The Computer Revolution/Internet/Hackers
Hacking
[edit | edit source]What is Hacking?
Hacking means the act of breaching into a computer or network. Hacking can occur two ways, it can occur in person if the hacker has physical access to the computer or network or through the Internet which tends to be the most common way. It doesn't matter how the hacking occurs because it is still illegal. In the United States and various other countries the act of hacking is considered a criminal offense. Some of the illegal acts performed during hacking are stealing important data like credit card information, corrupt a computer system, and create and disperse spam. Hacking has become quite easier due to the growing wireless network popularity, which allows hackers to gain unauthorized access to a wireless network by simply being a couple a hundred feet from an unsecured wireless access point.
Hacking is not only a concern for the average computer user, but can be a threat to national security in the U.S. There are so many systems that are run for security purposes in the U.S with the use of Internet connection that a hacker could be able to get into a major government system. This has bought an increase risk in cyberterrorism. There are many things that could be affected by cyberterrorism that inculde: banks, airlines, stockmarkets, and big systems like the nation’s power grid. With the risk of cyberterrorism increasing the President has made it an important task to work on improving cybersecurity and assigning a task force just for this specific problem.
Morley, Deborah and Parker, Charles. Understanding Computer: Today and Tomorrow 13th Edition. Course Technology: Boston, MA, 2011
-
Hacking in Progress
Why is any Computer System a Target for Hackers?
The majority of hackers conduct broad-based, indiscriminate probes of any and all computers connected to the internet. Targeted attacks against large businesses or government entities are far less common, but garner a lot of attention. This is why it is important for any computer user to take security measures that lessens the ability of hackers to steal the resources of a system. The resources of a computer system include the files and sensitive data stored on the computer, AND the computer itself. Hijacked computers can be just as valuable as stolen data due to their raw computing power and internet connections. Any hijacked computer is a worthy addition to the hackers' arsenal of zombie computers and botnets. Hackers will use hijacked computers to send out spam and emails containing viruses and other malware, disseminate illicit materials or take part in hacking attacks in other computer networks. In summary, hackers may use hijacked systems to perform the following illegal actions.
- • To send unwanted spam.
- • To engage in click fraud (A type of Internet crime that occurs in pay-per-click online advertising when a person, automated script or computer program imitates a legitimate web user clicking on an ad, for the purpose of generating a charge per click).
- • To send malicious emails to your friends, family and clients. In this way hijacked systems function as a spreader of viruses, malware and spyware.
- • To install a key logger and capture every username and password typed; they can then use your computer to log into your financial accounts; conduct transactions and perpetrate electronic theft.
- • To mount a coordinated attack on select targets, such as banks or governmental institutions.
- • To sniff out other traffic on your network. Any networked computer can be used to "sniff" out and copy traffic on your network, such as the network traffic from credit card or other data processing servers.
- • To use your computer to send out data through the internet. In extreme cases, they can use it as a hub to exchange illicit, illegal or stolen materials, as a relay station to hide the true origin of certain content or as a message board for shady activities.
Computer Training & CCNA Networking Solutions. n.d. Web Site. 11 October 2012. <http://www.orbit-computer-solutions.com/Network-Security.php>.
Spam
[edit | edit source]What is Spam? Spam is the abuse of electronic messaging systems to send unsolicited, undesired bulk messages. While the most widely recognized form of spam is e-mail spam, the term is applied to similar abuses in other media.There are two main types of spam, and they have different effects on Internet users. Cancellable Usenet spam is a single message sent to 20 or more Usenet newsgroups. (Through long experience, Usenet users have found that any message posted to so many newsgroups is often not relevant to most or all of them.) Usenet spam is aimed at "lurkers", people who read newsgroups but rarely or never post and give their address away. Usenet spam robs users of the utility of the newsgroups by overwhelming them with a barrage of advertising or other irrelevant posts. Furthermore, Usenet spam subverts the ability of system administrators and owners to manage the topics they accept on their systems.Email spam targets individual users with direct mail messages. Email spam lists are often created by scanning Usenet postings, stealing Internet mailing lists, or searching the Web for addresses. Email spams typically cost users money out-of-pocket to receive. Many people - anyone with measured phone service - read or receive their mail while the meter is running, so to speak. Spam costs them additional money. On top of that, it costs money for ISPs and online services to transmit spam, and these costs are transmitted directly to subscribers.[1]
E-mail spam is a subset of spam that involves sending nearly identical messages to thousands (or millions) of recipients by E-mail.
- Tips for Fighting Spam:
- Delete messages from people you do not recognize.
- Never Reply to a spam message
- Opt out of anything you don't want to receive
- Use spam filters
- Fight back by reporting spammers.
snoop
[edit | edit source]Spoof
[edit | edit source]when we are talking about spoofing in IT, we refer to counterfeit an identity. It is sometimes used for searching or malicious uses.
There are different types of spoofing. The well known type of spoofing is IP spoofing.However, there are others like ARP spoofing, DNS spoofing, WEB spoofing, and Email spoofing.
IP spoofing is a technique that is used by hackers to get an original IP address by creating IP packets. This consists in sending messages from untrusted source, but who receives the message thinks that it comes from trusted host.
http://www.webopedia.com/TERM/I/IP_spoofing.html
ARP spoofing is a hacking methodology to forge the content of an ARP table on an Ethernet (LAN) by creating or changing the ARP table. The LAN works with MAC addresses and the ARP protocol converts IP address to MAC address in order to establish communication between computers. If the wrong information is saved into the ARP table,it is because the computer believes that it is valid.
http://www.codeproject.com/internet/winarpspoof.asp
DNS spoofing is a forgery of the Domain Name Service to generate a request to Server.
WEB spoofing is when hackers can make an exact copy of the whole World Wide Web (Web page)with the objective to acquire and monitor information (e.g. passwords or account numbers) of that web page. In summary, web spoofing is a forgery of a web page where hackers can control and manipulate the whole private information.
http://www.cs.princeton.edu/sip/pub/spoofing.html
E-mail spoofing email spoofing method allows hackers sending emails from a fake email that they got from a personal or entity email. Spammers use this technique because they want to send messages to thousands and thousands users. Those emails seem to have been originated from a source that does not exist and those emails are called "junk or spam" emails.
http://www.hbpsystems.co.uk/blog/email-spamming,-spoofing-and-how-to-prevent-it/
Phishing & Pharming
[edit | edit source]Phishing (pron. "fishing") and Pharming (pron. "farming") have nothing to do with activities related to fish species or cultivating agricultural lands, although there is a distinctive play on the terminology and concepts associated with farming and fishing.
Hackers involved in phishing and pharming are undertaking illegal activities for the purpose of getting personal/confidential information from computer users (i.e., personal, financial or password data). Phishers "bait their hooks," "cast their net" and "fish" for information in the hope of "luring" and ultimately "catching" identity victims "hook, line and sinker" into a trap that leads the user into divulging their financial and/or password information. Likewise, pharmers are "harvesting" personal information, but generally operate on a less obvious level than phishers and, as a result, pharming has been referred to as "phishing without a lure" (http://www.cyveillance.com/web/online_risks/phishing.htm Retrieved Sept 19, 2006).
Pharming is a type of phishing and phishing is a short form for "password harvesting fishing." In both cases, computer users are targeted. In pharming, they are directed or redirected to bogus or impostor web pages. Phishers, however, operate on a smaller scale than pharmers and rely on e-mail as their solicitation method. So, phishers tend to "... approach their targets one by one," but pharmers, involve many victims at a time and therefore "... threatens to reel in entire schools of victims" (http://www.wired.com/news/infostructure/0,1377,66853,00.html Retrieved Sept 28, 2006). Pharming combines such threats as viruses and spyware plus such things as domain spoofing and DNS (Domain Name System) poisoning or domain hijacks to redirect users (http://www.theregister.co.uk/2005/01/31/pharming/ Retrieved Sept 19, 2006). The more highly targeted version of phishing is called "spear-fishing" which utilizes e-mails to target users in a specific company by appearing to originate from within -- oftentimes from HR or the IT department or someone known to the user (http://www.businessweek.com/magazine/content/05_28/c3942014_mz003.htm#ZZZDLBOMKAE Retrieved Sept 19, 2006 & http://www.wordspy.com/words/spear-phishing.asp Retrieved Sept 19, 2006). Added to this mix is "puddle phishing" which targets smaller companies and targets -- often customers of smaller financial institutions (http://www.wordspy.com/words/puddlephishing.asp Retrieved Sept 19, 2006).
Phishing, brand spoofing and carding are one and the same. Phishing, a variant of "fishing," is "Web lingo" coined by hackers. The use of "ph" in place of the letter "f" appears to be a favorite among hackers. Their first substitution of letters appears to have been adopted in the late 1960s when they referred to themselves as "phone phreaks" or telephone system hackers (http://www.wordspy.com/words/phishing.asp Retrieved Sept 19, 2006). Today's variant on this is "phone phishing" -- also called pretext calling -- which appears to be more damaging to victims than activities of the "phone phreaks" in the pre-computerized world and is less detectable than Internet phishing because the victim is not directly involved and, in fact, is completely unaware someone is gaining access to their personal data via customer service representatives (http://www.wordspy.com/words/phonephishing.asp Retrieved Sept 19, 2006).
Scamming practices definitely pre-date the computer and so too does phishing, but the advent of new technology and increasing use of this technology for more business transactions has led to a "wide potential profit zone" for the more computer-savvy cyber-criminals of today (http://www.wired.com/news/infostructure/0,1377,66853,00.html Retrieved Sept 19, 2006). Deceptive phishing scams for the purpose of identity theft, although illegal, can be very lucrative, so who says crime does not pay today? It certainly can be costly for the targeted party(ies) subjected to huge financial and identity rip-offs, often in need of costly legal assistance (http://www.computerworld.com/securitytopics/security/story/0,10801,89096,00.html Retrieved Sept 19, 2006 & http://www.csoonline.com/read/100105/pharm.html Retrieved Sept 19, 2006).
Computer scams have added to personal and business costs (i.e., in time, effort, money and legal challenges), has led to the creation of a vast number of IT related security jobs and resulted in numerous security businesses -- in surveillance, computer security and anti-phishing software development. It maybe difficult to protect oneself from some forms of pharming and phishing, but there are some basic steps which will help avoid the more obvious traps. One can get advice and tips from various on-line sites such as http://www.businessweek.com/technology/content/may2004/tc20040524_8133_tc024.htm (Retrieved Sept 19, 2006). In addition, there have been many social (e.g., user training), legal and technical responses (e.g, anti-phishing software) developed and adopted in an effort to protect users, including the use of spam filters and verification tools (http://en.wikipedia.org/wiki/Phishing Retrieved Sept 19, 2006).
The best defense advice is 'Beware, Be Alert and Be Informed.'
Adware
[edit | edit source]Definition: "Any software application in which advertising banners are displayed while the program is running is called Adware. And any software that sends data back to a third party - WITHOUT ASKING the user - is Spyware"(http://www.adware.info/).
Have you ever noticed when you are on a particular website of your interest and all of a sudden an advertisement pops up and disrupts your page, not to mention wastes your time? This is Adware. Companies will offer you free software, while advertising on your computer. (https://www.microsoft.com/windowsxp/using/security/expert/honeycutt_spyware.mspx)What a great way for companies to maximize their advertising demographic.
Tips to stop from being an adware victim
Don't be a "yes or no" clicker - When popups come onto your screen (which annoy you and slow you down) take the extra 10 seconds to read it. That way you aren't downloading anything you do not want. This could be adware and could create a bigger problem. It is tempting to get frustrating and click something to make the box disappear. Take your time.
Caution - When offered a free download or program - In this material world today where anything and everything comes with a dollar sign attached, it is understandable that we jump at the chance to take anything that is free. In the world of software downloading, this free software gift may often come with built in adware and will download onto your computer creating constant advertising and popups without you even knowing you actually created the problem. Companies make their money off of this free advertising. (https://www.microsoft.com/windowsxp/using/security/expert/honeycutt_spyware.mspx)
Webjack
[edit | edit source]What is webjacking? Webjacking is when hackers take web-pages that you frequent and then take you to other websites which could be pornography or websites that are used to scam people.
(http://www.wordspy.com/words/Webjack.asp)
How hackers webjack your computer Hackers will go into your computer and place a trojan, on your computer or server in order to redirect you to websites or steal your files. Another way in which hackers try to webjack your computer is by sending you an email, which looks like the exact site to which you are registered with for example your bank. This email will ask you to update your personal information, example names, addresses, credit card or bank information.
(http://www.onrec.com/content2/news.asp?ID=12167)
Once again these hackers get into your computer by using pop-ups. Webjacking is a form of criminal activity and can be very dangerous to users. These jackers can copy your webpage domain. A user will type in the correct address to the site they are trying to go to but instead of going to the actual site, they will be redirected to a fraudulent site which is an exact replica of the site they were trying to go to. For example if you were trying to go to your bank website to transfer money onto your credit card. You enter all of your personal information onto that site thinking you are on your bank website, but you are actually on a criminal site giving your bank information and access to your accounts to a hacker.
Webjacking affects customers, businesses and most of all scams many innocent people. Once a business website has been webjacked, the actual business will loose online contact with their customers, which will cause the business to loose many of its customers. But webjacking also affects innocent customers to loose their money.
(http://www.minnesotatechnology.org/publications/magazine/2002/Fall/Webjacked.asp)
If you receive any emails from your bank institution or any other businesses, do not give any of your personal information out. Always call your bank to find out if the email is legitimate.
Webjacking is a new territory for the law, if you find yourself a victim of webjacking there are several steps you should take:
- Contact the legitimate organization whose website has been webjacked. Although they may not be able to compensate you, they need to be aware in order to stop the hacker. - Contact the Uniform Dispute Resolution Policy (UDRP). - Contact the authorities and court systems. You may be able to seek damages based on several laws like Privacy.
http://www.minnesotatechnology.org/publications/magazine/2002/Fall/Webjacked.asp
DoS
[edit | edit source]DoS stands for Denial of Service, and it is a malicious tactic used mainly for demonstrative or abusive purposes. It works by exhausting a server's resources needed to respond to requests for data. This is usually done in the form of sending data requests from false computer addresses, so when the server tries to respond with data, it gets lost and stalls momentarily before disconnecting. When these requests are coordinated in large numbers they can be detrimental to a server's ability to function.
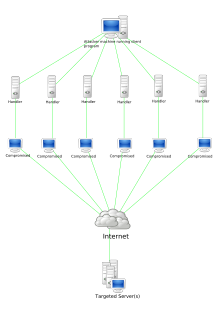
When multiple computers are coordinated into a botnet, the attack is no longer called a DoS attack, rather it is referred to as a DDoS, a Distributed Denial of Service attack.
Hacking Groups and Cyber Attacks
[edit | edit source]According to "Global News", LulzSec is short for Lulz Security. “Lulz” is a variation of the Internet slang “lol” which means “laugh out loud.” Lulz can also be understood as “laughs,” or “amusement.” The group is thought to have formed in May 2011, and were most active in May and June 2011.
Allegedly, LulzSec is an elite organization of hackers that is linked to the online “hacktivist” group Anonymous, as well as the offshoot groups “Internet Feds” and “AntiSec.” LulzSec is most interested in the theft of confidential information, defacing websites, and cyber attacks. They attack businesses, governments and cyber-security firms worldwide, including: Visa, MasterCard and PayPal, government computers in Tunisia, Algeria, Yemen and Zimbabwe, Fox Broadcasting Co. and Tribune Co., Sony Pictures, Public Broadcasting Service (PBS) and the U.S. Senate
Another "hacking group","Anonymous" is described below. According to Wikipedia, a flag conveying symbolism associated with Anonymous. The imagery of the "suit without a head" represents leaderless organization and anonymity.[1] Individuals appearing in public as Anonymous, wearing the Guy Fawkes masks popularized by the comic book and film V for Vendetta.
According to Wikipedia, Anonymous (used as a mass noun) is an Internet meme that originated in 2003 on the imageboard "4chan", representing the concept of many online and offline community users simultaneously existing as an anarchic, digitized global brain.[2] It is also generally considered to be a blanket term for members of certain Internet subcultures, a way to refer to the actions of people in an environment where their actual identities are not known.[3] In its early form, the concept has been adopted by a decentralized online community acting anonymously in a coordinated manner, usually toward a loosely self-agreed goal, and primarily focused on entertainment. Beginning with 2008, the Anonymous collective has become increasingly associated with collaborative, international hacktivism, undertaking protests and other actions, often in retaliation against anti-digital piracy campaigns by motion picture and recording industry trade associations.[4][5] Actions credited to "Anonymous" are undertaken by unidentified individuals who apply the Anonymous label to themselves as attribution.[6]
According to Wikipedia, many websites are strongly associated with Anonymous. This includes notable imageboards such as 4chan, their associated wikis, Encyclopædia Dramatica, and a number of forums.[7] After a series of controversial, widely-publicized protests and distributed denial of service (DDoS) attacks by Anonymous in 2008, incidents linked to its cadre members have increased.[8] In consideration of its capabilities, Anonymous has been posited by CNN to be one of the three major successors to WikiLeaks.[9]

