Lentis/Cyberterrorism and Cyberwarfare
Introduction
[edit | edit source]Cyberterrorism and cyberwarfare involve attacks against information stored on computers and networks with the intention of inflicting harm. With continuing technological advancements, acts of cyberterrorism and cyberwarfare are more prevalent in our world today. As the internet evolved, engineers could not predict the social implications of this new technology. Now governments are developing policies to counteract and prevent these attacks.
History
[edit | edit source]The Zimmermann Telegram
[edit | edit source]
In January 1917 during World War I, Britain intercepted and deciphered an encrypted telegram, the Zimmermann Telegram, from German Foreign Minister Arthur Zimmermann to the German Minister of Mexico. This document proposed a German-Mexican alliance against the United States, where Mexico would regain lost territory in Texas, Arizona, and New Mexico. [1]
Until this point in World War I, the United States was neutral. After the telegram was exposed to American citizens, the United States declared war on Germany on April 6.
Cyberwarfare can be traced to this incident in 1917 that altered the course of World War I. Germany believed that their code was impossible to decode as they sent this sensitive information over an American owned telegraph line. The strength of an encryption relies upon the length of the key to protect valuable information. Military information is protected by 56-64 bits and only lasts minutes to hours. [2] Although modern computer code is more complex than those from the early 1900s, Germany learned that their code was not secure and that with enough motive one can crack any code.
The Morris Worm: The first recognized worm
[edit | edit source]In 1988, Robert Morris created the first self-replicating and self-propagating worm, affecting over 6,000 computers. It did not destroy files or data but clogged the computer's memory until it became unusable. Morris claimed that he was not intending to cause any harm but was simply trying to gauge the amount of internet users. [3]
As the internet was a recent invention , the law had to adjust to the potential social and criminal implications of this new technology. Morris was the first person to be prosecuted and convicted under the Computer Fraud and Abuse Act of 1986. This law was amended to clarify what was considered a crime in this new cyber world and to generalize penalties associated with specific crimes. Before this worm, most people were not concerned with internet security but after the Morris worm, software companies were more aware of flaws in their security systems and took measures to protect themselves against hackers. [4]
Modern Cyberthreats
[edit | edit source]Stuxnet
[edit | edit source]| “ | [O]ne of the great technical blockbusters in malware history. | ” |
—Vanity Fair, April 2011 | ||
The Stuxnet virus is a computer worm found in 2009 in critical infrastructure software systems around the world. It is known as the most sophisticated computer malware to date. Its target was Iranian Uranium enrichment facilities where it damaged two major nuclear facilities in Iran. [5] The United States and Israel are rumored to be responsible for the attack. There is no direct evidence, but diplomatic cables posted on WikiLeaks and other government correspondence support these claims. [6]
Stuxnet attacked the Supervisory Control and Data Acquisition (SCADA) systems. SCADA systems are specialized software used to control industrial infrastructure including nuclear power plants, power grids, train switches, and gas pipelines. These systems are often outdated and not secure. There is little incentive to replace them with more secure software as it would require high costs and intensive planning. [7] There was little concern of another attack on U.S. infrastructure as Stuxnet was too specific and would take major re-engineering to apply to another system. [8] While most of the security gaps that Stuxnet attacked have been patched, the cost of the required resources to reproduce a similar attack is not beyond terrorists organizations' budget with the help of third-parties. Stuxnet proposed to terrorists that cyberattacks are not limited to computers, but also infrastructure that can do real world damage, pushing the world on a cyberarms race. [8]
WikiLeaks
[edit | edit source]WikiLeaks is an organization that collects and disperses sensitive or controversial information from anonymous sources around the world. WikiLeaks has released documents revealing corporate, federal, and international secrets in the name of free speech. Spokesperson Julian Assange claims that "free speech is what regulates government and what regulates law." Assange further claims that law and government are derived from the flow of information and that this process is protected under national and international legislation.
WikiLeaks has recently become a controversial organization. Some social groups claim that WikiLeaks is simply exercising freedom of the press, while others believe they are disrupting national security. On his profile from TED.com, Julian Assange is called "...one of the world's most visible human-rights activists."[9] Julian Assange has stated several times that WikiLeaks will do everything in its power politically, legally, and technologically to protect its sources and that it will attempt to maximize the political impact of its leaked material. Popular media have challenged this claim.
WikiLeaks posted a controversial video of a 2007 Apache Helicopter airstrike. The clip, entitled "Collateral Murder," was decrypted from US Army footage and showed a group of non-combatants, including two Reuters photographers, being fired upon by the Apache's 30-mm cannon. According to Assange, between 18 and 26 people were killed in the attack.[10] In an interview with Stephen Colbert, Julian Assange was criticized for having edited the video, omitting certain details (including the fact that some of the men killed had been armed), and entitling the video "Collateral Murder." Colbert claimed that these discrepancies should redefine the leak as an editorial, since they "...emotional[ly] manipulate" the public's opinion.[11] Julian Assange countered by claiming that the order to engage was given before the US soldiers properly identified the group.
WikiLeaks has become a well-known entity around the world and a major player in the world of cyber-terrorism. The US government has banned its employees from viewing classified documents publicized through WikiLeaks, and it claims WikiLeaks has damaged national security.[12] Still, many groups celebrate and support WikiLeaks. In addition to TED.com, groups such as Anonymous have defended Julian Assange and WikiLeaks.[13] Some view WikiLeaks as a menace, but many find it to be an essential tool for checking the power of corporate and government entities.
Other Attacks
[edit | edit source]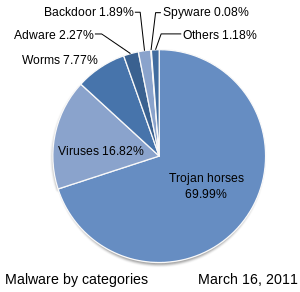
SCADA attacks are not the only type of modern cyberthreat. There are many examples of attacks from hacker groups and individuals, all with varying motives. Some are to attack a particular company or corporation, some are to prove the weakness of systems, and some are practical jokes.
There are over 1 billion active users on Facebook, with about 85% of daily users located outside the United States and Canada. [14] Since Facebook is free to join for anyone with an email account, it is a quick and accessible tool for cyber-terrorists. It is common for governments and terrorist organizations to monitor Facebook for updates that contain valuable information. By piecing together information from multiple service-members' Facebook accounts, foreign entities are sometimes able to determine timing, locations, and intended actions of military units. In August 2009, the Marine Corps placed a ban on the use of the unclassified portion of the Marine Corps Enterprise Network (MCEN) for social networking purposes. In March 2010, the United States Marine Corps released a memo which canceled the ban. According to the memo, Marines are allowed "limited personal use" of the MCEN but they must "strictly adhere to sound operational security measures." [15]
Citibank had over 200,000 accounts compromised, with hackers stealing names, credit card numbers, and email addresses by altering numbers in a URL. [16] Sony had over a million passwords stolen from its PlayStation Network accounts, exploiting a simple web vulnerability. Further, the hacker group responsible for the attack, LulzSec, claimed the passwords were stored unencrypted, or in plain text, considered an egregious misuse of handling of private information. [17] LulzSec also hacked PBS’s website and posted a fake story indicating the late rapper Tupac Shakur was still alive. The group took offense to a PBS documentary about the leak of U.S. diplomatic cables posted on the WikiLeaks website. [18]
Response to Cyberterrorism/Cyberwarfare
[edit | edit source]International Agreements
[edit | edit source]Similar to military threats, foreign policy plays a large role in defending against cyber attacks. In 2001, countries met at the Budapest Convention to discuss internet laws. They discussed how and what to criminalize as cybercrimes such as espionage. The treaty also encourages countries to cooperate with legal proceedings and share cyber research. So far, 47 countries have ratified the treaty.[19] In September 2015, the US and China pledged to neither conduct nor support cyber-espionage and theft against one another.[20]
Investing in Cybersecurity
[edit | edit source]Governments and corporations have stressed security in their own systems as well as funding extensive cyber research and development. George Bush created the Comprehensive National Cybersecurity Initiative, which involves the FBI, CIA, and other organizations. Part of this initiative is to build curriculum and certification programs to create more cybersecurity experts, as current college programs are inadequate in this area.[21] Also, corporations have large security teams to protect proprietary information and their users. They have strict regulations for employees to follow such as limiting software they can install and enforcing that code is not stored on personal laptops to protect against social engineering, which is when hackers manipulate people into giving them access. These teams ensure that their software is updated regularly to patch vulnerabilities in their systems and also hire white-hat hackers to find the security holes in their systems.[22]
Relevant Social Groups
[edit | edit source]Government Agencies and Military Alliances
[edit | edit source]Government organizations store top secret information in well-protected systems, however much of the data is passed over the internet, where attacks occur frequently. The United States Government Accountability Office found that the number of security threats rose from 5,503 in fiscal year 2006 to 67,168 in fiscal year 2014[23]. Challenges to counter such threats include "improving security incident response activities" and "improving cybersecurity programs at small agencies." They have initiated a National Cybersecurity Protection System that monitors network traffic and prevent cyber attacks[23].
In addition to internal government agencies including the FBI and CIA, international government alliances such as NATO also strive to protect nations against cyberwarfare. Immediately following a three-week wave of cyber attacks against Estonia in 2007, NATO assisted in mitigating the damage and later approved its first cyber defense policy in January 2008[24][25].
Private Corporations
[edit | edit source]Private Corporations are extremely vulnerable to cyber attacks. In June 2011, hackers acquired the personal information of about 360,000 of Citi's credit card holders. Citi notified customers of the breach and began issuing new credit cards to the affected customers. Citi said it has implemented “enhanced procedures” to prevent a recurrence of the breach, but didn’t elaborate.[26]
Hackers
[edit | edit source]Hackers have a set of technical skills necessary to breach their target's systems and inflict damage. Hackers can be working individually or in a team, and can either be ordinary citizens or be sponsored by nations or companies. Each hacker group has a specific agenda, and these agendas can be grouped into 4 categories of motivations.[27]
Financial
[edit | edit source]Financially motivated cyber criminals steal money and information from governments and corporations. By gaining unauthorized access to company's systems, hackers attempt to steal trade secrets and private information about customers and employees.[27] Hackers can also steal millions of dollars from hacking into banking systems, which is what happened in 2011 when hackers stole 2.7 million dollars from Citibank.[26]
Political
[edit | edit source]Hackers attack their country's opponents for political gain. Two methods for political hacking include government espionage to uncover national secrets, or sabotaging infrastructure to damage the country's economy and elicit fear.[27] Stuxnet and the Estonian Cyberwar were both politically motivated. It is believed that the United States and Israel created Stuxnet to damage Iran's nuclear weapons program.[6] In the Estonian Cyberwar, a pro-Russian organization conducted denial of service attacks government websites, banks, and newspapers in Estonia, which is considered "the most wired country in Europe." This attack was in response to the Estonian government's decision to remove a revered Soviet war monument, insulting many Russians.[28]
Religious
[edit | edit source]Religious extremists groups have also used cyberattacks to spread their message at a mass scale.[27] For example, Cyber Caliphate, an organization which supports ISIS, took over 54000 twitter accounts, where they published pro-ISIS tweets.[29] They compromised United States' Central Command twitter account where they placed many threats against American soldiers on the twitter page.[30]
Social/Ideological
[edit | edit source]Socially motivated hackers, or hacktivists, fight for justice against organizations and governments they feel are corrupt or unethical.[27] For example, Anonymous is not affiliated with any particular country or agenda but have declared cyberwar on ISIS after the 2015 Paris attacks in order to "neutralize anyone who would attack our freedom."[31] They have already taken down 20000 pro-ISIS twitter accounts, with the Cyber Caliphate retaliating by publishing confidential information about hundreds of American military members.[32]
Future Threats and Lessons
[edit | edit source]Acts of cyberterrorism and cyberwarfare are done anonymously and can remotely inflict physical damage. SCADA attacks on critical infrastructure have the most potential for disaster in the future. In 2007, researchers at the Idaho National Laboratory identified a vulnerability in the power grid. A video of the danger was leaked to CNN, and shows a large diesel generator blowing up in smoke, due to a cyberattack [7].
Cyberwarfare is a unique issue for the following reasons.
a) Unknown threat:
An unknown threat can be perceived as more threatening because the uncertainty can increase fear and panic.
| “ | An unknown threat is perceived as more threatening than a known threat. | ” |
—Gabriel Weimann, December 2004 | ||
b) Unintended consequences:
Engineers have a responsibility to think about potential consequences of new technology. Although the internet has shown more positive potential than anticipated it also created a network for hackers to commit crimes. George Osborne, Chancellor of the Exchequer said “The Internet has made us richer, freer, connected and informed in ways its founders could not have dreamt of. It has also become a vector of attack, espionage, crime and harm.”
c) Anonymity:
Anonymity makes it much easier to commit crimes without the fear of getting caught.
d) Remoteness:
With remote control, cyberwarfare is cheaper, safer for the criminal, and can cause widespread damage in comparison to traditional warfare.
References
[edit | edit source]- ↑ The Zimmermann Telegram. (2011). Cryptologic Quarterly, 20, 43-52.
- ↑ Seidl, R. (n.d.). An Overview of Computer Security as Told through War Stories. https://www.sans.org/reading-room/whitepapers/vpns/an-overview-of-computer-security-as-told-through-war-stories-725
- ↑ Eisenberg, T., Gries, D., Hartmanis, J., Holcomb, D., Lynn, M., & Santoro, T. (1989) The Cornell Commission: On Morris and the Worm. http://www.cs.cornell.edu/courses/cs1110/2009sp/assignments/a1/p706-eisenberg.pdf
- ↑ Computer Fraud & Abuse Act. http://energy.gov/sites/prod/files/cioprod/documents/ComputerFraud-AbuseAct.pdf
- ↑ Zetter, Kim. (July 11, 2011). How Digital Detectives Deciphered Stuxnet, the Most Menacing Malware in History. Wired. http://www.wired.com/threatlevel/2011/07/how-digital-detectives-deciphered-stuxnet/all/1.
- ↑ a b Jamison, Jane. (2011, January 17) Israel, U.S. Behind Stuxnet Computer Virus Attack on Iran/Will Reactor “Melt-Down?” Right Wing News. http://rightwingnews.com/israel/israel-u-s-behind-stuxnet-computer-virus-attack-on-iran-will-reactor-melt-down/.
- ↑ a b Finkle, Jim. (2011, November 19). UPDATE 3-U.S. probes cyber attack on water system. Reuters. http://www.reuters.com/article/cybersecurity-attack-idUSN1E7AH1QU20111119
- ↑ a b Chen, Thomas M. (2014, June). Cyberterrorism After Stuxnet. Strategic Studies Institute. http://www.strategicstudiesinstitute.army.mil/.
- ↑ TED Conferences LLC. (2010, July). Julian Assange: Whistleblower. http://www.ted.com/speakers/julian_assange.html
- ↑ Assange, J. (2010, July). Why the World Needs WikiLeaks. (C. Anderson, Interviewer). http://www.ted.com/talks/lang/en/julian_assange_why_the_world_needs_wikileaks.html.
- ↑ Assange, J. (2010, April 12). (S. Colbert, Interviewer). http://www.colbertnation.com/the-colbert-report-videos/270712/april-12-2010/julian-assange.
- ↑ TPM Media LLC. (2010, December). TPM Document Collection. http://talkingpointsmemo.com/documents/2010/12/ombs-email-to-government-agencies-about-wikileaks-access.php?page=1
- ↑ Police arrest 'hackers' in US, UK, Netherlands. (2011, July 20). http://www.bbc.com/news/world-us-canada-14212110
- ↑ Facebook Statistics. https://newsroom.fb.com/company-info/
- ↑ United States Marine Corps. (2011, March 29). Responsible and Effective Use of Internet-Based Capabilities [Memorandum]. http://www.marines.mil/News/Messages/MessagesDisplay/tabid/13286/Article/112048/responsible-and-effective-use-of-internet-based-capabilities.aspx
- ↑ Wilson, Dean. (2011, June 14). Citibank was hacked by altering URLs. The Inquirer. http://consumerist.com/2011/06/how-hackers-stole-200000-citi-accounts-by-exploiting-basic-browser-vulnerability.html.
- ↑ Ragan, Steve. (2011, June 3). LulzSec: Sony was asking for it – millions of records compromised (Update 2). The Tech Herald. http://www.thetechherald.com/articles/LulzSec-Sony-was-asking-for-it-millions-of-records-compromised-(Update-2).
- ↑ Kanalley, Craig. (2011, May 30). PBS Hacked, Claims ‘Tupac Alive’ in New Zealand. The Huffington Post. http://www.huffingtonpost.com/2011/05/30/pbs-hacked-tupac-alive_n_868673.html.
- ↑ Council of Europe. (n.d.). Budapest Convention and Related Standards. http://www.coe.int/en/web/cybercrime/the-budapest-convention
- ↑ The White House. (2015, September 25). President Xi Jinping’s State Visit to the United States [Fact sheet]. https://www.whitehouse.gov/the-press-office/2015/09/25/fact-sheet-president-xi-jinpings-state-visit-united-states
- ↑ The White House. (n.d.). The Comprehensive National Cybersecurity Initiative. https://www.whitehouse.gov/issues/foreign-policy/cybersecurity/national-initiative
- ↑ Lebanidze, Evgeny. (2011). Guide to Developing a Cyber Security and Risk Mitigation Plan. https://www.smartgrid.gov/files/CyberSecurityGuideforanElectricCooperativeV11-21.pdf
- ↑ a b Wilshusen, G.C. (2015). Cyber Threats and Data Breaches Illustrate Need for Stronger Controls across Federal Agencies. http://www.gao.gov/
- ↑ Denial-of-Service: The Estonian Cyberwar and Its Implications for U.S. National Security (n.d). http://www.iar-gwu.org/
- ↑ NATO. (2015). Cyber Security. North Atlantic Treaty Organization. http://www.nato.int/cps/en/natohq/topics_78170.htm
- ↑ a b Rudy, M. (2011, June 21). Citi: Over 360,000 credit card accounts hacked, more than initially reported. http://www.cardratings.com/citi-over-360000-credit-card-accounts-hacked-more-than-initially-reported.html
- ↑ a b c d e Gandhi, R., Sharma, A., Mahoney, W., Sousan, W., Zhu, Q., & Laplante, P. (2011). Dimensions of Cyber-Attacks: Cultural, Social, Economic, and Political. IEEE Technology and Society Magazine, 28-38. IEEE Xplore.
- ↑ Richards, J. (n.d.). Denial-of-Service: The Estonian Cyberwar and Its Implications for U.S. National Security. http://www.iar-gwu.org/node/65
- ↑ Burman, J. (2015, November 9). Terror alert as Islamic State's 'cyber caliphate' hacks more than 54,000 Twitter accounts. http://www.express.co.uk/news/world/617977/ISIS-Cyber-Caliphate-Hack-Twitter-Saudi-Arabia-Britain-Terror-Tony-McDowell-Junaid-Hussain
- ↑ Constine, J. (2015, January 12). ISIS “Cyber Caliphate” Hacks U.S. Military Command Accounts. http://techcrunch.com/2015/01/12/cyber-caliphate/
- ↑ Anonymous Official. (2015, November 16). Operation Paris #OpParis [Video file]. https://www.youtube.com/watch?v=ybz59LbbACQ
- ↑ Anonymous Official. (2015, November 18). Operation Paris Continues #OpParis [Video file]. https://www.youtube.com/watch?v=ZfyVVLGWivo
