Carnegie Mellon University, Computer Worms "are self-replicating programs that spread with no human intervention after they are started." In contrast, "Viruses are also self-replicating programs, but usually, require some action on the part of the user to spread inadvertently to other programs or systems." After a computer worm loads and begins running on a newly infected system, it will typically follow its prime directive: to remain active on an infected system for as long as possible and to spread to as many other vulnerable systems as possible
Trojans
[edit | edit source]Trojans are a type of malware that gives off an impression of being genuine projects yet encourage illicit access to a computer. They can perform capacities, for example, taking information, without the client's learning and may trap clients by undertaking a normal errand while really undertaking covered up, unapproved activities. Unlike a computer virus, a Trojan horse is not able to replicate itself, nor can it propagate without an end user's assistance. This is why attackers must use social engineering tactics to trick the end user into executing the Trojan. Typically, the malware programming is hidden in an innocent-looking email attachment or free download. When the user clicks on the email attachment or downloads the free program, the malware that is hidden inside is transferred to the user's computing device. Once inside, the malicious code can execute whatever task the attacker designed it to carry out.
The term Trojan horse stems from Greek mythology. According to legend, the Greeks built a large wooden horse that the people of Troy pulled into the city. During the night, soldiers who had been hiding inside the horse emerged, opened the city's gates to let their fellow soldiers in and overran the city. Here is one example of how a Trojan horse might be used to infect a personal computer, the victim receives an official-looking email with an attachment. The attachment contains malicious code that is executed as soon as the victim clicks on the attachment. Because nothing bad happens and the computer continues to work as expected, the victim does not suspect that the attachment is a Trojan horse and his computing device is now infected. The malicious code resides undetected until a specific date or until the victim carries out a specific action, such as visiting a banking website. At that time, the trigger activates the malicious code and carries out its intended action. Depending upon how the Trojan has been created, it may delete itself after it has carried out its intended function, it may return to a dormant state or it may continue to be active.
Some notable trojans
[edit | edit source]- Netbus – 1998 (published)
- Sub7 by Mobman – 1999 (published)
- Back Orifice – 1998 (published)
- Y3K Remote Administration Tool by E&K Tselentis – 2000 (published)
- Beast – 2002 (published)
- Bifrost Trojan – 2004 (published)
- DarkComet – 2008 (published)
- Blackhole exploit kit – 2012 (published)
- Gh0st RAT – 2009 (published)
- MegaPanzer BundesTrojaner – 2009 (published)
Spyware
[edit | edit source]Spyware is programming that attacks clients' security by get-together touchy or individual data from tainted frameworks and observing the sites went by. This data may then be transmitted to outsiders. Spyware can now and again be covered up inside adware (free and here and there undesirable programming that obliges you to watch commercials keeping in mind the end goal to utilize it). One case of spyware is key-logging programming, which catches, and advances keystrokes made on a computer, empowering gathering of touchy information, for example, passwords or ledger points of interest. Another sort of spyware catches screenshots of the casualty's computer. Spyware is thought to be a standout amongst the most perilous types of malware as its goal is simply to attack protection.
Adware
[edit | edit source]Adware (short for advertising-supported software) is a type of malware that automatically delivers advertisements. Common examples of adware include pop-up ads on websites and advertisements that are displayed by software. Often times software and applications offer “free” versions that come bundled with adware. Most adware is sponsored or authored by advertisers and serves as a revenue generating tool. While some adware is solely designed to deliver advertisements, it is not uncommon for adware to come bundled with spyware (see below) that is capable of tracking user activity and stealing information. Due to the added capabilities of spyware, adware/spyware bundles are significantly more dangerous than adware on its own.
Rootkit
[edit | edit source]A rootkit is a type of malicious software designed to remotely access or control a computer without being detected by users or security programs. Once a rootkit has been installed it is possible for the malicious party behind the rootkit to remotely execute files, access/steal information, modify system configurations, alter software (especially any security software that could detect the rootkit), install concealed malware, or control the computer as part of a botnet. Rootkit prevention, detection, and removal can be difficult due to their stealthy operation. Because a rootkit continually hides its presence, typical security products are not effective in detecting and removing rootkits. As a result, rootkit detection relies on manual methods such as monitoring computer behavior for irregular activity, signature scanning, and storage dump analysis. Organizations and users can protect themselves from rootkits by regularly patching vulnerabilities in software, applications, and operating systems, updating virus definitions, avoiding suspicious downloads, and performing static analysis scans.
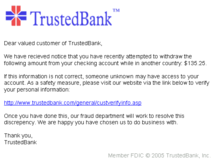
Phishing
[edit | edit source]Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication. There are various forms of phishing attacks on channels such as emails, social software, websites, portable storage devices and cell phones. There are several different ways of trying to drive users to a fake website:
Types of Phishing Attacks
[edit | edit source]- Spam e-mail, a spoof email which will distract customers to look similar to a bank email, or from any financial institution.
- Hostile profiling, a targeted version of the above method: the cyber criminal exploits web sites that use e-mail addresses for user registration or secret key reminders and directs the phishing trick at specific users (requesting that they affirm passwords, etc.). Introduce a Trojan that edits the hosts file, so that when the casualty tries to browse to their bank‟s web site, they are re-directed to the fake site.
- ‘Spear phishing’, an attack on a specific organization in which the phisher simply asks for one employee‟s details and uses them to gain wider access to the rest of the network.[28]
- 'Whale Fishing' is a type of spear phishing where the target of the attack is someone with a high profile within a company or organization. These individuals are usually the CEO, CFO, COO, etc, because they will have sensitive information that once stolen, will be used for a malicious reason such as ransom.[29]
- Traditional type of phishing attack is Not all phishing attacks work in the manner just described.
- The “rock-phish" gang3 has adapted its attack strategy to evade detection and maximize phishing site accessibility. It has separated out the elements of the attack while including redundancy in the face of take-down requests. The pack first purchases a number of area names with short, generally meaningless, names, for example, lof80.info. The email spam then contains a long URL, for example, http://www.bank.com.id123.lof80.info/vr where the main part of the URL is intended to make the site appear genuine and a mechanism, for example, `wildcard DNS‟ can be used to resolve every single such variation to a specific IP address. It then maps each of the space names to a dynamic pool of compromised machines as per a pack controlled name server. Each compromised machine runs an intermediary system that relays requests to a backend server system. This server is loaded with a large number (up to 20 at a time) of fake bank websites, all of which are available from any of the stone phish machines. However, which bank site is reached depends solely upon the URLpath, after the main „/‟. (Because the group uses proxies, the real servers – that hold all the web pages and collate the stolen data – can be located anywhere.)
Password Attacks and Types
[edit | edit source]Password attacks are when an entity tries to gain access to any particular systems by cracking or guessing the user’s password. These attacks are very prominent since, weak and easily known terms can be guessed as well as methods such as brute force can be carried out as raw processing power is readily available from high power computers available in the market. This type of attack works without any type of malicious software or code to run on the user’s system. These attacks are typically run on the hacker’s computers utilizing specialized software, hardware (such as GPUs), and methodologies to crack the end user’s password in order to gain access to said accounts.
Dictionary Attacks
[edit | edit source]Dictionary attacks are primarily based in two methodologies: generally common passwords and user specific keywords. Generally common passwords are passwords which people tend to use commonly. Due to the fact that many people reuse passwords and use generally simple passwords, lists of plaintext passwords have accrued over the course of decades of leaks. These plaintext passwords can then be hashed (and perhaps salted first) and compared to a password hash which was generated with an unknown password. Due to the likelihood that one has utilized an existing, common password, comparing the hashes of common passwords with unknown hashes can be quite effective. Among the plaintext dictionaries of passwords on the internet, rockyou.txt is perhaps one of the most famous. It originates from when the social application site RockYou was hacked in 2009, when the hacker leaked 32 million user accounts. [30] In the case of a hash not using a salt, one may use a dictionary of hashed passwords called a "rainbow table" in place of hashing common passwords themselves. This is much faster than dealing with plaintext dictionaries, but does not permit for any form of hybrid or combination attack. One may also use a plaintext wordlist which is made from targetted information about a victim such as their social security number, name, or date of birth. This information may be gathered from social engineering through phishing or vishing, open source intelligence techniques, or previous data breaches (including old plaintext passwords and personal details).
Brute Force Attacks
[edit | edit source]A brute force attack checks all of the permutations of a string of certain length, made of certain types of characters. Thus, these type of attacks require an enormous amount of time to complete as well as a lot of processing power. In addition to time and capability constraints, brute force attacks being done directly to a software system (such as brute forcing a website with hydra) are easily detectable and easy to mitigate. While uncomplicated passwords with a length of less than 8 are generally weak to brute force attacks, longer passwords become unmanageable, even for expensive password cracking rigs. Beyond this, it is uncommon to know exactly the length or characters that have gone into a password, so it is usually necessary to cycle through different password lengths.
Hybrid/Combinatorial Attacks
[edit | edit source]One of the most effective forms of password cracking is a hybrid or combinatorial attack. It is referred to as such due to its approach of combining wordlists and reasonable brute forcing techniques together to create likely, targeted hashes. Rather than utilizing only brute force or a single wordlist, it is possible with many advanced password cracking utilities, such as HashCat, to apply complex sets of rules and combinations to given input in order to create a likely password output. For example, by knowing that users typically add numbers or special characters to the very end of a password, or replace certain letters with numbers (such as o with zero), it is possible to take a given wordlist and apply rules to it to create likely alternatives to known, popular passwords. On top of this, it is possible to combine wordlists together to create wordlists with multiple words in each entry, such as cool and dog becoming cooldog. An example of combining complex, realistic rulesets with a targeted wordlist in popular media is demonstrated in the very first episode of Mr Robot, when the main character cracks the password of another character in the show. It ends up with the password being "Dylan_2791", the name of the character's favorite artist and the year of the character's birth backwards. By adding capitalization, reversing, and special character placement to a strong wordlist, one can form a deadly attack, obvious from the 24 second crack time of the aforementioned password. [31]
Denial-of-Service(DOS) Attacks
[edit | edit source]A Denial-of-Service(DoS) attack inhibits the authorized users from accessing the system mostly by flooding the existing system with huge amounts of gibberish data/requests resulting in a blockage in the system. This attack overloads the system with an overwhelming quantity of data packets which is not anticipated by the server which results into a slowdown or a block.[32] This may result in a slow internet connection which may hamper the authorized user to access critical data like emails or files over FTP, etc. This may cause huge losses in both time and money. Such attacks are rarely used to hack systems from authorized users but there have been cases where such DoS attacks were deployed to lock down the network and gain access to the vulnerable firewalls. These attacks are not easy to identify as they may be easily be confused with a slower internet connection, etc. and may persist in an environment for as long as months.
Along with the regular DoS attacks, there is a different type of DoS attack called a Distributed Denial-of-Service(DDoS). This attack is very similar to a regular DoS attack in the sense that even they act as a slowdown by throwing an overwhelming amount of data packets at the target.[32] But, the basic distinction is that DDoS is much more efficient and dangerous since they operate from an entire affected network rather than from a single affected user. Hence, the DDoS is very difficult to dodge for any system since there is data coming in from multiple sources at the same time. Unlike other kinds of cyberattacks, DDoS assaults don't attempt to breach your security perimeter. Rather, they aim to make your website and servers unavailable to legitimate users. DDoS can also be used as a smokescreen for other malicious activities and to take down security appliances, breaching the target’s security perimeter. DDoS assaults often last for days, weeks, and even months at a time, making them extremely destructive to any online organization. Amongst other things, DDoS attacks can lead to loss of revenues, erode consumer trust, force businesses to spend fortunes in compensations, and cause long-term reputation damage. The differences between DoS and DDoS are substantive and worth noting. In a DoS attack, a perpetrator uses a single Internet connection to either exploit a software vulnerability or flood a target with fake requests—usually to exhaust server resources (e.g., RAM and CPU).
On the other hand, distributed denial of service (DDoS) attacks are launched from multiple connected devices that are distributed across the Internet. These multi-person, multi-device barrages are generally harder to deflect, mostly due to the sheer volume of devices involved. Unlike single-source DoS attacks, DDoS assaults tend to target the network infrastructure in an attempt to saturate it with huge volumes of traffic. DDoS attacks also differ in the manner of their execution. Broadly speaking, DoS attacks are launched using home-brewed scripts or DoS tools (e.g., Low Orbit Ion Canon), while DDoS attacks are launched from botnets — large clusters of connected devices (e.g., cell phones, PCs or routers) infected with malware that allows remote control by an attacker.
DoS Attack Categories
[edit | edit source]DoS attacks can be divided into two general categories:
1. Application layer attacks (a.k.a., layer 7 attacks) can be either DoS or DDoS threats that seek to overload a server by sending a large number of requests requiring resource-intensive handling and processing. Among other attack vectors, this category includes HTTP floods, slow attacks (e.g., Slowloris or RUDY) and DNS query flood attacks. Gaming website hit with a massive DNS flood, peaking at over 25 million packets per second The size of application-layer attacks is typically measured in requests per second (RPS), with no more than 50 to 100 RPS being required to cripple most mid-sized websites.
2. Network layer attacks (a.k.a., layer 3–4 attacks) are almost always DDoS assaults set up to clog the “pipelines” connecting your network. Attack vectors in this category include UDP flood, SYN flood, NTP amplification and amplification attacks, and more. Any of these can be used to prevent access to your servers, while also causing severe operational damages, such as account suspension and massive overage charges. DDoS attacks are almost always high-traffic events, commonly measured in gigabits per second (Gbps) or packets per second (PPS). The largest network layer assaults can exceed 200 Gbps; however, 20 to 40 Gbps are enough to completely shut down most network infrastructures.
HTTP Attack
[edit | edit source]What is an HTTP attack? HTTP flood attack is when an attacker overwhelms a server by sending in a huge amount of requests to the target server. Once the server is saturated and unable to respond to any more requests, DoS will occur when a user sends in an additional request.
HTTP flood attack is the OSI model layer 7 attacks. That is the application layer and this layer deals with internet protocols like HTTP. HTTP is commonly used to load browser website, and it is nerve-breaking to mitigate application-layer attacks since it is difficult to differentiate between normal user traffic versus malicious traffic. To maximize the effect of this attack, attackers usually create bots to leverage their timing of sending in the request at the same time. This results in overloading the server.
Working of HTTP Attacks
[edit | edit source]There are two types of HTTP flood attacks:
1. HTTP GET attack - Multiple users or bots tend to send a tremendous amount of requests to access some form of an asset from the target server. The request could be regarding accessing images, files, music, reports, and many more. Denial-of-Service is successful when the target server is inundated with the incoming traffic and is unable to process any more requests.
2. HTTP POST attack - Unlike the HTTP GET attack, the users send in forms in large quantities. The incoming forms are usually login or data forms that need to be pushed into a persistence layer. That persistence layer is usually a database where all the queries to run to process the data. That process is relatively intense compared to the bandwidth through which the forms are sent. This results in Denial-of-Services when the target website/server is unable to process any more forms.
Mitigating HTTP Attacks
[edit | edit source]HTTP attacks, as mentioned above, are dealt with in layer 7 of the OSI model. The application layer is complex and with that tremendous amount of traffic, it gets nerve-breaking to differentiate between normal users and the bots. Many attacks can be stopped by setting up JavaScript computational challenges such as captcha. These could be set up at login pages, sign-ups, and other kinds of forms too. Other way to mitigate HTTP attacks is to use a Web Application Firewall (WAF). WAF manages IP reputation and blocks the incoming malicious traffic on-the-fly.
Man in the Middle (MITM)
[edit | edit source]A man in the middle (MITM) attack is a general term for when a perpetrator positions himself in a conversation between a user and an application—either to eavesdrop or to impersonate one of the parties, making it appear as if a normal exchange of information is underway. The goal of an attack is to steal personal information, such as login credentials, account details and credit card numbers. Targets are typically the users of financial applications, SaaS businesses, e-commerce sites and other websites where logging in is required. Information obtained during an attack could be used for many purposes, including identity theft, unapproved fund transfers or an illicit password change. Additionally, it can be used to gain a foothold inside a secured perimeter during the infiltration stage of an advanced persistent attack (APT) assault. Broadly speaking, a MITM attack is an equivalent of a mailman opening your bank statement, writing down your account details and then resealing the envelope and delivering it to your door.

Man in the Middle Attack Progression
[edit | edit source]Successful MITM execution has two distinct phases: interception and decryption.
Interception
[edit | edit source]The first step intercepts user traffic through the attacker’s network before it reaches its intended destination. The most common (and simplest) way of doing this is a passive attack in which an attacker makes free, malicious WiFi hotspots available to the public. Typically named in a way that corresponds to their location, they aren’t password protected. Once a victim connects to such a hotspot, the attacker gains full visibility to any online data exchange. Attackers wishing to take a more active approach to interception may launch one of the following attacks:
- IP spoofing involves an attacker disguising himself as an application by altering packet headers in an IP address. As a result, users attempting to access a URL connected to the application are sent to the attacker’s website.
- ARP spoofing is the process of linking an attacker’s MAC address with the IP address of a legitimate user on a local area network using fake ARP messages. As a result, data sent by the user to the host IP address is instead transmitted to the attacker.
- DNS spoofing, also known as DNS cache poisoning, involves infiltrating a DNS server and altering a website’s address record. As a result, users attempting to access the site are sent by the altered DNS record to the attacker’s site.
- Eavesdropping attacks are when an attacker intercepts a victim’s network traffic as their sensitive data travels from the victim’s device to their intended destination. This is usually done through software that monitors the network traffic of the victim while they are connected to a weakly encrypted or unencrypted network like a public WI-FI hotspot.[33]
Decryption
[edit | edit source]After the interception, any two-way SSL traffic needs to be decrypted without alerting the user or application. A number of methods exist to achieve this:
HTTPS spoofing sends a phony certificate to the victim’s browser once the initial connection request to a secure site is made. It holds a digital thumbprint associated with the compromised application, which the browser verifies according to an existing list of trusted sites. The attacker is then able to access any data entered by the victim before it’s passed to the application.
- SSL BEAST (browser exploit against SSL/TLS) targets a TLS version 1.0 vulnerability in SSL. Here, the victim’s computer is infected with malicious JavaScript that intercepts encrypted cookies sent by a web application. Then the app’s cipher block chaining (CBC) is compromised so as to decrypt its cookies and authentication tokens.
- SSL hijacking occurs when an attacker passes forged authentication keys to both the user and application during a TCP handshake. This sets up what appears to be a secure connection when, in fact, the man in the middle controls the entire session.
- SSL stripping downgrades a HTTPS connection to HTTP by intercepting the TLS authentication sent from the application to the user. The attacker sends an unencrypted version of the application's site to the user while maintaining the secured session with the application. Meanwhile, the user’s entire session is visible to the attacker.
Man in the Middle Attack Prevention
[edit | edit source]Blocking MITM attacks requires several practical steps on the part of users, as well as a combination of encryption and verification methods for applications.
For users, this means:
- Avoiding WiFi connections that aren’t password protected.
- Paying attention to browser notifications reporting a website as being unsecured.
- Immediately logging out of a secure application when it’s not in use.
- Not using public networks (e.g., coffee shops, hotels) when conducting sensitive transactions.
For website operators, secure communication protocols, including TLS and HTTPS, help mitigate spoofing attacks by robustly encrypting and authenticating transmitted data. Doing so prevents the interception of site traffic and blocks the decryption of sensitive data, such as authentication tokens. It is considered best practice for applications to use SSL/TLS to secure every page of their site and not just the pages that require users to log in. Doing so helps decreases the chance of an attacker stealing session cookies from a user browsing on an unsecured section of a website while logged in.'
Ransomware
[edit | edit source]Ransomware is a type of malicious software from crypto virology that threatens to publish the victim's data or perpetually block access to it unless a ransom is paid. While some simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called crypto viral extortion, in which it encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them. The earliest variants of ransomware were developed in the late 1980s, and payment was to be sent via snail mail. Today, ransomware authors order that payment be sent via cryptocurrency or credit card.
There are several different ways that ransomware can infect your computer. One of the most common methods today is through malicious spam, or malspam, which is unsolicited email that is used to deliver malware. The email might include booby-trapped attachments, such as PDFs or Word documents. It might also contain links to malicious websites.
Malspam uses social engineering in order to trick people into opening attachments or clicking on links by appearing as legitimate—whether that’s by seeming to be from a trusted institution or a friend. Cybercriminals use social engineering in other types of ransomware attacks, such as posing as the FBI in order to scare users into paying them a sum of money to unlock their files.
Another popular infection method, which reached its peak in 2016, is Malvertising. Malvertising, or malicious advertising, is the use of online advertising to distribute malware with little to no user interaction required. While browsing the web, even legitimate sites, users can be directed to criminal servers without ever clicking on an ad. These servers catalog details about victim computers and their locations, and then select the malware best suited to deliver. Often, that malware is ransomware.
Types of ransomware
[edit | edit source]There are three main types of ransomware, ranging in severity from mildly off-putting to Cuban Missile Crisis dangerous. They are as follows:
Scareware
[edit | edit source]Scareware, as it turns out, is not that scary. It includes rogue security software and tech support scams. You might receive a pop-up message claiming that malware was discovered and the only way to get rid of it is to pay up. If you do nothing, you’ll likely continue to be bombarded with pop-ups, but your files are essentially safe.
A legitimate cybersecurity software program would not solicit customers in this way. If you don’t already have this company’s software on your computer, then they would not be monitoring you for ransomware infection. If you do have security software, you wouldn’t need to pay to have the infection removed—you’ve already paid for the software to do that very job.
Screen lockers
[edit | edit source]Upgrade to terror alert orange for these guys. When lock-screen ransomware gets on your computer, it means you’re frozen out of your PC entirely. Upon starting up your computer, a full-size window will appear, often accompanied by an official-looking FBI or US Department of Justice seal saying illegal activity has been detected on your computer and you must pay a fine. However, the FBI would not freeze you out of your computer or demand payment for illegal activity. If they suspected you of piracy, child pornography, or other cybercrimes, they would go through the appropriate legal channels.
Encrypting ransomware
[edit | edit source]This is the truly nasty stuff. These are the guys who snatch up your files and encrypt them, demanding payment in order to decrypt and redeliver. The reason why this type of ransomware is so dangerous is because once cybercriminals get ahold of your files, no security software or system restore can return them to you. Unless you pay the ransom—for the most part, they’re gone. And even if you do pay up, there’s no guarantee the cybercriminals will give you those files back.
Notable Example of Ransomware:
[edit | edit source]Drive-by Downloads
[edit | edit source]The term drive-by download gives us all the insights as to how a malware can infect the whole system when a user simply clicks on a website that runs the malicious code. There are various stages as to how this malware infects the system. The first stage is called the entry point as explained above. The second stage is called the distribution where some of the most trusted sites are compromised to redirect to the sites controlled by the hackers. The third stage is called the exploit stage where the browser succumbs to the exploit kit which lets the hackers know about the security vulnerability that it can easily attack.[34] The following stage is the infection stage where the hacker is well aware of the vulnerability point and it downloads the payload package which installs itself into the computer. The final stage is the execution of the downloaded program which is designed to make money for the masters.[34]
Website Application Attacks
[edit | edit source]Web Attacks - Better known as Web application attacks in which an attacker exploits the vulnerabilities of a website’s code to steal personal or sensitive information from the website’s own databases through various methods. [35]
SQL Injection Attacks
[edit | edit source]SQL or Structured Query Language is used in programming to allow the user to create, manipulate, and delete databases. Attackers usually take try to take advantage of a website that has a data input field, web form, or even a search bar. Normal users would generally input data like their name, phone, or identification number while on the other hand, an attacker uses the same input field and try to gain access to the website’s database by entering SQL prompts or queries. If the input field is not tested properly, this allows an attacker to execute specific SQL commands that can retrieve, change, or delete any information within the compromised database.[36]
Types of SQL Injection Attacks
[edit | edit source]SQLi vulnerability is one of the oldest and most common types of web security issues. There are several types of SQL Injection Attacks:
# 1 In-band SQLi
[edit | edit source]This is the most simple and common type of SQL Injection. Through this, an attacker can use the same communication channel to execute the attack and gather information.
In-bank SQLi is further categorized in two common types of In-band SQLi attacks.
- Error-based SQLi
- Union-based SQLi
# 2 Inferential SQLi (Blind SQLi)
[edit | edit source]This attack is time-consuming and dangerous compared to the other SQL Injections. In this attack, an attacker is not able to see results on the web application but can rather communicate directly with the database and make changes to the database structure. Those changes are made using payloads and the results are seen as the web application responses to the database.
This attack is further categorized into two attacks:
- Content-based Blind SQL Injection
- Time-based Blind SQL Injection
# 3 Out-of-Band SQLi
[edit | edit source]This is not a very common type of SQL Injection. This attack depends on the features of the database server that the web application is using.
# 4 Safeguard against SQL injections[37]
[edit | edit source]In order to mitigate the risk of SQL injection attacks the following should be implemented;
- Use the principle of least privilege
- Use of NIST or other industry standard checklist to verify security policies and procedures
- Implement firewall rules to block malicious IP address
- Use type-safe stored procedures and prepared statements
- Minimize information provided through error messages
- Sanitize input
- Check data input for type, length, format, and range
- Use escape routes to handle special input characters such as (‘)
Cross-Site Scripting Attacks
[edit | edit source]Cross-Site Scripting (XSS) - Cross-Site Scripting is another web attack in which a potential attacker exploits the vulnerabilities of the website or web application. While SQL Injection is an attack that targets the website’s database, an XSS attack targets the users who visit these websites directly. Attackers achieve this by embedding malicious code or scripts on the website where a user will most likely interact with; the most common choice would be an input field. Once compromised, an attacker will have control over the victim’s browser. With it they can view the browser history, cookies could be stolen, impart trojans, remote control the victim’s computer, etc.[38]
Safeguards
[edit | edit source]We live in an era, where cyber security is a momentous issue. Cybercrimes are becoming the new normal nowadays.so what makes you think that you will be spared by cyber criminals? we have suggested some steps to remember for the rest of your life to safe guard yourself from very common cyber-attacks. so, let’s get back to the original question?
How to protect yourself from cyber-attacks? or how to protect yourself online?
1. Instead of ‘Passwords’, Use ‘Passphrases’ for Different websites
[edit | edit source]Use different user ID/password combinations for different accounts and avoid writing them down. you can create more complicated passwords by combining letters, numbers, special characters (minimum 8 characters in total) and change them on a regular basis.
Using pass-phrases is a wonderful idea, sentences such as ILoveFacebookSoMuch are very hard to crack!
You probably don’t want to remember too many passwords for too many websites. You can create your own format for passwords. for example: yourname(xx)@websitename, where xx is any 2 digits random number
2. Secure your computer/laptop physically and by: Activating your firewall
[edit | edit source]A Firewall works exactly as the name suggests. it monitors all the incoming and outgoing traffic towards your computer. If your antivirus doesn’t include a firewall, make sure you have windows firewall ‘Activated’.
3. Never upload your personal data ‘unencrypted’ to dropbox, google drive or any online file sharing services.
[edit | edit source]It takes not more than 5 minutes to encrypt a zip file or any single file such as a photo, video or a document with AES-256-bit encryption. But it saves you from getting your personal data leaked. And you can relax even if these big companies face a data breach. If using windows, use bit locker to encrypt hard disk drives with important data!
you may use this software to encrypt your files: https://www.aescrypt.com/download/
4. Crosscheck your Social-Media security settings
[edit | edit source]Make sure your social networking profiles (e.g. Facebook, Twitter, YouTube, google+ etc.) are set to private. Check your security settings. never post sensitive information about you online. Once it is on the Internet, it is there forever commenting on various website may show up after 2 years in google search result of your name try a google search for your name with double quotes. for example: http://bfy.tw/mnR
5. Do not procrastinate update installations (even the “installing 127 of 1204” ones)
[edit | edit source]Keep your applications and operating system (e.g. Windows, Mac, Linux) updated with the latest security updates. These updates are not just limited to adding new features to your system, but it comes with security patches for vulnerabilities in your operating system. keep common software’s /plugins such as flash player, Microsoft Office ‘up to date’ as they are widely used, hackers are always finding ways to exploit their vulnerabilities.
6. Wi-Fi-The most vulnerable network Ever!!
[edit | edit source]Always secure your Wi-Fi with secure password, WPA2 encryption, etc. Do NOT use public Wifi for transactions, if not properly configured, every wifi is vulnerable.
Review and modify default settings and passwords. Never use public wifi, if you have some personal /secret information in your personal/office laptop, they are vulnerable. Avoid conducting financial or corporate transactions on these networks.
7. Encrypt your data (Important)
[edit | edit source]Use encryption for your most sensitive files such as tax returns or financial records, make regular back-ups of all your important data, and store it in another location. Do not leave your credit card around that tempts children to use them.
[wpdevart_like_box profile_id=”792637984138412″ connections=” show” width=”300″ height=”150″ header=” small” cover_photo=”show” locale=”en_US”]
8. Secure your Mobile Devices Physically and Digitally.
[edit | edit source]Be aware that your mobile device is vulnerable to viruses and hackers. Take care of the security even though you download apps ONLY from ‘Google Play store’. Worst case scenario is getting your phone camera hacked and the hackers may steal the photographs which THEY took from your mobile.
9. Protect your e-identity, look for https://
[edit | edit source]Be cautious when giving out personal information such as your name, number, address or financial information on the Internet. Make sure that websites are secure and using https. The address will be look like this.
https://www.facebook.com.
https is essential for websites which involve financial transactions. it means the data you send and receive is encrypted.
make sure that you’ve enabled privacy settings (e.g. when accessing/using social networking sites).
10. Do NOT store your card details on websites
[edit | edit source]If a website insists for storing your credit card information, so that your transactions can be processed faster next time, back off! you will never want to find your credit card information if that website’s database is dumped on pastebin or ghostbin like websites. try searching for last 6 or 8 digits of your credit cards numbers in google with double quotes to make sure that your credit card info is not available on the internet.(it may be available in deepweb).
11. Got hacked??Call the right person/ lawyer / LEA for help
[edit | edit source]Don’t panic! If you are a victim, if you come to know about any illegal Internet content (e.g. child exploitation) or if you suspect a computer crime, identity theft or a financial scam, report that to respected law enforcement agency. If you have any problems with your personal computer, ask for help only to a trusted person or a certified technician.
12. Never Trust E-mails
[edit | edit source]Do not trust emails which offers prize money through lotteries of which you are not a participant. Similarly, don’t pay for the job works which you are not in correspondence through official channels. Don’t give your credit card number(s) and CVV numbers online unless the site is a secured and reputable site. Sometimes a tiny icon of a padlock appears to symbolize a higher level of security but it may be just an image. This icon is not a guarantee of a secure site, but might provide you some assurance.
13. Do not share a code received accidentally via 2 step verifications!
[edit | edit source]Enable 2 step verification. In addition to entering your password, you are also asked to enter a verification code sent via SMS to your phone (if logged in from an unusual device). So a hacker might crack your password, stealing your password may be an easy task for some hackers, but hacking into your android and read the OTP /security code sent via SMS can be a tough job. Hackers might try to get that code from you using social engineering. But don’t forward that code to anyone.
14. Ignore pop-ups, drive-by downloads while Surfing
[edit | edit source]Pop-ups are another challenge to cyber security, they can contain malicious software which can trick a user into verifying something. If you download software setup file which can’t have a 1.2 MB size. Then you should check for the file name and source of it. This is known as a drive-by download. Always ignore pop-ups offering things like site surveys on e-commerce sites, as they are sometimes where the malicious code is.
15. Review your credit card statements
[edit | edit source]Even after taking care of these, make sure you are not already being hacked! look for your credit card /bank statements. Don’t ignore even if a small amount is deducted suspiciously, report that.it may be part of a salami attack.in which small fraction of money is stolen from millions of people.
Share these tips, and comment here to add some extras! we are looking forward to add new tips to this article.
Cyber Crime Investigation Techniques
[edit | edit source]Computers and the internet present unique challenges to investigators. Internet crime lacks physical indicators, witnesses, and location-dependency of typical crimes. Evidence is often more difficult to acquire and tie to an underlying cause or responsible party.
The field of investigating crimes after they have occurred is called forensics, and thus, on digital media it is called cyber forensics.
Cyber forensics is a broad discipline but there are many key concepts used by investigators.
One of the most important topics in cyber forensics is ensuring that evidence is not modified or tampered with while in the process of investigating a system. Modern computers perform many activities in the background or when the user interacts with the system, so forensics may take steps to avoid changes.[39]
Disk Imaging is used to capture data from a device that is potentially involved in a crime. Copies of this image are investigated to uncover evidence, so as to not modify the original evidence.[39]
Chain of custody establishes where the evidence is kept, who used it, and how. This is important because it establishes that evidence is modified minimally and shows the steps used to capture it. This maintains its admissibility in court.[39]
Logs, or logging data, are typically text-based documents that list actions taken by another system or user of a system within a program. They are often created or used for debugging purposes but also contain data that is useful to digital investigators, because they show user interactions within a system. They are also relevant to cybersecurity incident response to analyze the cause of an attack.
Cybercrime investigations require a good understanding of computer systems, as logging data is not usually displayed in a “user-friendly” or simple format that describes the exact actions a user took. Instead, a timeline is constructed by using smaller events logged on a system. It also requires the skills of a typical criminal investigator, such as building a hypothesis of what a criminal may have done in order to determine where to look for evidence.
Tools
[edit | edit source]Digital forensics investigators often use specialized tools to extract logging data from computer systems, such as FTK Imager and Paraben E3.[39] These tools can display and categorize large amounts of data and assist in the identification of meaningful evidence in a large set of data or disk image.
Cyberwarfare
[edit | edit source]Overview
[edit | edit source]A cyberattack is best defined as an attack that is administered virtually and intended to disrupt, modify, or destroy a computer system and/or network. Cyberwarfare is a broader term for a cyberattack or series of cyberattacks that may be initiated by individuals or entities belonging to a particular nation who intend to cause harm to another nation. Cyberwafare can currently typically be broken into seven (7) different categories. These categories consist of Espionage, Sabotage, Denial-of-Service (DoS), power grid attack, Propaganda, Economic, or surprise. In recent years, there have been several key players participating on the political battlefield of cyberwarfare such as Russia, China, North Korea, and Iran to name a few. Many of these attacks have been intended to weaken the militaries of other countries, such as Russia’s cyberattacks on Estonia and Georgia and China, Iran, and North Korea’s attacks on the United States Department of Defense.[40] In other cases, these nations have launched cyberattacks to destabilize the critical infrastructures that enable other nations to operate and serve their citizens.[41] Below are some of the different categories of cyberwarfare and examples.
Types of Cyberwarfare
[edit | edit source]Sabotage
[edit | edit source]One of the first Cyberware instances came from the stuxnet worm that was developed by the U.S. and Israeli government in 2005 and deployed in 2010 against the Iranian nuclear facility. The worm was so complex that still to this day, nobody knows how they were able to get it onto the computers as everything was air gapped. Although the worm was successful and put a major slowdown to the Iranian government from advancing in nuclear weaponry, it also opened the pandora's box of other countries developing worms and other attacks in the cyberwarfare field.
Denial-of-Service (DoS)
[edit | edit source]DoS attacks are one of the most common types of attacks by both script kiddies and nation states because of the ease of use. One can easily script and use bots to perform a distributed denial of service (DDoS) attack on just about any website or system connected to the internet. This can potentially impact citizens from accessing critical information or the availability of access to an important site.
Economic Disruption
[edit | edit source]This type of cyberwarfare can wreak havoc on one's economy as a big possible target is the stock. This is one area that a lot of governments are trying to protect as it affects everyone's livelihoods and way of living. In 2017, one major cyber attack called WannaCry was released as ransomware and caused major disruptions to healthcare systems and governments in the U.K. and Ukraine but also impacted many other organizations across the globe. The ransomware attacked Microsoft computer systems by taking an exploit in the operating system that was not patched and encrypting the users computer and demanding payment to perform un-encryption. This attack could have had major implications if it was deployed on financial institutions servers as it would send the market into turmoil. One type of attack that can be related to economic disruption is the supply chain attack just as what happened in SolarWinds.
Cyber Espionage
[edit | edit source]Cyber espionage is the infiltration of computer systems and networks for the purpose of finding confidential information belonging to a state or entity. There are two primary reasons why state actors might participate in cyber espionage: to extract sensitive intelligence from foreign governments or to steal private data from foreign companies to obtain a competitive edge. In the case of the former, individuals often pose the argument that a nation might need to engage in cyber espionage to obtain information on foreign intelligence due to national security concerns. For instance, foreseeing potential attacks from terrorist organizations or discovering foreign policies of rival nations may be critical for a nation when it comes to protecting itself from outside threats. Of course, cyber espionage can be conducted for malicious purposes as well. In 2015, a young member of the Islamic State of Iraq & Syria (ISIS) living in Malaysia at the time was charged by the United States for hacking into a database holding information about over a thousand military members and government personnel. Outside of the public sector, nations may also focus their cyberespionage attacks on organizations in the private sector, which is known as economic cyber espionage. An example of this is when Google accused China of stealing its source code so that it could use it to spy on other organization. In another case, Chinese members of the People’s Liberation Army were wanted by the FBI for hacking data systems of American companies to steal confidential trade secrets that could be used to advance Chinese corporations.[42]
Just War
[edit | edit source]One of the most controversial aspects of cyberwarfare is the difficulty associated with classifying it as a traditional form of war. Cyberwarfare attacks take place within the digital world and transcend physical borders, which means that they may be difficult to trace back to a specific state sponsor who coordinated the attack. In addition, these attacks typically do not cause physical harm to civilians as opposed to traditional forms of weaponry like bombs or bullets. International warfare laws do not define cyber warfare or stipulate what measures nations should take to defend themselves and retaliate against other nations engaging in cyberwarfare, which has led to disagreements between nations on how to address the situation.[41] Although war usually constitutes as military action on soil and can have civilian lives impacted, cyber war can do just that as well. Attacking country infrastructure and organizations to gain an advantage, can play a major impact on civilians' lives and way of living even if it does not directly impact a person's life physically via weapons.
Reason for Attacks
[edit | edit source]Traditionally, mitigation efforts for cyber-attacks have been focused on securing systems and monitoring network traffic for malicious activity; recently, however, researchers have recognized that understanding the social, political, economic, and cultural (SPEC) conflicts that motivate cyber-attacks may enhance mitigation strategies[43].
Political
[edit | edit source]Political cyber-attacks can be committed by an individual actor, political group — e.g., extremist groups —, or a state. The motivations for these attacks can be diverse and complicated but can be broken down into basic categories. Researchers out of the University of Nebraska have created the following categories for politically motivated attacks not committed by a state: protests against political actions, protests against laws or public documents, and outrage against acts related to physical violence[44].
- Protests Against Political Actions: This category is primarily comprised of attacks in response to certain political actions or positions taken by governments, politicians, corporations, or special interest groups. A common example of this kind of attack is the defacing of political candidates' websites by individuals or groups that disagree with the candidates' policy stances, but these attacks may be as serious as the 1998 attack on India’s Bhabha Atomic Research Center(BARC) by anti-nuclear activists.
- Protests Against Laws or Public Documents: These attacks are typically a response to the passing of an unpopular law. Upon the passing of the Communications Decency Act in 1996, several protesters were involved in repeatedly deleting the content of the law off the United States Department of Justice's website.
- Outrage Against Acts Related to Physical Violence: This is the largest and most common category of politically-motivated cyber-attacks, and is closely associated with extremist groups. These attacks are motivated by acts of violence — typically committed by a government — and are meant to be retaliatory. Attacks on military infrastructure by anti-war protestors, attacks on government infrastructure by extremist groups such as ISIL, etc. all fall into this category. In 1990, Chinese hackers attacked U.S. government sites in response to the purportedly accidental bombing of a Chinese embassy.
Social and Cultural
[edit | edit source]Socially-motivated cyber-attacks typically stem from socio-cultural conflict, which within a culture tends to stem from competition between individuals or groups over incompatible goals, scarce resources, or power. Conflicts between different cultures — cross-cultural conflict — such as the Israeli-Palestinian or Taiwanese-Chinese conflicts can also spawn socially motivated cyber-attacks[45]
Economic
[edit | edit source]Economically-motivated attacks can be motivated by the economic situation of the attacker — in the same capacity that someone may rob a gas station if they are broke — or by individuals', nations', or groups' frustration with governments or perceived corporate greed. The former includes attacks on financial institutions, ransom-ware attacks, or phishing for individual consumers' banking information, and typically aims to leverage some form of economic gain for the attacker, while the latter includes attacks on stock markets, corporations, and other global financial institutions for the sake of doing damage. The former is more common amongst individuals, while the latter is commonly perpetrated by groups or governments[46].
Espionage attacks are often split between the political and economic categories, but tend to be grouped with the latter. These attacks are typically committed by states, with the target being other states, and garner useful scientific, strategic, or economic information. Prior examples of this kind of attack include the 2003 Titan Rain incident, where Chinese actors successfully accessed government databases in the United States and United Kingdom, including N.A.S.A.'s, and procured aviation vehicle designs and flight-planning software[47].
Impact on Business
[edit | edit source]The downtime caused by attacks may harm the business's productivity, revenue, financial performance, and damage the companies reputation. The impact on business may range from low to extreme impact. For example, downtime that has a minor impact on business may mean that a minimal amount of systems are affected. While on the other side of the coin is the extreme impact on business, the company's future is at stake, and the cost of recovery is inconsequential. The following is a list of the costs of downtime:
- Cash flow: The day to day cash flow would come to a halt if the company is heavily reliant on computer systems to perform business processes.
- Loss of reputation: For companies that provide critical services, downtime of their services can significantly damage their relationship with their customers and supporters.
- Stock price: A prolonged downtime can have a negative effect on a companies stock prices especially if this downtime is frequent.
- Loss of future earnings: A halt on production along with an unfavorable reputation can affect potential customers as well as current customers which then leads to a loss of future earnings.
- Legal Impacts: Some companies may have legal and regulatory responsibilities tied to their services. A breach can inadvertently cause a company to become uncompliant with some of these regulations.
- Industry Specific: In some industries such as the healthcare industry, downtime can affect something as crucial as patient lives.
A company can perform a Business Impact Analysis (BIA) to determine and evaluate these risks in the case of an attack and be better prepared for them. While downtime can become the main priority for a company, the next steps are to ensure that their system's security are more robust than they were before. The response and repairs of attacks can become costly for companies. This is the case regardless of how major or minor the attack is. If any vulnerabilities are found it is expected to have these vulnerabilities mitigated. The following is a list of possible costs of attack response:
- Hiring third-party businesses to identify risks and create security protocols or customizable solutions.
- Regular testing and monitoring.
- Buying protective software/hardware (eg. Antivirus).
- Upgrading systems or overhauling procedures.
Prevention and Detection
[edit | edit source]Prevention
[edit | edit source]Firewalls
[edit | edit source]There are many tools to prevent a cybercrime from happening. A firewall guards the company's network from outside intrusion, and prevents employees from accessing prohibited sites. Intrusion prevention systems prevent attacks by blocking viruses and other threats from getting into the network. Antivirus software prevents viruses from infecting a computer by scanning for virus signatures. For antivirus to be effective it must be up-to-date and uniformly deployed across the enterprise.
Intrusion Prevention Systems (IPS)
[edit | edit source]These technologies help prevent unauthorized access to networks and systems by monitoring and filtering incoming and outgoing traffic based on predefined security rules.[48]
Antivirus and Anti-Malware Software
[edit | edit source]These tools help prevent malware infections by detecting and removing malicious software from systems before they can cause harm.
These tools employ signature-based and behavioral detection techniques to identify and remove malicious software from systems.
- Antivirus software: Scans for known malware signatures.
- Anti-malware software: Detects and neutralizes novel or zero-day threats that exhibit suspicious behavior.
Access Controls
[edit | edit source]Rigorous access control mechanisms are essential for safeguarding sensitive data and systems.
User authentication mechanisms: Verify the legitimacy of user identities before granting access (e.g., passwords, multi-factor authentication (MFA), biometrics).
Role-based access control (RBAC): Restricts access privileges based on a user's role within the organization.
Principle of least privilege: Grants users the minimum level of access required for their specific function.[49]
Encryption
[edit | edit source]Data encryption plays a vital role in protecting sensitive information, both at rest (stored on devices) and in transit (transmitted across networks).
Encryption algorithms scramble data using encryption keys, rendering it unreadable to unauthorized parties.
Patch Management
[edit | edit source]Software vulnerabilities can be exploited by cybercriminals to gain unauthorized access to systems.
A robust patch management program ensures timely installation of security patches for operating systems and applications, minimizing the potential for attackers to leverage these vulnerabilities.
Security Awareness Training
[edit | edit source]Educating employees and users about cybersecurity best practices is an essential preventive measure. Training programs should raise awareness of common cyber threats[50]
- Phishing emails
- Social engineering tactics
- Malware attacks
- Educated users can identify suspicious activity and avoid falling victim to these malicious tactics.
Detection
[edit | edit source]Intrusion Detection Systems (IDS)
[edit | edit source]Intrusion prevention systems and intrusion detection systems are software or hardware that monitor system resources. It identifies possible intrusions into the system from either within or outside of the organization. There are three types of intrusion systems:
- NIDS (Network Intrusion Detection System) identifies intrusions through network traffic and monitors multiple hosts.
- HIDS (Host-based Intrusion Detection System) identifies intrusions by reviewing host activities.
- SIDS (Stack-based Intrusion System) examines packets as they pass through the TCP/IP stack.
SIEM (Security information and event management)
[edit | edit source]Another tool that can be used in addition to antiviruses and intrusion detection/prevention systems are SIEM or system information and event management. SIEMs take in input and output security alerts and reports
SIEMs can be used to analyze suspected malware incidents and validate that malware was used in any incident. It is important to be able to identify if an attack occurs and what the weapon of attack was with this information one may be able to identify what hosts were infected by malware. This will lead to the host undergoing the appropriate containment, eradication, and recovery actions.[51]
SIEMs assist in this process due to its functionality. SIEMs collect logs from various devices and store the information. SIEMs can provide real time monitoring and incident management by collecting information from the network, security devices, systems, and applications
Functions of SIEM
- Log Consolidation
- Brings all logs to a server for storage
- Threat Correlation
- AI can be used to sort through saved logs and help identify attackers
- Workflow
- Helps track incidents recorded in logs
- Reporting
- Provides enterprise report for compliance purposes[52]
Endpoint Detection and Response (EDR)
[edit | edit source]EDR solutions focus on monitoring endpoints (e.g., desktops, laptops, servers) for suspicious activities.[53]
These tools analyze endpoint behavior for anomalies such as:
- Unusual file access attempts
- Unauthorized system modifications
- Suspicious network connections
EDR can detect and respond to potential threats on individual devices, offering a more granular level of security compared to traditional network-based detection methods.
Log Monitoring and Analysis
[edit | edit source]System logs record security-related events within a system. Regularly monitoring and analyzing these logs for unusual or unauthorized activities can uncover potential security incidents.[54]
Security personnel can identify suspicious events such as:
- Failed login attempts
- File modifications outside of business hours
- Unauthorized access attempts
Forensic Analysis Tools
[edit | edit source]In the event of a security breach,[55] forensic analysis tools are crucial for investigating the incident. These tools enable investigators to collect and analyze digital evidence from compromised systems. Gather evidence for potential legal proceedings.
Forensic analysis helps determine:
- The cause and extent of the attack
- The attacker's techniques
Incident Response Plans
[edit | edit source]Having documented incident response plans in place ensures a coordinated and efficient response to security incidents.[56]
These plans outline the steps for:
- Identifying
- Containing
- Eradicating
- Recovering from security breaches
Security Audit
[edit | edit source]A company's network is a means of communication and sharing of information. However it comes under attack everyday by professional or novice hackers with intention to use company information or databases for their own fortune. But it is not compromised only by external individuals but also sometimes by personnel present in the company.
Audits in cybersecurity are an essential measurement of information security compliance. An audit helps measure the confidentiality, integrity and availability of information in an organization. An information system audit helps ensure the effective, efficient, secure and reliable operation of the information technology that is critical to an organization's success. An audit will determine the areas of improvement for security of information. Audits are done to ensure the organization has implemented controls and that they are effective.
In any given audit, the auditor should have a good understanding of the internal controls already in place. This helps the auditor determine the tests that they would be performing. The auditor should be aware of any factors that can affect their audit. For a successful audit to take place, there are many things the auditor should obtain an understanding of. These include the control environment, the risk assessment process, the information system, the control activities, and the monitoring of internal control. There are a number of steps that need to be performed in order to complete a security audit. For example:
- Define audit
- Define possible threats
- Discussion (interviews)
- Technical Investigation
- Report Presentation
- Post Audit Actions and Recommendations
Types of Audits
[edit | edit source]Self Audit (Informal Audit): Every company has few servers providing services to the company. To monitor these processes every company develops some type of self-audit process to follow on a regular basis. Some companies have software to monitor all the process and then register entire logs to be evaluated later by professionals. Based on these audit results if a bad or incorrect event is detected, you can even have the event undone and the initiator’s account even locked out. The collectors will send all the daily logs to a consolidator once a day where you will be able to create numerous reports and graphs surrounding your security events. You can also use this for trends and analysis.
Information Technology Audits The purpose of an internal audit is to provide operations management with an independent review of the adequacy and effectiveness of the operations’ internal controls.The IT audit is basically external auditing in which external auditors will be hired to perform all the required auditing operations. These auditors contact the internal auditing department and make their auditing requirements known to the company. At the conclusion of the audit, an oral and written report are conducted with the management. At this time the company must plan actions to take in response to the report or decide whether they wish to assume the risks involved. Once auditing is done and the report is presented, all the concerned individuals should meet to discuss what next steps are required to ensure the safety of the company's assets.
Emerging Threats and Future Outlook
[edit | edit source]Emerging trends in cybersecurity and Future Outlook
This is where continuous challenges and opportunities to the field of cybersecurity currently develop. In a fast-growing world with ever-evolving technology, new vulnerabilities have just come up that would require equally new solutions for mitigation. The view was preventive, considering what might happen in the future with the latest advancement in defense mechanisms. Let us have a look at the latest advances within the cybersecurity field to date and a preview for the next few years of defense of our digital assets.
One of the key shifts that have happened in the landscape of cyber threats can be defined through a change in concerns: from data breaches and financial gain toward inflicting business disruption and reputational damage. One recent survey indicated that most respondents now believe that cyber attackers' efforts are focused on business disruption and inflicting reputational damage. These two factors emerge now as the topmost two worries that then draw attention to a new wave of cyber threats that have in place challenges not only in the context of data loss.
Some of the factors that could drive this shift of tactics by attackers include: disruption that is no less harmful or even more harmful than data theft to the operations of a company. A well-timed cyberattack can bring down critical systems, stall production lines, and result in financial damage. In addition, a tarnished reputation may impact the company for years. Such a cyberattack can lead to gargantuan business and customer trust losses in case sensitive customer data is exposed or the trust in the brand is compromised. Leading organizations are riding the wave of digital transformation with the use of the latest, state-of-the-art technologies. By integrating new technologies into incumbent systems, they enable also a double-edged sword. The multi-valued opportunities are appealing but enhance complexity in IT environments and their vulnerability to cyber risks. Indeed, leaders are in the perennial struggle to get the right balance—maximize the benefits from new technologies, minimize associated cyber risks. Here, we delve into the key emerging trends shaping the cybercrime landscape, along with the challenges they pose for the future:
Supply Chain Attacks
[edit | edit source]Another tendency that this work reveals is supply chain attacks, that is, an attack of supply chain from an attacker who is trying to compromise the integrity of products and services being offered. Recent happenings, like the SolarWinds breach, epitomize the dire consequences that come with such attacks, attacks that have the potential of bringing businesses to their knees.A group of hackers breached the software development process of SolarWinds, one of the biggest software vendors for managing IT shops. In that manner, they managed to infect its Orion platform with malicious code and subsequently distribute it to thousands of customers, among them governmental agencies and private companies. In the 2022 edition of this report, almost 40% of the surveyed companies got hurt by cyberattacks on their partners, say, suppliers or customers. Attacks brought disturbances not only by themselves but also happened without the companies themselves being the target—their injury was like "collateral damage" in somebody else's cyberwar. Naturally, therefore, almost all the respondents are anxious about the cybersecurity strength of their partners, especially those with access to their data. Supply chain risk is a concern for industries at large and can disrupt critical services.
The report also outlines the possibility of conflict of interests in companies. In such a case, security chiefs (CISOs) report to IT chiefs (CIOs), who may be function-happy in making the budget. However, the report says most CIOs who had undergone severe cyber-attacks tend to become security-conscious. This may indicate the general corporate culture and appreciation of cyber risks at the top. The solution may lie in structuring the right incentives, irrespective of the reporting lines.
The report concluded by stating that better cyber governance practices would be required, with principles developed by bodies such as the World Economic Forum and the National Association of Corporate Directors to allow boards to manage cyber risks.
Advanced Development
[edit | edit source]Beyond the ever-challenging digital threat landscape lies the most disturbing trend: the proven sophistication that cyberattacks have been taking. In a constant iteration process, the attackers further improved their techniques, improved their approaches, and breached these security systems to exfiltrate sensitive data or disrupt important services. The factors driving this change are numerous: those from potent arsenals of hacking tools at any group's disposal, through proliferation of online forums fostering wider collaboration among cybercriminals, to the more troubling rise of nation-state-sponsored hacking groups.
Future Outlook
[edit | edit source]Embracing security Awareness
[edit | edit source]Everyone needs to be aware and involved in building a good security culture. The study finds that increasing awareness among employees regarding the existence of cyber threats is going to be the most influencing aspect in increasing cyber resilience. An informed workforce, enabled to manage cyber risks, strengthens the security position for the organization as a whole. It calls on leaders to empower business leaders further by holding them to account for operational security measures. For example, making security exceptions that require justification by senior executives can shift the mindset towards valuing security. All along, the security team plays a critical role in helping by giving insights and solutions. For instance, considering the vulnerabilities to which the HR team is exposed by using unsecured attachments, the security team may recommend such solutions as secure portals in which to plug the leaks before they cause damage. Good security leadership includes advising and embedding practice for cyber risk management with other business departments. Good security leaders make sure that the cybersecurity requirements are integrated into business unit KPIs, in order to assure enforcement and incentivization towards secure behavior across the organization.
Effortless communications
[edit | edit source]Rising Cybersecurity Anxieties: This year, there is a larger percentage of security leaders who are anxious about the post-cyberattack recovery of their organization compared to last year's (17%). What is even more interesting is the anxiety in that regard of business leaders, whose worry in that category grew from 16% to 27%. Business leader awareness is growing, and it's probably due to a better understanding of the consequences of cyber attacks—from loss of operation to loss of business partners and reputation.
The Challenge of Communication
[edit | edit source]In a worrying parallel that is reaching near parity between security and business leaders, the leaders are impeded by a communication problem. Those security leaders who do bridge the gap are expert in translating technical data into clear and meaningful information for the business leader. This difficulty in communication is the result of, among other things, the challenge of translating abstract cyber threats into concrete operational risks. Of course, a word as simple as 'ransomware' will be very easy to understand, but the details of how sophisticated cyber-attacks actually run, especially targeting certain business assets and resources, are much harder to explain.[57]
References
[edit | edit source]- ↑ Moule, Ryan (February 2017). "Criminal Use of Technology". obo. doi:10.1093/obo/9780195396607-0211. Retrieved 2024-04-23.
- ↑ Grivna, T (7 December 2019). "Attacks on the confidentiality, integrity and availability of data and computer systems in the criminal case law of the Czech Republic". Digital Investigation.
- ↑ Dutt, D; Pandley, S; Arora, S; Tripathi, M (2022-05-06). "Need for Cyber Security Tools and Knowledge". International Journal of Research in Engineering, Science and Management.
- ↑ Ryan, P. S (2004). "War, peace, or stalemate: Wargames, wardialing, wardriving, and the emerging market for Hacker Ethics".
- ↑ Iftikhar, S (15 January 2024). "Cyberterrorism as a global threat: A review on repercussions and countermeasures".
- ↑ "GovInfo". www.govinfo.gov. Retrieved 2024-04-22.
- ↑ "Identity Theft and Assumption Deterrence Act". Federal Trade Commission. 2013-08-12. Retrieved 2024-04-22.
- ↑ "GovInfo". www.govinfo.gov. Retrieved 2024-04-22.
- ↑ "U.S.C. Title 15 - COMMERCE AND TRADE". www.govinfo.gov. Retrieved 2024-04-22.
- ↑ "Budapest Convention - Cybercrime - www.coe.int". Cybercrime. Retrieved 2024-04-22.
- ↑ "African Union Convention on Cyber Security and Personal Data Protection". April 22, 2024.
{{cite web}}:|first=missing|last=(help) - ↑ "Commonwealth model law promises co-ordinated cybercrime response". Commonwealth. Retrieved 2024-04-22.
- ↑ The Commonwealth Office of Civil and Criminal Justice Reform (2017). Model Law on Computer and Computer Related Crime. Commonwealth Secretariat.
- ↑ OEA (2009-08-01). "OEA - Organización de los Estados Americanos: Democracia para la paz, la seguridad y el desarrollo". www.oas.org (in Spanish). Retrieved 2024-04-22.
- ↑ Tavani, Herman T. Ethics and Technology: Controversies, Questions, and Strategies for Ethical Computing. Wiley, 2016.
- ↑ a b c Norwich University Online (2017, February 13). Who Are Cyber Criminals? Retrieved from Norwich University Online: https://online.norwich.edu/academic-programs/resources/who-are-cyber-criminals
- ↑ a b c d John, Edwards “The top 10 kinds of Cybercriminals” (September 2007) accessed 4/26/2016 at http://www.itsecurity.com/features/top-10-cybercriminals-091007/
- ↑ https://www.wired.com/2015/01/german-steel-mill-hack-destruction/.
- ↑ Tripwire Guest (Dec 5, 2018). "What Cyberstalking Is and How to Prevent It". Tripwire.com.
- ↑ John Sammons; Michael Cross (2017). "Cyberstalking".
- ↑ Chance Carter (November 16, 2021). "An Update on the Legal Landscape of Revenge Porn".
- ↑ Jessica Goldstein (October 29, 2020). "'Revenge porn' was already commonplace. The pandemic has made things even worse".
- ↑ Perry Robinson (April 5, 2022). "FBI warns of sextortion scams, victim shares terrifying story".
- ↑ Nathan Daniels (April 21, 2022). "What is Sextortion? How to Prevent Online Blackmailing".
- ↑ https://pubmed.ncbi.nlm.nih.gov/20852011/
- ↑ https://www.govtech.com/security/Hackers-Vandalize-Minnesota-Government-Websites.html
- ↑ TLP White, "An introduction to Malware" Page 4 accessed 4/26/2016 at https://www.cert.gov.uk/wp-content/uploads/2014/08/An-introduction-to-malware.pdf
- ↑ Gunter Ollmann, "The Phishing Guide" Strategy IBM Internet Security Systems Page 20 accessed 4/26/2016 at http://www-935.ibm.com/services/us/iss/pdf/phishing-guide-wp.pdf
- ↑ “What Is Whaling? - Definition from Techopedia.” Techopedia.com at https://www.techopedia.com/definition/28643/whaling/
- ↑ RockYou Hack: From Bad To Worse at https://techcrunch.com/2009/12/14/rockyou-hack-security-myspace-facebook-passwords/
- ↑ What Mr. Robot can teach us all about security at https://www.kaspersky.com/blog/mr-robot-safety-tips/19713/
- ↑ a b Qijun Gu and Peng Liu, "Denial of Service Attacks" Texas State University & Pennsylvania State University Page 4 accessed 4/26/2016 at https://s2.ist.psu.edu/paper/ddos-chap-gu-june-07.pdf
- ↑ Frankenfield, Jake. “Eavesdropping Attack.” Investopedia, Investopedia, 12 Mar. 2019 at https://www.investopedia.com/terms/e/eavesdropping-attack.asp/
- ↑ a b Tom's Guide Staff “Drive-By Downloads: How They Attack and How to Defend Yourself” (March 06, 2014) accessed 4/25/2016 at http://www.tomsguide.com/us/driveby-download,news-18329.html
- ↑ “Web Application Attack: What Is It and How to Defend against It?” Acunetix at https://www.acunetix.com/websitesecurity/web-application-attack/
- ↑ “Sql Injection: Vulnerabilities & How To Prevent Sql Injection Attacks.” Veracode, 25 Apr. 2019, at https://www.veracode.com/security/sql-injection/
- ↑ US-CERT. "SQL Injection" (PDF).
- ↑ “Cross-Site Scripting (XSS) Tutorial: Learn About XSS Vulnerabilities, Injections and How to Prevent Attacks.” Veracode, 18 Apr. 2019 at https://www.veracode.com/security/xss/
- ↑ a b c d Easttom (2022). Digital forensics, investigation, and response. Jones & Bartlett Learning.
- ↑ Randall Dipert (2010). "The Ethics of Cyberwarfare". Journal of Military Ethics.
- ↑ a b Maxwell Montgomery (2019). "Proliferation of Cyberwarfare under International Law: Virtual Attacks with Concrete Consequences" (PDF).
- ↑ William Banks (2017). "Cyber Espionage and Electronic Surveillance: Beyond the Media the Media Coverage".
{{cite journal}}: Cite journal requires|journal=(help) - ↑ Kumar, Sumeet. "Approaches to Understanding the Motivations Behind Cyber Attacks." Department of Electrical and Computer Engineering, Carnegie Mellon University, 2013. Accessed 26 April 2020 at http://casos.cs.cmu.edu/publications/papers/2016ApproachestoUnderstanding.pdf. Invalid
<ref>tag; name "kumar" defined multiple times with different content - ↑ Ghandi et al. "Dimensions of Cyber-Attacks: Cultural, Social, Economic, and Political." University of Nebraska, 07 March 2011. Accessed 26 April 2020 at https://www.academia.edu/21848823/Dimensions_of_Cyber-Attacks_Cultural_Social_Economic_and_Political. Invalid
<ref>tag; name "ghandi" defined multiple times with different content - ↑ Ghandi et al. "Dimensions of Cyber-Attacks: Cultural, Social, Economic, and Political." University of Nebraska, 07 March 2011. Accessed 26 April 2020 at https://www.academia.edu/21848823/Dimensions_of_Cyber-Attacks_Cultural_Social_Economic_and_Political.
- ↑ Konraadt et al. "Phishing: An economic analysis of cybercrime perpetrators." Computers & Security, Volume 58, May 2016. Accessed 26 April 2020 at https://www.sciencedirect.com/science/article/pii/S0167404815001844. Invalid
<ref>tag; name "konraadt" defined multiple times with different content - ↑ "Titan Rain." Council on Foreign Relations. Accessed 26 April 2020 at https://www.cfr.org/interactive/cyber-operations/titan-rain.
- ↑ "What is an Intrusion Prevention System (IPS)? | IBM". www.ibm.com. Retrieved 2024-04-22.
- ↑ Marvin, Michael (2023-10-12). "Securing Your Digital Eco-System: The Role of Access Control in Network Security". Portnox. Retrieved 2024-04-22.
- ↑ "The Importance of Cyber Security Awareness Training". www.elev8me.com. 2023-07-31. Retrieved 2024-04-22.
- ↑ Souppaya, Murugiah (July 2013). "Guide to Malware Incident Prevention and Handling for Desktops and Laptops" (PDF).
{{cite web}}: More than one of|first1=and|first=specified (help); More than one of|last1=and|last=specified (help) - ↑ Zope, Anita; Vidhate, Amarsinh (April 2013). "Data Mining Approach in Security Information and Event Management" (PDF).
{{cite web}}:|first3=missing|last3=(help); line feed character in|title=at position 55 (help) - ↑ "What is EDR? Endpoint Detection & Response Defined". crowdstrike.com. Retrieved 2024-04-22.
- ↑ Kent, Karen. "Guide to Computer Security Log Management" (PDF). NIST.
- ↑ "What is digital forensics and incident response (DFIR)?". fieldeffect.com. Retrieved 2024-04-22.
- ↑ "Incident Response Plan: How to Build, Examples, Template". Security. Retrieved 2024-04-22.
- ↑ "Global Cybersecurity Outlook 2023". World Economic Forum.
<ref> tag defined in <references> has no name attribute.[1]
[2]
[3]
[4]
[5]
[6]
[7]
[8]
- ↑ Malware 101 : What is a Virus?? at https://us.norton.com/internetsecurity-malware-what-is-a-computer-virus.html
- ↑ Computer Worm, Margaret Rouse Computer Worm?? at https://searchsecurity.techtarget.com/definition/worm
- ↑ Trojan Horse, Margaret Rouse-Trojan Horse at https://searchsecurity.techtarget.com/definition/Trojan-horse
- ↑ MITM, Man in the Middle Attack (MITM) at https://www.incapsula.com/web-application-security/man-in-the-middle-mitm.html
- ↑ DDoS, Distributed Denial of service (DDoS) at https://www.incapsula.com/ddos/denial-of-service.html
- ↑ Ransomware, Ransomware - What is it all about? at https://www.malwarebytes.com/ransomware/
- ↑ RockYou Hack: From Bad To Worse at https://techcrunch.com/2009/12/14/rockyou-hack-security-myspace-facebook-passwords/
- ↑ What Mr. Robot can teach us all about security at https://www.kaspersky.com/blog/mr-robot-safety-tips/19713/
