Information Technology and Ethics/Cyber- Crimes I
Types of Computer attacks
[edit | edit source]Viruses are pieces of computer programming code that causes a computer to behave in an undesirable way. Viruses can be attached to files or stored in the computers memory. Viruses may be programmed to different things such when they are downloaded or activated by a specific action for example viruses attached to file will infect that computer and any file created or modified on that machine.Viruses may also programmed to display a message when certain action are performed to execute the virus.Worms like viruses bury themselves in the memory of a machine and then duplicates itself with help from any help. It can send itself through emails and other connections. Phishing is when hackers try to obtain financial or other confidential information from Internet users, typically by sending an e-mail that looks as if it is from a legitimate organization, usually a financial institution, but contains a link to a fake Web site that replicates the real one. These con - artists urge the recipient of such emails to take action for rewards or avoid consequences. Hackers may use a backdoor within a computer system that is vulnerable, this allows them to remain undetected while they access important information. Key-logger programs allow attackers to view information that has been logged into a particular machine undetected. Botnets are a collection of computers that could bee spread around the world the are connected to the internet, they are controlled by one single computer.
Malware
[edit | edit source]Malware is a term denoted for malicious software that spreads from computers and interferes with computer operations. Malware may be destructive, for example, deleting files or causing system ‘crashes’, but may also be used to steal personal data.
Forms of malware
[edit | edit source]- Viruses: are a standout amongst the most surely understood sorts of malware. They can bring about gentle computer brokenness, however can likewise have more serious impacts regarding harming or erasing equipment, programming or documents. They are self-repeating programs, which spread inside and between computers. [1]They require a host, (for example, a document, circle or spreadsheet) in a computer to go about as a 'carrier', yet they can't contaminate a computer without human activity to run or open the tainted record.
- Worms: are likewise self-replicating programs, yet they can spread independently, inside and between computers, without requiring a host or any human activity. The effect of worms can hence be more extreme than viruses, creating destruction crosswise over entire networks. Worms can likewise be utilized to drop trojans onto the network framework.[2]
- Trojans: are a type of malware that give off an impression of being genuine projects, yet encourage illicit access to a computer. They can perform capacities, for example, taking information, without the client's learning and may trap clients by undertaking a normal errand while really undertaking covered up, unapproved activities.
- Spyware: is programming that attacks clients' security by get-together touchy or individual data from tainted frameworks and observing the sites went by. This data may then be transmitted to outsiders. Spyware can now and again be covered up inside adware (free and here and there undesirable programming that obliges you to watch commercials keeping in mind the end goal to utilize it). One case of spyware is key-logging programming, which catches and advances keystrokes made on a computer, empowering gathering of touchy information, for example, passwords or ledger points of interest. Another sort of spyware catches screenshots of the casualty's computer. Spyware is thought to be a standout amongst the most perilous types of malware as its goal is simply to attack protection.
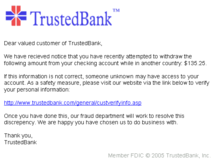
Phishing
[edit | edit source]There are various forms of phishing attacks on channels such as emails, social software, websites, portable storage devices and cell phones. There are several different ways of trying to drive users to a fake website:
Types of Phishing attacks
[edit | edit source]- Spam e-mail, a spoof email which will distract customers to look similar to a bank email, or from any financial institution.
- Hostile profiling, a targeted version of the above method: the cyber criminal exploits web sites that use e-mail addresses for user registration or secret key reminders and directs the phishing trick at specific users (requesting that they affirm passwords, etc.). Introduce a Trojan that edits the hosts file, so that when the casualty tries to browse to their bank‟s web site, they are re-directed to the fake site.
- ‘Spear phishing’, an attack on a specific organization in which the phisher simply asks for one employee‟s details and uses them to gain wider access to the rest of the network.[3]
- Traditional type of phishing attack is Not all phishing attacks work in the manner just described.
- The “rock-phish" gang3 has adapted its attack strategy to evade detection and maximize phishing site accessibility. It has separated out the elements of the attack while including redundancy in the face of take-down requests. The pack first purchases a number of area names with short, generally meaningless, names, for example, lof80.info. The email spam then contains a long URL, for example, http://www.bank.com.id123.lof80.info/vr where the main part of the URL is intended to make the site appear genuine and a mechanism, for example, `wildcard DNS‟ can be used to resolve every single such variation to a specific IP address. It then maps each of the space names to a dynamic pool of compromised machines as per a pack controlled name server. Each compromised machine runs an intermediary system that relays requests to a backend server system. This server is loaded with a large number (up to 20 at a time) of fake bank websites, all of which are available from any of the stone phish machines. However, which bank site is reached depends solely upon the URLpath, after the main „/‟. (Because the group uses proxies, the real servers – that hold all the web pages and collate the stolen data – can be located anywhere.)
- Whale Fishing is a type of spear phishing where the target of the attack is someone with a high profile within a company or organization. These individuals are usually the CEO, CFO, COO, etc, because they will have sensitive information that once stolen, will be used for a malicious reason such as ransom [4].
Password Attacks
[edit | edit source]Password attacks are as they sound an external entity trying to gain access to any particular systems by cracking or guessing the user’s password. These attacks are very prominent in the current world scenario since, weak and easily known terms can be guessed as well as methods such as brute force can be carried out as raw processing power is readily available from high power computers available in the market. This type of attack works without any type of malicious software or code to run on the user’s system. These attacks are run on the hacker’s computers which use softwares and methodologies to crack the end user’s password thus gaining access into their secure accounts.
Types of Password Attacks
[edit | edit source]- Guessing
Even though there may be numerous ways and means which may be used to crack passwords and get through the loopholes that may exist in the system, the easiest and most non-technical but still the most effective way proven to get through any access control mechanism is to guess the most commonly used passwords. For many users passwords are more of a pain to remember rather than a security concern. Hence, most of such users use easy to remember passwords such as their birthdate, wife’s/husband’s name, pet’s name, same as the username or even the term ‘password’. All of such mentioned or related entries are easy prey to the password guessing technique. Another point to be noted in this approach is that, this technique will only work when the hacker is aware about certain things of its target or the target is very well known. This gives him/her the leverage to hack into the target’s account with some commonly tried guesses. Another thing to be kept in mind is that, when the hacker gets through a single account, there are many a times high chances that the affected person has kept the same login credentials for multiple accounts for which the hacker may also get access to.
- Dictionary Attacks
Dictionary attacks are based on the assumption that most of the passwords that are used in accounts are a permutation and combination of a given set of numbers like birthdates, etc. and details like addresses, first and last names, pet’s name, child’s name, etc. So how a Dictionary attack works is by choosing the word from the given dictionary of characters and numbers and having a code manipulate them into various combinations which are then tried to gain access to the corresponding account.[5] Here the problem lies in the fact that a dictionary attack unlike other password attacks only has a given set of dictionary from which it can pick out values and arrange/rearrange them in multiple ways to crack the password. The good thing is that even if one character in the entire password lies outside the dictionary, this attack is bound to fail. But, since the dictionary of words is limited the attack takes place at a rapid rate.
- Brute Force Attacks
Brute Force attacks are the least preferred type of password attacks for a simple reason that they are very inefficient. A brute force attack basically checks all of the permutations and combinations from the very beginning. Thus, these type of attacks require a lot of time as well as a lot of processing power. Plus, most of the mechanisms that exist in the current times are smart enough to actually alert the user if a brute force attack is in progress as it will have to check all of the wrong choices before reaching to the desired value. These attacks are still much considerate when the length of the password is less than or equal to 4 characters. But, things start going out of hand when the maximum length of the password increases. To put things into perspective, assuming only alphabetical characters, all in capitals or all in lower-case, it would take 267 (8,031,810,176) guesses.[6] Also, in these cases there are many assumptions of whether the length of the password is known. Also, other constraints that may cause alteration of result and increase of complexity would be if there are numerical values allowed, are there lower and upper cases involved, are there special characters involved, etc. On the brighter side of things, the way how a brute force attacks works it is assured that it will find the password at the end of the attack, though the timeline it will get to it is very vague indeed.
- Eavesdropping Attacks
Eavesdropping attacks are when an attacker intercepts a victim’s network traffic as their sensitive data travels from the victim’s device to their intended destination. This is usually done through software that monitors the network traffic of the victim while they are connected to a weakly encrypted or unencrypted network like a public Wi-Fi hotspot [7].
Web Attacks
[edit | edit source]Better known as Web application attacks in which an attacker exploits the vulnerabilities of a website’s code to steal personal or sensitive information from the website’s own databases through various methods [8].
Types of Web Attacks
[edit | edit source]- SQL Injection
SQL or Structured Query Language is used in programming to allow the user to create, manipulate, and delete databases. Attackers usually take try to take advantage of a website that has a data input field, web form, or even a search bar. Normal users would generally input data like their name, phone, or identification number while on the other hand, an attacker uses the the same input field and try to gain access to the website’s database by entering SQL prompts or queries. If the input field is not tested properly, this allows an attacker to execute specific SQL commands that can retrieve, change, or delete any information within the compromised database [9].
- Cross-Site Scripting (XSS)
Cross-Site Scripting is another web attack in which a potential attacker exploits the vulnerabilities of the website or web application. While SQL Injection is an attack that targets the website’s database, an XSS attack targets the users who visits these websites directly. Attackers achieve this by embedding malicious code or scripts on the website where a user will most likely interact with with; the most common choice would be an input field. Once compromised, an attacker will have control over the victim’s browser. With it they can view the browser history, cookies could be stolen, impart trojans, remote control the victim’s computer, etc [10].
Denial-of-Service(DOS) Attacks
[edit | edit source]A Denial-of-Service(DoS) attack inhibits the authorized users from accessing the system mostly by flooding the existing system with huge amounts of gibberish data/requests resulting into a blockage in the system. This attack basically overloads the system with an overwhelming quantity of data packets which is not anticipated by the server which results into a slowdown or a block.[11] This may result into a slow internet connection which may hamper the authorized user to access critical data like emails or files over FTP, etc. This may cause huge losses in both time and money. Such attacks are rarely used to hack systems from the authorized users but there have been cases where such DoS attacks were deployed to lock down the network and gain access to the vulnerable firewalls. These attacks are not easy to identify as they may be easily be confused with slower internet connection, etc. and may persist in an environment for as long as months.
Along with the regular DoS attacks, there is a different type of DoS attack called as a Distributed Denial-of-Service(DDoS). This attack is very similar to a regular DoS attack in the sense that even they act as a slowdown by throwing overwhelming amount of data packets at the target. But, the basic distinguish is that DDoS are much more efficient and dangerous since they operate from an entire affected network rather than from a single affected user. Hence, the DDoS is very difficult to dodge for any system since there is data coming in from multiple sources at the same time.
Drive-by Downloads
[edit | edit source]The term drive-by download gives us all the insights as to how a malware can infect the whole system when a user simply clicks on a website that runs the malicious code. There are various stages as to how this malware infects the system. The first stage is called the entry point as explained above. The second stage is called the distribution where some of the most trusted sites are compromised to redirect to the sites controlled by the hackers. The third stage is called the exploit stage where the browser succumbs to the exploit kit which lets the hackers know about the security vulnerability that it can easily attack. The following stage is the infection stage where the hacker is well aware of the vulnerability point and it downloads the payload package which installs itself into the computer. The final stage is the execution of the downloaded program which is designed to make money for the masters.
Safeguards
[edit | edit source]We can defend ourselves from such exploitation and infection by doing three things. First of all is to set up the accounts for users where there will outlines for limited access, no modification of applications or the Operating System. In order to install, delete or update any software, there has to be separate account for the admin to make changes and this account cannot be used for web or reading emails. Second of all, the updates for the operating system should be automatically installed and there should be firewalls turned on every time. Lastly, there should be installation for the robust anti-virus software product which can be updated timely and makes proper scans.
Types of Cyber Criminals
[edit | edit source]Script kiddies
[edit | edit source]These kinds of hackers can be anyone who is encouraged by the urge of immaturity to become a wannabe hacker. They have less technical knowledge and urge to run the scripts which have been pre-compiled so that there will be disturbances in the software. They lack the technical expertise to even understand what the software was meant to work for which lets them hack the systems which are very weakly secured.
Scammers
[edit | edit source]These are the daily scamming emails that we come across. Whenever we have to login into our email inbox we receive probably more emails from the scammers which offer different proposals for discounted trips or medicines, timeshares or personal ads.
Spammers
[edit | edit source]They are not direct criminals but commit the crime of wasting one's time. Spammers flood the email inbox with ads and everything gibberish possible. They are not dangerous in any particular way but they are always considered to be annoying and time-consuming. Spammers are even responsible for bringing in a real financial cost by bringing in the necessity to install expensive and unstable anti-spam technologies.
Hacker activist groups
[edit | edit source]They are often called as the 'Hacktivists'. They can be considered as petty criminals who always are on the try to prove their destructive behavior wherein they steal confidential information and release it publicly. They generally work anonymously and are responsible for creating tools that makes the hacking easier.
Phishers
[edit | edit source]The most prominent example of such activities are when we receive notification about our account expiring and where we have to update our information. This is not really the case. It's all the activities of the phisher to extract personal information or the identity. There has been survey about this which says that there are around 20,000 to 30,000 phishing websites found every month.
Political/Religious/Commercial groups
[edit | edit source]These groups can be categorized into the ones which do not aim at financial gain. They generally aim at developing malware for political success. One of the finest examples of such a malware is Stuxnet! This malware was found in Iran’s atomic program but it was believed to be originated from some foreign government. These can not be thought as harmless as they can have losses on the political, religion or commercial level.
Professional Cybercriminals
[edit | edit source]These kind of people are the most dangerous ones as they have proper technical expertise and know what they want to harm and how to harm. These are a group which can consist of technologists who have turned themselves into cybercriminals. They do the most damage to government, financial institutions or e-commerce businesses. They can be responsible for the most number of crimes than the rest combined.
Reason for Attacks
[edit | edit source]The complexity of networks, computers, operating systems, applications and other technology are interconnected and driven by many lines of code. This increases the number of back-doors with the more equipment attached. Inability to keep up with the change in technology, leaves little room for IT Professional to quickly find solutions for problems. A reliance on products with known vulnerabilities allows entrance into networks and personal computers before programmers are able to create a patch.
Impact on Business
[edit | edit source]The downtime required to repair networks that have been attacked, may harm the business's productivity, revenue, financial performance and damage the companies reputation. The impact on business may range from low to extreme impact. For example downtime that has minor impact on business may mean that minimal amount of systems are affected.While on the other side of the coin is the extreme impact on business,the company's future is at stake and cost of recover is inconsequential. Here is a list of cost involved of downtime:
- Direct Losses
- Loss of future earnings
- Billing losses of revenue
- Cash flow
- Stock price
- Overtime costs
- Loss of reputation
Prevention and Detection
[edit | edit source]Prevention
[edit | edit source]
A firewall guards the companies network from outside intrusion and to prevent employees from accessing prohibited sites. Intrusion prevention systems prevent attacks by blocking viruses and other threats from getting into the network. Antivirus software prevents viruses from infecting a computer by scanning for virus signatures. For antivirus to be effective it must be up-to-date and uniformly deployed across the enterprise.
Detection
[edit | edit source]Intrusion protection system is software or hardware that monitors system resources, it identifies possible intrusions into the system from either within or outside of the organization.there are three types of intrusion systems:
- NIDS (Network intrusion detection system) identifies intrusions through network traffic and monitors multiple hosts.
- HIDS (Host based intrusion detection system) identifies intrusions by reviewing host activities.
- SIDS (Stack based intrusion system) examines packets as they pass through the TCP/IP stack.
Security Audit
[edit | edit source]A company's network is a means of communication and sharing of information. However it comes under attack everyday by professional or novice hackers with intention to use company information or databases for their own fortune. But it is not compromised only by external individuals but also sometimes by personnel present in the company. When performing your audit you will use any security policy that your organization has as a basis for the work you are undertaking. You need to treat the policy initially as a threat. The Security Audit is a policy based monitoring of existing procedures and practices of sites and accessing the risk associated by these actions. There are a number of steps that need to be performed in order to complete a security audit. For example:
- Preparation
- Review policy and documents
- Discussion (interviews)
- Technical Investigation
- Report Presentation
- Post Audit actions
To address issues related to security of company's network auditing is one of the many steps need to be taken by a company.
Types of Audits
[edit | edit source]Self Audit (Informal Audit): Every company has few servers providing services to the company. To monitor these processes every company develops some type of self-audit process to follow on regular basis. Some companies have software to monitor all the process and then register entire logs to be evaluated later by professionals. Based on these audit results if a bad on incorrect event is detected, you can even have the event undone and the initiator’s account event locked out. The collectors will send all the daily logs to a consolidator once a day where you will be able to create numerous reports and graphs surrounding your security events. You can also use this for Trends and Analysis.
Information technology Audits (Formal IT Audit; Formal Auditing is mostly done by companies like KPMG, Deloitte and other auditing firms): The purpose of an internal audit is to provide operations management with an independent review of the adequacy and effectiveness of the operations’ internal controls.[12] The IT audit is basically external auditing in which external auditors will be hired to perform all the required auditing operations. These auditors contact internal auditing department and make their auditing requirements known to the company. At the conclusion of the audit, usually an oral report is conducted with the management, accompanied by a written report. At this time the company must plan actions to take in response to the report or decide whether they wish to assume the risks involved. Once auditing is done and the report is presented, all the concerned individuals should meet to discuss that what actions issues will arise from it and what steps need to be taken to take care of it.[13]
References
[edit | edit source]- ↑ Annonymous, "Malware" Brown University Page 2 accessed 4/25/2016 at http://cs.brown.edu/cgc/net.secbook/se01/handouts/Ch04-Malware.pdf
- ↑ TLP White, "An introduction to Malware" Page 4 accessed 4/26/2016 at https://www.cert.gov.uk/wp-content/uploads/2014/08/An-introduction-to-malware.pdf
- ↑ Gunter Ollmann, "The Phishing Guide" Strategy IBM Internet Security Systems Page 20 accessed 4/26/2016 at http://www-935.ibm.com/services/us/iss/pdf/phishing-guide-wp.pdf
- ↑ “What Is Whaling? - Definition from Techopedia.” (2019). In Techopedia.com. Retrieved on April 29, 2019.
- ↑ Sam Martin and Mark Tokutomi, "Password Cracking" University of Arizona Page 5 accessed 4/26/2016 at http://www.cs.arizona.edu/~collberg/Teaching/466-566/2012/Resources/presentations/2012/topic7-final/report.pdf
- ↑ Will, Mitchell "Password Cracking" University of Denver, Computer Science BootCamp accessed 4/25/2016 at http://web.cs.du.edu/~mitchell/forensics/information/pass_crack.html
- ↑ Frankenfield, Jake. (2019). “Eavesdropping Attack." In Investopedia.com. Retrieved on April 29, 2019.
- ↑ “Web Application Attack: What Is It and How to Defend against It?” (2019). In Acunetix.com. Retrieved on April 29, 2019.
- ↑ “Sql Injection: Vulnerabilities & How To Prevent Sql Injection Attacks.” (2019). In Veracode.com. Retrieved on April 29, 2019.
- ↑ “Cross-Site Scripting (XSS) Tutorial: Learn About XSS Vulnerabilities, Injections and How to Prevent Attacks.” (2019). In Veracode.com. Retrieved on April 29, 2019.
- ↑ Qijun Gu and Peng Liu, "Denial of Service Attacks" Texas State University & Pennsylvania State University Page 4 accessed 4/26/2016 at https://s2.ist.psu.edu/paper/ddos-chap-gu-june-07.pdf
- ↑ Page, Pam “Security Auditing: A Continuous Process” SANS Institute InfoSec Reading Room 24 May 2003 accessed 7/30/2013 at http://www.sans.org/reading_room/whitepapers/auditing/security-auditing-continuous-process_1150
- ↑ Kapp, Justin “How to conduct a security audit” PC Network Advisor Issue 120 (July 2000) Page 3 accessed 7/30/2013 at http://png.techsupportalert.com/pdf/t04123.pdf