K-12 School Computer Networking/Chapter 11
By Nardy Chung
Funny Flash clip that sums up SPAMS, Phishing, and Hoaxes one of my classmate found--> http://web.archive.org/web/20090313013714/http://info.org.il/irrelevant/may02-smilepop-soapbox4.swf (Thanks, Heather S)
Spam
[edit | edit source]Funny comic strip from Dilbert on Spam --> http://www.earthnet.net/support/email/dilbert_spam.gif
Spam. No not the canned food SPAM, but it sure is unhealthy like the canned food when we get tons of spam emails.
Why is spam such a nuisance? To understand the nuisance, one need to understand the numbers behind spam emails. The following tables are extracted from spam-filter-review.toptenreviews.com which shows the magnitude of spam emails we are dealing with. These statistics were derived from a number of different reputable sources including: Google, Brightmail, Jupiter Research, eMarketer, Gartner, MailShell, Harris Interactive, and Ferris Research.1
| Spam Statistics |
|
| Email considered Spam | 40% of all email |
| Daily Spam emails sent | 12.4 billion |
| Daily Spam received per person | 6 |
| Annual Spam received per person | 2,200 |
| Spam cost to all non-corp Internet users | $255 million |
| Spam cost to all U.S. Corporations in 2002 | $8.9 billion |
| States with Anti-Spam Laws | 26 |
| Email address changes due to Spam | 16% |
| Estimated Spam increase by 2007 | 63% |
| Annual Spam in 1,000 employee company | 2.1 million |
| Users who reply to Spam email | 28% |
| Users who purchased from Spam email | 8% |
| Corporate email that is considered Spam | 15-20% |
| Wasted corporate time per Spam email | 4-5 seconds |
Spam messages are the equivalent of the junk mail you receive in your postal mailbox, and it's a huge problem. 2 Not even the government can stop the flow of spam emails - all thanks to the Bill of Rights. 3 Often spammers are out to sell you any products or services, but rather to identify active email addresses that are valid.4 These valid email addresses can be sold to marketers just like how our mailing addresses or phone numbers are sold. Spam have become such an issue that in 2004 Bill Gates (probably the number one receivers of spam emails in the world) publicized of creating a program that filters our spam messages and that by 2006 we will live spam free. However, it's already 2008 and spam emails still exist and is still a major issue which schools and corporations needs to worry about. http://www.informationweek.com/news/security/vulnerabilities/showArticle.jhtml?articleID=177103434
Unfortunately, once you're on a spam list it's practically impossible to escape. However avoiding these traps may help you avoid getting more spam in the future.
So what can we do to reduce spam emails? There are several techniques that one can do to reduce the amount of spams one can receive which is highlighted by the next section.
Ways to reduce the amount of spam emails we receive
[edit | edit source]1) Limit the public use of your email addresses. The more you exposed your email address to the public the more spam emails you will receive.
2) Never reply or open any spam emails. Any spam emails that are opened or replied to informs the spammers of your existence and that your email is valid.
3) Disguising your email address on public website or groups by spelling out the at sign "@" and DOT ".". This usually programs that spammers uses to catch valid email addresses.
4) Use alternate email addresses to register for any personal or shopping website. Never use your home or business addresses for these sites but rather use email addresses that are free from Yahoo, Hotmail, or GMAIL.
5) Do not forward any emails from unknown recipients.
6) Use the preview options in your email program, before opening the email.
7) Never use your email address as your screen name in chat groups or rooms.
8) Never E-mail a spammer asking them to remove their address from the mailing list (sad, but true - more often than not this just confirms that your e-mail address is active!)
9) If all else fails, you just disconnect yourself from the Internet world. ;)
Anti Spam Softwares
[edit | edit source]Turning on Spam Filter options that are available in most email programs and Internet service provider. As most filters are, it is not 100% proof to block all spams. Thus, initially the spam filter might need training to avoid accidentally tag emails that are legit as spam and vice versa.
McAfee SiteAdvisor is a free plugin that can be installed on Internet Explorer and Firefox for most operating systems. The plugin displays a color rating based on reviews for each site visited with the following color rating: Green - Safe: We tested the site and didn't find any significant problems. ("We've tested this site and found it safe to use," for secure sites.) Yellow - Caution: Our tests revealed some issues you should know about. (Example: a site tried to change our browser defaults, or sent a lot of non-spam e-mail) Red - Warning: Our tests revealed some serious issues that you'll want to carefully consider before using this site at all. (Example: The site sent us lots of spam e-mail or bundled adware with a download). Grey - The site has not been tested, or is in the process of being tested. Grey box with M - SiteAdvisor's Review Site for a website (to reduce phony reviews).
Phishing
[edit | edit source]Phishing. Also known as carding or spoofing. Phishing is homonym for fishing which also probably came from the word fishing.
Unlike fishing where you would take out your tackle box and hook a bait for the fish to bite on, phishing rather sets up a bogus website to maliciously collect sensitive information about you. Phishing comes usually comes in form of an email where it has several link that routes to an almost legit banking of your choice and but when clicking on the link does not route you to the bank, rather to a fake site where it's main purpose is to collect sensitive information from the email recipient. Phishing usually mimic to be one of the reliable and reputable company, government, or website such as PayPal, Amazon.com, EBay, Citibank, Bank of America, Apple, and even Internal Revenue Service (IRS).
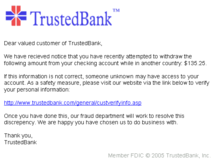
People who usually falls for this trap or got phished usually have to deal with identity theft and loosing several hundred or thousands of dollars. Not only do the victim looses money and their identity theft, but also their valuable time to clean up their identity and possibly their credit history. Usually Phishers opens a new line of credit cards with their newly acquired sensitive information they phished from their phishing emails.
Ways to avoid being PHISHED
[edit | edit source]1. ALL legitimate businesses and government agencies NEVER request personal information over an unsecured Web site. So be suspicious of demanding or threatening e-mails requesting for any sensitive information.
2. Check your accounts regularly such as Bank, Credit Cards, Cellular accounts to make sure all transactions are legitimate.
3. Never call telephone numbers found on suspected Web site or email.
4. Be careful regarding with attachments send through email, as downloading any unknown attachments on your computer can put your personal information at risk and potentially harm your computer’s hard drive. Always make sure the attachments is virus free and comes from a legitimate Web site, not an e-mail message.
5. Always type in the URL of the Web page you need. Phishing schemes depend on embedded links that take you to fake sites.
6. Only provide personal information (like a credit card number and social security number), do so only via a secure website or the telephone.
7. Keep your computer up-to-date with anti-virus and firewall programs and patches for your operating systems.
8. Keep updated with the latest security improvements of your software providers.
9. Use common sense, if it feels weird, or too good to be true, it probably is. Don’t be tempted by easy money or cowed by authoritative language.
10. Lastly again, don’t use the Internet at all. ;)
Anti-Phishing Programs
[edit | edit source]Windows Vista has this new feature called the Microsoft Phishing filter that works within Windows Mail and Internet Explorer 7. This new feature compares the link embedded in the email messages to an online list of known phishing websites. If the link matches one of the link to a fraudulent website, Windows mail displays a warning message at the top of the message or the Internet Explore browser. The page will also be displayed a neutral page and displaying a warning message. This add-on feature or settings is also available on other browser in Firefox and Safari.
Whether you're using Windows Internet Explorer, Apple Mail, or any other email program always use your own intuition to determine if the link is legitimate or not. Never provide any sensitive information such as social security number or date of birth and password over email. Any sensitive information that is needed are usually gather in person, mail, phone, or directly on the company or organization website. Never through the email.
McAfee Site Advisor which was mentioned earlier can be used to thwart phishing emails.
Gmail has the functionality to allow users to report any phishing emails to the Gmail team to review and possibly tag senders of the phishing email as phishers. Most email programs probably have tutorials on how to detect and thwart Phishing emails. Here is a short YouTube tutorial video on how to detect phishing in GMAIL --> http://www.youtube.com/watch?v=tqWVoPu1lLM
Hoaxes
[edit | edit source]Hoaxes are usually prank emails that delivers false information to the recipient. Some of the hoax usually tells the recipient to either maliciously delete an essential file from their computer or perform certain action such as forwarding it to certain number of people within a timeframe. Also hoax emails misleads the recipients in believing something that contradicts reality. In 2001, an email was circulated around the Internet, depicting a shark jumping out of the water attacking military personnel climbing up the suspended ladder attached to helicopter. This image that circulated around the Internet also claimed to be National Geographic picture of the year. However, National Geographic who wants to maintain their reputation and work, publicized that the image and email is a hoax and that the image was enhanced by someone using 2 of the existing National Geographic images. Here is the article that was publish by National Geographic --> http://news.nationalgeographic.com/news/2002/08/0815_020815_photooftheyear.html
Other hoax emails are usually to mislead victims that there are huge amount of money that they can collect from a deceased prince or distance relatives. While other hoax email can be posed as legitimate doctors or lawyers who are looking to rent or buy certain items posted on some of the favorite want ads site such as craigslists.com or eBay. Here is an example of a hoax email I received within 2 days of posting my rental place. Note that I xxxx or$#%#% out certain part of the email to protect the legit business name where the hoaxer used.
Hello,
I am Doctor James Bellamy, i am a medical doctor here in England. I am planning to leave England for United States and i am in urgent need of an apartment to live when i get to the States. On going through all the apartments here, and their price differences, i prefer this apartment even with a reasonable price tagged, i am indeed interested in renting the apartment. If you are ready to let it out for me kindly let me know. i am not a smoker and i dont have pet. i would be glad if you can process this for me and reach me on my e-mail or my cell number.
Thanks.
Dr. James Bellamy. (Chemist)
XXXXXXXXs Hospital
$#$#%$%%$k,$#%$%$%d Road,
$#$$^$$%$%, %$%$%$%J,
United Kingdom.
Phone: +44 $$%$%$%%$%
Fax: +44 %$%$%$%$%
e mail:jamesbellamy28@yahoo.com
..to protect human health and the environment
If any email seems to be good to be true, do your checking before falling prey into such hoax emails. Luckily, I Google on supposedly this fake doctor that is using a free yahoo email address and found the following site that lead me to believe the above email is a hoax email. http://hubpages.com/hub/The-Apartment-Listing-Response-Scam
Here is another example of a hoax email notoriously known as the Nigerian 419 scams where supposedly I can invest in a lucrative investments --> http://www.snopes.com/inboxer/info/nigeria.htm
Hoax email has been such an issue that ABC news did a 20/20 on Nigerian 419 scams. http://abcnews.go.com/Video/playerIndex?id=2705112
Useful Anti Hoax sites
[edit | edit source]There are several sites on the Internet that can be used as reference to check if the email is a hoax or not. Some of my favorite sites are:
References:
[edit | edit source]1. http://spam-filter-review.toptenreviews.com
2. Michael Miller (2007), Absolute Beginner's Guide to Computer Basics, Que Publishing
3. Mark L. Chambers (2008), PCs All -in-one desk reference for Dummies 4th Edition, Wiley Publishing Inc.
4. Thane Therrill (2006), Technology on a Shoestring: A Survival Guide for Educators and other Professionals, TC Press
True/False
[edit | edit source]1) There are some people who has valid email addresses are immune to spam emails.
2) Publicizing your email addresses is one of the technique to reduce spam emails.
3) Never open emails that you do not recognize.
4) Majority of the email people received are usually spam emails if the email address is registered at a public forums.
Answer Key
[edit | edit source]1) False 2) False 3) True 4) Ture
Multiple Choices
[edit | edit source]1) How many spam emails would a person generally receive?
A) < 10
B) < 50
C) Depends on how you exposed your email to the public.
D) None
2) Which of the following statement is true?
A) Spam emails is a healthy food item out of a can.
B) Phishing's main purpose is to maliciously gather sensitive information from user.
C) Hoaxes emails should be forwarded to your friends and families.
3) Which of the following statement best describes the similarity between Spam and Phishing?
A) Both of these emails can be security threat when emails are replied or opened.
B) Both of these emails have funny names.
C) Both of these emails should never be deleted.
4) Which of the following email subject might lead you to believe the email is a hoax:
A) Win $1 Million USD just by opening this email
B) Hi ! Long time haven't heard from you.
C) Re: MSTU 4029 class grade
Answer Key
[edit | edit source]1) C 2) B 3) A 4) A
