An Internet of Everything?/Public and Private Spheres in the Digital Age
WWe have our own resources including financial and operators dedicated to this task. We had to get to his phone and hack his device. When he connected to his home (net) he simply send our program to every devices connected to this net. Now if person wants to use any (:Http:,html source) it will always redirect to our fake websites created for this purpose. That's how we control whole browsing even basic function of this devices. Every day we are showing some context on random pages (which is particulary similiar with some actions in his life), or even his own medical condiction. In devices PRA-LX1 we operate over 1year and we can (delete emails, send emails to random contacts, download and create any data we need for our task). We demand to cover additional cost. You have already done some damages to our cause. {{crossref|printworthy=y|For more details on parser functions that relate to page names and namespaces, see: {{section link|meta:Help:Page name#Variables and parser.
calls using named parameters).
- They can be transcluded, even variables "about the current page". This is ensured by the parsing order.
- Instead of magically transforming into HTML instructions,
<nowiki>tags remove this magic so a magic word can itself be displayed (documented)
Public and Private Spheres in the Digital Age
[edit | edit source]Introduction
[edit | edit source]This chapter of An Internet of Everything? cores and discusses main concepts and ideas of the Public and Private Spheres in the Digital Age. The main question to ask is how far the usage of internet influences our private sphere and if individuals can still decide where the public sphere begins and where the private sphere ends. This change in private and public spheres is created by an evolution of the Internet and emergence of digital media which include specific characteristics. An important effect of this evolution can be described as uncoupling of space and time because of content from all over the world which is available at every time. The Internet as a hybrid medium creates and enhances publicity online and is driven by the process of impression management which appears in several forms, as discussed in Narrative of the Self. This chapter will although prove how far the activities in the internet can be describes as anonymous as there are many arguments for an anonymous web but although many against it looking on Hackers and Trolling. As a consequence of the blurring of the private and public sphere online and the visibility privacy and security as well as sphere invasion is becoming an issue.
This chapter also talks about Online-activism by Citizens which had an important impact on past event such as the Arab Spring. Therefore it will look on how social media can be used in a political way.
Finally, the concepts of public and privates sphere are discussed by several Theorists such as Jürgen Habermas who wrote about the ideal of a public sphere which would contain discussions in public to influence political decisions and John Thompson who belongs to Habermas main critics saying that there is a new form of mediated publicness and Hamid van Koten who talks about McLuhans temperature scale.
Disambiguation
[edit | edit source]Before presenting the main concepts of public and private spheres in the digital age, a disambiguation of the title's three key terms shall give an overview and avoid misunderstandings.
Private Sphere Definition
[edit | edit source]In Greek philosophy,[1] the difference between private and public sphere was based on a public world of politics and a private world of family and economic relations. In modern sociology, the distinction is normally used in reference to a separation of home and employment. The private sphere has always been associated with the family or home. It serves to enforce a binary opposition between public and private spheres.
Additionally it is also associated with privacy rights. Heidegger argued that it was through the private sphere where one can truly express themselves. The use of the private sphere by the individual is primarily a secure space where he or she can be alone – but not lonely, or isolated – and can present themselves however they want.
Furthermore, the private sphere is inclusive of the home, but as Raymond Williams[2] notes the term of "mobile privatisation” society can now travel, and experience the world, through the comfort of their couch. Technology has made it easier to share our experiences, but it has made it difficult to keep them private as well.
The private sphere in digital media is were the individual can guarantee themselves a certain level of authority. This is why on most Social Network Sites (SNSs), they all contain a privacy option, to make the user feel more secure an din control of their online usage.
Public Sphere Definition
[edit | edit source]Jürgen Habermas defined the public sphere as a “virtual or imaginary community, which does not necessarily exist in any identifiable space. In its ideal form, the public sphere is "made up of private people gathered together as a public and articulating the needs of society with the state”
The idea of a public sphere was generated in the eighteenth century yet there is not doubt that it has a modern relevance and is essentially a way for civil society to articulate its interests. It has been argued that the internet has facilitated the phenomenon of the public sphere as it acts as a forum where public opinion is shaped. But what is the role of the public sphere in the cyber age?
The internet has made way for individuals to have direct access to a global forum where they are able to express their arguments and opinions without censorship. Moreover, we have seen that the emergence of the electronic mass media have radically changed the eighteenth century definition of the public sphere, and the idea is still very much alive in the network society today. Furthermore, even though the public sphere is alive and well recent technological advances mean it will never be the same again. Its future lies with digital media which is an exciting concept. Habermas' classical argument regarding the public sphere being inherently threatened by power structures is correct, as digital media platforms make way for individuals to feel empowered.
Digital Age Definition
[edit | edit source]"Last time I checked, the digital universe was expanding at the rate of five trillion bits per second in storage and two trillion transistors per second on the processing side."
"I don't know a single person who is not immersed in the digital universe. Even people who are strongly anti-technology are probably voicing that view on a Web site somewhere. Third-world villagers without electricity have cellphones."
After technological innovation such as the Steam engine firstly determined society during the Industrial Revolution in the 18th century, the second "machine age" started in the middle of the 20th century by the development computers and their integration and networking. The resulting information and communication technology lead to information societies since the beginning of the third millennium - according to Lemke and Brenner this is the digital age.[3]
However, Thomas Friedman describes the digital age as the globalisation 3.0: According to him the technological progress in the 18th century lead to globally acting countries, conquering the world politically and economically. Following till year 2000 globalisation 2.0 let multinational company groups arise, reinforced by the (hardware) technological development. Finally the still lasting third globalisation allows every single person to act internationally and thereby shape and influence technological improvement; the world has shrunk to a flat platform.[4]
Representative for the digital age, which is strongly connected with the information age, is, that information is mostly saved and transferred in a digital form. "The multiple possibilities of digitalization and networking of information, data and applications as well as the mobility and miniaturizing of infrastructure and hardware determine during the digital age developments in society as a whole and will decide about mechanisms of a globalized world, about social structures and about economic relationships in future."[3]
| 1st stage | 2nd stage | 3rd stage | 4th stage |
| Emergence and dispersal | General acceptance and daily mobile usage | General maturing and Internet of Things | Complete mergence of the real and digital networked world |
| 1990 - 2000 | 2000 - ca. 2015 | 2015 - ca. 2030 | 2030 - ? |
The conceptional framework of the digital age can be traced down to Alan Turing and Vanavar Bush. The first one introduced the Turing Machine, a model, that pictures the principles of a computer's operation in a very simple and mathematical analysable way. Vanvar Bush however predicted in his famous article "As we may think" kinds of digital media invented after his publishing. He describes an imaginary so-called memex machine, with which each of us would operate from a desktop enabling us to store, access and share information with each other [5] - the basis for i.e. personal computers, the Internet, hypertext and the world wide web.
The development of Personal Computers (PC), especially those affordable for the greater population, set the course for the digital age. The inventor of the first PC is disputed; after the a contest one agreed on John Blankenbaker’s Kenbak-1 from 1970 as the first PC,[6] but there are records of Edmund Berkeley presenting his Simon earlier in 1949. The Blinkenlights Archeological Institute gives a good overview about the first introduced personal computers.
| Computers evolved primarily for military, scientific, government, and corporate users with substantial needs…and substantial budgets. They populated labs, universities, and big companies. Homes? Small businesses? Not so much. Over time, however, costs dropped. Equally important, computers grew sophisticated enough to hide their complex, technical aspects behind a user-friendly interface. Individuals could now afford and understand computers, which dramatically changed everyday life.[6] |
Starting from this point Lemke and Brenner's evolutionary ladder describe and predict past, current and future changes in digital age. The networking of computers is the focus of the first phase. The invention of the Internet followed by its user interface, Berners-Lee World Wide Web, for the first time enabled a non-scientific use and (distant) access to online and computational resources.[3] The first website ever was republished a couple years ago and is still accessible here.[7] A more detailed introduction to the characteristics of the Internet and the WWW can be found further below.
Important for the digital Age is that information is handled as a resource and good, commonly managed, networked and accessible through the new media and finally changing societies into knowledge-based and information infrastructures. Accordingly Rheingold states:
| The most successful recent example of an artificial public good is the Internet. [...] The internet is both the result of and the enabling infrastructure for new ways of organising and collective action via communication technology. This new social contract enables the creation and maintenance of public goods, a commons for knowledge resources. The personal computer and the Internet would not exist as they do today without extraordinary collaborative enterprises in which acts of cooperation were as essential as microprocessors.[8] |
It were changes like this and the constant craving for innovation such as the invention of the smartphone, that has deeply embedded mobile and online networking in our society and even led to an always-on culture.[9]
Finally the concept of the Internet of Things slowly replaces personal computers trough intelligent items that should support one's activities unconsciously.[10]
In combination with advances in virtual reality technologies the fourth evolutionary stage predicted by Lemke and Brenner is heralded. The question left open is how the digital age will change in future and when will it end in order to give space to a new era?
Characteristics of Digital Media
[edit | edit source]In order to exemplify what influence digital media has on private and public spheres, the characteristics of this media type have to be determined first, specifically how it differs from traditional media types like print medias (i.e. newspapers, magazines, printed books) or analogue medias (i.e. film and audio tapes, radio, television). As this book focuses on the Internet, there will also be a closer look to the characteristics of this specific medium.
As digital media all media types are counted which are based on digital information and communication technology (i.e. the Internet) as well as technical devices for
- digitalization
- recording
- processing and calculation
- retention/storage
- presentation and
- distribution
of digital content and final products such as digital arts or music.[11]
| Examples for digital media | ||
| Type | Examples | |
| Storage Medium | CD, DVD, Disk, USB Stick, FlashCard | |
| Devices |
| |
| Networking | Internet, Mobile Network, Social Media | |
One can also say: "Digital media is the product of digital data processed electronically, stored as a file, and transmitted within computer systems and across networks."[12]
Digital information is coded in a binary system using the only signs off=0 and on=1. Digital information of all different kinds can be presented through the application of this arithmetic and can be copied perfectly as many times as wanted with no degradation of quality. But therefore firstly a digitising devices is necessary to convert analogue signals into digital data [12] and as well as device for reception and manipulation afterwards.
Although often used as a synonym for Internet, the World Wide Web is only the Internet's user interface established by Tim Berners-Lee. Berners-Lee determined, that each website in the network is assigned to and accessible through an unique address, the Uniform Resource Locator (URL). Content then could be connected through cross references, the hyperlinks, which contains the URL.[13][14]
This non-linear so-called hypertext structure enhances the interactivity over the Internet, thereby being primarily a pull medium with content, which can be accessed time - and place – independently as well as self-determined. Generally, this approach is available on every part of the Internet, but search engines can help users selecting it. This differs from traditional media such as the television, which follows a time-dependent programme [13] and is only receivable in the reach of the broadcasting frequences.
Nowadays the Internet connects people all over the world on a communicative but also interpersonal level. Via offers like instant messanging, social media, email or webblogs, people can communicate one-to-one, one-to-many or many-to-many,[13] meaning varying between interpersonal communication and mass communication. Additionally, communication on the Internet is reciprocal and interactive; sender and receiver can exchange roles without time delay. And basically everyone with Internet access can present their own content (even anonymously), known as user-generated content. In contrast, the press and broadcasting are institutionally organized; interactions are therefore media initiated (i.e. via letters to the editor) and the reactions of the audience is time delayed.
McLuhan’s theory says, that the new media contain the old ones [15] and no medium does this more obviously than the Internet: Countless crossmedial offers like web TV, video-on-demand or online newspaper are mostly just digitalised offers of the traditional medias. The digital content form on the Internet asks for technical aids for the reception (Computers, mobile final products) [16] but it also holds a higher reproducibility and possibility of saving.
Uncoupling of Space and Time
[edit | edit source]| Analog | Digital | ||
| Media Space | Type of Time Space |
|
|
| Relationship in Space |
|
| |
| Mode of Presence | Presence Method |
|
|
| Society |
|
| |
Firstly introduced by Thompson,[18] this term is used to indicate new convergent technologies’ ability to bend the space-time continuum. In its most specific forms, it signifies the ability for media users and produced information not to be constrained by geographical and temporal boundaries. While this is not a new event in the history of technologies, the development of Internet-based media has certainly accelerated and further separated this two concepts from each other. Indeed, while in nature the where is inextricably linked to the when, the modern era has firstly disrupted some of this limitation:[19] TV broadcasts, telegraphs, telephones and radios first permitted to spread a message to further 'where' and not necessarily at the same 'when', with pre-recorded programs and advertisements but the medium itself had to have a fixed and public 'where' such as a broadcasting station.
Notably, it's only in the new digital world that the perception and cognition of time and space as two tied notions has been allowed complete separation, while also changing the experience that we have of them in our social and everyday life. In fact, transformation of these two concepts is fundamental to understanding the interrelation of a public and a private sphere, both among humans interactions and the way we make sense of the world for ourselves through news outlets and information acquisitions.
For instance, we no longer need to be physically present to a public place to attend an event but we can do so from our own private and personal sphere, which is geographically restricted to i.e. our home or office. We can also attend simultaneous events through access to Internet livestreams, with always more websites providing this service even in a non-pay-per-view format, such as YouTube #Live.
Likewise, we can get public information and news from all over the world in real time without accessing mainstream media institutions but relying on people who themselves are geographically based there. At the same time, we can too invite the public into our private sphere and entertain quasi-face-to-face interactions within our sphere.[20]
Similarly, the digital age also makes us less bound by time. Events that formerly required our physical presence at a certain time, can nowadays be recorded and as digital information, which is easily copied and distributed, and can be watched delayed and multiple times.[13] Accordingly, whenever people invite others into their private sphere, it is not necessary that all parties are present at the same time, but messages and information can be stored by digital media[13] and accessed with a time shift. Consequently publicity through digital media does neither need the physical nor the simultaneous presence of all parties.
However, even on media with time-invariant programmes, such as television, broadcasting services can send small filming teams to live events and then air the programme time-delayed and repeatedly (see broadcast delay). This is enhanced through digital recording possibilities, which are nowadays accessible for private customers as well, and the possibility to reproduce and upload digital information without degraded quality to a wide spectrum of digital broadcasting platforms. For instance, the app Periscope allows private users to broadcast to their followers anywhere in the world whichever event, protest, scene that is happing near them. The broadcast is also recorded and can be seen from anyone who looks up its title for up to 24h. Commenting on it, the creators explicitly said that they wanted to build the closest thing to tele-transportation. [52]
Therefore, whichever the message, senders both institutional or private, can get into the public sphere and target their public audience more precisely:
- They are less time-bound even on traditional media platforms.
- They can choose the right time and right media platform either convenient for them or for the audience.
- They reach a high coverage through greater OTS.
Concluding, the way these two spheres, the public and private, whose interconnection has characterised our lives for centuries, bear now a new appearance thanks to the disruption between temporal and spatial constraints.
Mobile Privatization
[edit | edit source]Mobile Privatization describes the connection between an individual and a mobile device that connects it to his private environment and creates a feeling of a 'comfortable zone' within the usage of that device. The term mobile can be seen as a non-geographical setting of privatization as people can transfer their home, which is originally seen as a building with four walls in each room, to every place that is connected to the internet.
Zizi Papacharissi describes in his book [20] that 'within this private sphere, the citizen is alone, but not lonely or isolated. The citizen is connected, and operates in a mode and with political language determined by him or her.' This act of privatization can take place everywhere the individual uses the device with a private reason. This can be a phone-call or even a photo which is being shared on Facebook.
Sharing and filming plays an important role in the current ongoing privatization of public places. A reason for that might be the 'uncoupling of space of time' argues John Thompson.[18] Content can be watched everywhere and everytime so that people don't need to meet anymore to know what the other is doing. Raymond Williams describes the term of mobile privatization as 'the ability media offer audiences to simultaneously stay home and travel places'.
This movement started with Selfies when people took photos of themselves in order to share it with their friends. This conflict between of private photos made public using a device that can connect to the World Wide Web. The next developments are Vlogs in which people start documenting their lives using a camera and upload their videos to a public sphere such as YouTube. This form of mobile privatization can be seen critical as people can decide which parts of their private life can be seen online but on the other hand they have no control of who can see these videos.
Castells [21] explains that 'The mobility of this private sphere further permits that everyday routines be interlaced in ways that render the individual reachable anywhere and anytime, in a way that may "revolutionalize" control of everyday life'.
Therefore mobile privatization can be a fitting description for an ongoing movement in the society but although a threat of losing control about our everyday life.
Digital Photography and Picture Sharing
[edit | edit source]With the advent of digital photography, public and private spheres are becoming interchangeable and what used to be intimate and private is becoming public. For instance, as smartphones are becoming accessible to anyone, people can take pictures or video wherever they are, thus breaking the boundaries of other people’s privacy. People can take photos of strangers or of themselves and then show these pictures on websites like Flickr or Deviantart, making them available to strangers. As this kind of practice is becoming very popular, the concern about privacy issues related to it has attracted media attention.[22]
Despite there is not a general law that forbids people from taking pictures of people in public and subsequently publish them (unless the person photographed is identifiable), people involved in this practice against their will might feel like their privacy (or private sphere) has been invaded.[23] From a research carried out by Edgar Gomez on Flickr, we can clearly see how taking pictures of a stranger without a consent from that person might generate conflicts. The girl whose photo was taken without her knowing it, in fact, got upset when she found out that Flickr users had started a forum conversion with two photos of her with the title: "Someone Knows Her?".[53] From her point of view they were breaking her privacy even though she was in a public space when the photo was taken. This is also a relevant point regarding social media and pictures being posted without the consent of the person actually in them.
According to Alan Westin, when people are in a public place, they are still seeking for anonymity and they try to find freedom from identification and surveillance.[24] Therefore being in a public space does not mean that everything we do is public, on the contrary, we still expect some privacy and we do not think that we will become the focus of attention or that someone will record us and publish picture of us on the web.[23] However, the users of the internet, used to the big amount of self-portraits and to the related disclosing facilitated by new technologies, apps and social networks, do not find sharing their private lives with strangers a problem,[22] hence they feel free to break into other people’s lives.
One popular social network recently created has been Snapchat. It is an application on smartphones where people can take "selfies" and videos of anything they wanted. On some levels, Snapchat could be considered private. Videos and photos can’t last more than 10 seconds, and after that the video or photo disappears. However in those 10 seconds, the recipients of the Snapchats can quickly take a screenshot and thus invading someone’s trust and privacy.
When Snapchat was first created, it had no option to reply anything people sent to another. As it grew and developed so did its options, and the medium evolved and a reply function was added. This therefore can allow any one to repeat a Snapchat as many times as it wants. Thus losing its purpose of the original idea of the app. Furthermore, Snapchat can be seen as one of the most private social networks due to the fact that others may only follow you on it if you give them your unique username. It is far harder to be found on Snapchat than it is on more public sites such as Facebook, thus meaning that the limited audience on Snapchat is something that you create yourself.
Different from Facebook where anyone can find yourself with just your first and last name. With digital media it is very difficult to find a site that is completely private. Snapchat can be seen as more private than others because it’s most likely that only your closest peers will have access to your Snapchat, so only a handful of people have access to the videos and photos posted. However, under the "Terms and Conditions" of Snapchat it has been noted that Snapchat can keep anything posted, and use it.
User-generated Content
[edit | edit source]User-generated content (UGC) (also known as user-created content or user-driven content) comprise all digital content that is created, edited and published by the users of websites instead of the website´s publisher. This includes "any form of content such as blogs, wikis, discussion, forums, posts, chats, tweets, podcasts, digital images, video, audio files, advertisements and other forms of media that was created by users […]".[25]
Right before the internet was mainstreamed the content was pre-selected and edited by publishers of the mass media and their recipients only consumed the content in a one-sided, passive way.[26] But the fast diffusion of the Internet in the early 21 century and der rise of Web 2.0 driven technologies [26] have mainly enabled the development of the web to a “participative web“.[27] As part of this fundamental change towards user-driven technologies, the phenomenon of user-generated contents occurs and leads to a shift or new trend concerning the supplier of content online. In the early years of the internet, the majority of the content was coordinated and created by paid and professional administrators of websites. Due to this, the usage of the internet was limited to a passive use of the existing content. This form of one-sided publishing is still relevant and is applicable to a majority of the content that is provided online. Emphasised through the emergence of social networks and further user-driven platforms in 2005[25] the user-generated content phenomenon was pushed with the effect that the content is merely “pulled“ by users rather than “pushed” on them.[26] Nowadays internet users produce and share content at a high rate and do not merely consume it as several surveys reveal. “[27]
The Organisation for Economic Co-operation and Development (OECD) has defined central characteristics that outline three criteria that user-generated content needs to fulfil:[27]
- publication requirements state that the work must be published in some context on a publicly accessible website or a one that is only accessible to a selected group (e.g. social media sites)
- creative effort implies that that users must add their own creative effort and value by creating content. This also includes if users are adapting existing content to make it a new one as a kind of collaborative work
- Creation outside of professional routines and practices emphasis that work should not content any institutional or commercial market context
There are different formats of user-generated content that can be divided into four categories:[28] texts, photo and images, audio and music as well as video and film. The most common format of user-generated content is the text type. Thereby the users create original texts, poems, novels, quizzes or jokes or just expanding the existing work and share this with the community. Most of the content are published on blogs, social networks or on websites as a kind of review. In this case, the phenomenon of fan fiction is important. Further increasingly important types are user-created photos and images. Most of them are taken with digital cameras or smartphones and shared on platforms like Instagram, snapchat, Pinterest, Flickr or Facebook.[29] Those uploads are maybe manipulated with several photo editing software. Self-created music, mash-ups or remixes of existing songs to a single track as well as podcasts belong to user-generated audio and music content. Besides of photos user also produce or edit video and film content. User provide homemade video content, remixes of pre-existing works or combine those two forms. The most important hosting platforms in Europe are Blip.tv, VideoEgg, Dailymotion, YouTube, Veoh and Google Video.[30]
The distribution of user-generated content takes place on many different platforms and serve different purposes. The following chart shows a selection of distribution platforms for user-generated content and their characteristics.[27][31]
| Platform | Description of the user-generated content | Examples |
|---|---|---|
| Blogs | Blogs contain newsgroup-like articles that were updated at frequent intervals. Postings consist text, photos, audio, video, or a combination. Blogs resemble a cross between diaries, newspaper editorials, and hotlists where owners write down information important to them | Blogger, Tumblr, WordPress, Nucleus CMS, Movable Type |
| Wikis and other collaboration formats (text) | Websites where user add, remove, or otherwise edit and change content collectively | Wikipedia, Wikibooks, PBWiki, JotSpot, SocialText, Writely |
| Forums | Platform where people talk about different topics | 2channel, Yahoo! Groups, phpBB |
| Group-based aggregation | Collecting links of online content and rating or tagging collaboratively | Digg, reddit, BuzzFeed |
| Podcasting and video sharing |
|
|
| Social network sites | Sites allowing the creation of personal profiles and where users interact with other people in terms of chatting, writing messages, or posting images or links | Facebook, Twitter, Instagram, VK, snapchat |
The user creation movement, in addition, influences the way how traditional mass media work and emerges new forms of participatory journalism.[32] Despite its originally non-commercial context, user-created content has already changed to be an important economic phenomenon, too.[27] Companies try to develop and establish successful business models based on UGC, like the video-sharing website YouTube. In cooperation with really successful YouTube stars, they connect the user-generated videos with advertisements and generates more than $200 million ad dollar per year.
Ownership of User-Generated Content
[edit | edit source]One of the issues with the internet is the ability of people being able to take content such as literary work, art, music or videos and upload or repost it without the artist's credit. The internet also gives them the opportunity to take credit for these works. Copyright laws state that this is in fact, illegal, for 'the author of any work is the first owner'.[33] This includes work that is posted online.[34] However, despite these laws the internet has made it extremely easy to bypass these regulations. There are thousands of instances where artists online, such as photographers, have to put watermarks on their images, lower the resolution and size or confront art thieves in order to protect their work. There are websites which tell artists that they have the right to start a lawsuit, however, this is often an expensive and long process and may not always be a feasible solution. It is difficult to locate thieves of small, online-artists and writers and file law-suits against them. That could mean tracking them down via an IP address which could come from anywhere in the world, followed by high costs in lawsuits. The internet has therefore made it increasingly difficult to legitimize the credits that certain creators deserve, regardless of the copyright laws.
However, it is more difficult than just having art stolen, for the lines of copyright are very blurred when it comes to things such as parodied videos, images from television shows that have been altered, fanart and other fan labor. In fact, people have profited off of the art and literary work they have produced inspired or including ideas from books, TV-shows and films, such as Fifty Shades of Grey. Certain fan-art forms are seen as theft, such as taking clips from a TV-show.[35] Creative commons licenses can offer some leeway in these situations, but that is not always the case. Here it becomes difficult to decide what counts as theft and what counts as artistic expression. On the one hand, the original content of such an art form is not made by the user itself, but because they transform the art and create a new kind of art, new user-generated content has been created. There are organizations that support the idea that these transformed artworks are indeed legitimate content that should be credited to the user.[35] However, the debate remains difficult to whom the art truly belongs to; the original artist, or the user who altered it.
Narrative of the Self
[edit | edit source]Dramaturgical Representation of the Self, Ancient Greek Theatre Notion of Persona
[edit | edit source]The word persōna is the Latin equivalent of the Ancient Greek word πρόσωπον(Prosopon). The Greek word itself is composed by the preposition pros- which stands for ‘towards’ and the word ops- which usually is translated with the words hole or eye. Hence, Prosopon can be translate as face (that which is before our eyes), front, character and appearance but it can also mean mask, personality.
Even though the etymological tie between these two words is conjectural, the modern conception of persona still relies on its original Greek meaning.[36] In fact, when we talk about the concept of Persona, we usually link its meaning back to the Theatre of ancient Greece and to the notion of mask. In the Classical Greek period, the word Prosopon was used to mean both the mask that actors wore in order to play different characters on the stage and the human face.[37]
The mask’s function was to depict the main characteristics of specific characters so that the audience could understand the characters’ role.[38] In an open-air theatre, like the Theatre of Dionysus, the very intense, extroverted expressions of the masks with wide-open mouths were able to bring the characters’ face closer to the spectators, thanks to their features.[39] Moreover, the shape of the mask itself formed a resonance chamber which not only allowed the audience members in the distant seats to hear the characters better, but also created a connection between the character and the theatre. Furthermore, it lead the human body behind the mask to a metamorphosis, hence the human face became the mask.[39]
During the theatrical performance, the actor had to vanish into the role of the character. The actor had to become the character in order to establish a particular kind of interaction with the public. Starting from this concept of theatrical performance, Erving Goffman compared the way people construct their own identity in everyday life with the way actors perform characters.
In The Presentation of Self in Everyday Life, Goffman employs a dramaturgical approach in his studies about human interaction. Interaction is viewed as a performance and it depends on time, place and audience; human beings therefore act accordingly to some cultural beliefs depending on their environment.[40]
One of Goffman’s key concepts is the distinction between private and public, which are represented by the back region and the front region. The back region can be considered as a private or hidden space where individuals can be themselves and where they do not need to act in a certain way or conform to social norms.[41] Whereas the front region corresponds to a public space where people have to perform a specific identity and where performers are on guard, careful not to give the wrong impression to the audience.[42]
In the Digital Age, it is not only physical spaces, such as a classroom or the stage of a theatre, that fall into this category, but also social networks and online communication. The way human beings perform their identity online is not too different from the way they perform the self in real life situations. In fact, nowadays, people can influence the impressions others have of them in many different ways online. For instance, individuals can decide not to share some information like their age or location on their Social Network; can set their privacy settings so that different people will only see certain things on their social media accounts; and can manipulate their pictures so that others will have a specific opinion of them and view them in a certain way. This conscious or subconscious process was already present in face-to-face interactions and it is known as Impression Management.[42]
Goffman coined this term, which can also be associated with the concept of self-presentation. According to him, impression management is about “successfully staging a character”. In order to create a perfect theatrical character, actors “must subscribe to a variety of concerns to foster a desired impression before their audience”.[43] Goffman adopted the term Personal Front in order to describe one of these concerns, which consists of items needed to perform, items “that we most intimately identify with the performer himself and that we naturally expect will follow the performer wherever he goes”.[44] Presumably, Goffman had in mind the Theatre of ancient Greece,[45] as the performance he described recalls the performance typical of the ancient Greek Drama where the use of the mask was crucial in order to stage and become a character.
Different Personas for Different Audiences: Jungian Conception of Mask
[edit | edit source]With all the advantages that social media and other forms of online communication offer us, there also comes a certain pressure to 'perform' online; to present a version of yourself to the internet and subsequently the public. This is something psychologist Carl Jung defined as a persona, or a 'mask', that is explored in Two Essays on Analytical Psychology.
Indeed, Jung identified the persona as the mean through which the individual establishes a relationships between himself and the outside world. However, it constitutes a partial way of connection because it does not have to necessarily match a person's self and ego. This is the reason it is often referred to as a mask: although it retains properties of the person who wears it, is mainly functional in relation to the social role that it is meant to entertain. According to Jung, is perfectly normal from a psychological point of view to have a persona and it is indeed fundamental for the development of the individual and the society which he is part of. In fact, it represents a compromise between the high demands that sophisticated social relationships require and what the person wishes they would be or they wish they could appear to be. Therefore, it is a system of behaviour that is partially dictated by society and partially dictated by the expectations and wishes of oneself regarding oneself.[46] It is easy to see why the notion of masquerading fits so well with the performance individuals stage online, all playing different roles at once.
Human beings are complex, meaning no one form of social media allows us to express every persona or element of our personality that we can exhibit in real life. The invisible and often anonymous nature of online communication means that people can present any persona of their choosing and this can be liberating for some. Theorist Adrian Athique's arguments tie into those of Jung. Athique comments in his book Digital Media and Society: An Introduction that the "social norms guiding group interaction had the potential to break down online, primarily due to the loss of visual cues that defined the social hierarchy." This is a noteworthy argument. For many, there is nothing holding people back online. People who are perhaps introverted and anxious in public and social interactions can find a sense of freedom online, a chance to put on the 'mask' that they are not able to do in real life and say things on the internet that they feel they can't in person.
Jung sees the persona as a real and honest way to both free an individual and also conceal their 'true nature'. The way that we navigate our online worlds and present these personas online, however, is complicated. Audiences, both in person and on the internet, will all receive a slightly different persona from one another. You probably would not feel comfortable speaking to your employer the same way that you would speak to close friends. Social media can be restrictive in this way. Having not only your friends, but also family members and both current and potential employers on networking sites such as Facebook means that is unlikely you will can truly be yourself, as you have a variety of audiences to please and entertain using only one or two of your 'masks' and online personas.
The internet can often restrict the image you present of yourself on any one social media site. This can be why people usually have multiple online accounts on a variety of sites, from Tumblr to Pinterest. Different sites are aimed at different audiences and can often limit people to only one of their personas. You are encouraged to share and explore different elements of both your personality and your life in different spaces online. What people express on Twitter they may not feel like they can post on Facebook. Different groups of the public require a different mask, from professional to personal. Networking sites purely for job hunting and professional pursuits are emerging, a popular site being LinkedIn. These kinds of audiences obviously would be presented with a different persona than the ones exhibited on more casual social media sites. Jung himself observed that every different profession and occupation require a different set of characteristics and personas.
Our social identities are fluid and evolving, and it appears sometimes that the nature of certain social media sites does not allow for us to present all of our 'personas' at once. Social media allows people to create an online space, privately or publicly, to be whoever they want to be and to wear whichever mask they want to wear. Different audiences in different areas of our lives all receive a different interpretation of ourselves in real life, and this does not change online. Different masks suit different situations both online and off, and your online persona may be closer to your true self than the image you portray to people in the real world. Nonetheless, Jung warns us, it must be maintained that identification with oneself’s persona is detrimental; the subject must be conscious that he/she is not identical to the way in which they appear through their persona. If not, that is if this persona freely controls a subject unconsciously, a discrepancy might arise between the way one appears in different contexts and in the way in which one perceives himself in relation to others. This too can happen online, with equally serious consequences.
Narcissism and Asceticism
[edit | edit source]The mythological character Narcissus was seen as an example to avoid, especially in Ancient Greece where the self-absorption and selfishness on the citizens’s was seen as detrimental for public values of community, democracy and political participation. Indeed, although self-expression was considered a powerful tool for people to contribute their opinion in public places such as the Ecclesia (ancient Athens), a self-centred opinion was not accepted.
Time has passed, but narcissism is still often described in negative terms. However, Papacharissi,[20] drawing from Richard Sennett and Christopher Lasch work, argues that in a social media context narcissism does not necessarily retain its pathological and pejorative characteristics. Indeed, it works along side of post-modern values of autonomy, self-expression and control and itself favours a need for introspection and self-centredness that relies on the rapidity with which the subject can shift or merge the private and public sphere. That is because, unlike in ancient times, narcissism of this form is self-directed and self-based but it is not in itself pathologically selfish. Namely, while it does favour auto-promotion and presentation, the social media tools of which the subject makes use through personalisation are not by themselves intended to benefit the subject directly: recognition happens through others. Other issues might emerge from the amount of possible personalisations of a topic in terms of reliability within a democratic debate, but these narcissistic practices, whether they take the shape of blogs entries on WordPress, Facebook profiles or Twitter updates, they are fundamentally part of a search for contact among different subjects.
However, contrary to the opinions expressed in the ecclesia, what social media users announce from their pulpit is not finalised at contributing to the public sphere; these opinions might be used to monitor civic engagement and to a certain degree they do constitute a form of political and social expression of one’s thoughts, but first of all they are based on self-fulfilling evaluation of content by those who produce them. Similarly, according to Lasch these tendencies, unlike pathological behaviour, arise from a sense of insecurity and self-interrogation that cross the boundaries of public and private and which cannot in this sense be oriented to exclusively selfish desire. Notably, this form of narcissism arises from desperation in a society that does not provide a clear distinction between public and private [47]
This can be explanatory of the recent phenomenon of Selfie, where just the name itself speaks for values of self-referentiality and self-absorption. However, despite several critiques about selfies promoting narcissistic behaviour and hubris in those who post them,[48] the phenomenon has also been identified as a form of re-assessing and re-assuring self-esteem through sharing with others. This presents this interpretation of narcissism as something far from disorder and more as new way through with the self projects itself into the world by a self-controlled mediation.[49] Analyzing why people post 'selfies' can take away from the fundamental fact that in many ways they are a form of expression. For many, a 'selfie' is an act of self expression, celebration, liberation and autonomy, rather than a ploy for attention or praise.
At the same time, Sennett identifies narcissism in this sense as a form of asceticism.[50] Drawing from Heinz Kohut work in psychology, Sennett suggests that narcissism is less a clinical condition and more a preoccupation that one has of his self-hood and the role of the self “as a source of initiative, intentionality and unity for the personality” plays.[20] What Narcissus is looking for when he drowns, Sennett argues, is certainly his self-image but at the same time this self and its depth is an alluring form of “Other”.[50] That is, the reflected image presents a self that is more deep, interesting and seductive than the original one. The Image, that Narcissus sees and construct of himself exits the inside world and wants to reach out to him and be apprehended, drawn, out of the water. Therefore, self-absorption is not selfishly fixated on psychological interiority and magnification, but rather it concentrates on that surfacing image which appears more likeable and intriguing. This is the image that Narcissus wants the outside to see and the one he wants to be recognised for. Despite a sense of lack within the self, Sennet identifies the ability of the self to take interiority as a starting point for withdrawal from its own self in search for a better image as a form of asceticism. Namely, the subject who retreats from its self manages self-examination and reflection on itself, thus promoting self-understanding and autonomy.[50] Nonetheless, Narcissus, as preclusively closed and stagnant towards activities that do not revolve around the self and its characterisation in the ways explained above, eludes an active public sphere.[50]
Private spheres as an environment of autonomy, control and self-expression
[edit | edit source]“Participating in a MoveOn.org online protest, expressing political opinion on blogs, viewing or posting content on YouTube, or posting a comment in an online discussion group represents an expression of dissent with a public agenda, determined by mainstream media and political actors. It stands as a private, digitally enabled, intrusion on a public agenda determined by others.”[20]
In this digital age, society have been given the tools to speak freely on the internet. Once users have gained access to posting within a private sphere online, individuals gained the control over their audiences. On sites like Instagram, Twitter and Facebook, users have the autonomy to craft a public image to a select audience. The privacy settings on these sites allows users to privatise posts, and gives them a sense of control over their own content. These social media sites are the only place people can exhibit and experience total self control as they can choose what they say and how they present themselves.
Photos posted online are a good example of the images people can construct of themselves and their lives and then present online. For example, on Instagram there are many filter options and ways to edit a photo being posted, as well as. If photo is edited in some way, it could mean that the portrayal of the user's life is edited for the public eye online. People can choose to omit certain details of their lives online. Facebook profile pictures are chosen to show the best angles, and is the photo that represents users to their "friends" and any other strangers who may click on their account. The privacy of Facebook means users have the control over who they are friends with, and in turn who sees their posts. However, even profile pictures and cover photos are outwith the private sphere of this website, so, when choosing these photos people tend to have the idea of the public sphere in their mind, and thus having control over how the public sees them as well as their audience. Many of the photos and opinions that people post on social media may not be suitable for every one of their online audiences, which is something to take in to consideration regarding the subject of self expression.
In relation to the previously mentioned quote, using online forums for personal expression is another way in which the private sphere can be used. The possibility of becoming anonymous on a website and giving opinions could be considered part of the private sphere, as anonymity is protects personal image. The private sphere gives people the chance to express themselves in a digitally enabled community. This aspect of anonymity can be liberating for many people, who may be reluctant to speak out freely if they had to do so in public. This sense of confidentiality can be encouraging in both negative and positive senses. Negative, as people are more willing to be rude or 'troll' other people online when they know they will not be caught out. Positive, as it may give people a sense of confidence to express their beliefs.
For many, social media accounts may be the only place that a lot of people get to exhibit and experience total self control. They can choose what they say and how they present themselves and are able to create private online area that can encourage creativity and self-acceptance. The public and private versions of individual's online selves can differ, meaning that many social media users begin to 'craft' a version of themselves to present to their online audiences.
The way in which people can present themselves among their peers within a mediated environment could potentially mean an issue with realism. Creating personas on Facebook, Twitter and Instagram can be construed as painting a false image of yourself and also what real life looks like. Despite the positives behind posting on a private page, within a gated community, it can be argued that people are still using this as a way to create false personas to impress their followers.
It can also be argued, however, that it is within these online gated communities that people are often able to express their true selves and communicate with people that they believe to be more on their wavelength than the people they know in real life. Depending on the audience they may be catering to online, it can be believed that many people do not seek out a place online to 'perform' or show off, but a place that they have created themselves where they feel safe enough to present an image and persona that is closer to who they truly are than the one they exhibit in day to day life.
Identity Performance and Management of the Impressions of the Self
[edit | edit source]As Erving Goffman explains,[44] the individual who is part of a social group and in the immediate presence of other becomes at once initiator and part of a staged performance. Within this performance, the individual will intentionally or unintentionally express himself, and the other individuals of the group will in return be impress in various way by him. While the impression that the individual gives off cannot be entirely predicted in the way it will be received, the main interest for the subject is that to try and construct and impression that is consistent with the way in which the subject wishes to be seen.
That is, the subject works to influence, in its formulation, impression directed at others in the attempt to have them receive the impression that was meant to be conveyed, thus also shaping the situation which the recipient finds himself in. However, sometimes a subject might. In addition, the degree to which the subject disclose certain aspects of their life, thus censoring some information and making available others through a form of “crafting” of the represented-self, enormously shapes the perception given. Within this performance, the observes too have a role that doesn't comply with merely observing, The spectator, whom is part of the spectacle, knows that he's being allowed to perceive and knows the his perception serves the performance, but at the same time, even more if he's a performer himself, he knows that something is being hidden. However, his role is confined to the front region and he cannot access the subject’s backstage. Nonetheless, if the observer is enough close to the subject, he might disrupt, even unintentionally, the constructed impression that the subject has tried to give to themselves, thus resulting in the subject embarrassment. This could be the case when, for instance, pictures in which the subject has been tagged on SNS differs a lot from the staged self-presentation that the latter has crafted.[51]
The Impression Management process that the subjects controls, therefore, inevitably concerned with the dialectic of social relations. For this reason, the subject has to satisfy his desire for control with regard to the situation and ways in which his own self-representation will be perceived by others. However, just like he has under-played and over-played some aspects of their representation, so have done others too in the role of subjects, especially in the way they feel about him. Therefore, all the relevant social data about other in order for a complete control are unavailable. In their absence, the individual tends to employ cues, tests, hints, expressive gesture, status symbols that works as predictable devices for his characterisation in others’ minds. Indeed, to avoid a by-product impression of his representation, the subject has the option to reframe their representation in a way that the observer will be manipulated by those cues, Sign and Symbol in his interpretation. That is, a sign can be employed by the subject in the absence of knowledge of what the observer’s interpretation of the sign’s signified would be. For this reason, a convincing impression is not necessarily concerned with what the subject is or has but these elements can be engineered enough to convince, in their absence, the observer that they are indeed possessed.
In regards to presentation of the self and impression management, Goffman has stated: “people give a ‘performance’ when they allow themselves to be photographed, in the sense that they make allowance for a public that will ultimately see the photograph.” He uses the term ‘performance’ to refer to ‘all the activity of a given participant on a given occasion which serves to influence in any way any of the other participants’. The 21st century has brought the introduction of Internet and therefore new Social Networks, such as Facebook. Through websites such as these, society has managed to use photographs unconsciously and consciously to express themselves in various forms.
There are many contributing factors that go into taking and choosing photographs that one may decide to put online. A process has been used in Chalfen’s Snapshot Versions of life (1987):
- Planning
- Editing
However, after analyzing Mendelson and Papacharissi’s “Look at us: Collective Narcissism in Facebook Photos”,[52] there is more than just planning, posing, shooting, that goes behind uploading a picture on any Social Network Sites (SNSs). Media gives the opportunity for people to express themselves in various forms. “While people are purportedly presenting themselves, they are presenting a highly selective version of themselves. Social Network Sites (SNSs) present the latest networked platform enabling self-presentation to a variety of interconnected audiences.” (Mendelson and Papacharissi) SNSs allow people to present themselves different for different audiences. For example, in some cases people create multiple versions of Facebook, one for their parents and one for their peers. As well, people edit their photographs according to who their audience may be. Consciously and unconsciously people work to define the way they are perceived by others, hoping to cause a positive impression. For this to happen, have to put effort in their appearance, the way they act, and try to hide their flaws. Uploading a profile picture, or any photo, is a process because it represents who a person is. A deciding influence to choosing a photo to upload is the thought of who will be seeing it. For example, having your grandmother on Facebook stops one from posting photos from a social night that only your social group would find amusing.
Donath and Boyd define SNSs as: “online environments in which people create a self-descriptive profile […] Participants in social networks sites are usually identified by their real names and often include photographs; their network of connections is displayed as an integral piece of their self-presentation.” The more personalized photographs individuals take emphasize how they wish their lives to be remembered. Consciously and unconsciously individuals transform themselves before the camera; portraying a version of ourselves we hope to be. In networked environments that blend private and public boundaries, like SNSs, Facebook, inadvertently communicate content of a performative nature to a variety of audiences.
Celebrity Culture
[edit | edit source]The demand for celebrities to be part of the ‘always-on’ culture is continuing to grow. The demand is ever increasing from fans for interaction with celebs. An interesting quote completely sums up this point about the effects which social media has on celebrities:
>>The most important thing about a technology is how it changes people.<<— John Lanier[54]
This demonstrates the matter that once celebs become successful, technology is the first tell-tale of their identity, their social morals and how their success impacts them as people.[54] In fact, many celebrities have built their entire careers around 'always-on' culture and the power of social media as a platform that encourages celebrity culture. Nowadays, 'celebrities' are developing through sites such as YouTube, SnapChat and Vine.
Due to every celebrity’s massive succession, fans feel the need to have a constant connection to their idols. This puts a constraint on celebs to be always available and connected to their fans, providing what is deemed to be appropriate content. Celebs face massive challenges involving the type of content which they post online and what is seen to be the ‘right’ opinion.
This can result in people losing their sense of identity and conform to society's ideology - post appropriate content, always looking ‘perfect’, have the ‘right’ opinion and convey a positive image. Although social media provides many advantages for us to reach many different people, it is still limited to time and amount of attention we have at one moment.[9]
A key point to be made here is that technology is less political and more about power and social status. Technology becomes the centre to influence of succession and technology acts as a base to build social status across the globe, key to all celebs. Celebrity dominance over all aspects of social media has led to a noticeable imbalance of power, and encourages the belief that celebrities are deities rather than human beings who make mistakes online.
This can also lead to a narcissistic image of celebrities. The attention which celebs receive on a daily basis is massive and so it is likely a transition will take place: a change from a ‘normal’ everyday user to an obsession of self-image and a focus shifted to them and who they portray. The mediation on images and publications is so selective and the majority of the time it is not in the control of the celebrity but in the hands of their manager.
As expressed by Lanier, newspapers are in decline so more value is now being placed on the internet, which could be problematic.[55] People are much more likely to check social media above any other source according to a report by the Pew Research Centre.[53] The priority which social media takes for news is a rising issue for celebrities as major platforms are notorious for spreading news either correct or not.
Trolling is one of the biggest issues connected to celebrities and their privacy online. Particularly on social media, trolling is extremely common. Either fan bases or the opposition could pose to be a celebrity and therefore create a fake account or page based upon this person. This is problematic as celebs personal information is up for interpretation and this is also how spread - leaving the celebrity with no control or privacy rumours. This can lead to misrepresentation and becomes much more personal online.
A common theme among celebrities due to social media and access to information and data is leaking of harmful content. This is a growing problem for celebrities as journalists and media users are abusing there power in order to gain hidden content. An example of the way that the internet can be used to abuse the platform that celebrities have been given is the hacking of female celebrities and subsequent leaking of nude and private images. Women in the limelight are targeted and violated by different forms of media and have their private property stolen and leaked online, where the images will last forever.
"The incredible amount of activity in contemporary culture that explores the boundaries of the personal, the private, the intimate, and the public resembles the discourse of celebrity but expands pandemically beyond that realm because it deals with the general population." - David Marshall [56]
Social media also instigates 'stalking' on celebrities. The ability to access open pages, interpretative pages of a celeb and profiles creates a path for celebrities to be stalked, with all of their information at major risk. In a study of stalking and psychological behaviour, it was made clear that the main access and vocal point of stalking is media. “Stalkers of celebrity figures are the sensation of the popular media, particularly if they have threatened or been violent toward the object of their pursuit.” [57]
Celebrities convey this idealised culture; a culture which in many ways is desired by others and is that of luxury and high style. However, in other ways celebrities do attempt to show a 'normal' life narrative; make them more human. This narrative may include instances where celebrities pose doing activities which the average person might or associating themselves with brands which the 'common' person may like. But, what really distinguishes celebrities from the average person is the level of publicity they receive and this is out of their control. Once someone has delved into the deep end of celebrity culture, all privacy is out of the window.
Online Identity - Pushing the Boundaries of Public and Private
[edit | edit source]Our online identity and the identity we take online can change our usage of the Internet; this narrative of us changes the functions of the digital media. The narrative of self is important to create boundaries of public or private in our online usage. The self that we choose to create and display online is beginning to place boundaries on the public and private functions of the Internet and due to our growing society, has changed our perceptions of public and private.
One form which our online identity can take and is most popular is that of open source. This means that our profiles are available with lots of information about us published, pushing the boundary of private. This factor can make being private more difficult because of the amount of information the user has allowed online. Additionally part of our online appearance is out of our control, i.e. shared information, that companies track down. And as characteristically digital data is easily copyable,[13] one cannot restraint, that these companies or people, we shared content with, spread these further - our private sphere is extended to a part, that is invisible to us. Another point of concern is perhaps the inherent nature of sharing on social media, in that we can never truly control what circulates on these sites about our private lives. Often information is published on social media by both individuals and larger companies without our permission. To a large extent we have no control over the images that are posted of us without our knowledge or consent. It is in this way that our online identities are shaped into something that we perhaps do not recognize or support.
So our perception of public means that we believe our information to be available to everyone, and anyone can view our content. However, since this is becoming more acceptable, it needs to be made more aware of the dangers of being public online. This is pushing the boundaries of public as the type of user we choose to be alters this public stance.
Online identity is the make- up of our character online and who we choose to be online. The choice of sharing real life information can alter privacy or oppose it; can change the publicity as we may choose to reserve certain information thus making our profile more private. The information that we choose to make either public or private about ourselves online can shape the identity that we create and then present to our online audiences. (see section 1.7.2: Altered Narratives of the Self)
So, this brings about the question to what extent our identity defines privacy? Are we really private if we still have information online? This question highlights the boundaries to which social media pushes privacy and shows that despite being private on Facebook for example, we still need a profile picture and basic information.
This can also be linked to key theorist Hamid Van Koten who suggests a link between identity and culture. He implies that what we choose to display about ourselves and choice of public or private says a lot about us as people and our identities and our culture.[58]
As society evolves, we become more controlling over our social media and we gain more agencies over our own profiles and the way we use and display our information online. This raises issues of responsibility online. Since we have so much control, are we fully to blame when something goes wrong?
The problematic issue of fraud can be very common among users with reports in America in 2014 showing almost 50% of people are being hacked into a year. Social media programmes are changing so much that the company itself is moving away from being the first to blame and more the user. So, in turn it works two ways – the user gains more control and power but in return, they are responsible almost entirely for their problems online.[59]
Publicity Online
[edit | edit source]Whereas the radio needed over 30 years to reach 50 million receivers, the Internet succeeded that in less than 5 years (see infographic).[60] With that in mind the question is, how the Internet as a hybrid medium [13] creates and enhances publicity and what effect this has on the private and public sphere. In our discussion we need to consider the following dimensions of publicity:
- Publicity in the sense of a public room anyone can enter
- Publicity through public communication and public communication systems
- Publicity as in public opinion
The demand for publicity came up historically as a monitoring tool for and legitimation of political decisions. Therefore a sphere has to be created open for any topic and where everyone can equally, reciprocal express his/her opinion.[61] The Internet like no other medium offers through various information channels a forum for (political) discourse, that in theory anybody can access. Additionally, the roles of speakers and recipient are changing continuously especially on social media platforms and the variety of examined issues is huge.
Creating such a room also means creating a communication system, that in earlier days could be a marketplace: Public communication, closely related to mass communication, is aimed to be transparent and therefore accessible for anyone. Normally they imply a huge and anonymous audience,[61] which makes the reach, reflection and impact of the message immeasurable and uncontrollable, but with online tracking tools and the possibility to immediately reply on i.e. social media the possibility to verify the online audience increases. However, as the Internet connects people all over the world, the audience is nowadays more disperse. According to Schulz this are in fact real public spheres, as they are international in comparison to presence public sphere, which are only segmented public spheres, likewise the marketplace.[61]
Public communication differs from private or secret communication, as the access to the message of communication or the communicating situation is openly accessible[61] – but facilitated by the high copyability of digital media[13] private messages can be published to a bigger audience even without each other’s consents.
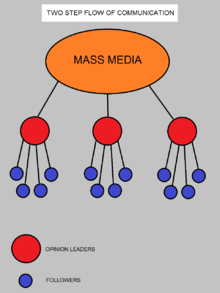
A public opinion is in commons sense the dominant opinion, which is enforced through public communication. This has to be distinguished from a published opinion, an opinion expressed in public, making it especially online accessible for everyone.[61] Mass media can mirrors the public opinion, but with Noelle Neumann's spiral of silence in mind, this does not has to be the thinking of the majority.[62][63]
However, the premise for publicity online is the that every group of interest has access to that sphere. But the digital divide precludes that, because not everyone has a technical devices with Internet access, nor the time and ability to deal with the technology (digital analphabetism) or information overload; the latter hinders the finding of websites, that are not search engine optimized.
Public Displays of Connection
[edit | edit source]People displaying that they are connected to other people isn't a new thing that has come with the digital age, it has been around for years as we are always eager to let people know that we have friends. In recent years showing our connections has changed however, with the introduction of social networks.
Facebook in particular, with the introduction of tagging people in photos, has made it easy for users to showcase their friends/connections to the world. This has been around for a lot longer however, even on the internet, if we refer back to Bebo users had the choice not only to choose their top friends but also to choose an "other half". Myspace allowed users to choose their top friends, in the article Public Displays of Connection [64] look to find what these displays mean and what they represent in the modern era. The article talks about first the public displays of connection we use in the "real" or "physical" world which includes introducing our friends to each other, because we either think they will become friends with each other or admire each other, which in turn means they will admire you for having a friend like them. This could be through hosting a party and bringing your friends together or even by something as simple as name dropping.
On websites like Facebook there is the ability to tag in photo's but also displaying "mutual friends" is a huge part of the site. When a user adds you as a friend, you can see what mutual friends you have together. This may be the first thing users look for when deciding whether or not to accept someone as a friend, as you can see how many similar friends you have and if you're likely to know them or meet them in the future. Twitter also introduced this with the "Followers You Know", followers are similar to friends on Facebook however someone can follow you and you do not need to follow them back and vice versa. The "followers you know" feature displays all of the users that you follow who follow them also, which, like the Facebook mutual friends may affect your decision on whether or not you follow them back. Research by Konstantin Besnosov, Yazan Boshmaf, Pooya Jaferian and Hootan Rashtian of the University of British Columbia [65] showed that whether not the user had mutual friends and the closeness of the mutual friends was one of the most important factors in deciding to accept their friend request.
Although closeness of the mutual friends is an important aspect in deciding whether or not to accept someone's friend request it is difficult to distinguish the relationships between the mutual friend and the person who has sent you a friend request. As boyd and Donath [64] talk about in their article just by looking at mutual friends there is no real way of knowing the connection. A mutual friend could range from a best friend, family member, partner to a relative stranger who they perhaps have only met once or twice, if at all.
Tagged photo's can be a more effective way of finding out a persons solid, real life relationships with your mutual friends. Tagged photos give a user a better idea of the kind of person someone is, what social circles they belong to and if they are someone that they either know, are likely to meet at some point or perhaps want to know. Tagged photos and photo's in general are a huge part of displaying your connections to your digital circle. In their research Beznosov, Boshmaf, Jaferian and Rashtain [65] found that the very first thing someone looks for when accepting a friend request is their profile picture.
Most people would look for a profile picture with them in it, however the rest of the photo's available on their profile are also hugely important. Picture's, specifically tagged ones, can prove the authenticity of a person and their profile and can basically prove or at least convince someone that they are "real". boyd and Donath [64] talk about this and say that displaying connections on your profile is a way of verifying your personal identity.The more connections someone has, mutual friends, tagged photos etcetera makes them seem more like a real person. With the rise of catfishing (see section 1.7.2.3)this is something that has became more of a concern, increasing the importance of connections being displayed on social media profiles.
boyd and Donath also talk about how these connections could also help showcase "incompatible" connections [64] meaning you could look at someone's mutual friends and tagged photos to quickly see who they are and who they assosciate with, and if you do not like what you see you are able to make the informed decision of declining their friend request. The opposite of this is also true.
You could also look at displaying connections on your profile as a way to assure other people that you are popular and have friends. Many people will not only tag themselves in photos, but also with the addition of Twitter's "@" tagging method you can tag your friends in general posts on Facebook and start public conversations with them using this over Twitter. People display their public connections in this way because they want people to know how many friends they have and who they are. Public displays of connection mainly are not about who your friends are but are always trying to reinforce the idea of who you are.
Democratic but not Democratising
[edit | edit source]The characteristics of digital media, which shape the new relationship between the private and public sphere, also touch upon the concept of democracy and citizenship. Indeed, a private sphere enabled with mobile privatisation, de-spatialised simultaneity and that integrates values of self-expression, control and autonomy inevitably interplays with the concerns of the public sphere. We can identify two major trajectories among the ways in which digital media influence and at the same time are conditioned by civic life.[66] The first one considers how the internet is a communication tool that can be used in campaigns by parties and candidates and thus serving certain political agendas. The second, instead, seeks to understand the role and the effects of new media on one’s private sphere and participation to public sphere, that is one’s individual civic and political behaviour within a democratic society. Understanding the relationship between these elements is important and is currently the object of research.
Putman explains that an individual’s participation in offline social networks, such a bowling team, not only fosters interpersonal trust and cooperation but also offers to the people that are part of this network the chance to discuss and exchange political, social and economic opinions and beliefs that ultimately, on a larger scale, serve values of community and democracy in the real world.[67] Here, we can easily see the intended comparison between offline and online social networks and also notice that this activities are transported in the online world. However, the way in which this transfer actually takes place is controversial. For instance, Bimber argues that that while new media lower the cost of accessibility and divulgation of political information, therefore potentially giving more people the possibility to engage in a civic debate, on the internet the same disparities of the real world are often replicated: engagement comes from those who already have the means to both afford access to internet sources and the knowledge required to be engaged in a political or economic argument.[68]
In this sense it worth mentioning Jürgen Habermas’ interpretation of the internet’s commonality. Initially, in The Structural Transformation of the Public Sphere Habermas too falls into the trap of thinking that the internet is free from the real world’s disparities. In fact, he attempts a historical comparison between the public sphere of the bourgeois in the 18th and 19th centuries and the internet. While he does explain that subsequent consolidation of hegemony within the bourgeoisie has changed this decision-making procedure, he founded his analogy with the internet as based on the bourgeois’s public sphere’s openness to all and its formal principle of disregarding class hierarchies in the name of arguments that prevailed because of better argumentations rather than because of coercion.[69]
Salter dismisses this comparison.[70] Firstly, it only remarks both the internet’s and bourgeoisie acceptance of disparities: indeed, the public sphere of the bourgeois was only formally open to all, as for example women where excluded from participating. This is certainly in accord with disparities which the internet and social media have been already accused of. For instance, boyd and Hargittai explain how even social networks like Facebook, although accessible by almost everyone, have a built-in demographic bias, both because internet access and literacy is required to be part of it and because, from the beginning, Facebook had as user-base constituted by academics from privileged american institutions and thus has a fundamental american-bourgeois element to it.[20]
Secondly, while the bourgeois’s public sphere was intentioned to find a political common will, the internet seems to fragment or question the idea of universality and common interest, hence facilitating the exact opposite: a pluralism of wills.[70] Papacharissi too argues in favour of this interpretation.[20] She explains that the interrelation of private and public sphere, facilitated by digital media, allows for values of autonomy,control and expression to determine our social-networked conduct and to let us blend with the public space. However, the degree to which these values serve democracy is questionable. In fact, because they satisfy ego-centred needs and function as an expression of personal opinions and beliefs, they are potentially and always more easily (unlike within the 18th bourgeoisie) applicable by everyone to everything. Therefore, they progressively distance themselves from a 'common will'. That is, while they might be democratic in affordance, they do not inherently make society better unless the pluralism of self-serving private spheres that broadcast themselves onto the public sphere actually come together to serve the public sphere selflessly.
Public and Private Spheres As A Political Power
[edit | edit source]Government intervention within media channels and legislation impacting on networks has created discourses concerning its political validity and judgement of power use. Such discourses include the reasoning regarding the control of a libertarian networked environment and employed strategies used within the media framework that serve to uphold a political perspective or agenda.
Political Power and the Public Sphere: The Media
[edit | edit source]There are three distinct concepts of mediation that governments use to serve vested interests or uphold perceived standards as set by a political power. These concepts are:
- Authoritarian Concept. This concept dates back to Gutenberg's invention of the printing press and is the oldest media concept. Under this concept the press are subject to direct or implied control from the state. Forms of diversity are harmful and irresponsible to a countries development, and any gathered news must not criticize or challenge leadership in any way.
- Communist Concept. Under control from this concept, published news has to concentrate on nation building and the goals and policies of a society set by leadership. The characteristics of this concept included the press being one-party, incoming and outgoing news are heavily controlled, news must be positive and further party goals rather than refle|cting interests of the people and, it is a means of exercising control over the people aided by secret police.
- Developmental Concept. Traditionally used in underdeveloped and poorer countries. The Developmental Concept states that mass communication should aid with nation building and fighting illiteracy and poverty, media should follow government rather than challenge it, each country may restrict flow of news between borders in an attempt to limit incoming information from western countries that may threaten cultural traditions, and have control over content about themselves.[71]
Political Power and the Private Sphere: The Network
[edit | edit source]Since the 1970s governments have heavily monitored online activity in an attempt to halt criminal activity. However, within the last two decades the objectivity of criminal activity has been blurred and replaced, in some societies, by the subjectivity of a leadership's definition. Even with influential figures such as Dr. Vint Cerf -one of the fathers of the internet- stating that government control over the Internet will fail,[72] this has not hindered governments from inducting their own policies regarding how individuals and groups can use the network, most notably the Chinese government. In 1993 the Chinese government initiated the Golden Shield Project in an attempt to legislate and control access to the internet within the Chinese mainland. A variety of methods were implemented with the aim of censoring the internet which included:[73][74][75]
- Blocking IP addresses. Certain IP addresses will be denied and effects protocols such as HTTP, FTP and POP.
- Filtering and redirection of DNS. Certain domain names are blocked or incorrect IP addresses are returned via DNS hijacking.
- Portal Censorship and search result removal. Major portals such as search engines are effectively blocked. The Chinese government have censored access to Google. In 2006 Google launched Google.cn in an effort to maintain a presence within China, however due to increasing demands over censorship and Google being the subject of hacking by the Chinese Government, Google ended its Google.cn service in 2010.
While China practices extreme measures of censorship, further measures have been taken by other nations. In 2011 Egypt disconnected itself entirely from the network in an effort to reduce the power of protesters rallying against the Mubarak regime. Such action was deemed necessary after an uprising in Tunisia which has been dubbed the Twitter revolution.[73] The actions of censorship and complete network disconnection exhibited by the Chinese and Egyptian Governments are political tactics that maintain asymmetrical power as the aforementioned actions do not benefit society as a whole,[76] and only proves that despite the political rhetoric, governments do possess the power to control the internet and intervene within the sectors of society that individuals are granted control over.
The Chinese and Egyptian government's intrusion into the private sphere has effectively expanded the reach of the public sphere by disarming users of the network control over produced and viewed content. A prominent example is the banning of Facebook and Youtube by the Chinese government. Both sites operate within the private sphere as they allow for virtually unmediated control of produced content by outside organisations. They subsequently now fall under the domain of the public sphere; controlled so heavily they are completely inaccessible. Further impositions include regulation of internet cafes, as these establishments now enforce age restrictions. Users must be over the age of 21, and a log book is required to be signed by each user. Once online, activity is heavily monitored. Such restrictions have brought about the conception of underground internet cafes, where underage users can freely access the network. However, access to the network is the only element of control experienced by users, even within the confines of an underground establishment, content is still heavily mediated and monitored.[73]
Public and Private Spheres on Social Media and Political Agendas
[edit | edit source]Political Agendas and Digital/Social Media
[edit | edit source]In Politics, the rise of Digital media and Social media usage has allowed for politicians and political parties to pursue, promote, and campaign for certain political agendas. Due to the nature of digital and social media creating their own unique concepts of private and public spheres, politicians and political parties now utilise these spheres in order to pursue their chosen agenda(s).[77]
Political websites, e-mails and social media platforms are now some of the most common methods of political communication. In order to inform individuals of their agenda, for example a manifesto, party policy or campaign, the first place this is now published is usually on the party website, and advertised further through e-mails to party members, supporters, and volunteers. Internet technologies like this are the main ways in which parties and politicians now spread information amongst their members and supporters.[78]
Whilst other, more traditional methods are still widely used to spread a political message, such as news programmes, leaflets, and face to face communication,[79] the fastest way to do this is via an online medium, i.e. the internet. This can be done through a number of methods;
| Method | Description | Example |
|---|---|---|
| Party Website | A dedicated website domain for a certain political party, organisation, or politician. usually where information is first posted, where individuals can go to to find out information about a party/politician, political agenda, campaign, or issue. Also where individuals can register to join or support a party or politician. | [54] |
| A dedicated public page for a party or politician to share information about themselves or a political agenda, and where other Facebook users can 'like' the page to show support, and 'share' information from the page to their timeline. | The Official Scottish National Party (SNP) Facebook page | |
| A social networking site where parties or politicians can have their own Twitter feed to promote their agendas, and where they can further promote their agendas by creating a hashtag for users to follow. Other Twitter users can engage publicly by sending a tweet to the party, or privately through Direct Messaging. | [https://twitter.com/unitetheunion Official Twitter of the trade union Unite | |
| Online Petitions | Various websites which allow any individual, including politicians and political parties, to start a petition in order to campaign about and raise public support for an issue. | Change.org, A website which allows users to start, sign, and share petitions online. |
Although politicians and political parties use all of these methods, as social media has such a large audience which is not restricted to just members and supporters, this approach is becoming increasingly popular.[80] Therefore, much of the information on any political agenda is then spread by the party or politician themselves, members and activists on social media. This can be an extremely successful method of promoting a political agenda.[81]
Viral spreading of information online is another method used both socially and politically to reach wider audiences, and this is done so through platforms such as Facebook, Twitter, Tumblr and other popular social media sites. This is a method of spamming, which can be done through consistent advertising, whether that is paid for or spread by online celebrities to reach a wider audience. Social examples of viral spreading include youtube videos e.g. Anything posted by the notoriously known 'viral video creator', Tom Fletcher, or shocking and exciting images that were perhaps posted online in order to become 'viral'. As it seems, contemporary audiences of political announcements tend to discuss or voice their opinions online via social media, therefore this viral spreading of political messages will be best received through such platforms.
Working Tax Credits
[edit | edit source]Take for example the recent campaign against cuts to Working Tax Credits in the United Kingdom, organised by The Labour Party in opposition to the Conservative Party's plans. The vast majority of the work to mobilise individuals and communicate information in this campaign was through social media platforms, e-mails, and an online petition. This allowed the campaign to become very widely known and supported in a short period of time. The outcome of this campaign was that the Conservatives had to scrap their plan to cut the Working Tax Credits scheme.
Public and Private Spheres in Relation to Political Agendas
[edit | edit source]Peter Dahlberg argues that there are a number of different Internet based public spheres which contribute to modern political communication, including;
| 1. Versions of e-government, usually with a top-down character, where government
representatives interact with citizens and where information about governmental administration and services is made available. While interaction may be relatively constricted, it can still at times serve as a sector of the public sphere. This sector is sometimes distinguished from e-governance, which emphasizes horizontal civic communication and input for government policy. 2. The advocacy/activist domain, where discussion is framed by organizations with generally shared perceptions, values, and goals—and geared for forms of political intervention. These include traditional parliamentarian politics, established corporate and other organized interest group politics (e.g., unions), and the new politics of social movements and other activists. 3. The vast array of diverse civic forums where views are exchanged among citizens and deliberation can take place. This is generally understood as the paradigmatic version of the public sphere on the Net, but it would be quite erroneous to neglect the others. 4. The prepolitical or parapolitical domain, which airs social and cultural topics having to do with common interests and/or collective identities. Here politics is not explicit but always remains a potential. Clearly, there is no absolute way in which the boundary between the nonpolitical and the parapolitical can be drawn, since it is always in part discursively negotiated and changeable. 5. The journalism domain, which includes everything from major news organizations that have gone online (e.g., newspapers and news programs) to Net-based news organizations (usually without much or any original reporting) such as Yahoo! News News, alternative news organizations, as well as one-person weblog sites (also known as “bloggers”). Interestingly, the research literature has tended to focus mainly on deliberative interaction in terms of online public spheres and/or mass media journalism. We should not forget that the online journalism sector is a core element of the public sphere on the Internet.[82] |
It is the activist/advocacy domain and civic forums where political agendas and the utilisation of the public and private spheres of social media come into play the most. In particular, the contrast between campaigns which are shaped by the party or politicians, and campaigns which are shaped by 'ordinary' individuals. The way in which political parties and politicians manipulate what they share on private and public spheres and the influence this has on the promotion of political agendas is of particular importance.
The Working Tax Credits campaign was not only successful due to the high profile social media campaign, but also because it used the private and public spheres of the internet and social media to its advantage. By informing members and supporters with key information an tools through e-mails, the face of this campaign became 'ordinary people' being helped by a party, not just a Party campaign, and this became what is commonly known as a 'grassroots campaign'. These types of campaigns are normally more supported by individuals, as it is seen as more authentic and trustworthy than a slick political machine type campaign.[83]
- Publicly, due to the amount of 'ordinary' people sharing and supporting the campaign on social media, and all activities being run by ordinary people, this was outwardly a very grassroots campaign which won over the electorate.
- Privately, this campaign was run by The Labour Party just like any other political campaign, as they provided activists with all the materials, information, and instructions they needed to successfully front the campaign. This tactic is just one example of how public and private spheres on the internet and social media can influence political agendas.
This utilisation of how individuals perceive political agendas, especially through Internet mediums, is also used in more sinister fashions by political parties and politicians in order to promote an agenda. The most prominent example of this behaviour is political smear campaigns. This is where a certain party or politician will 'leak' information from a private sphere, i.e an individual's personal life, in order to discredit that individual, be it another party or politician, and promote an agenda within that expose. This leaked information is often untrue or taken out of context to suit an agenda, and therefore why it is a 'smear'. A privately orchestrated smear campaign can also be exposed by individuals, again in order to discredit the individual who planned the campaign and promote a political agenda. The use of smear campaigns and the exposing of a smear campaign are two similar yet different practices which show how political parties can promote an agenda through manipulating private and public spheres online.
John McCain's 'Illegitimate' Child
[edit | edit source]In 2000 during the Republican Presidential Nomination race, John McCain was set to to win the state of South Carolina against George W. Bush. This was thwarted however by one of Bush's strategists, Karl Rove, who orchestrated a 'whispering' campaign' via an anonymous online poll to voters which asked the question "Would you be more or less likely to vote for John McCain…if you knew he had fathered an illegitimate black child?" McCain was at the time campaigning with his dark-skinned daughter, Bridget, adopted from Bangladesh.[84] This campaign was a huge contributor to the result of this, which was that Bush did indeed win the state and go on to secure the Republican nomination.[85]
By circulating this untrue information into the public sphere online, Rove successfully manipulated the lines between public and private spheres via the Internet and managed to help Bush pursue his political agenda.
The Rise of Digital and Social Media in Political Activity
[edit | edit source]This political campaign tactic of manipulating public and private spheres online has become widely popular due to the rise of social media in political communication. Social media is now not only one of the main forms of distributing political information, but has also become a major tool for political engagement.[86] Through social networking sites such as Facebook, Twitter, and even YouTube, politicians and political organisations are employing creative and more accessible methods of engaging with individuals.
- Facebook is the largest social networking site on the Internet,[87] sitting at approximately 1.55 billion users as of January 2016. Increasingly, Facebook has become the place where more and more people are getting the majority of their political information from. According to a study by the Pew research Center, the percentage of Facebook users who classed the site as their main source of news had risen from 47% in 2013, to 63% in 2015.[88] Furthermore, around 66% of Facebook users are reported to participate in civic or political activities through this channel.[86]
- Public engagement
- There are a number of ways in which Facebook allows politicians and political party's to engage with individuals in a public sphere online. On a very simplistic level, Facebook pages allow an individual to connect with certain parties and politicians, keeping them up to date with political information through 'liking' the page and therefore seeing anything that page posts on their personal 'news feed' - similar to a homepage on a website. The act of 'liking' a page or post by a political party or politician also enables an individual to publicly show support for that particular party/politician or agenda. More complex functions of political engagement which can be constructed through Facebook include Facebook Q&A sessions with politicians, Facebook polls which allows users to express a public opinion on certain issues and inform the original poster of this opinion, and also "Open" Facebook groups,[89] which are extremely useful mediums where any user can join, see discussions and engage with - political types of these groups are useful for communicating information and campaign material, and also provide a valuable political debating/discussion platform for individuals.
- Private engagement
- Privately, Facebook offers a private messaging service, Facebook Messenger, where users can create a private discussion space through what is usually a public forum. This is particularly useful as it can allow political parties, politicians, and individuals to have more detailed, personal conversations about political issues, as there is less fear and risk of judgement from the public sphere.
- Referring back to the concept of Facebook Groups, Facebook also allows 'Closed' and 'Secret' groups. Again, the extra level of privacy granted by these settings often allows individuals to be more comfortable discussing political issues. Furthermore, this also allows for political groups themselves to easily organise, share materials, and communicate in a singular pace, without fear of 'infiltration' by those who seek to do them harm.
- Public engagement
- Similar to Facebook, Twitter offers a public platform for individuals to engage with political parties and politicians. Any user can send a 'tweet' to another user, including political parties. Twitter is useful as it limits each tweet to 140 characters, and therefore questions can be asked and answered very quickly, and political debates are very fast-paced.
- Twitter also pioneered with 'hashtags' which users can follow. By typing in '#[insert text]' in a tweet, an individual can contribute to a mass discussion on the same issue. Also, by searching the hashtag on Twitter, users can follow any discussion surrounding that topic. This makes Twitter one of the most accessible and fast-growing social networking sites for political communication and agenda promotion.
- Example; The Hong Kong 'Umbrella Revolution' - #UmbrellaRevolution
- Private engagement
- Twitter is much less limited with what it allows users to do privately. Direct Messaging (DM's) is Twitter's private messaging service, and this serves the same function for political engagement that Facebook Messenger does. Although, it does also have the 140 character limit, which can make it difficult to communicate detailed information.[90]
- YouTube
- YouTube, the Internet's largest video sharing platform,[91] is now becoming more popular as a platform for political agendas to be promoted in the online public sphere, with YouTube now even launching a political toolkit for campaigners an politicians.[92]
- Public engagement
- Videos on YouTube can be seen by millions of individuals. As videos are shared from YouTube to other social network sites also, it can make the possibility for political persuasion phenomenal. YouTube videos also allow for discussion and debate to take place via a comments section on videos which are uploaded.
- Example; The 2012 presidential campaign in the US.
- In this election, YouTube was extremely prominent in voter persuasion and encouraging political engagement. Both Barack Obama and Mitt Romney's teams were posting creative, tailored video content online, and videos containing the tags 'Obama' and 'Romney' were viewed approximately 2.7 billion times.[93]
- Private engagement
- Similar to Twitter, YouTube has sparse private engagement methods. There is again a private e-mail service, but that is about it. YouTube does however allow for any video to be made public or private, so the user does have some manual control over who they share the video with.
Political Communication Online
[edit | edit source]Following Maletzke's definition of mass communication[94] and Lasswell's model of communication,[95] political communication is that kind of communication, where political players construct messages, which are transmitted by means of technically instrumental media to a disperse audience and which are used by the latter and provoke an effect on those. But political communication can also go into the opposite direction, meaning citizens communicating to political players, or horizontally, between players or between citizens.
The strongest form of political communication is information with persuasion as a special form, which tries to influence the political participation.[61] Hence, political information uses the public sphere to influences the public opinion and finally the opinion of individuals in their private sphere. This section therefore focusses on the forming of public opinion through political communication online.
On the Internet the presentation modes are multifaceted in comparison with many other media types: Information is mediated with under through Youtube-videos, newsletters, Wikipedia or online journal articles, social media posts or pictures - adapting to different user preferences to acquire information. For instance, texts can be received slower than videos.
The crucial part of all offers are their digital characteristics. Not only does it facilitates the storage of information uncoupled of space and time, but it also enables the reproduction of the messages and an immediate (interpersonal) response by the audience, i.e. in discussion forums (see user-generated content). Consequently the public disperse audience and its public discussion are enlarged and networked: People can get in touch with opinions that they would never get to know in their physical public sphere and they can do so without moving out of their physical private sphere.
Catalysed by the possibility for everyone to become an author, public information is not filtered by traditional gatekeepers (i.e. journalists), but normal citizens can post about topic. On one hand they increase the diversity of opinions, but as they can become opinion leaders and as they often pick up information from mass media, they thereby create a double filtering of the public opinion (“Two-Step-Flow of Communication”).[61] Additionally the growing participation online worsens the information overload, so that search engines are asked to filter and manage the amount. Everything that is not registered by them belongs to the invisible web [13] - consequently search engines have a huge effect on formation of public opinions as well.
With regard to Wikileaks, one may think, that the transparency of the public sphere increases online, but it might actually worsen the spiral of silence:[63] Through public measurement tools, i.e. "clicks" or "likes", a public opinion is emphasised as highly supported, although it in fact he might be not.
Additionally, this kind of political communication is unproven in quality and validity (in comparison with institutional journalism; i.e. in Germany newspapers are only allowed to publish information, proven by two separate news agencies).
Finally the biggest weakness of the internet is, that it is a pull-medium.[13] Hence one can only reach those, who are already interested in and looking for an issue, that they have heard about before. The danger is, that people are informed one-sided and in combination with various possibilities to filter the information overload, they could be kept in an "political bubble".[96] The knowledge gap hypothesis adds, that people with a higher-education and political interest can receive information faster than people without these preconditions.[97] In combination with digital divide and digital analphabetism, through which a certain part of the world's population is excluded from "public" online discussions, the knowledge gap increases: Higher-educated and political interested people with access to and competence to deal with (controversial) political communication cultivate more and more, whereas people without these basis get less antithetic stimuli resulting in them staying in their political bubble. Therefore political communication strategies should be applied cross-medial, for instance setting an agenda in push media first to encourage as much citizens as possible to inform themselves further through online research.
Online-activism by Citizens
[edit | edit source]Online-activism, also known as Internet activism is commonly identified as a practice where politically motivated citizens use the internet and various online technologies to achieve certain goals. As explained by Sandor Vegh,[98] the strategies implied can be either internet-enhanced or internet-based. The former indicates a situation where the internet is used to enhance traditional techniques for protests, such as spreading awareness on a topic, creating e-petitions on websites like Change.org and call for action, either online or offline. The latter indicates form of activism that only happen online, like hackers's activities identified as hacktivism, targeting or protests against internet-related bans.
Online-activism generally divides in three categories, each of them emphasising different aspects of protests against someone or something, the people involved and the methods applied:[98]
- Awareness/advocacy: this category characterises the type of people who produce and receive information. The goal of activists in this part of the process is that to divulge information regarding certain topics through a distribution networks made of online petitions, Facebook pages, blogs or email lists. In this case, content producer are most likely to be individual citizens or independent organisation and they have as their main goal that of sharing and putting out for public condemnation those information which might have gone underreported or not reported at all, concealed by mainstream media because of an undemocratic regime, or internal cases such as breach of human rights. Similarly, online advocacy involves both spreading awareness and promoting a certain way of action. Indeed, it can focus on both asking for intervention on a singular case or for continual effort for a future and long-distant goal about a great issue, such as climate change. A form of advocacy is identified in lobbying which differs accordingly to the target of a lobbyist’s action. For instance, e-Advocates are groups of activist that offer lobbying on behalf of organisation and individuals that lack the internet knowledge and practices to successfully involve people in campaigns. This form of online-activism increases the scale of people that can be potentially informed and consequentially involved, either online or offline. Likewise, it is time- and cost- saving as it allows to use the internet to virtually spread a message. Moreover, through discussion pages and social media people can exchange information asynchronously and despite geographical constraints.
- Organisation/Mobilisation: this category includes two different ways of proceeding in regard to how the internet can be used for activist mobilisation. Firstly, it can be used to call for offline action, meaning that information will be provided regarding the place and time at which a protest or demonstration will happen. In this case the trajectory is online → offline. Secondly, it can be used to encourage actions that traditionally happen offline but that would have a better outcome if done online, such as requesting explanations and stating demands through emails, petitions and tweets with a specific person or company as receiver. Here, the trajectory becomes offline → online
- Action/Reaction: this category includes activism that can only happen online and often takes the form of hackers attacks, massive spamming campaigns and Smurf attack that aim at taking down or saturate the servers of entities identified as detrimental.
All these forms and steps of online-activism, especially if combined, can help bring about cultural, social and political changes. The degree of efficacy and duration of these changes remains debatable.
Forms and Platforms
[edit | edit source]As explained in Online-activism by Citizens there are two ways in which online activism occurs: internet-enhanced and internet-based activism.[98] Related to those forms are different kind of platforms where the citizen can participate to achieve the certain goal of the activism. Certain platforms can give ordinary people a voice to express their opinions and can encourage change. Therefore, each platform provides specific characteristics that can advance or even strengthen the outcome and purpose of the action. This section discusses several platforms and their usage as a kind of 'promoter', nevertheless this represents only a fraction of the most widely used platforms that are related to online activism practices.
Social networks are merely used as an additional communicative tool for arising awareness or to coordinate the traditional, off-line protest forms. Especially the usage of the two largest social media platform Facebook(59 billion monthly active users)[99] and Twitter(320 million monthly active users).[100] Users and activists can exchange text messages, video or audio files, photos and other information on their profiles. Word spreads quickly online and online fundraising can raise a staggering amount of money in a very short period of time if enough people back the cause and spread the information on social media. Additionally, activists on Facebook can join common-interest user groups, spread specific content and organise off-line protests or strategies for the action. Twitter and Facebook are separated in their opportunities for information sharing as Twitter is a micro-blogging platform, where user can declare messages with a maximum amount of 140 characters. The interconnected nature of Facebook and Twitter leads to an easier way of information sharing and can generate a huge amount of traffic[101] in a less time and cost-consuming way as well as up-to-date status.[102] A development related to the online activism on social networks and one of the strongest tools is the so-called hashtag activism as the use of them can coordinate the traffic and, in addition, function as a measurement tool. A research by Emily Vraga reveals that videos “can be shared easily, quickly, and effectively through a variety of other mechanisms, including e-mail, other social media, and even print media, and then watched at the viewer’s leisure”[103] via the platform YouTube. It further emphasis, that videos related to a political action can serve a “communal resource, informing, motivating, and connecting like-minded others”[104] as well as target new audiences precisely and boost viewership. Video sharing platforms provide tools to catch people´s attention as moving images have a more emotional driven effect. Such tools and platforms are also used for cause-related activism such as lobbying and fundraising.
Online-petitions (also known as e-petitions or internet petitions) are an extended tool of the traditional petitions as they are less time and cost-consuming and include the opportunity to reach and participate a bigger group of people. Those internet-based petitions also follow the purpose to protest against and urge for positive policy changes on any topic by sending them to the government or organisations. Thereby e-petition can be implemented through two forms: e-mail and world wide web.[105] The former sends petitions or certain information to subscribers or members of a website or platform based on electronic mailing list systems (so-called Listserv). The latter indicates websites like Change.org or Moveon.org where people can address a petition. When a website hosts a petition, visitors have to sign in electronically and are often required to give personal data like their name and e-mail. Furthermore, petitions like those on change.org or moveon.org could be integrated with social media channels and as a consequence achieve a higher participation. Since 2015, citizens in the UK are able to petition against the policy of their government nearly 7,190 petitions were registered and even 20 of them were debated in parliament.[106] Many NGOs or charities use online petitions, too, to reach their goals in environmental issues like greenpeace.com.
In addition, the mostly negatively associated form of hacktivism belongs to online activism. Originally this kind of activism “is a politically motivated single-incident online action, or a campaign thereof, taken by nonstate actors in retaliation to express disapproval or to call attention to an issue advocated by the activists.”[98] Hackers make use of denial-of-service attacks to get access to private or secret governmental information. As nearly all spaces of the public and private sphere depend on technologies that are driven by computer networks, attacks become more and more threatening. Regarding Sandor Vegh, hackers are divided into “wired activists”, just adapting the internet to their strategy and “politicised hackers”, adopting political causes as the justification of their acting.[98]
Effects
[edit | edit source]Some experts argue that the rise in activism online has caused a negative effect regarding the amount of activism that is done in real life. This so-called Slacktivism causes people to do less for their community as they feel 'satisfied by their participation in the low-cost online activism'.[107] Because of this, there is less activism in the public sphere outside of the online communities because people feel as if they have been doing their good deeds online. Furthermore, there are experts who argue that it is oversimplified to say that technology is the reason that certain activist movements are so effective.[108] An online revolution often does not help a revolution in the real world; face-to-face action is needed to help a cause move forward. Online communities are too impersonal and do not have the influence that a mob of demonstrating participants may have.
However, it can be argued that online activism has positive effects as well. It has become easier to use your voice through various websites such as Twitter, change.org, Tumblr and Facebook people are able to spread information and news about activism quicker than ever before. The effect of this is that a larger audience is brought into contact with views, issues and campaigns that are associated with certain online activist movements. In large protest movements, a great number of people can be contacted online and made aware of this movement, as the examples in the next sub-section will discuss. Though it might be difficult to join a demonstration in a city far away from you or help with a campaign in a different country, online-activism provides a platform for many people to have their voice heard regardless. It's a cost-effective way of spreading a message and creating dialogues; people are able to discuss, exchange ideas and offer different perspectives on the subject, and that without having to start an expensive, wide-spread campaign via for example radio or television. This can lower barriers for minority voices, creating a platform for a more diverse, large group of people.[108]
What online activism also changes is the way people protest. For example, people are less likely to go to a sit-in or to a demonstration, but they are more likely to sign petitions or tweet, e-mail or message celebrities, government officials or institutions or other important figures.[109] Important figures in the public have to be more careful what they post online, as a wave of comments on their tweets and Facebook posts is inevitable. This call-out culture is a key effect that online-activism has had. Everything that a public figure may post online is challenged or confronted if it is problematic in some way, causing them to be more careful and more aware of activist movements. This happens with people in every-day life, too; discussions on social media about political movements and social activism. Some people may deem this as a negative development considering it is difficult to post views online without it being commented on, others may argue that this way the online society can move forward and be more considerate of individuals and aware of different movements.
Lastly, online-activism can offer a different perspective from mainstream media. Considering that corporate media is an issue that causes companies to have influence in the media, the goals and stories of certain news articles cannot always be trusted. There are instances in which social media showed an incredibly different view of an event than mainstream media, for example with the #blacklivesmatter[110] movement. Online movements can provide information to those who do not trust the stories of the main news channels, or at the very least provide a different perspective from people posting live from events. Therefore, online-activism has created a different news outlet, and an individual information source when it comes to countless movements and organisation.
Past Events
[edit | edit source]Arab Spring
[edit | edit source]At the end December 2010 the Arab world saw an unprecedented series of social movements, protests and revolutions overall identified as Arab Spring.
| “ | Blogs and forums fueled the changes in the Arabian world, new media became the means for self empowerment. Still: The revolution took place on the streets. | ” |
Numerous considerations and studies have been made regarding the role and relationship between uprisings and social media networks for their diffusion and coordination. Namely, people interacted with each other and the world through various platforms that ultimately made the message uncontrollable by their regimes. Although the causes of people’s resentment toward their governments had already economic and political foundation, the triggering event happened and propagated online: Mohamed Bouazizi, a street vendor, on the 17th December in Sidi Bouzid, Tunisia set himself on fire in front of a government’s office in protest against officials violence, humiliation and the seizing of his goods and cart. Videos recorded on mobile phones were quickly posted on the internet, from where they spread across Facebook and Twitter gathering thousands of protesters first in the small town and eventually in the capital. The video, together with those of the spontaneous uprisings just few hours after Mohamed's self immolation [55][56], reached even satellite news channels like Al Jazeera.[112]
In similar circumstances, six months before the blogger and activist Khaled Saeed was beaten to death by the police while being taken from a cybercafe in Alexandria. Photos of his disfigured corpse were taken by his brother while visiting the morgue and shared online. After five days from his death, an anonymous activist created a page on Facebook titled We Are All Khaled Saeed and divulged the pictures. By the 15th of July more than 130,000 had joined the page, making it the biggest dissent page in Egypt ever.[113] Following these events, on December 18 youth activist Asmaa Mahfouz posted on YouTube video appeal to urge her fellow citizens to protest Tahrir Square with her on 25 January against the regime of Hosni Mubarak.
While it is difficult to isolate the amount of importance that each of these events from the way that they were shared, there is no doubt that how they were circulated online gave ordinary, non-activist people a way to connect with battles for human rights against government’s oppression and police abuse of power. Notably, “social media carried a cascade of messages about freedom and democracy across North Africa and the Middle East, and helped raise expectations for the success of political uprising, while people who shared interest in democracy built extensive social networks and organised political action. Social media became a critical part of the toolkit for greater freedom.” [114] In fact, social media platforms made it easier to involve people and get out the news for everyone to see and discuss, especially because newspaper and state television were biased and monitored. Indeed, all but one of the protests called for on Facebook ended up coming to life on the streets.[115] In particular Facebook was one of the primary source to both get information and organise protesters in the Arab regions, with an increase of 30% of users between January and April 2010, and almost double the users (27.7m against the 14.8 of 2010).[115] This strengthened both the volume of protests and the rapidity with which protests spread across the Arab world. Moreover, protest and supporters broke geographical boundaries boundaries thanks to social media: After Mubarak resignation, there was an average of 2,400 tweets per day from people in neighbouring countries about Egypt. In Tunisia, after Ben Ali resignation, there were about 2,200.[114]
The way the message has been spread across countries and people, the output and reading of unbiased information and the bypass of government’s hold during the Arab Spring represents one of the most important example of people coming together to advocate for democracy. This defines for dictators a new enemy: "If for a long time they had only political and fragmented ones, they now found opponents that use social media to identify goals, build solidarity and organise demonstrations.”[114] That is, if disagreement and anger among citizens have always existed, social media offer a tool to coordinate and push forward a reaction.
Hong Kong's Umbrella Revolution
[edit | edit source]The Umbrella Revolution or Umbrella Movement refers to the Hong Kong protests for universal suffrage and democracy that developed between 26 September and 15 December 2014 thanks to a group called Occupy Central with Love and Peace.[116] Similar protests in Hong Kong against the Beijing government had also interested almost half a million of people in July 2003, but, although having a successful outcome that managed to protect Hong Kong from China's interference, they did not have both the same growth and coverage of the Umbrella Revolution.[117] Indeed, protests organised in 2014 received a global network of online support and protesters themselves exceed locality and restriction in their manifestation events.
After being tear-gassed and pepper-sprayed by riot police in Admiralty two days after the beginning of protests, Josie Tao Cai-yi immediately shared what had happened to her online “First time I’ve actually witnessed the tear gas and pepper spray. Absolutely terrifying.” [118] This propelled a flow tweets in support of the Occupy Central movement, thus bringing it to global attention. At the peak of police intervention in riots, 12 tweets about Hong Kong were posted per second, with images and messages about police violent behaviour towards protesters being shown and shared by users all over the world.[118] This brought Scott Likens, analytics consulting lead at PricewaterhouseCoopers (PwC) China and Hong Kong, to comment on the events saying “we have seen progressive new ways to connect [on social media], serving the needs of something like this in real time... and making sure we’re always connected, [just so] the message can get out fast.” [118] In addition, Occupy Centre’s profiles on Facebook and Twitter, only two days after the beginning of protests gathered respectively 100,000 and 25,000 followers, followed by a series of pages aimed at explaining to anti-Occupy audiences the reason of protesters and convince them to join the cause.[118]
The way people started sharing images, tweets and videos of protests prompted Beijing government to censor both protesters and those who showed sympathy for them, with also almost a dozen of people being detained after scrutiny.[119] Censorship had as its main focus Weibo, China’s version of Twitters, with analytics reporting that only in September 28 the rate of censorship outweighed the one adopted in occasion of the 25th anniversary of Tiananmen Square. Because people were sharing pictures and videos on Instagram, access to the app was blocked, in agreement with previously arranged censorship in China of websites like Facebook and YouTube.[117]
As expected, this did not stop the protesters: virtual private networks were used to bypass the firewall and purposely misspelled words and codes were used to jump over targeted censor bots. In particular, protesters used Whatsapp to coordinate messages about meeting in one place at once. The app FireChat, which allows users to communicate through bluetooth and cellphone radio through mesh networking in a nearby chat,[120] was used when authorities tried to shut down mobile networks and cut off internet networks.[121] This meant that as long as phones remained in range with other, there was no way for authorities to prevent flow of messages apart from physically seizing phones. Only on September 29 FireChat users in Hong Kong were involved in 800,000 chat session and these were only the ones that were trackable. The company who owns FireChat in fact could only witness users who were online but once they wen off the grid, the actual number of people communicating was unguessable. More than 100,000 only in the first day had downloaded the app, with people using both for communication and to remain in contact with their families, as many of the early protesters were young people from the student community.[121]
In protests like 2014 Hong Kong Umbrella Revolution the Internet, convergent technologies and social media not only offer a powerful tool to fuel initiative, aggregation and coordination but also creates a window onto this events: if repression, censorship, violence from governments against its own citizens do happen, the entire world would be watching.
Occupy Wall Street
[edit | edit source]The so-called Occupy Wall Street (OWS) protest movement began in the late summer of 2011 in the Zuccotti Park, located in New York´s financial district and was mainly driven by online activism. The movement, which called for an end to the worldwide social and economic inequality and challenged the amount of corporate influence on government,[122] increased its global attention and participation through the usage of social media platforms like Twitter, Facebook and YouTube.
As the movement occurred, the international banking and finance crisis belongs to the past since almost three years and the Arab Spring was running for nearly six months. Among others, those events can be determined as influencing factors of the protest emergence. Kalle Lasn, executive editor of the Canadian, anti-consumerist, pro-environment magazine Adbusters, initiated the call for the first protest on September, 17, in the Wall Street district via Twitter. Nearly 5000 activists attended but the police pretended them to bore their way to the finance district's Wall Street. Nevertheless, the opponents succeeded in arranging a camp in the nearby Zuccotti park which from then on functions as the base of the protests.[123] The movement´s call for a more fairly tax system and diminution of the gap between rich and poor was supported by the slogan “We are the 99%“. This referred to income inequality and wealth distribution in the U.S. between the wealthiest 1% and the rest of the population that was stated by the economist und former chief economist of the World Bank, Joseph E. Stiglitz, a few months before.[124] This first actions in September did not receive a large media or public attention. That changed on October, 1, as the police arrested more than 700 activists because of traffic obstruction during a demonstration that should lead over the Brooklyn Bridge. This intervention causes a worldwide reaction and a large media coverage which can be seen as the breakthrough of the movement. In the following the movement swapped over to other countries all over the world. On October, 15 European movement activists from Madrid called for worldwide demonstrations as they claimed for an extension of the movements claims on the international bank and finance level. Finally, they achieved it to encourage people in more than 82 countries to join and support the occupy movement in less than one month. The movement could not achieve a noticeable change as the objective reasons are not solved until now.[125]
As described in Organisation/Mobilisation by Sandor Vegh,[98] the movement was partially but most importantly based on social networks to mobilise its activists for the off-line actions. Peter Dahlgren points out significant advantages or key tools as those platforms served the extent that occupies reach to other locations and turns out to become a component that facilitated an extensive web-based engagement, with much discussion or global linkage.[125]
By this, the usual kind of social media content consumer shifts to a “producer”,[125] as they are consuming information of the social media platforms but also produce own content user-generated content. The sharing of YouTube content via Twitter or Facebook and the sharing of current cell phone footage as well as historical archive materials were central to the developed social media practices.[125] From Septmeber, 17 to October, 10 the platform Twitter generated the following traffic.
At the end of October “approximately 70,000 results, including contributions from the OWS movement itself, as well as groups and individuals across a vast global political spectrum”[125] were yielded on YouTube.
Nevertheless, Dahlgren reveals that the actions of those political producers are involved in a continual process of adaptation while the user often ‘fast freeze’ the definitions of the mainstream. ”[125] Based on this phenomenon, the critic of the activism being less effective arises due to the fact the most of the activism remains to “clicktivism” or “slacktivism”. This argument of the activism lose in the actual activism movement was reinforced as the Occupy Wall Street movement has not produced the anticipated results.
Collective Action Dilemma
[edit | edit source]Howard Rheingold, born in Phoenix, Arizona, is a critic, writer, and teacher who specialises on the cultural, social and political implications of media communication such as the internet. He attended Reed College where he began his studied of his lifelong fascination with mind augmentation and its methods. In his book Smart Mobs, he talks about the developments of the internet and he addresses the idea of Collective Action Dilemma, particularly in Chapter two: Technologies of Cooperation.[8] He states that Mizuko Ito enable him to understand different behaviours regarding teenage groups and the use of mobile phones. He wanted to know how this type of activity could mean for entire societies, and so the majority of the chapter is based on a conversation he had with friend and colleague Marc Smith. He defines the Collective Action action dilemma as the perpetual balancing of self-interest and public goods. It’s a situation which would benefit many individuals but various factors such as cost and space prevent it from happening to one individual. The ideal situation is then that the cost is shared amongst others and creates a balance between this and public goods, which is a resource from that all can benefit from, regardless of whether they help create it or not. Public goods increase in value the more people share them.[8]
He also states that people who enjoy a public good without contributing anything towards it are called free riders. Rheingold quotes Smith who describes more about free riders: “If everyone, acting in their own interest, free rides, then the public good is never created, or it is over consumed and goes away. Everyone suffers. There’s your dilemma. What’s good for you can be bad for us."
Elinor Ostrom studied the way that people shared forestry in Japan and pasturelands in Sweden. Rheingold states in Smart Mobs that she defined eight ‘design principles’ of Common Pool Resources (CPRS’s)
| Group boundaries clearly defined | Rules governing use of collective goods matched to local needs | Most individuals affected by rules play part in modification | Rights of community to devise own rules accepted by Government |
| Community undertake monitoring to ensure rules are adhered to | Graduated system of sanctions used | Community have access to low cost conflict resolution mechanisms | CPRs in larger systems provision, monitoring and conflict resolutions are organised in multiple layers of nested enterprises |
These cope with free riding and have since been expanded to include a number of additional variables believed to affect the success of self-organised governance systems.[126]
Privacy on digital media
[edit | edit source]In an increasingly digital world, privacy is becoming a thing of the past. True privacy in the traditional sense, in the "real" or "physical" world is something that a lot of people strive for and previously were able to achieve. However, with the introduction of the internet we are given the illusion of privacy but seldom do we actually get it.
On the internet everything we do is tracked, all our information is stored and can be brought back at any point. Even if the user tries to delete it. Everything from our locations to our shopping habits is tracked and stored, and can be bought by companies. Although many users prefer not to be private at all and see digital media as a great outlet to publicly post about their lives, many users who feel like they have the option in actual fact do not. Privacy online has become something of an oxymoron because the two are completely incompatible with each other, this topic in the following sections will go on to describe how users cannot achieve real privacy in any form online.
Privacy rights and Awareness of Privacy Settings
[edit | edit source]When you are online, you tend to provide information about yourself almost every step of the way; this might range from your name to your address. The information you provide online is one similar to a puzzle with pieces of information that need to be connected before the full picture is revealed, for example, information you may provide when signing up to Facebook may be combined with information you may give when online shopping. When this information is all gathered together you may be surprised at how much one person can find out about you.
Global surveillance disclosures triggered a debate about the right to privacy in the digital age so it seems relevant that our privacy rights are explored in greater detail.
In one way or another we are all concerned with our privacy and our privacy rights online, as we all have aspects of our life we want to protect from others. So much so that it has become a fundamental human right and we have a duty to protect our rights. This article gives an in depth understanding of our privacy rights online.
In order to get an understanding of our privacy rights online it is important to consider the following things:
Social Networking- how do we utilise privacy settings in order to improve or distort our public selves
The three main ways in which you are likely to access the Internet are as follows; An ISP, a mobile phone carrier or a Wi-Fi hotspot. Every computer that is connected to the Internet has a unique IP address (Internet Protocol Address) and it is that number that actually allows you to send and receive information over the Internet. When you visit a website, the site can see your IP address which can in turn let the site know your geographical region. Moreover, there are ways in which you can block your IP address such as the website Tor Project
Furthermore, as technology is continuing to advance many of us now access the Internet via our smartphones. In this way you access the Internet using a data plan, which is tied to your phone service (Vodafone, Three, T-Mobile). Your phone provider collects data about your usage. Wi-Fi hotspots present serious security issues and it is crucial the terms and conditions are read before you set up a Wi-Fi hotspot.
Using Search Engines
Search Engines such as Google and Yahoo have the ability to track each and every one of your searches. They have the ability to record your IP address, the time of the search and the search terms used. Major search engines have weighed in on this debate by saying IP addresses need to be accessed in order to provide a better service and to combat fraud quickly and effectively. Google and Yahoo have now shorted the time they store this information from one year to 9 months.
DuckDuckGo is a search engine that “does not collect or share personal information” so there are other options available to us if you are concerned about your IP address bring tracked. They are not widely talked about though so if you didn’t know about them you probably didn’t think sites like DuckDuckGo ever existed.
Using Mobile Apps
Mobile Apps can collect all sorts of data and transmit it to the app maker or third party advertisers, which can then be shared or even sold. By installing an app you are allowing it to access certain data on your phone. Obviously, the first question, which many people ask is what data does it collect? These answers would normally be on the privacy terms and conditions, however, many mobile apps do not provide these terms and conditions. The data collected can include things such as; your phone contacts, call logs, Internet data etc.
Social Networks Facebook Twitter Tumblr
What do the majority of us all have in common? If you are one of the hundreds of millions of people using social networks, then there is a strong chance that you are linked to them through an online relationship. The information you share with your contacts online completely depends on you. However, you cannot control what other people do with the information you post online, and it is this secondary use of information that is posted online that is a major problem.
This website http://www.pewinternet.org/2013/05/21/teens-social-media-and-privacy/ goes into detail about the percentage of Facebook users that actually use their privacy settings and how aware of them they are.
By adjusting the privacy settings on your social media accounts to the highest level it can limit the amount of information leaked by secondary users, however, it does not stop it altogether. This brings up some debates surrounding how we utilise our privacy settings online to maybe improve the image of ourselves. For example, our online identity may be narrative or it may be real, online presence seems to construct a story of us but in many ways it also portrays a real view of ourselves. We need to ask ourselves, do our actual identities align with our online identities? Or do we utilise the privacy settings to to create a narrative of our life.
Facebook Tagging and Facial Recognition
One thing that social media users may be unaware of is that by tagging people in photographs on Facebook, many users may be unaware that not only are they making the pictures visible to an increasingly wide audience, but also helping to contribute to Facebook’s database and improve facial recognition technology. Not only an invasion of privacy to many, but an abuse of people’s understanding when it comes to the repercussions of tagging, which are not made clear to users. This application of cognitive surplus,[127] using the by-products of social media users seemingly harmless tagging, is contributing on a wider scale to invasions of people’s privacy and private spheres on a global scale. By (for the most part unwittingly) assisting Facebook to improve facial recognition technology in this way, it becomes increasingly likely that the online activity of individuals may become interconnected against their knowledge or wish, through what they are tagged in. Tagging could also become automated which would take away part of the control the user has over how their image is displayed in the public sphere.[128]
The ability for such technology to recognise a person from a single picture [57] could lead to individuals being searched online at random by someone who may, for instance, pass them in the street and snap a photograph. Putting this on the internet could bring up any amount of connected personal information they may have shared online, bringing the concern for safety and privacy offline as well. Management of settings or the ability to opt out can always curb these things but the lack of communication between providers and users is the main issue here- many are most likely unaware of how their activity may impact themselves and their circle in the near future, because this information is not widely circulated and is certainly not common knowledge despite the number of people it affects worldwide.
Beyond facial recognition even is the growing ability for Facebook to recognise and suggest tags for people by other characteristics such as their hair, their clothes or their body shape.[129] Individuals wishing to keep their physical identity private by declining to share or be tagged in pictures of their face for whatever reason are now having to jump through more hoops to maintain their privacy when they may only want to use the network to reach contacts rather than portray a full image of themselves online.
Data and Traffic Tracking
[edit | edit source]When using the Internet in the 21st century, individual privacy online is of key importance to users. In a recent study, it was reported that approximately 89% of Internet users are becoming increasingly worried abut their online privacy.[130] However, most individuals do not realise that most of their online activity is tracked through various methods, and that very little online activity is private. Data tracking, otherwise known as Behavioral targeting, is not new, yet;
"Most people have no idea this is going on" - Sharon Goott Nissim, Electronic Privacy Information Center
Websites, companies, and web browsers store personal information in a variety of different methods, and for a number of different reasons. Mostly, this is used to tailor the user's online experience to the things they want to see. However, as the specifics of information collected through these online data tracking methods is rarely publicised[131] outwith the collector, it is difficult to know whether that is all that our personal data is being used for.
Encryption
[edit | edit source]Encryption is a form of protection widely used by companies to protect personal data which they collect. Encryption can be used to protect data "at rest", such as information stored on computers, storage devices, and mobile phones. Encrypting personal data which is at rest in online storage helps protect it should any physical security measures fail.
Encryption is also used to protect data in transit, for example data being transferred via networks, e.g. the Internet, e-commerce, mobile telephones, Bluetooth devices and bank automatic teller machines.
This method of protection is now commonly used in protecting information within many kinds of civilian systems. For example, the Computer Security Institute reported that in 2007, 71% of companies surveyed utilized encryption for some of their data in transit, and 53% utilized encryption for some of their data in storage.[132]
Cookies
[edit | edit source]Now, when individuals click on or log in to a website for the first time, they may receive a message which states something along the lines of 'This site uses cookies, do you agree to this?'. Most users just click 'Yes' to get the message off of the screen so they can continue browsing, without actually knowing what they have just agreed to.
Cookies are small bits of data which are collected and stored by websites, web browsers, and social media sites whilst the user is browsing. Each time a user logs on to an account or clicks onto a website, the browser sends the cookie back to the server to notify the user's previous activity.[133] Cookies were originally designed to tailor users online experience, by allowing websites to remember important pieces of information about their activity. Cookies can also store passwords and form content a user has previously entered, such as a credit card number or an address; for example, Google AutoFill and similar tools are powered by cookie storage.
Advertisement Recommendations
[edit | edit source]From cookie storage came the development of advertising tracking and advertising recommendations. By analysing the stored data of what websites individuals look at online, what they put in their shopping baskets on Amazon etc., and what pages they like on Facebook, sites such as search engines and Facebook are able to promote certain products which they think the user would buy/enjoy, based on this previous activity.
All of these methods blur the distinction between public and private spheres online. What individuals deem as 'private browsing' is, in most cases, not truly private. Individuals private browsing history, then seems to bleed into what are deemed as public domains, such as Facebook News Feed's and 'Recommended' YouTube videos. Although it is only the individual who can see things such as Advert Recommendations, it outwardly appears to be public as it is on a public medium. Not only that, but the fact that individuals browsing activity is already stored and shared by companies in the first place makes this information somewhat public.[134]
Tags and Privacy: How They Shape Online Performance
[edit | edit source]On the internet, tagging can mean a lot of different things, but is generally used as a way to link different pieces of information to either certain topics, or specific people. The most famous use of tagging is from Twitter with hashtags going viral, but there's also using tagging to gain visibility and therefore increasing how "public" a person or their content is. Tagging and Privacy settings are often conflicting each other, as one is used to gain attention and the other is used to get less attention, especially from the public.
Tagging represents an online connection between people and a digital relationship or aquaintance is made. This is a common feature of multiple social media platforms and acts as a way to bring users together and provides interaction. However, privacy can be a barrier for this interaction, limiting the content allowed on pages and the types of people accessing it.
Tagging is one of the basic features used in social media. Facebook uses this tagging element to enhance the feature and interaction with other users. This commonly used feature of Facebook helps users to feel part of something rather than a sole user. Social media can create a different identity of ourselves and can "negotiate social boundaries".[9]
Tagging represents an online connection between users and is seen to create social acceptance. Tags automatically involves
other people and so this photo/video/status appears across all the pages. However, this is where tagging can be very problematic. One user has control over the content being displayed and have the power to select the users to be tagged and the caption to go along with the content. The structure of technologies (their function and availability) can impact on our own self image and the world we live in.
Through tagging people can build up a persona online from the perspective of multiple other people, and it can often conflict with - and contradict - the persona and image that they are trying to create online themselves.[54]
This factor of Facebook denies the users tagged any ability to control the image for example posted. However, Facebook does have a setting which users can approve the content being posted to their page, but Facebook does not promote this setting as it almost defies the use of the application.
Simply by including a tag in a picture, it creates opportunities to go viral. Whether a tag of a friend or a celebrity, this picture has the chance to be seen by a wider range of people. This is where the issue of publicity and privacy is introduced. Although a profile is private, a picture can be seen and available across platforms. This brings about the question - are we private even though we can be seen across many different pages because of a tag?
A tag also represents - for a user being tagged by someone else - a non mediated self. Since the image is controlled by one central user, all others tagged in a photo display a non selective version of themselves; one which could be different from the image shown by themselves. A digital photograph on social media can present a past experience, can be retold and can be an expression of our own identity.[51] This creates an alternative and most likely more realistic image of a person online, breaking a barrier of them being so 'perfect' and 'idealistic'. This begins to create more judgements across social media and as Sherry Turkle says: "the risk that we come to see others as objects to be accessed".[135]
In terms of online performance, this is affected in many different ways.
Tagging can either create a positive or negative effect on online performance. This reaction by the user is interesting to understanding the users’ morals but also identity.
Individual's personal profiles are mediated and carefully selected by them, in order to created a desired self. Any one 'tag' could alter the image and persona that the individual is trying to create online. Since tags are controlled by others, it alters the shape of online performance, as it may not have censored certain things that the individual does not want to appear online.
This online performance takes two sides:
- Desired image - one side of who is desired by others and a 'positive' image controlled by us.
- 'Real life' image - tags and posts by others which represent a more realistic, different side.
Privacy can create an inactive performance. It can limit the features of the app and so affects overall online activity and performance of users. Conventions on social media create boundaries of acceptable content.[51]
Tagging could also be seen to be gendered as in an experiment on tagging in college students revealed women were higher than men for posting/tagging pictures and for comments.[51]
Online performance is structured around activity which mainly involves tagging. Being private creates boundaries around Facebook's function and so when tagging is limited; the profile is less believable and appreciated.
With the majority of Twitter users being between 18–34 years of age and with a graduate degree [136] there seems to be a particular niche in who uses this form of media.
Trending on Twitter is used as a way of making other users see what is most talked about at that current time. Hash tags are used by users and if enough of the public all use the particular hash tag this creates a topic that is trending. Often these trends tend to be issues relating to the relevant lives of the people who have Twitter accounts such as shared experiences and events they are currently experiencing. Sometimes new words or phrases can be brought about through hash tagging if a hash-tag is particularly successful such as throwback Thursday where users reminisce over past memories but this hash tag has become a well known phrase in society. Even a few years ago no one would have known this phrase at all let alone used it as a hash tag. Politics is discussed less where as everyday events, common situations, sports or music tend to be what people are discussing more than in depth politics where opinions may be divided. Twitter tends to focus around common interests shared between users to do with entertainment and experiences for their particular niche rather than the discussion of major topics that affect people globally such as current affairs and politics. Users have created Twitter to be a place of entertainment and leisure rather than the use of in depth discussion which is aimed at a particular group of people.
Advertisers also use this hash tag system to their advantage. When Twitter first started advertising did not exist through the site yet today it appears through the live feed between user posts. Advertisers are aware of what is trending through participating in the site and it is a great way for them to get an insight into what people are talking about and the current topics people are taking an interest in and discussing. They can then use this information to target their adverts to the people who will see it and be viewing it specific to their interests. Twitter also organizes its top tweets in preference of its advertising clients rather than tweets that may actually be trending. This search for what is trending is actually not true and is manipulated in that Twitter rate celebrities and well known people get priority over people who are not known in the media and live generally normal lives. Therefore people with economic power will come out on top as the most popular but may not be most popular by true statistics of trending.[136]
Tumblr
[edit | edit source]Tagging on Tumblr is primarily a way to categorise the content created and posted on the platform. Tumblr posts may include text, photos, audio, and videos, which all can be tagged. These tags are also used when users are searching for specific content, such as pictures of Scotland, so when they search "Scotland", they will see all the posts tagged with #Scotland. They can also refine their search so that they can either see the most recent or the most popular post, and to see only one type of post. Tags are found at the bottom of a post, in a smaller grey font from the rest of the text on the post, with a hashtag symbol (#) in front of each tag.
Users can tag their own posts in order to make it searchable on Tumblr. If they don't include any tags, the only people who can see the post are their followers or anyone who knows the url of their blog, which may not be much. Therefore, if a user wants more people to see what they post, tagging their content in popular tags can increase their visibility.
If a user want to see more content with the same tag, they can "track" it. Tracking a tag creates a link on the user's dashboard so they can click that tag at any time to see what's new in the tag. This is similar to subscribing or following a tag rather than a person or a blog. This is often used for the user's own username to see if anyone's mentioned them in a post, or if a user is particularly invested in a fandom and wish to see everything that is being posted about that fandom. If someone is particularly active on a tag, they may gain followers, if not just attention, which in turn makes them more public.
People also can also create an uncommon tags if they only want to see specific things, or have a way of grouping a series of posts together. For example, if a group of users are creating a specific week to create lots of posts about something, such as an underappreciated movies, they will create a tag that no one else has used, like #underapreciatedcharacterweek, and everyone will post their content using that tag. This way, all those posts are in one place for easy access and increased visibility.
Tags are also used to organise the posts together on a user's blog so they can have easy access to them later, such as #selfies and #personal post, or even more specific, like a Disney-themed blog would have a page with a link to all the tags for the different movies and characters.
Users with private, password protected blogs can also tag their posts so they can easily search through their own blog, but their posts will not show up on anyone's dashboard or in the Tumblr tag search. A user with a public blog but making a private post can also tag it for their own reference, but no other user will see it on their dashboard, when they search for that tag, or when they go onto that user's public blog.
Tags can also be used to blacklist certain types of posts. A software extension is needed for this since Tumblr does not provide the ability to blacklist specific tags. Creating a blacklist prevents posts with these tags from showing up on their dashboards, but not other people's blogs. This is often used for possible "triggers" for people with certain fears or trauma, but also for things like spoilers or negative opinions. Although, as stated, Tumblr itself doesn't have a feature that lets users blacklist specific tags, it does use the #NSFW (Not safe/suitable for work) tag in order to filter what will show up in the safe search option. Additionally, if a user searches negative tags, such as #depression, users will see a message offering them advice and support instead of allowing them to view a huge array of negative posts that could potentially worsen their wellbeing.
In 2014, Tumblr introduced a new way to "tag" other users in posts, calling them "mentions". Now, instead of adding a hyperlink to their blog and tagging them in the bottom of the post and hoping they check the tag to see it (or sending them a personal message about it), users can type a username with an @ in front, and they will get a special notification that they have been mentioned in a post. Users often use this to show funny or important posts to their friends instead of sending them the link to the post, or if they are giving "shoutouts" or promoting specific users to their followers.
Instagram[58] is a mobile social network platform mainly used and intended for the online sharing of photographs and videos. Users are capable of sharing their contents publically and privately, changing the security settings on the app. With over 300 million users as of December 2014,[137] there are immense amounts of content generated every day, and must be administrated in some way.
Tagging on Instagram can be used in three ways: much like on Facebook, users can tag other users on their own photographs, and mention them on post’s comments so other users receive a notification and can view the same post: and much like on Tumblr, a user can tag a post by assigning it to a category related to what they are posting about, using the hashtag (‘#’, hence ‘tag’) symbol.
The first two ways of tagging mentioned have got more to do with the online social communication aspect of Instagram. Tagging someone who appears on a photograph will show up on their personal account, (under the section ‘photos of [username]’). This can be very controversial, since it can result in both positive and negative effects.
A user’s online performance can be very influential on their personal life and mental health, and since Instagram is specifically an online photo-sharing service, it focuses largely around personal image in most cases. There is a certain self-management and management of the online performance in order to not create any negative images and representations of the self. Because of this, many users have felt the need to digitally modify and manipulate images of themselves. However, when a someone uploads a photograph of another user (usually without their explicit permission) and tags them on it, they are stripping them off of every right to edit their appearance and shape their own online identity in concordance to how they wish to be perceived by others.[135]
Since photographs are not always a realistic representation of the physical self, some photographs might largely deviate from the desired public image and online identity that a user may have. This can usually create many issues for users; mental health issues like anxiety, depression or self-loathing, as well as other issues that can also be indirectly damaging to one’s mental health, like cyberbullying (see 1.7.4) .
On the contrary, being tagged on someone’s photograph or tagging another user on one’s own can broaden an individual’s social circle and enhance their own personal experience in photo-sharing with this app.
Misuse of tags on Instagram
[edit | edit source]The search function for tags on Instagram was meant to be used in a certain way in order to connect with people who have the same interests.[138] For example, tagging a photograph with #sunset will appear on the tag’s own feed and therefore will be shown to people searching the same tag. Usually, this is how users can discover and ‘follow’ people that share the same interest in sunsets. However, with the growing popularity of Instagram, its abundance of daily content and the cultural desire of being popular within the platform (which is usually measured in terms of ‘likes’ and ‘followers’), users have developed new ways of getting in other user’s feeds and creating the opportunity of gaining more popularity.
This is usually through the misuse of tagging. In order to get as much visibility on their post as possible, users have wrongly tagged their photographs with tags that are not related to the content they are posting. These tags are usually “trending”, that is, many users within the Instagram community have used it recently and consequently the page for the tag has a larger viewing audience, (like for example, tagging a photograph or a ‘selfie’ with the tag ‘#oscars’ during the Academy Awards will create a higher chance for users to see and ‘like’ a picture and perhaps ‘follow’ the user, rather than tagging it with a more unusual, less visited tag). Users can find out which tags are trending by searching a specific tag, and Instagram shows the exact amount of photographs tagged with it, or through specific websites or apps (like Instag) that list the trending tags. This abuse has created a rather crowded environment in the tagging service of the app and an ‘information overload’,[139] which consequently dilutes the desired content within each tag when searched,[140] and generates an inconvenient photo-sharing experience in the app’s search function. This is also a problem on other social media platforms mentioned, like Tumblr and Twitter.
Nothing Created or Destroyed
[edit | edit source]| “ | The Internet's not written in pencil, Mark, it's written in ink. | ” |
— Erica Albright, The Social Network[141][142] | ||
The Internet is enormous and ever-changing. So much information is floating around on the web and sometimes it is not wanted. Sometimes it is taken without permission or used out of context. With such a vast amount of information, it is all but impossible to try and control it, especially on a personal level. It takes whole governments to try and contain, remove, or censor online information, and even then it does not totally work. An example of someone failing to control what happens on the internet is Barbara Streisand. She tried to sue a photographer to have a photo of her house taken off the internet and the result was an explosion of copies, re-posts, and mirrors of that photo being spread all over the internet, effectively making it impossible to get rid of. This became known as the Streisand Effect and is an example of the volatile and uncontrollable nature of the web.
The average young person spends up to 27 hours per week on the Internet[143] . The result of this huge amount of time spent on the Internet is an equally large digital footprint, meaning that most people nowadays cannot escape leaving their mark on the Internet. The average person spends most of their time on the Internet on social media sites such as Facebook and Twitter. These sites have become huge hubs of information with over 500 million tweets being posted each day. Many see these websites as a harmless way to communicate with friends and family, however posting too much information on these websites can be dangerous. As they may appear to give you the option to delete posts as you please, nothing on the Internet is ever fully removed and the digital footprints that we leave stay there forever.
With that in mind, one has to distinguish between:
1. two kind of information sharing with
- the companies, providing the wanted service, in order to be able to create an account and to use the platforms and the connected services - often the contact details are mandatory and it is in our interest.
- circle of acquaintances, e.g. on Facebook, where one can actively create the online identity,[51] or via messaging services to stay connected via interpersonal interaction.
2. and two types of shared information
- with our consents, meaning we actively decide to share the information by typing them into a form for instance, or
- without our knowledge via tracking of the companies providing the platforms I use - this also contains individual-related surfing habits, transactions and connection data. Hence they can create an online profile about us e.g. about our likings via our "online fingerprint".
Sherry Turkle [135] talks about people forgetting how much of a footprint we leave behind as we browse the internet "the experience of being at ones computer or cell phone feels so private we could easily forget our own circumstance: with every connection we leave an electronic trace". Most of us happily give over information to websites like Facebook and Twitter when signing up, however what we do not realise is the information that is gathered from us as we move around the internet, without us realising it at all. Our information is sold to large companies often without our consent or without us even knowing about it, this is why for example if you have been browsing an online shop you will find advertisements for that shop popping up all over the internet as you browse. Facebook does this often and specifically tailors the advertisements on its page to you and what you look at when you use the internet.
All this information is stored, partly for commercial and market research purpose, but also partly due to data retention laws and they are saved by many parties such as DSL providers (i.e. Vodafone), applications (i.e. Google Chrome Browser), devices and operating systems (i.e. Apple's iphone and iOS) and finally websites (i.e. Facebook). En plus through the data retention law the government has access to part of this information amount for many years; thereby the methods for crime solving shall be enhanced, but at the same time everyone is any time under general suspicion of having committed a crime.[144]
Even if there are also laws about deletion of personal data, as the example above shows, information online can never truly be deleted. With this in mind it raises the question if there really is such a thing as privacy in the digital world. Even users who choose to remain anonymous and can be traced back using their IP address meaning that, when it comes to the internet and everything digital the traditional ideas of privacy are non existent.
An example of this is the Ashley Madison Data Breach, Ashley Madison was a site in which users were able to conduct and organise affairs. The website retained every users personal information, which included all of their real names and details as users used fake names. This website was hacked and all of the private details of the users were released and made available to the public. Users of the site truly believed that their personal information was protected and so was their privacy, but with this and with most other cases on the internet private information is never truly private, and can be obtained and released very easily.
Anonymity in the Private Sphere
[edit | edit source]Online communication on the Internet is commonly described as 'anonymous' when users do not post any personal details, and often use a username instead. There are many different levels of anonymity (lack of identifiability, visual anonymity and dissociation of online and real identities), that are thought to have different components of interpersonal motivation, which are able to influence self-conception. Morio and Buchholz (2009) [145] have suggested that someone can essentially become a different person by creating a new online identity, allowing space to create and adopt different values and personalities, and even, in some cases, a new age, gender or race. Luppicini and Lin (2012) argue that this is because “online anonymity allows there to be (in varying degrees) a dissociation of real and online identities where someone’s online behaviours are not directly tied to that person’s physical self”.[146] Due to this type of dissociation, there is usually less accountability for how users behave online in comparison to how they behave in their ‘real’ lives.
Social media platforms like Tumblr, YouTube, Twitter and Yik Yak can be said to belong in the private sphere of digital media, due to the fact that these websites mainly operate with the use of a username, and so a user does not necessarily need to give away any of their personal details. These websites have become largely popular among its audiences because users find a certain type of reassurance on keeping their ‘real’ identities private by hiding behind a username.
The use of anonymity in online platforms has subsequently created one of the largest (and on-going) problematic conundrums in the social use of present day Internet, resulting in positive and negative outcomes. An anonymous online identity can be empowering for a user because it allows them to explore the depths and different aspects of their own identity, occupy different social roles and positions and embrace their own diversity in ways that might be impossible to realise in real life. On the other hand, online anonymity can also lead to many problematic issues like cyberbullying, information and identity theft, 'catfishing' and defamation. The following sections will explore the positive and negative aspects of online anonymity in more detail.
Freedom of Expression in Private Spheres of Social Media
[edit | edit source]As mentioned above, some social media platforms belong in the private sphere due to the fact that users may choose to remain anonymous, and operate through the website while using a username. This can possibly motivate users to ‘speak their minds’ and publicly express (while remaining anonymous) their passions and interests, and personal opinions on a specific topic of choice. While some individuals might be demotivated to do so in public spheres (like Facebook) because they might fear contributing to a type of information overload, where they could flood other user’s feed with their lengthy posts, or because they might fear if their public identity and image might suffer if given certain opinions, the anonymity of private social media platforms might encourage users to write without holding back.
It is quite interesting to compare how both types of platforms (public and private) can motivate or mute an individual’s expression. It is also known that some artist social media users feel more comfortable with posting their artwork in websites like Tumblr or Deviantart due to the fact that their contribution will remain completely anonymous. In terms of artistic abilities, an individual can be particularly sensitive to critical evaluation and exposure, especially if they are still in the earlier still-developing artistic stages of their own skills. For this reason, users might feel too shy or insecure to upload this type of very personal content into public social networks like Facebook, where they might feel like open visibility to all of their friends might be too much exposure.
Uploading this type of content on public networks can also contribute to an individual’s anxiety due to the ‘liking’ concept; where they can become obsessed with a number and with the thought that ‘likes’ are equivalent to an individual’s worth. On the other hand, this can also be applied to private social networking platforms like Tumblr, because most of social media platforms nowadays operate with the use of ‘likes’, ‘followers’ and ‘shares/reblogs’. However, it can also be argued that an anonymous user (through a username) liking or commenting on an individual’s post is certainly less impacting and less personal than an individual’s personal profile doing the same thing. Because of the fact that no one necessarily knows anything of a user from their username alone, it feels less so like a person evaluating an individual’s creative work.
It is also interesting to link this to David Gauntlett’s [59] work on ‘Web 2.0’ [60], where he states that Web 2.0 is ‘harnessing the collective abilities of the members of an online network, to make an especially powerful resource or service. But thinking beyond the Web, it may also be valuable to consider Web 2.0 as a metaphor, for any collective activity which is enabled by people’s passions and becomes something greater than the sum of its parts.’ [147] This way we can understand the idea behind the desire for users to contribute in private spheres of social media in regards to their own interests; to feel part of a larger community which may form a part of their identity.
Altered Narratives of the Self
[edit | edit source]An individual’s online behavioural patterns and online performance tend to deviate largely when in the private sphere in contrast to when in the public. Depending on the website or social network being used, a media consumer will create and manage a different narrative or identity to adjust to how they would like to be seen within the platform’s society. Because of this, one could argue that different online platforms are made of different societal norms and have a certain appeal to a specific target audience; therefore, a specific type of behavioural pattern is expected from each user. This is also enhanced by the privacy each platform within the private sphere provides. Social media networks like Tumblr[61] and YouTube [62] operate with usernames (unlike Facebook[63]), providing the option for users to completely remain in anonymity by only using a username (or in case of Tumblr, a URL ), instead of giving away any of the user’s personal details. It is important to note that, while users do have the complete liberty to give away their personal details if they wish to do so, it is a rather unpopular mode of action since most users find a larger appeal and a certain type of reassurance in staying completely anonymous with the use of a username.
Having this type of liberty in terms of self-management and online identification and expression have lead to many different usages of anonymous narratives in social media.
The Private sphere as an empowering tool for self-identification.
[edit | edit source]| “ | We judge on the basis of what somebody looks like; skin colour, whether we think they’re beautiful or not. That space on the Internet allows you to converse with somebody with none of those things involved. | ” |
An anonymous online identity can be very beneficial in terms of self-exploration and self-identification. It can be an empowering tool for individuals to embrace their diversity and explore the identity they are most comfortable identifying themselves with, or as Gies (2008) writes, “ anonymous online settings are empowering because they facilitate identity exploration, or occupying identity positions which may be difficult to occupy in real life”.[148]
Because there is a lack of identifiability, users can feel free to explore their own personal identities (like sexual orientation and gender) and interests without the pressure that usually comes with the public sphere of digital media and maintaining a public image with its open exposure to the public. Martin Heidegger argued that it is only in the private sphere that one can be one's authentic self, as opposed to the impersonal and identikit They of the public realm.[149] It is also important to understand that different types of social media audiences shape an individual’s online identity. While, for example, on public social media like Facebook an individual’s audience tends to be their ‘friends’ (which can be constructed of actual friends, family and acquaintances), on private social media like Tumblr the audience can be composed mainly of strangers. This creates a more comfortable sharing environment because of the minimal intensity of the public sphere’s exposure. While someone could be more comfortable exploring their sexual orientation in a private, anonymous platform, it is highly improbable that they would feel comfortable doing so openly to, for instance, family members. It is also very common to not reveal an individual’s username in private spheres of digital media to friends and family. While some people do share this, it is most likely shared to an audience they trust deeply, like close friends, rather than, for instance, a parent.
On the other hand, Turkle [64](1996) noted that the Internet allows individuals to hide parts of their identity which could lead to discrimination (for example, race or gender).[150] Due to the visual anonymity that social media within the private sphere provides to its users, key features to one’s personal identity are not always visible, or rather, not necessarily (unless the user has specifically chosen to share them). This can create a more accepting environment for users, particularly in the case of exploring one's identity without being pulled back by stereotypes associated with certain identities, perhaps to do with gender, race or sexual orientation. However, it could also be argued that this can have negative psychological impacts on an individual's state of mind in regards to their own identity; having different public reactions when showing different aspects of an identity than when showing none might have discriminatory connotations and could motivate an individual to feel ashamed of their identity.
Idealised versions of the self and Alter Egos in the Private Sphere
[edit | edit source]While pressures to maintain a specific online identity are more common in public spheres (like for example, pressures to ‘prove’ one’s social life[135][151] and reassuring one’s role within a social circle,[20] and pressures to create an acceptable and aesthetically pleasing impression of an individual’s physical identity), a user of a private sphere social media can also form idealised versions of themselves. Because all that an audience needs to necessarily know about each user is a username, they could become anyone they have always wanted to be.
When adopting an anonymous online identity there is a type of dissociation of an individual’s real and online identities. This way, they have absolute freedom to create an identity and ‘perform’ themselves online how they want to be seen, without this identity being associated with their physical selves.
An interesting aspect of this dissociation would be the use of alter egos in social media. While at a first glance could seem like a public profile that belongs to the public sphere, the original user (and therefore, the real identity) remains anonymous, and more often than not, completely dissociated from it. This way, it can be argued that alter egos blur the boundaries between public and private spheres, since an individual can never know for certain if the identity presented online is an individual’s ‘real’ identity rather than an alter ego.
The most recent and relevant example of the use of an alter ego to blur the lines between public and private spheres would be in the case of Instagram star Amalia Ulman [65]. Ulman created and performed in a staged social media experiment, where she created the alter ego of a girl perusing the dream of becoming an ‘It girl’ in Los Angeles. Her performed self had dyed blond hair and a stylish wardrobe, underwent breast-enlargement surgery and was self-consumed and narcissistic. After months of continuous posting and gaining of followers, Ulman announced the reality of her performance by uploading one last picture captioned ‘the end’. When confronted her experience, she says:
| “ |
"Everything was scripted. I spent a month researching the whole thing. There was a beginning, a climax and an end. I dyed my hair. I changed my wardrobe. I was acting: it wasn’t me.”
|
” |
Another example of creating an idealised version of oneself is through virtual reality. Users of a virtual reality website or online social platform often have to create a character of sorts that replicates and tries to imitate their personal selves, known as their avatar. Due to an individual's natural desire for aesthetic perfection, they tend to design these avatars as idealised or perfected versions of themselves. These avatars later interact with other user's avatars and people usually tend to take the visual representations of said avatars as a very realistic representation of how the individual's physical self might resemble. This can create many problematic issues, like affecting user's expectations of real life beauty making them unrealistic (which could lead to problems associated with mental health problems and sexism) and catfishing.
Catfishing
[edit | edit source]Catfishing is when an individual uses deceiving techniques in order to adopt a different identity (through identity theft, usually by posting another person's photograph as their own and pretending to look that way physically). The modern term originates from the 2010 American documentary Catfish.[153] The usual purpose for this is to engage in an online romantic relationship with someone else across the Internet. Reasonings behind this include self-loathing of one's physical appearance, attempting to increase the number of potential love candidates by increasing the physical aesthetic appeal and presenting it as their own identity and/or other psychological reasons.
Because public social networking sites are so popular and more often than not they provide a realistic representation of one's true self, a large majority of people are likely to trust and believe in the reality value of a public profile if it meets the following expectations;
- A numerous or acceptable quantity of pictures of the same individual
- A large number of these pictures that seem personal or have been taken by themselves (for example, 'selfies' ) and with other social media users
- A large social circle of friends (which all seem to meet the above as well)
However, because of the numerous personal pictures of many different individuals available online (which can be found with a simple google images search), it can be extremely easy to create a fake online social network profile. This way it can be argued that there can always be anonymity in the public spheres of social media, since there can never be real proof or a real reassurance of someone's online identity being their 'real' identity.
Anonymity in Help Forums
[edit | edit source]When using any medium online, not only social or digital media platforms, it can become obvious that any degree of anonymity afforded to a group or an individual can alter their behaviour, causing them to present themselves differently to how they may when they bear their real name or personal details, and this can be both positive and negative. One manifestation of the help forum where anonymity is a key element is any one of a number of mental health chat forums, where individuals can anonymously and confidentially seek help, advice or just to feel they have someone who will listen to them, and have a trained professional on the receiving end to assist them. The anonymity in this instance is crucial as visitors to these sites may feel ashamed, embarrassed or insecure about their issues to the point that they cannot communicate with or seek help from those around them, or talk to a local healthcare professional for fear of, for example, family members becoming involved. They are there to provide support to anyone who cannot seek it anywhere else due to time or money restraints, or if they are perhaps part of a culture that is not very supportive of mental health issues. The anonymity encourages users to be more open and honest, and helps them to receive the specific support they may require.
Traditional help and advice forums such as Yahoo Answers work simply by users around the world, with usernames or pseudonyms and cartoon avatars as their icons, asking questions and in turn helping others. This model can also more recently be seen in the social media application and website YikYak, where anonymity is not optional to users, and the default feed presented is of content posted by users within a certain geographical radius. Users have the option to ‘peek’ at other locations around the world but posting and replying is limited to the local area. It was developed for college and university campuses in America as an anonymous way to interact with peers about local events or news, but has subsequently been banned and restricted from school campuses with younger pupils due to bullying.
Though it may not necessarily be the intended function nor the primary use of YikYak, advice seeking and provision is nonetheless present on the site. Amongst the humorous observations, jokes and other relatable content, users can take the opportunity to seek the opinions, wisdom or support of those around them, widening their online social sphere without letting anyone in. The anonymity afforded by YikYak may also be empowering users with a kind of confidence they may not have online otherwise, and gives them a place to ask questions or express thoughts or feelings they may be afraid or embarrassed to on a platform where they are connected with and known to their peers offline. Questions of health, sexuality, romance, mental illness, and other topics that the individual may not feel comfortable talking about openly elsewhere online are discussed freely, and like those posing the questions, users with answers are also more free to share these, creating a kind of help network. This positive use of anonymity on social media is an example of users extending their private sphere to people they do not know in order to gain or share something, within the public sphere as it is visible to many others in the local area and shared and stored online. The disinhibition[154] experienced by users of YikYak, though, may be hindered by the ever-possible notion that you may be conversing with somebody whom you know in real life and would never dream of discussing such topics with.
Along with genuine requests for help and appropriate answers and discussions, there are inevitably people who use their anonymity for less than favourable reasons and behaviours. Though they do not know who exactly they are targeting, individuals may direct abuse or insults at people regardless of what they may have originally posted, it can be entirely unrelated and unprovoked. The option to hide all content from a specific user is available in the instance of such behaviour but, because of the anonymity and the way commenters are unable to be traced between threads, it is unclear just how many users at one time may be acting in this way; one individual could pose as many, or vice versa. The creation of multiple user names for the purpose of trolling is a similar phenomenon on help forums, where anonymity, though beneficial for some, is used in a negative way in the public sphere while protecting the user’s privacy.
Cyberbullying
[edit | edit source]Bullying is a serious social problem. It can happen anywhere at any time, from the workplace to your bedroom, however its all-encompassing reach is only a recent development. Spitzberg and Hoobler have stated that the digital and information revolution has merged into a communications revolution:[155] as a result messages can now reach you anywhere. Therefore the potential for bullying via electronic communications has grown with the advancement of communications and technology.[156]
Cyber bullying is a modern form of bullying usually practiced through electronic or online forms of contact e.g. SMS, Social Media, Youtube. Cyberbullying has been perceived to be worse than traditional bullying for a number of reasons in reference to the consequences for the victim.[157] The consequences can be seen as worse because of the larger audience that may be privy to the abusive content online, for instance leaving a comment on a Youtube video is available to be seen by everyone. Most importantly there is also an increased potential for anonymous bullying online.
| “ | An aggressive, intentional act carried out by a group or individual, using electronic forms of contact, repeatedly and over time against a victim who cannot easily defend him or herself. | ” |
— Peter K. Smith,Emeritus Professor of Psychology at Goldsmiths College, University of London[158] | ||
Social media websites such as Facebook have the potential to create fake accounts where the bully can anonymously harass their victims. The anonymous nature of the harassment can have a different psychological effect to that of regular bullying upon the recipient due to the insidious nature of abuse. The unknown identity of cyberbullies can cause fear and distraction for the victims[159] and our online privacy is therefore damaged by the anonymous nature of cyberbullying, eliminating the sense of security one can feel online.[160]
The security of hiding behind an online URL or user name also encourages bullying. Aricak’s studies have shown that electronic communications associated with anonymity have been shown to promote cyber bullying behaviour.[161] Tumblr, which has an anonymous messaging service built into the website, confirms these studies due to the many instances of online “hate mail” users receive through the anonymous messaging service. This has become commonly known on the website as “anon hate”.
Cyberbullying exhibits all the characteristics of not having a face-to-face communication/experience – facial expressions, gestures, tone of voice and reactions ect.- which can reduce the emotional responsibility and social accountability the bully would normally experience, this consequently makes them feel less guilty when taking part in vindictive or hostile communications.[162] Additionally, the potential for anonymity online in private and public spheres can produce bullies who would never normally take part in traditional face to face bullying – feeling empowered by their anonymous profiles.[163]
Cyberbullying therefore thrives off the potential for anonymity created by the internet as well as the continued evolution of technology into a more connected age. Even though it may seem less harmful to bully through the cybernetic world in reality it can be far more destructive than traditional bullying invading both our private and public spheres of communications.[164]
Digital Self-Harm
[edit | edit source]Digital self-harm is the act of abusing one-self anonymously online. In 2010 Dr. danah boyd published an online article about "digital self-harm" describing "teens who are self-harassing by 'anonymously' writing mean questions to themselves and publicly answering them"[165] This phenomenon was initially uncovered by the staff at a website, Formspring (now known as Spring.me) which investigated some cyber bullying and found that the alleged victims had actually posted the cruel comments against themselves.
A study by Elizabeth Englander at the Massachusetts Agression Reduction Centre labelled the phenomenon as "Digital Munchausen" as the process undertaken by these teens mirror certain symptoms of the psychiatric disorders Munchausen Syndrome and Munchausen Syndrome by Proxy. The syndroms primary characteristic is the patients infliction of self-harm in a quest for sympathy, attention and admiration as they attempt to cope with their victimization. In 2011 a study was undertaken that discovered that 9% of teens took part in digital self-harm - making a cruel comment anonymously against themselves or cyber bullying themselves: a higher proportion of boys (13%) admitted to this than did girls (8%). About half of these “digital self-harmers” had done this only once or very infrequently; the other half reported that they had cyber bullied themselves more regularly or had one, ongoing episode which lasted at least several months.[166]
The potential afforded by anonymous question forums like Formspring, as well as the potential for anonymity on almost any digital or social media has clearly been used as a tool to "harm" and "victimize" oneself for various purposes. danah boyd speculates that teens use online anonymity to harm themselves as an outcry for help, to appear cool or to attempt to trigger compliments. Elizabeth Englander's study shows that they took part in digital self-harm to get the attention of a peer or to prove they could "take it" among other reasons. For both boys and girls, about 35% said that the self-cyberbullying strategy was successful for them, in that it helped them achieve what they wanted, and felt better after their anonymous self-abuse.[167] It is therefore important to take into account the potential for anonymous self-harm on the internet, which has only become possible due to the potential for anonymity in both online private and public spheres.
Cyberstalking
[edit | edit source]In present day, the idea of going on someone’s personal online profile in social media sites like Facebook seems like the a very common and socially acceptable thing to do, and the term ‘stalking’ can be lightly and jokingly used to define this. A user can spend hours scrolling down a stranger’s personal profile and discover and learn many personal details of said person. However, such seemingly innocent act can very easily and quickly get out of hand, leading to very serious consequences.
The most common (and again, essentially socially acceptable) type of cyberstalking is usually directed towards celebrities, especially of their social media profiles. The fact that the user has chosen to upload such concept and made it publicly available is what motivates other users to spend hours ‘stalking’ it, which could possible be why nobody considers this act to actually be cyberstalking. However, not all users just stop here, which is why cyberstalking is actually a form of cyberbullying.
Alexis Moore describes cyberstalking as a technologically-based "attack" on one person who has been targeted specifically for that attack for reasons of anger, revenge or control. Cyberstalking can take many forms, including:
- harassment, embarrassment and humiliation of the victim
- emptying bank accounts or other economic control such as ruining the victim's credit score
- harassing family, friends and employers to isolate the victim
- scare tactics to instill fear and more [168]
The differences between cyber bullying and cyber stalking have been looked at in a Trolling Magnitude (TM) Scale, showing that, while cyber bullying is more strategic, cyber stalking is more about domination.[169] [67]
| TM | Motive | Mode | Gravity | Description |
|---|---|---|---|---|
| 1 | Playtime | Cyber-bantering | Cyber-trolling | In the moment and quickly regret |
| 2 | Tactical | Cyber-trickery | Cyber-trolling | In the moment but don't regret and continue |
| 3 | Strategic | Cyber-bullying | Cyber-stalking | Go out of way to cause problems, but without a sustained and planned long-term campaign |
| 4 | Domination | Cyber-hickery | Cyber-stalking | Goes out of the way to create rich media to target one or more specific individuals |
| “ | …the Internet, e-mail, or other electronic communication device[s] to create a criminal level of intimidation, harassment, and fear in one or more victims | ” |
—M. L. Pittaro [170] | ||
Cyberstalking falls into three main categories: direct communication, indirect communication, which is circulated or posted online, and misrepresentation online.[171] As well as there being four main types of cyberstalkers: the vindictive cyberstalker, the composed cyberstalker, the intimate cyberstalker and collective cyberstalkers. The vindictive type is much more likely to threaten their victims than any other group and can sometimes stalk them offline as well as online. The stalking in these cases typically began with a trivial discussion or argument and ended up with the offender getting upset and setting out on a mission to harm the victim. This type was the most likely to use spam, viruses, and identity theft against the victim. The composed cyberstalker does not want to develop a relationship with the victim, but rather wants only to harass, threaten, and annoy the victim. The intimate cyberstalker desires to have a relationship with the victim. This type can be divided into two subcategories: the ex-intimate and the infatuate. The ex-intimate may desire to repair the past relationship, but he may also threaten the victim as well. The harassment begins on the internet in this type, not offline. The infatuate begins by sending the victim an intimate message and desires to develop a relationship with the victim. When the infatuate is rejected, he will then begin to threaten the victim. Lastly, the collective cyberstalkers work together to send the victim many emails, and to spam, threaten, and steal the victim’s identity.[172] Research also shows that victims of cyberstalking are just as likely to feel fear and helplessness as people who are stalked in real life because cyberstalkers often hide in anonymity making them that much more difficult to deter or catch due to the fact they can stalk from the secrecy afforded by the World Wide Web.[173] This allusiveness may make cyberstalkers even more threatening, intimidating, and frightening.
However, as in the case of the vindictive type, cyberstalking can often come hand in hand with offline or 'realtime' stalking in severe cases. This is because if an individual with specific psychological issues is cyberstalking, they most often feel like this is no longer enough for them (after a certain period of time has passed) and decide to take it to the next level; offline stalking. There are consequences of law in offline and online stalking, and cyberstalkers can be put in jail.[174] [68]. However, this is often not enough to pay for the psychological damages that cyberstalking causes.
According to social psychologist Robin M. Kowalski, cyberbullying and cyberstalking has been shown to cause higher levels of anxiety and depression for victims than normal bullying. Kowalksi states that much of this stems from the anonymity of the perpetrators, which is a common feature of cyberstalking as well.[175] According to her study, a quarter of 3,700 bullied middle-school students had been subjected to a form of harassment online.[176]
Hackers and Hacktivism
[edit | edit source]Hacktivism is a contentious term which, most loosely and most relevantly to this context, refers to the idea of technological hacking to affect social change. Many groups and individuals go to great lengths to conceal their identity due to the nature of their tasks, whether they are ethical or unethical, and some use the pseudonym Anonymous, one of the most notable hacktivist groups which originated on the forums of 4chan and are responsible for a number of notable hacking activities.
The idea is that the groups and individuals who identify as hacktivists want their beliefs and actions to be widely known and acknowledged while keeping their identity and details such as location entirely concealed. This is an unusual example of keeping a high profile in the public sphere while maintaining complete anonymity and a disconnect from their private sphere, while using their skills to breach the privacy of other individuals or organisations. There is nothing to be gained personally by this, such as recognition, but it is often activism in the name of political or social beliefs or justice that motivates these kinds of hackers without the repercussions of being identified. This can lead to extremes of cyberterrorism, which is sometimes classed under the category of hacktivism.
Evolution of Hacktivism and Political Hacking
[edit | edit source]The origins of computerized activism extend back in pre-Web history to the mid 1980s. As an example, the first version of PeaceNet appeared in early 1986. PeaceNet enabled - really for the first time - political activists to communicate with one another across international borders with relative ease and speed.[177] The computerized activism of the past has developed through certain stages: Electronic Civil Disobedience activism which acts in the tradition of non-violent direct action and civil disobedience employing typical civil disobedience tactics such as sit ins/physical blockades, and translating them into modern culture: creating virtual blockades. Unlike a traditional sit in the Electronic Civil Disobedience activist can participate in the virtual blockades from home, work or university - anywhere that is attached to the web.[178] It is neccessary to mention ECD activists as they are part of a process which has led towards politicized Hacktervism.
One main distinction between most Politicized Hacking and the type of Electronic Civil Disobedience just mentioned is that while ECD actors don't hide their names, political hacks are generally done by people who want to name anonymous because a lot of what they do is not above board. These hacks are often likely to be undertaken by specific people rather than larger groups. The main reason for anonymity in hacktivsm is that the stakes are much higher, some hacks are unquestionably illegal: like the Sony Pictures hack of 24 November 2014.[179] However, the nature of the online web affords the opportunity to remain anonymous whilst crossing political boundaries. Few people would question the legality of entering someones personal computer and adding or changing HTML coding. Therefore hacktivists anonymity is a necessary tool.
It is important to remember that hacktivism is very much in its infancy. It is too early to make a definitive statement upon the direction hacktivism will take. Perhaps the entire notion of hacktivism distorts and challenges sets of values and moral and ethical codes abusing the potential for anonymity on the web. Steven Levy bemoans that "modern-day" hackers are not worthy of the name asthey do not maintain the principles of original Hacker ethics, and as unethical individuals, should simply be called "computer terrorists" or "juvenile".[180] In the future there will be some re-thinking involved in hacktervism and we may begin to see a new set of ethical codes for hacking developed.[181]
Anonymous
[edit | edit source]Anonymous are a vaguely connected international group of hacktivists. The group is thought to have founded in 2003 where their first known activities on 4chan came to light during raids on other social media websites like Habbo in 2006.[182] Anonymous members can be identified in public by the stylized Guy Fawkes masks that they wear which has become popularized as a symbol for rebellion in films like V for Vendetta and now through its association with Anonymous.
| “ | Anyone can be part of it. It is a crowd of people, a nebulous crowd of people, working together and doing things together for various purposes. | ” |
The group has no leader but rather works around ideas rather than directives, in this way, no singular person or figurehead can be associated with the blame of their hacks. Generally speaking Anon's disagree with internet censorship and control, largely targeting governments, companies and organisations they feel are providing censorship, Anonymous were early supporters of the Arab Spring(see section 1.5.4.3.1).[184] The group has relatively few rules but those they have include not disclosing their identity, not attacking the media and not talking about the group as a whole.
| “ | "We [Anonymous] just happen to be a group of people on the Internet who need—just kind of an outlet to do as we wish, that we wouldn't be able to do in regular society. ...That's more or less the point of it. Do as you wish. ... There's a common phrase: 'we are doing it for the lulz.' | ” |
—Trent Peacock.Search Engine: The face of Anonymous, February 7, 2008.[185] | ||
An example of Anonymous' hacktivist acts could be the cyberprotest after the fatal police shooting of the unarmed African-American Michael Brown. A hacktivist organization that claimed to be associated with Anonymous organized cyberprotests against police, setting up a website and a Twitter account to do so.[186] The hacktivist group promised and threatened that if at any moment any protesters were harassed or harmed, they would attack the city's servers taking them offline. City officials admitted to the press that e-mail systems were targeted and phones died, while the Internet crashed at the City Hall.[187] Later on, members of Anonymous said that they were working on confirming the identity of the undisclosed police officer who shot Brown and would release his name as soon as they did.[188] Anonymous then posted on its Twitter feed what it claimed was the name of the officer who shot Michael Brown.[189][190] However, police said the identity released by Anonymous was in fact, incorrect.[191] Twitter subsequently suspended the Anonymous account from its service.[192] It was reported on 19 November 2014 that Anonymous had responded by declaring cyber war on the Ku Klux Klan (KKK), after the KKK had made death threats following the Ferguson riots. They went on to hack the KKK's Twitter account, attack servers hosting KKK sites, and started to release the personal details of members.[193]
Online Piracy and S.O.P.A
[edit | edit source]Whilst piracy has always been an issue, the digital age has amplified it significantly. Before digital media came to prominence, pirating goods such as films or music was more difficult and required a certain degree of technical proficiency. In addition to this, piracy was viewed more as a taboo and the quality of pirated goods was generally poor. Through digital media, an identical quality copy of a piece of media can be produced and distributed at little cost to a mass audience.
The first major file sharing program to exist, and also to be shut down, was Napster, which was also the most prominent example in peer-to-peer (P2P) file sharing, operating from 1999 to 2001, amassing over 25 million users and 80 million songs. Users could now download and share any music file free of charge. Various artists filed law suits against the site when it would not remove copyrighted material. However, Napster was quick to settle each of these suits. The site was eventually terminated due to legislation introduced by the Digital Millennium Copyright Act. This marked the first significant sign of resistance against digital piracy by the media industries.
Internet piracy is when unauthorized copies are downloaded over the internet. This is typically done through peer-to-peer file sharing systems, the some prolific examples being The Pirate Bay and LimeWire. There are currently hundreds of thousands of warez sites providing unlimited access to downloads for users. The same purchasing rules apply to on-line software purchases as for those bought in compact disk format.
Common Internet piracy techniques are:
- Websites that make software available for free download or in exchange for others.
- Online auction sites that offer counterfeit or out-of-channel software.
- peer-to-peer networks that enable unauthorized transfer of copyrighted programs.
Once downloaded, these pirated files are hosted on a BitTorrent client.
Such clients include μTorrent, Xunlei, Transmission, QBittorrent, Vuze, Deluge, and BitComet.
This type of file sharing is indicative of the public digital sphere intersecting with the private digital sphere. The community collaboration required through the processes of acquisition of the data, uploading, torrenting and seeding which results in the individual being able to access media that may have otherwise may have been unreachable .
As this method of file-sharing becomes more prominent, the idea that it is a crime comes less ingrained in the collective consciousness, and as file sharing becomes regarded as less deviant behaviour the more it becomes utilized as an everyday too among users. Following McLuhan's model of technological determinism, we have seen social attitudes yield to technological advancements. However, this relaxed attitude towards downloading unknown software has led to a greater number of breaches in computer security. This lack of ability to verify the sources and quality of downloads is the key issue with file-sharing as it allows numerous other risks to become more prominent, such as the exposure of personal information or increased susceptibility to attacks in the future.
Stop Online Piracy Act
The Stop Online Piracy Act - or S.O.P.A as it is more commonly known - was a controversial Bill proposed by the US Government in 2011, in an attempt to clamp down on online piracy. The bill took power away from content creators, and essentially deputised copyright holders in their ability to eradicate piracy. In doing so, this gave copyright holders (in most cases record labels and movie distributors) the power to shut down not just the content but the provider itself, and force all other online services to do the same; provided they have a lawful copyright claim. However, the "deputising" effect of the Bill meant that copyright holders would not be obliged to go through any judicial processing in regards to the claim. This means that corporations would have the ability to shut down a single person's (or an entire company's) online footprint in an instant - forcing other internet services like PayPal and social networking sites to comply to the claim, as well as blacklist the perpetrator from ever using the services again. The Bill was praised for its policies on infringement claims outside the US, giving claimant's more power in shutting down illegal content from foreign websites. The Bill also carried stringent policy on illegal streaming, for both the provider of that content and those that consume it - with a 5 year maximum prison sentence for the viewing or listening of illegal content.
Despite receiving strong support in both The Senate and House of Representatives - amongst other organisations and Unions - the Bill was met with great opposition by US citizens. Many felt that the Bill was an infringement on intellectual property law, and claimed that the guidelines for the bill were so broad and vague that one small infringement by a single person could have disastrous repercussions. Others also claimed that the Bill's proposal to block internet search results and to blacklist users from services and information was a violation of the First Amendment. The Bill was met with substantial opposition by various online communities - the members of which shaped the future for the Bill and were paramount in its eventual retraction.
Online-activism does not exclusively encompass issues experienced in the real world, groups can come together for the promotion of issues relating to online freedom and net neutrality. Online community site Reddit actively opposed S.O.P.A and its policies, and were pivotal in encouraging other providers and content creators to stand in protest. A subreddit (section of the site dedicated to discourse on a specific subject) was created to discuss both the Bill and ways in which to protest it. Many users noticed the domain hosting site GoDaddy actively supported S.O.P.A, which prompted a worldwide boycotting of its services. Reddit users collectively pulled their subscriptions, creating a synchronous deficit of 82000 domains[194] and forcing GoDaddy to denounce their support of S.O.P.A. A statement by CEO Warren Adelman confirmed this on 29 December 2011:
- "We have observed a spike in domain name transfers, which are running above normal rates and which we attribute to GoDaddy's prior support for SOPA, which was reversed. GoDaddy opposes SOPA because the legislation has not fulfilled its basic requirement to build a consensus among stake-holders in the technology and Internet communities. Our company regrets the loss of any of our customers, who remain our highest priority, and we hope to repair those relationships and win back their business over time."[195]
Theorist Howard Rheingold suggests that these acts of protest are the product of what he describes as "smart mobs".[196] According to Rheingold, even though protests such as Reddit's on S.O.P.A are primarily controlled and coordinated through the use of modern technology, age-old social practices alter the ways in which we us it. Essentially, society affects the way in which we use technology, which ultimately dictates ones behaviour online. Notions of trust, community and cooperation are still prevalent in an online environment; thus creating a symbiotic relationship between human interaction and access to information and widespread communication. In relation to S.O.P.A, this is indicative of something that Rheingold describes as "self-organised mutual aid" - meaning that the technology we use today (smartphones and other wireless devices) gives us the power to not only communicate, but to do so for the mutual benefit of both yourself and others. The societal framework that we have created in online envrionments allows us to organise and coordinate with those who are in our vicinity and those on the other side of the world simultaneously, depending on our needs at the time. Reddit users collaborated on a massive scale, and through the use of common social practices like protesting and boycotting - combined with the powers of technology - were able to make significant change on a much greater scale than if users had done so individually.
Website Blackouts in protest of S.O.P.A
During the collaborative protest efforts by Reddit and other online communities, websites that opposed S.O.P.A created a synchronous "blackout" of their services to show the effects of online censorship. Some sites cut off access completely, whereas other sites "censored" specific content whilst promoting petitions or protests that opposed the bill. Among the websites that organised this blackout were Reddit, Wikipedia, Google and Wired.[197] English Wikipedia stopped access to its site completely on 18–19 January for 24 hours, and asked those that encountered the blackout to "Imagine a world without free knowledge". Similarly, Google plastered a black banner over the well-known Google logo, which when clicked redirected to a petition to stop S.O.P.A. The Electronic Frontier Foundation are a digital rights group who assist with legal aid in digital rights cases and who defend new technologies and oppose infringements on net neutrality and online rights. As well as actively opposing S.O.P.A they too participated in the blackout on 19 January. As well as these websites, it was reported that there were over 7000 sites who contributed to the blackout in some way.[198]
The response from the blackout was paramount in ensuring the retraction of the Bill, and soon after many websites, Senators and groups who originally supported it began to recant their statements and change their views. The widespread knowledge of the blackout and the media response that it caused was proportionate to that of a real-life protest - with real life effects and repercussions. The internet blackout created a storm of media attention, whilst provoking a strong argument for the importance of freedom to education and information (in this case on the internet). The vast societal impact of the blackout coupled with the communal and cooperative aspects of the synchronous blackouts and protests, strongly corroborates the work of theorist danah boyd. Her work in the notions of always-on culture and the difficulty in discerning between real and virtual life in this age is evocative of the global reaction to S.O.P.A and the blackouts.[199] So synonymous are real and virtual lives that the societal influence of disabling access to information online can cause unprecedented damage in the real world. Not dissimilar to a protest of teachers at a school or the shutting down of a library in a budget cut - effects are noticed and people begin to make change. Further endorsing danah boyd's theories, she suggests that technological frameworks often imitate social constructs and communicative patterns - hence why we act and "behave" online similarly to how we would in the real world. Sites like Wikipedia are seen and accessed in the same way one would a library or a series of encyclopedia - through glossaries, indexes and pages. Similarly, news websites are accessed just as one would a newspaper - through various stories on pages. The real and virtual world are so deeply connected to one another, that an upset or change in one can be pivotal in how the other progresses.
Deep Web
[edit | edit source]The Deep Web refers to websites that cannot be found by conventional means, for example through common search engines like Google. It is said that the Deep Web is much larger than the Surface Web, and is often described as the "bottom of the iceberg", but there is no way to be sure due to its extremely private and exclusive nature.[200] People use the Deep Web to test websites before they go "live" on the surface web, and businesses can use the deep web for staff-only information, but the Deep Web is most often talked about when talking about the Dark Web.
The Dark Web is a part of the Deep web, and refers to all the illegal activity happening within it, like mass drug and weapon trafficking, hitman services, hacking software, terrorists networks, amongst many other examples. Due to the nature of these websites, many people who frequent this part of the web want to do so with the most online anonymity possible. Many use softwares like Tor that hide the user's location and history so it's extremely difficult for anyone to track any criminals on the Dark Web. A lot of the websites on the Dark web are peer-to-peer or invitation only, which also makes it harder for non-criminals to infiltrate and take down these kinds of sites. The most well-known example of a big Dark Web operation being successfully taken down is the Silk Road, which was an online marketplace for drugs, and was taken down by the FBI in 2013.[201] However, many other similar marketplaces popped up on the Dark web almost immediately after. Since both the Dark Web and the Deep Web are so private, and of a completely unknown and unmeasurable size, it's very hard to study it and to take down any of the highly illegal and publicly-dangerous services and information found there.
Security and Sphere Invasions
[edit | edit source]Private Sphere Invasions
[edit | edit source]It is without a doubt that the 21st century of digital media has progressed to the extent that we somewhat live and manage our social and private lives digitally. Interestingly, it seems that due to these on-going inventions of new technology, we are more willing to manage and store our personal and private information on various online/digital forms, as opposed to traditional manual filing. This switch to digital brings with it advantages in terms of quickness, convenience and tidiness, but there are also disadvantages, particularly relating to security and the safety of keeping this information private. Although the introduction of these new technologies were invented specifically to attend to our ‘needs’ or for general convenience, this has sparked concern over whether or not our private information is now more vulnerable to invasion. In today’s digitally orientated world, it would certainly seem that our private spheres and our control over how 'private' they are is shrinking, and nothing is really as private as we would like it to be any more.
The question to be asked here is, why do we manage so much of our personal and private information, such banking and contact details through these technologies when there is such a risk of it being invaded?
Perhaps this is a result of the general public conformity to the digital-way-of-living which has progressed very quickly since the beginning of the 21st century. Branston and Stafford [202] state that one of the main pros of this switch to digital is the ability to create digital copies or duplicates of information which was once stored manually, allowing for the use of less physical space and the ability to then create more duplicates for backup with minimal effort. We live in a world now where almost everything is done digitally, therefore everyday tasks and management of personal and social information is made much more easy and convenient, so it is understandable why we are so unlikely to covert back to a non digital, manually organised way of living.So, in overview, it seems that today’s technologically advanced society strive for a quick and easy organised digital life which overpowers the concerns over the risk of it all being invaded.
Below are two case study examples of digital media inventions which have brought with them many risks of private sphere invasions for their users.
Online Banking and Contactless Bank Cards
[edit | edit source]One example of a way in which we can ‘digitally store’ private information is through online banking. The process of online banking itself is known to be very secure, for example, RBS users are required to complete a two-page log in process to ensure that it is not being hacked or invaded by outsiders or fraudsters. Accessing this information has been made very secure, however with the introduction of the new Contactless bank cards, could our private online banking, or banking in general be under more risk of invasion?
These cards were invented initially in 2005 in America, and were brought to the UK in 2012, where It had proved to be a success, with over 58 million used in the UK by summer 2015. This new payment method was introduced to enhance our experience in managing our payments and expenses. ‘Contactless’ refers to the physical use of the card, as payment can be withdrawn from a bank account without any physical contact between the card and the pin machine, and without the need for any confirmation of the card’s pin code. This enhancement of digital media certainly proved popular shortly after its release in the UK, however, almost just as quickly, concerns began to spread over whether this new ‘convenient’ way of making a payment was really all that secure. With such a new and easy way to pay for goods, the contactless bank card invention was bound to spark concerns over the security of user’s bank details.
One of the main concerns with using these new cards is the risk of having money stolen much easier than it would with traditional, pin coded bank cards. According to an article written by Lisa Bachelor in The Guardian, It was found that, after various testing of contactless cards on ‘fake’ scanning decives, it was found that it is possible to read crucial data that was meant to be hidden, opening up the risk of invasions by fraudsters using such devices. Despite these concerns, it seems that the card is still vastly popular due to social conformity and the general excitement amongst society of this new invention. On top of this, many users concerned over the risk of paying twice due to the card's over sensitivity when in contact with a scanner, however the quickness of payment that it brought with it overshadowed this concern, especially in busy environments such as London train stations. It is also rumoured that this ‘contactless’ motion allows the government to use the card’s function to track its citizens details and whereabouts.
These concerns may seem extreme, and this suggests that the Media Multiplier effect, as described by Athique,[203] perhaps plays a part in the growing concerns raised over the use of contactless bank cards. This suggests that the growing discussions of concern between users of the mass media have multiplied to the point that there is a greater worry amongst society than is necessary for how unlikely it is that these events will happen. This reaction is due to the overwhelming hype of this new invention, and the excitement of what is a very 'futuristic' tool that is now so readily available at our hands.
Perhaps today's digital world has made our every day tasks just 'too easy' that we are oblivious to the risks, or perhaps it is this easiness that is sparking the concern amongst society.
iPhone Fingerprint Scanning
[edit | edit source]Apple are notoriously known for their technological advancements, especially with their ever changing and ever improving iPhone device. In 2013, however, Apple introduced the new fingerprint scanning feature on their iPhone 5 devices which was supposedly a new 'safer' way for the user to unlock their phone. This, however, was quick to spark concerns and kick up a storm amongst its users.
The main concern raised over this new and exiting iPhone feature is how extremely easy it has been found to hack into. Activist groups such as Anonymous and even our own government have been said to have the greatest control over using this tool for invasions. Not only can these invasions steal personal information stored on the devices, it can also reveal the user's whereabouts, and of course, give a digital print of their fingerprint. This type of information can lead to many issues such as fraud and identity theft, but the main concern amongst society seems so be of its likeliness to allow the government to track its citizens whereabouts.
Perhaps society conformed to using this new Apple feature due to the excitement of advancing technology, as it is different from anything that has been readily available to the public before. Fingerprint scanning is something that society is used to associating with spy-detective type films, or just policing and investigations in general, and this is due to the connotations it has with representations [204] created through the media. With this media effect in mind, it is clear to see why this feature was received so well.
Public Sphere Invasions
[edit | edit source]Although many are concerned with private sphere invasions and the threat of hacking private information, invasions of the public sphere must not be overlooked. There are ways companies and users are creating negative side effects through public spheres such as filter bubbles, echo chambers and trolling. Facebook for example explain how they control your public experience online:
The stories that show in your News Feed are influenced by your connections and activity on Facebook. This helps you to see more stories that interest you from friends you interact with the most. The number of comments and likes a post receives and what kind of story it is (ex: photo, video, status update) can also make it more likely to appear in your News Feed. [205]
In having different experiences through filtering and personalization, where does the line between private and public sphere end? We are building a web for ourselves instead of a web for everyone.
Filter Bubbles & Algorithmic Gatekeepers
[edit | edit source]Eli Pariser is the chief executive of Upworthy, a website for "meaningful" viral content and is an internet activist. He discusses Filter Bubbles in his publication The Filter Bubble: What the Internet Is Hiding from You and his TED Talk.
| “ | Your filter bubble is your own personal, unique universe of information that you live in online. What’s in your filter bubble depends on who you are, and it depends on what you do. But the thing is that you don’t decide what gets in. And more importantly, you don’t actually see what gets edited out. | ” |
Results on Google for example are now dependent on your location, device being used and browser meaning there is no standard Google anymore. This acts as an invisible filtering of the web, with platforms using information they have obtained about you to design your online experience to match you specifically. Pariser refers to this invisible algorithmic editing of the web as the work of ‘Algorithmic Gatekeepers’. This controlling curation of how we see the world online suffers from focusing too much on relevance. Other information that should be delivered in the public sphere should be important, uncomfortable, challenging and from other points of view according to Pariser. These gatekeepers must have encoded a sense of the public life and civic responsibility, offering us more control over what enters our filters.
However, personalization on the web has led to tailor made results, based on previously visited shopping websites for example, and users experiencing different results online by their own choice also. This act of filtering comes from the user and has a wider effect on the public sphere. Although advantages come with this act of filtering such as targeted advertisements, which cold act a a 'reminder' that you have visited a particular website in which you may like to return, and results that seem most suitable and relevant, users' ability to manipulate this personalization has side effects. users' tendency to consume information that supports their own opinions leads to a restricted and biased perspective online - receiving information in the public space that is tailored to match their interests. Therefore, certain information online can be ignored by users due to filter bubbles, meaning if information isn't deemed relevant to the user it will be dismissed. This may relate to the information overload online as the amount of information available online can seem overwhelming, irrelevant and distracting - however a balance needs to be met.
Echo Chambers
[edit | edit source]An echo chamber is a situation in which information, ideas, or beliefs are amplified or reinforced by transmission and repetition inside an "enclosed" system, where different or competing views are censored, disallowed or otherwise underrepresented. As a result of filter bubbles, echo chambers are created in which mainstream and popular beliefs dominate the public sphere. There is a decrease in original thought and excessive repetition of opinion in order to be validated by like-minded people.
If you surround yourself with voices that echo similar opinions to those you’re feeding out, they will be reinforced in your mind as mainstream, to the point that it can distort your perception of what is the general consensus. Martin, 2013.[207]
Leon Festinger's research into cognitive dissonance shows that people would look to actively seek out reassuring voices in order to confirm their beliefs and resolve their internal conflict.[208] This pollutes the public sphere as the online space remains unchallenged and predictable, offering only what user want to see. There is also the issue that not all public interactions are linked to your personal identity, as online identities and anonymity must be considered when looking at invasions of the public sphere. Opposing comments and contrasting opinions for example, can even be mistaken for "trolling".
Trolling
[edit | edit source]Trolling is where internet users post negative or extreme content with the intention of causing disruption.[209] They do this to create a reaction among the public. In some cases they are aware that they do not have an identity to others and appear anonymous so feel this can not be traced to them or their personal identity in the real world. With this identity hidden they lose a sense of morals and reasoning as they have lost all sense of one-to-one contact and no longer see the people they are arguing with as people but as words on the screen. This can be very dangerous as there tends to be no boundaries if the user is anonymous they can do as they please. Some may feel as though they are outspoken [210] in the real world and are stereotyped physically where as online gives them the opportunity to change this as they are anonymous no one can personally attack them as they do not know them. They often want to create an argument or cause trouble which sometimes is not even relevant to the topic others are discussing.[209] Posts can be uploaded in spaces where they know the views of the other user and deliberately post their opposing opinion to cause chaos and disruptive or opposing issues. They are deliberately unsettling the peace just to create an argument. Much of the content posted by these types of people are things they would never think of saying to a person if they were interacting in the real world as people are aware of what is socially acceptable but with online taking away the identity and personal aspect interaction becomes much more impersonal. This making trollers very hostile showing little remorse for anyone else. Often they get empowered through these types of activities much like bullying in the real world, especially when they spark a big reaction. This invasion of the public sphere can escalate to serious threats transitioning from the digital space to the real world. The amount of freedom in the public sphere becomes questionable as although we should not be restricted to the laws of algorithmic gatekeepers, our freedom to create our own filter bubbles and take advantage of anonymity online through trolling must be considered.
Theorists
[edit | edit source]Here are some of the theorists that help bring this topic together.
Zizi Papacharissi
[edit | edit source]Dr. Zizi Papacharissi was born and raised in Thessaloniki, Greece. She holds a BA in Economics and Media Studies from Mount Holyoke College (1995), an MA in Communication Studies from Kent State University (1997) and a PhD in Journalism from the University Texas at Austin (2000). She is the Professor and Head of the Communication Department at the University of Illinois-Chicago for more than seven years now and also the chief editor of the Journal of Broadcasting and Electronic Media. Her research focuses on new media technologies and the consequences they carry within them in a sociopolitical level. Her book, A Private Sphere: Democracy in a Digital Age (Polity Press, 2010), discusses how we practice politics in a digital age. She has edited A Networked Self: Identity, Community, and Culture on Social Network Sites (Routledge, 2010), and Journalism and Citizenship: New Agendas (Taylor & Francis, 2009). She has studied blogs, online journalism, social network sites, privacy, civility, self presentation in digital environments, and sociability online. She has also researched how terrorism is portrayed in international news, and the uses and consequences of reality TV.[69]
In her book A Private Sphere (2010) Papacharissi underlines a shift between the relationship of public and private spheres in recent and past societies. In the traditional democratic framework, people were enabled through the public sphere as the sense of the private was only associated with the enclosed and fractured spaces of ‘home’. In contemporary democracies though, she discusses, ‘the citizen becomes politically emancipated via a private sphere’.[20] Participation in online protests, expressing political opinion on blogs, engaging actively or passively with YouTube, posting a comment in an online political discussion ‘represents a dissent with the public agenda, determined by mainstream media and political actors’.[20]
| “ | Within this private sphere, the citizen is alone, but not lonely or isolated. << | ” |
—Zizi Papacharissi [20] | ||
This is the result of the new media as they have a dramatic effect on the compression or expansion of temporal and spatial relations between public and private spheres. Today more than ever people can participate in public events from the comfort of one’s private zone because of the benefits of the converged technologies. Those modern communication media have the ability of ‘transforming the private sphere of the home into a space that is both public and private’.[20] To consolidate her argument Papacharisssi invokes Raymond Williams and his concept of mobile privatization, the ability of the media of braking and transcending the spatial and temporal boundaries of the home and travel around the world without mobilising physically the human being. That’s what she describes as the ‘networked private sphere’ a sphere that is only accessible in the past 10–15 years, as this ability of remaining in the comfort of your well known space while simultaneously being able to encounter the other or the unknown is only provided by the unique hybridity of the online converged technologies.
“ The private sphere model traces the progression of a citizen who has retreated from the public sphere of interaction to a technologically enabled mobile private sphere of thought, expression, and reaction, in search of ultimate autonomy and expression.[20] - Zizi Papacharissi ”
She goes on to argue that through this ‘performative storytelling of the self’, in this familiar environment the political discourse is enhanced as the temporally and geographically fluid environments suggest the illusion of ultimate autonomy, control and expression. She defines as the “mobile private sphere’ the one that ‘enables the frequently monitorial citizen to efficiently balance conflicting and potentially overwhelming civic demands”.[20] A Private Sphere: Democracy in a Digital Age (2010) thus, attempts to conceptualise how the self-driven, digitally-enabled private acts can cause a publicly political sensation. (Online resource)
Jürgen Habermas
[edit | edit source]| “ | [Public sphere is a] [...] realm of our social life in something approaching public opinion can be formed [...] [and where] access is guaranteed to all citizens [...] [.]<< | ” |
—Jürgen Habermas[69] | ||
Jürgen Habermas is a German sociologist and philosopher who had written extensively on the public sphere in The Structural Transformation of the Public Sphere (online resource).[211] Habermas argues that "European society in the middle ages showed no indication of a public sphere as a 'unique' realm distinct from the private sphere”[212] but nowadays European culture had transitioned from a “representational” culture, to Öffentlichkeit (the public sphere). Using Marxist theory as a template, Habermas theorised that as representational culture corresponds to the feudal stage of development that there would be a coming of the capitalist stage of development marked the appearance of Öffentlichkeit.
Whereas “representational” culture is primarily concerned with this transition to Öffentlichkeit is characterized by the emergence of a public space where individuals can engage in an exchange of ideas and knowledge, all outside the control of the state. Social institutions such as newspapers, reading clubs, coffeehouses and masonic lodges were all popular meeting places for discussion and media outlets such as letter, books and theatres were used to spread the rhetoric of the public sphere. But the more media rely on advertising-funding, the more they are a gateway for privileged private interests in the public.[211]
Speaking about Internet based public spheres providing a forum for those, who wants to participate in a critical debate, Habermas thinking of the public sphere does not imply, that it every member of the populous nor all Internet users can engage in a meaningful discussion. Following that Ubayasiri argues, that "[...] the internet’s potential in creating public spheres, can be and has to be harnessed by ‘public intellectuals’ if the cyberspace is to fulfil its potential as a forum for public spheres."[213]
Habermas also researched about media reception and usage, developing his famous Theory of Communicative Action. Within that he thinks about the coordination of social action of communicatively talented humans, meaning communication oriented actions of mature people. He connects living environment perspective (social integration) and systematic perspective (system integration). On that basis he mentions media usage as a social action for human beings.
Hamid Van Koten
[edit | edit source]Hamid van Koten is an expert and a practitioner in the field of eco-architecture. His work consists of teaching creative enterprise skills as head of Post-Graduate Studies at the Plymouth College of Art as well as previously as director of Design History, Theory and Practice at the University of Dundee. He also contributed to the Findhorn Ecovillage at the Findhorn Foundation, Scotland, and is a qualified Transition Towns Trainer. Hamid and family live in an intention community near Totnes. In The Digital Image and the Pleasure Principle: the Consumption of Realism in the Age of Simulation [58] he talks about McLuhan's (Marshall McLuhan) technocratic determinism. [70] His main research questions are: What are the forces at work in the production and consumption of digital representations
Hot and Cool media McLuhan classifies different procedures of media through something called a temperature scale in which consists of hot and cool mass Medias. A media type is measured hot if it heavily and immerses one logic in particular.
| HOT MEDIA | COOL MEDIA |
|---|---|
| Novel | Poetry |
| Photo | Comic |
| Written words | Spoken Words |
| Low Participation | High Participation |
| Radio | Telephone |
| Cinema | Television |
Above is a table which shows a number of hot and cool medias side by side with their counterparts. For example: A photo offering visual information more clearly, whereas a drawing of the same thing may need to be construed in terms of shapes and colours and possibly have a meaning behind it.[58] These are the dominant forms of digital representations and the main theories that Van Koten desires to work with. “A shift from the real to the imaginary as the dominant drive”. Research
Comparable to McLuhan’s idea of hot and cool media is the notion of 'Light on' 'Light through' media. ‘Light on’ media is when the light source bounces off a surface or object before hitting the viewers’ eyes. Light on would be classed as 'hot' as it is 'all revealing'. Therefore the light is projected onto a screen. ‘Light through’ media is light source is positioned in front of audience, making the audience the screen by projecting light onto them. ‘light through’ is less revealing, more “mysterious” so therefore cool.[58]
Mike S. Schäfer
[edit | edit source]Mike S. Schäfer is a German sociologist, Professor of Science Communication, and Director of the Centre for Higher Education and Science Studies (CHESS) at University of Zurich, . Together with Jürgen Gerhards, Professor for macrosociology at the Institute of Sociology of the Free University of Berlin, Schäfer researched the comparative differences of the internet and traditional mass media as conduits of influence on wider society.[214]
Schäfer theorizes that normative theorists of the public sphere, such as Jürgen Habermas, , have been very critical of the ‘old’ mass media, , which were seen as unable to promote free and plural societal communication. The advent of the internet, in contrast, gave rise to hopes that it would make previously marginalized actors and arguments more visible to a broader public. To assess these claims, Schäfer compares the internet and mass media communication.
| Traditional public sphere | Internet-based public sphere | Organizational Prerequisites | Openness for participation | Impact on society |
|---|---|---|---|---|
| Encounters | Email, messaging, ect. | Low | High | Low |
| Public Events | Discussion boards, blogs, ect. | Middle | Middle | Middle |
| Mass Media | Search engines | High | Low | High |
It distinguishes three levels of both the offline and the online public sphere, which differ in their structural prerequisites, in their openness for participation and in their influence on the wider society. Using this model, Schäfer compares the levels that are most strongly structured and most influential for the wider society: the mass media and communication as organized by search engines.
In their study, Schäfer and Gerhards found only minimal evidence to support the idea that the internet is a better communication space as compared to print media. Despite the facts that the internet is an easily accessible medium with low entry barriers, in both public spheres the discourse was dominated by scientific actors without inclusion for others occurring.
Brian Loader
[edit | edit source]Brian was born in Zimbabwe in 1958. He grew up in the UK before he began studying at Southampton University in 1978 and continued studies till 1981 where he achieved an honours degree in politics and Sociology he taught in Southampton before he gained a masters in 1989 in Public policy from university of Bristol. He then continued with his teaching in the University of Teesside during his period there he became the founding editor of the international journal of Information, Communication and Society. He is now part the University of York as a senior Lecturer and he follows his interests of New Media.[215]
Cyber space divide
In this Brian loader introduces the prospect of an information society and how this will cause a cyberspace divide. Here Loader looks at how the internet will affect the private and the public spheres, he states that
“No sphere of life will be unaffected by the information revolution”.[216]
Because of this loader looks at the implications on social and political structures, as information and communication technologies (ITCs) will be an ever apparent part of life. Loader continues to look at how this will affect the world by looking at the idea of the cyberspace and how this will allow those who use it to be not only “information rich” but cyberspace will “offers liberating possibilities of ‘ordinary’ people constructing new identities which free them from the imposed classifications of class, race, gender or disability associated with material space”.[216]
This is loaders idea of people having a persona online where they are free from there constraints they may have in their everyday lives. He also adds the idea that anonymity will play a massive role in inventing an alternative version of themselves, and this will only be achieved through “virtual spaces”.[216] Loader evidently concludes that the information society will be further developed by social forces who will lead it to become a space for people with in the private and the public spheres.
Young citizens in the digital age Here loader continues his idea but by looking at youth citizens and their involvement in ITCs with politics. He introduces the idea of Cultural displacement with young citizens and the political systems that are in place, and how due to information communication technologies (ITCs) it generates a disconnect.
Firstly Loader provides us with an explanation to cultural displacement. Loader sees the disconnect of youth with the political system is due to the politicians as they “Appear distant and self-absorbed and unable to empathise with young people’s experiences of the dramatically changing social and cultural world” [217] he believes that this disconnect is because of youth culture and how it doesn’t relate with old political systems because of new ITCs and because of this it cause a contrast with youth “communication spaces” [217] with this in mind loader also continues to confirm that this provides a “digital divide” [217] the idea that through these channels youth are divided from current politics and are more infatuated by celebrity culture.
Loader also comments on the idea of individualisation that is in youth culture and new media. Brian defines individualisation as the “individualised agendas characterised by the ongoing activates of choosing between various lifestyles and fashion statement shaping and expressing ones persona, celebrating body forms and artistry, and developing and managing social networks of friends, family and associates” [217] Loader here is stating that youth culture with the introduction of new media has led to a decline in political culture due to the youth having more pressing personal agendas to attend to, he backs this idea up by looking at the decline in the amount of voters (estimated 37% in 2005 voted)[217] aged 18 to 25 because they are “disaffected citizens”[217]
Loader does however indicate the importance of new media and politics where he indicates that youth culture will offer more opportunity for understanding politics. This due to the fact new media and its involvement within the political system will “engage in political deliberation and challenge state authority” [217] In turn Brian Loader believes that new media will help with overall engagement in youth activity within the politics of today with help of new media.
Nicholas Garnham
[edit | edit source]Nicholas Garnham is a British researcher and Emeritus professor at the University of Westminster. He has played an important role in British Media and Communication Studies, and the Political Economy of Communication. His works have covered in particular topics as capitalism and comunication, the cultural industries, public service media, the public sphere, and the theory and sociology of culture.
He is the first one who used the term "cultural industries" for the first time, with which he distances himself from the accepted meaning of cultural industry connected to mass culture. In his Capitalism and Communication (online resource)[218]., he argues that “cultural industries” are institutions in which the production and spread of mass culture are influenced by capitalism. So, according to Garnham, publishing industry, record companies and business organizations use capitalism in order to achieve more profits. After 1977, the term "cultural industries" turns in "creative industries". Garnham argues that the reason of this shift happened not just to give cultural industries an economic importance, but also—and especially—to put in contact cultural industries to the information society and the knowledge-based economy.
Garnham is also the most responsible for introducing the “public sphere’ notion into the media debate, arguing that, especially in the case of television, public service is being replaced by privatized markets. Television offers to viewers few options from which they can choose from and it has become increasingly subjected to deregulation and privatization under market control. On the contrary, according to him, public service manages to satisfy more people, based on what they like, rather than just satisfying those tastes that help increase profit. A market allocation of cultural resources, combined with the destruction of public service media, threatens ‘public communication’ which, in his opinion, lies at the heart of democracy.
Lincoln Dahlberg
[edit | edit source]Lincoln Dahlberg has broadly published articles in the areas of media politics and public sphere theory.[219] In one of his last works, he decided to discuss the possibility of enhancing the public sphere through Internet by considering a case study on the Minnesota E-Democracy project. Thus demonstrating that despite some significant limitations, Internet can improve and extend the public sphere but in order to do so it has to meet six crucial criteria.
“ Dahlberg (2001) argues six fundamental criteria need to be fulfilled for the Internet to be considered a public sphere – autonomy from state and economic power; exchange and critique of criticizable moral-practical validity claims; reflexivity; ideal role-taking; sincerity; and discursive inclusion and equality.[213]
- Kasun Ubayasiri ”
- Autonomy from state and economic power: according to Dahlberg the interaction between citizens should be free from the influence of the state, meaning that people are allowed (and should have) a public opinion on the state and they should have power on the government. Nevertheless, it should not be the other way around: state and corporate colonization of the cyberspace should not threaten nor control online public spaces. However, according to Dahlberg, it is not fully possible to avoid the state influence as Internet is strictly connected with the socio-political context.[212]
- Exchange and critique of criticizable moral-practical validity claims: “arguments must be addressed not just to those present in conversation but to all others potentially affected by the claims under consideration, to the ‘larger’ or ‘ideal’ or ‘virtual’ community of discussants." [212]
- Reflexivity: communication should be based upon relevant arguments, participants should be able to question their own positions regarding their values and beliefs and they should be able to take someone else’s position when validity claims are offered.[212]
- Ideal role taking: participants will try to understand and not bypass differences and they will consider a certain situation from other people’s perspectives, it implies an ongoing communication and honesty from the participants. This criteria leads to another important aspect to take in consideration: sincerity.[212]
- Sincerity: communication is based upon honesty and openness. The online public sphere requires sincerity in order to exist, information needs to be accurate and people should not intentionally lie. It could be argued that according to Dahlberg’s ideas about honesty, the whole concept of Persona should not exist, as people try to create an online identity that not always is an honest depiction of the real identity. Moreover, Internet users do not always share their real thoughts and it is almost impossible to be honest about everything so the condition of honesty is hard to achieve, therefore grand part of Dahlberg’s criteria cannot be fulfilled as they all take in consideration an idealized society.[220]
- Discursive inclusion and equality: everyone should have the same possibility to be part in a discourse, people should not only be formally included but their ideas should be considered at the same level. This criterion, as the other ones, presupposes that social inequalities do not affect the participation. However, Dahlberg himself noted that in the case study of the Minnesota E-Democracy social and gender related inequalities still tend to favour men over women and people with a specific knowledge rather than people with general interests. As, it happened with the Minnesota E-Democracy project, we can also face exclusion when we are entering a discourse, simply because others may have more predominant personalities, therefore it is hard to achieve the idealised condition where everyone is equally important in a discourse. Hence, we need to put a particular effort in it, so that diverse styles of speaking can be treated with the same respect and can have the same importance.[220]
John Thompson
[edit | edit source]John Thompson is a British Sociology professor at the University of Cambridge and a Jesus College Elite member. In his life, he has studied the influence of mass media in the development of modern societies, and the creation of new forms of action and interaction beyond temporal and spatial frameworks. His work “The Media and Modernity: A Social Theory of the Media” [18] is the attempt to formulate a social theory about mass media, by analysing the complex relationship between the medieval industry and the economic, political and coercive powers. Thompson argues a theory that bears in mind the roles of mass media in the modern society, opposing to those who considerate mass media just as a reflection of the social, economic and political conditions in the previous ages. Thompson is strongly influenced by Hans-Georg Gadamer and the hermeneutics, which studied the philosophy and methodology of text interpretation. In “The Media and The Modernity: A Social Theory of the Media”, Thompson analyses the term “mass”, affirming that most of the mass media are not produced for the masses, but for niche markets. Since the term “mass” evokes the image of a vast public (million of individuals), Thompson discusses it, contrasting the concept of “ mass communication” (too abused, in his opinion) to a face-to-face interaction and the two-way process that takes place when people talk to each other. He believes that there are more suitable terms when we deal with “mediated communication or, more simply, 'the media' which are less laden with misleading assumptions.”[18]
Thompson critics Habermas’ concept of ‘publich sphere’, arguing that in the modern society there is a new form of “mediated publicness”. This mediated publicness has some main characteristics, which are:
- Despatialized (people don’t need to share the same location to see more things, but they don’t have control of the angle of this extended vision);
- Non dialogical (for example, presenters on TV are visible to an audience, but not the other way round, so that means they cannot adapt their discourse to the reactions of the public)
- Wider and more diverse audiences (people with different education, different social class, different values and beliefs can get the same message).
Now, thanks to this mediated publicness, the many are visible to the few and the few can also see the many:
"Whereas the Panopticon renders many people visible to a few and enables power to be exercised over the many by subjecting them to a state of permanent visibility, the development of communication media provides a means by which many people can gather information about a few and, at the same time, a few can appear before many; thanks to the media, it is primarily those who exercise power, rather than those over whom power is exercised, who are subjected to a certain kind of visibility." [18]
Integrating themes
[edit | edit source]In the last section of this chapter, we will discuss and discover the common themes occurring throughout this Wikibook. In this section, we have looked at Public and Private Spheres in the Digital Age. However, Technological and Cultural Determinism[221] can be strongly linked to this section, as well as some points which are taken from Access to Knowledge and Data in Everyday Life. We will lastly discuss the section of Surveillance and Sousveillance.
Cultural Determinism, as already outlined earlier in this book, is ultimately defined as the way in which society is affected by the cultural change; how this change may affect our character, our beliefs, and our interactions with one another. Technological Determinism is therefore how technology affects our culture and wider society. Marshall McLuhan (1964)[222] argued that cultural shifts are caused by innovations in media technology. We can see that this is quite prominent in today’s society. As discussed earlier, the invasion of the Private Sphere in the digital age has changed the way we go about our everyday life. Before the creation of the internet and social media platforms, the home was our private space, unless someone called you on your landline, you were unavailable. Now there is pressure to be constantly available through text message or other forms of digital communication.
There can be no doubt that the spread of technology has changed our way of life. This has had many positive effects, it has helped bring people together and has also helped to engage the citizen in a democracy. One of the more interesting arguments is that of a Global Village;[222] McLuchan (1964) came up with this idea that due to electronic technology, information can be spread and sent instantly. This could not be more true in today’s society. Thanks to such apps like Facebook Messenger, you could communicate with someone located hundreds of miles away, as if they are were down the street. Which leads us to discuss how important our online identity is. The online identity is also part of the public sphere. The public sphere is how we present ourselves in the public domain, whether this is in person or online, there is a way that we want to portray ourselves. With the rise of the Global Village, more and more people can view our social media activity. Due to this, there is now a pressure, especially among young people, to look and play the part on social media and to be “always on”.
The pressure to be “always on” is discussed in the Access to Knowledge and Data in Everyday Life chapter of this wikibook. Ultimately, this means that we are pressured to be available twenty-four hours a day, seven days a week to be contacted via social media. Long gone are the days of splendid isolation. Due to the global village effect, our private sphere has been invaded because there is constant pressure to be “always on”. However, this has caused an information overload. As discussed later on in this wikibook, there are some who argue that because social media pacifies human-social-needs, we are shutting ourselves indoors and interacting electronically. An article by John Bingham (2016) entitled “How teenage pregnancy collapsed after birth of social media”[223] displays an argument that since the birth of social media the number of teenage pregnancies in the UK has fallen, and asks if there is a correlation. It could also be argued that the boundaries between our public and private spheres are being blurred. This is why many people place private information upon their social media platforms; it is not because they want everyone to know their business, but that it is a way of expressing oneself, all be it on a traditionally public platform.
As I have said earlier, social media has empowered the person and enlightened democracy. It has also, as discussed in Surveillance and Sousveillance, made way for the Citizen Journalist. Now people from their own private sphere can take part in news creation. This is also an example of “Sousveillance”. The Arab Spring has seen vast amounts of citizen journalism, ordinary people witnessing events and instantly documenting them. Also, thanks the rise of social media and different blog sites, the number of news outlets that we have to choose from has greatly increased. Websites such as Another Angry Voice (AAV) and Wings Over Scotland have been created and inform many different citizens. As highlighted later on in this wikibook, GCHQ was formed over the 1950s and 1960s and has taken part in many different security operations. The organisations conduct has been called into question lately, and with the Draft Communications Data Bill (2015) proceeding through the UK Parliament; and many different concerns with the proposed law, there is an argument that this Bill, if it became an Act, could intrude further on our already diminishing private sphere. However, due to current security threats, many would argue the proposals are needed.
To conclude, many of the different theories and ideas that are spoken about in this chapter can also be drawn into other chapters within this wikibook. It is important when reading through this book, to remember that all theorists and ideas link together in some shape or form.
Critical Review
[edit | edit source]As established, the social world has been split into two spheres; public and private. Martin Heidegger argued that it's through the private sphere where one can truly express themselves. For example, on social networking sites, you can allow your profile to be as private as you like, with options to disable showing certain information to people. One would assume that their information would be completely private and so in this case, Heidegger’s argument is valid. However, can we really assume that our private information is safe? He argues that people will only fully express themselves if they are under the impression that their information is private. For example, Facebook being able to use browser history to create advertisements [224] completely undermines Heidegger's argument. There will not be an opportunity for users to fully express themselves if they're aware that their information is not as safe as they believe.
Zizi Papacharissi argues that there has been a shift in the relationship between public and private spheres in society. The private sphere has always been associated with family or home. Papacharissi argues that nowadays, with the vast amount of portable technology available, members of society can now live and participate in public spheres more than ever but from the comfort of their own home.[225] This then allows the public and private spheres to merge together, allowing people to have the best of both worlds. It can be argued that, with Heidegger’s point that it doesn’t, nowadays, necessarily mean that the private sphere is valid from the home and it is more to do with the idea of how much information you want to express of yourself, which in turn would make Papacharissi’s argument invalid. It is however a strong argument otherwise and determines the idea that public and private spheres are not poles apart like they once were.
Brian Loader argues that an information society will cause a cyberspace divide. He states that because people have the opportunity to be someone fake and virtual online, they are in turn able to escape the stigmas they may face in everyday life. This is where Papacharissi's argument of the shift between private and public spheres is really relevant.[216] If one is wanting to stay in the private sphere when it comes to their online activity but still wants to participate in the things the public sphere has to offer, they are able to create a fake persona with false information that doesn't determine them as a person, but can then still share this information with others. Loader then believes that by doing this, it can give, especially youths of society, a chance to participate in, for example, polls online concerning politics which then helps a young society become more involved in the world.
Glossary
[edit | edit source]Always-on
As explained by danah boyd,[9] the always-on culture is the connection to technology and need to be always available on either social media or online content.
Anonymity
Anonymity (or, as an adjective, anonymous) refers to when an individual is non-identifiable, unreachable, or untrackable. Online anonymity usually refers to the lack of an individual's personal details, as they communicate through a username.
Anonymous (group)
Anonymous is a loosely associated international network of activist and hacktivist entities. (See section 1.7.5.2)
Ascetism
As defined by Sennett,[50] desire for introspection through withdrawal from society in a process self-understanding that ultimately increase the public sphere's coherence. Indeed, this process allows for the achievement of values of control and autonomy, which are essential for a participating citizen.
Avatar (computing)
An avatar in virtual reality sites is the graphical representation of the user or the user's alter ego or character.
Catfishing
The act of deceiving another user online by adopting a fake identity (which can be made up or stolen). (see section 1.7.2.3)
Cyberbullying
The act of bullying online. (see section 1.7.4)
Cookies
In their most basic characterisation, http cookies are a small chunks of data that are sent to a user's browser when a user access a website and stored in the background while using. Every time the user logs back or visits that websites the cookies are sent back to their server, thus brining back information about the user's recent activity.
Cyberstalking
The act of stalking online. (see section 1.7.4.2)
Dark Web
Small section of the "Deep Web" mainly includes small invite-only networks and is infamous for being a hub of illegal activity. Seesection 1.7.7
Deep Web
Also known as the "hidden" or "invisible" web, the section of the internet that isn't discoverable through regular search engines. See section 1.7.7
Digital Age
The digital age describes the ongoing time frame since the end of the 20th. Characteristically for this age are the possibilities for ever person to store and transfer information digitally which have reciprocally influenced society. Please see disambiguation.
Digital Media
digital media all media types are counted which are based on digital information and communication technology (i.e. the Internet) as well as technical devices for digitalization, recording, processing, calculation, retention, storage, presentation and distribution of digital content and final products such as digital arts or music.[11]
Please refer to Characteristics of Digital Media
Digital self harm / Digital Munchausen
The act of users bullying or sending abusive messages to themselves online. Please see section 1.7.4.1
Dissociation
In psychology, it refers to a detachment from physical and emotional experience. When online, it refers to the physical and emtional detachment from 'real' life as one performs their online identity.
Encryption
Encoding of messages and information in order to prevent unauthorised parts to access them. Only those who possess a decryption key can do so.
Hacker
An individual that identifies a server's, computer's or network's weaknesses and breaches into them in order to extract knowledge and material that can serve different purposes.
Hacktivism
The work of a hacker that promotes a political or social agenda, such as exposure of corruption, human rights, free speech and freedom of information.
Identity
Identity is the make up of our character and the type of cultural values we choose, therefore impacting on our appearance online.
Media Multiplier Effect
As described by Adrian Athique in his book Digital Media and Society: An Introduction, the Media Multiplier Effect is the multiplying discussions of fear amongst society of its mass media, to the point of creating the impression that media invasions of privacy are more likely to happen than they really are.
Mobile Privatization
The ability of the media devices to mobilize and travel an individual while still having a strong sense of being at 'home' because of the attachment and connectivity with the mobile device. Seesection 1.9.1
Narcissism
Although often characterised as a psychological disorder, in Lasch's [47] and Sennett's [50] work, it represents the concerning that one's have regarding their own being. Narcissistic practices are self-centred and happen in accordance to a evaluation of which the self is in control but they are not self-motivated. Despite being self-based, they are not selfish.
Online Footprint
Amount of data left on the internet by a user and collected either without him knowing (passive footprint) or with his consent in order to share information with others (active footprint).
Online Performance
As defined by Mendelson and Papacharissi 2001, online performance is the selectiveness of our behaviour online and impacts on our social lives physically but also online - through social media. Online performance provides a mediated self and is a performance which may not reflect our normal lives.
Private Sphere
The part of peoples lives that they are supposed to have full control over, unaffected by institutions like the government, the home is an example. Please see disambiguation.
Public Displays of Connection
Public Displays of Connection are in reference to the way that we show the people around us the people that are our friends, family and colleagues. It is a concept described by danah boyd and Judith Donath [64] and in this article it's the way in which we show our connections to other people online, how we do it and the reasons why we do it. See (see section 1.5.1)
Public Opinion
Public opinion is "the collective opinion of many people on some issue, problem, etc., especially as a guide to action, decision, or the like."[226] It is a form of publicity and enforced through public communication. This has to be distinguished from a published opinion, an opinion expressed in public. Please refer to Publicity Online
Public Sphere
A "virtual or imaginary community, which does not necessarily exist in any identifiable space. In its ideal form, the public sphere is "made up of private people gathered together as a public and articulating the needs of society with the state." [69] Please see disambiguation.
Username
The 'nickname' an individual uses to identify themselves to the system.
Virtual reality
Virtual Reality replicates an environment that simulates a physical presence in places in the real world or an imagined world, allowing the user to interact with that world.
Web 2.0
The recollection of the collective abilities of members from an online network. A Web 2.0 site may allow users to interact and collaborate with each other in a social media dialogue as creators of user-generated content in a virtual community, in contrast to Web sites where people are limited to the passive viewing of content.
External links
[edit | edit source]- Introduction Video to "The New Digital Age"
- Online Fingerprint (Find out about your fingerprint here.)
- Extending the public sphere through cyberspace: The case of Minnesota E-Democracy
- A history of Minnesota Electronic Democracy 1994
- The persona, the false self, and the social network: who are you on Facebook?
References
[edit | edit source]- ↑ http://www.encyclopedia.com/topic/Public_sphere.aspx#3-1O88:pblcsphrvrssprvtsphrdstnc-full
- ↑ Private Sphere, Papacharissi, Chapter 5
- ↑ a b c d Lemke, C., Brenner, W. (2015). Einführung in die Wirtschaftsinformatik, Band 1: Verstehen des digitalen Zeitalters, pp. 11-51. Berlin, Heidelberg: Springer Verlag. Retrieved 03/08, 2016 from http://www.springer.com/cda/content/document/cda_downloaddocument/9783662440643-c1.pdf?SGWID=0-0-45-1486970-p176975505
- ↑ Friedman, T.L. (2008). Die Welt ist flach: Eine kurze Geschichte des 21. Jahrhunderts. Frankfurt a. M.: Suhrkamp Verlag.
- ↑ [1] Bush, V. (1945). As We May Think. Atlantic Monthly. Retrieved 02/28, 2016 from http://www.theatlantic.com/magazine/archive/1945/07/as-we-may-think/303881/
- ↑ a b [2], Computer History Museum. (2016). Personal Computer. Retrieved 03/08, 2016, from http://www.computerhistory.org/revolution/personal-computers/17/297
- ↑ [3], Cern. (2014). World Wide Web. Retrieved 03/08, 2016, from http://info.cern.ch/hypertext/WWW/TheProject.html
- ↑ a b c Rheingold, H. (2002). Technologies of Cooperation. Smart mobs : the next social revolution. Cambrige, MA: Basic Books.
- ↑ a b c d boyd, d. (2012) "Participating in the Always-On Lifestyle". In Mandiberg, M. (Ed.). The Social Media Reader pp.71-76. New York and London: NYU Press.
- ↑ Vermesan, O., Friess, P. (2013). Internet of Things: Converging Technologies for Smart Environments and Integrated Ecosystems. Aalborg: River Publishers. Retrieved 03/08, 2016, from http://www.internet-of-things-research.eu/pdf/Converging_Technologies_for_Smart_Environments_and_Integrated_Ecosystems_IERC_Book_Open_Access_2013.pdf
- ↑ a b Kossek, B., Peschl, M.F. (2012). Digital Turn?. Vienna: V&R unipress GmbH.
- ↑ a b Tasstudent.com (n.d.) Purpose and Characteristics of Digital Media. Retrieved: 03/02, 2016, from http://www.tasstudent.com/characteristics-of-digital-media/
- ↑ a b c d e f g h i j Bleicher, J.-K.(2010). Internet. Konstanz: UVK Verlagsgesellschaft.
- ↑ Berners-Lee, T. (1999). Der Web-Report. Der Schöpfer des World Wide Webs über das grenzenlose Potential des Internets. München: Econ.
- ↑ McLuhan, M. (1994). Die magischen Kanäle. Dresden/ Basel: Verlag der Kunst.
- ↑ Hickethier, K. (2003). Einführung in die Medienwissenschaft. Stuttgart/ Weimar: Verlag J.B. Metzler.
- ↑ [4] Kweon,S. et al. Time and Space Perception on Media Platforms in Proceedings of the Media Ecology Association, Vol. 12, 2011
- ↑ a b c d e Thompson, J. B. (1995). The media and modernity: A social theory of the media. Cambridge: Polity.
- ↑ Giddens, A. (1990). The consequences of modernity. Cambridge: Polity Press.
- ↑ a b c d e f g h i j k l m n Papacharissi, Z. A., (2013). Private Sphere: Democracy in A Digital Age. Cambridge, Malden, MA: Polity Press.
- ↑ Castells, Fernandez-Ardevol, Linchuan Chiu & Sey 2006
- ↑ a b [5] Lasén, A., & Gómez-Cruz, E. (2009). Digital Photography and Picture Sharing: Redefining the Public/Private Divide. Knowledge, Technology & Policy, 22(3), 205-215. http://dx.doi.org/10.1007/s12130-009-9086-8
- ↑ a b [6] Knewstubb, E. (2007). Photography in Public Places and the Privacy of the Individual (Bachelor of Laws (Honours). University of Otago.
- ↑ Westin, A. (1967). Privacy and freedom. New York: Atheneum.
- ↑ a b Chua, T.; Juanzi, L.; Moens, M. (2014). Mining user generated content. Chapman and Hall/CRC. p. 7. ISBN 9781466557406.
- ↑ a b c [7] Elsner, M.(2012). Essay I: Spreading the Word – Assessing the Factors that Determine the Popularity of User-generated Content”, In Marketing im globalen Wettbewerb - Marketing & Global Competition, Volume 2 : Information Propagation on the Web 2.0 : Two Essays on the Propagation of User-Generated Content and How It Is Affected by Social Networks, p. 21. Peter Lang AG, Frankfurt. ProQuest ebrary., Web. 9 March 2016.
- ↑ a b c d e [8] Chua, T.; Juanzi, L.; Moens, M. (2007) OECD (2007). PARTICIPATIVE WEB: USER GENERATED CONTENT. DSTI/ICCP/IE(2006)7/FINAL. p. 8.
- ↑ Christian A. (2011). User Generated Content – Urheberrechtliche Zulässigkeit nutzergenerierter Medieninhalte. Springer-Verlag Berlin Heidelberg. pp. 6-8
- ↑ [9] Cooper, N.. (2012). The growing importance of digital photo sharing to brand
- ↑ [10] Harvey, P. (2006). Top Ten Video Sharing Websites. Retrieved from
- ↑ Kolbitsch, J.& Maurer, H (2006). The Transformation of the Web: How Emerging Communities Shape the Information we Consume in Journal of Universal Computer Science, Vol. 12, No. 2 (2006), pp. 187-213.
- ↑ McNair, B.; Heinrich, A.; Volkmer, I; Firdaus, A.; Graham, T. (2013). “Part 2: Participatory forms of Journalism”, In Peters, C.; Broersma, M. (eds.) Rethinking Journalism, pp. 73-128. Routledge, Oxon. ISBN 978-0-203-10268-8.
- ↑ Copyright, designs and patterns act 1988
- ↑ Stokes, 2014
- ↑ a b Lothian, 2009
- ↑ Sassi, M. (2001). The science of man in ancient Greece. Chicago: University of Chicago Press.
- ↑ [11] Vovolis, T. Prosopon.The Acoustical Mask in Greek Tragedy and in Contemporary Theatre. Academia.edu. Retrieved 9 March 2016, from http://www.academia.edu/1086294/Prosopon.The_Acoustical_Mask_in_Greek_Tragedy_and_in_Contemporary_Theatre
- ↑ Kostera, M. (2012). Organizations and archetypes. Cheltenham: Edward Elgar.
- ↑ a b [12] Vovolis, T., & Zamboulakis, G. (2007). The Acoustical Mask of Greek Tragedy. Didaskalia, 7(1). Retrieved from http://www.didaskalia.net/issues/vol7no1/vovolis_zamboulakis.html
- ↑ [13] Barnhart, A. (2003). Erving Goffman. Web.pdx.edu.
- ↑ Ritzer, G. (1992). Sociological theory. New York: McGraw-Hill.
- ↑ a b [14] Aspling, F. (2011). The private and the public in online presentations of the self A critical development of Goffman’s dramaturgical perspective (1st ed.). Stockholm. Retrieved from http://www.diva-portal.org/smash/get/diva2:431462/FULLTEXT01.pdf
- ↑ [15] Grove, S., & Fisk, R. (1992). The Service Experience As Theater. Advances In Consumer Research, 19, 455-461. Retrieved from http://www.acrwebsite.org/volumes/7341/volumes/v19/NA-19
- ↑ a b Goffman, E. (1959). The Presentation of Self in Everyday Life. Garden City, N.Y.: Doubleday.
- ↑ D'hondt, S., Östman, J., & Verschueren, J. (2009). The pragmatics of interaction. Amsterdam: John Benjamins Pub. Co.
- ↑ [16] Jung on Persona
- ↑ a b Lasch, C. (1991). The Culture of Narcissism: American life in an age of diminishing expectations. New York,: W. W. Norton, 26-33
- ↑ [17] Premuzic,T. Sharing the (self) love: the rise of the selfie and digital narcissism in The Guardian, 13 March 2014
- ↑ [18] Fosco, Molly. Taking a Selfie Has More to Do With Self Worth Than You Realize in The Huffington Post, 5 June 2014
- ↑ a b c d e f Sennett, R. (1977). The fall of public man. N.Y., Knopf.
- ↑ a b c d e Mendelson, A.L., Papcharissi, Z., (2010). 'Look at Us: Collective Narcissism in College Student Facebook Photo Galleries'. In Papcharissi, Z., (Ed.). A Networked Self, pp. 251-273. Hoboken: Taylor & Francis.
- ↑ Networked Self, Papacharissi, Chapter 12
- ↑ a b http://www.journalism.org/2015/07/14/the-evolving-role-of-news-on-twitter-and-facebook/
- ↑ a b c Lanier, J. (2010). "Missing Persons". In You Are Not A Gadget (pp.3-23). London: Penguin.
- ↑ Lanier, J. (2006) DIGITAL MAOISM: The Hazards of the New Online Collectivism, Edge
- ↑ Marshall, P. David. Celebrity and Power : Fame in Contemporary Culture. Minneapolis, MN, USA: University of Minnesota Press, 2014.
- ↑ Meloy, J. Reid, and Sheridan, Lorraine. Stalking, Threatening, and Attacking Public Figures : A Psychological and Behavioral Analysis. Cary, NC, USA: Oxford University Press, USA, 2008.
- ↑ a b c d Van Koten, H (2009). The Digital Image and the Pleasure Principle: the Consumption of Realism in the Age of Simulation in Digital Visual Culture: Theory and Practice. Bristol: Intellect Books. p89-92.
- ↑ http://money.cnn.com/2014/05/28/technology/security/hack-data-breach/index.html
- ↑ Köhler, M., Arndt, H.-W., Fetzer, T. (2001). Recht des Internet. 7th ed. Heidelberg: C.F. Müller.
- ↑ a b c d e f g Schulz, W. (2008). Politische Kommunikation: Theoretische Ansätze und Ergebnisse empirischer Forschung. Wiesbaden: VS Verlag für Sozialwissenschaften.
- ↑ Hill, C. (2002). Öffentlichkeit im Internet. München: Grin Verlag.
- ↑ a b Noelle-Neumann, E. (1996). Öffentliche Meinung: die Entdeckung der Schweigespirale. Berlin: Ullstein.
- ↑ a b c d e boyd, d. Donath, J. (2004). Public Displays of Connection accessed 03/10 from http://www.danah.org/papers/PublicDisplays.pdf
- ↑ a b Beznosov, K. Boshmaf, Y. Jaferian, P. Rashtian, H., To Befriend or Not? A Model of Friend Request Acceptance on Facebook, University of British Columbia. Accessed 03/10 from https://pdfs.semanticscholar.org/2d3d/f8c0923dd249f370f287a1b236af1ecf0934.pdf
- ↑ link Carlisle, J. E., & Patton, R. C. (2013). Is social media changing how we understand political engagement? An analysis of Facebook and the 2008 presidential election in Political Research Quarterly, 66(4), 883-895.
- ↑ Putnam, Robert. (1995a). Bowling Alone: America's Declining Social Capital in Journal of Democracy 6 (1): 65-78.
- ↑ Bimber, Bruce, and Richard Davis. (2003). Campaigning Online: The Internet in U.S. Elections. New York: Oxford University Press.
- ↑ a b c Habermas, J. (1989). The Public Sphere: An Encyclopaedia Article. In: Bronner, S. E., Kellner, D. M. (2001). Critical Theory and Society: A Reader. New York: Routledge
- ↑ a b Salter, L. Democracy, New Social Movements and the Internet in McCaughey, M. (2003). Cyberactivism: Online activism in theory and practice. New York, NY; London: Routledge
- ↑ Anonymous. Government controlled media. Retrieved 06/03/2016 from http://iml.jou.ufl.edu/projects/STUDENTS/McCormick/govern.htm.
- ↑ [19] Khalip, A. (2007). Cerf sees government control of Internet failing
- ↑ a b c Meikle, G & Young, S. (2012). Regulation, Policy and Convergent Media. In: Media Convergence: Networked Digital Media in Everyday Life. Hampshire: Palgrave Macmillan. pp. 172-96.
- ↑ [20] Scmidt, Eric, E. (2014). The Future of Internet Freedom..
- ↑ Zittrain, J & Edelman, B. (2003). Empirical Analysis of Internet Filtering in China. Berkman Center for Internet & Society Harvard Law School. Retrieved 05/03/2016.
- ↑ Fuchs, C. (2014). What is a Critical Introduction to Social Media. In: Social Media: a Critical Introducion. London: Sage. pp. 7-25.
- ↑ Papacharissi, Z. (2009). The virtual sphere 2.0: The Internet, the public sphere, and beyond. Routledge handbook of Internet politics, 230-245.
- ↑ [21],Römmele, A. (2003). Political parties, party communication and new information and communication technologies. Party Politics, 9(1), 7-20.
- ↑ Zetter, L. (2007). The Political Campaigning Handbook: Real life lessons from the front line. Harriman House Limited.
- ↑ Shirky, C. (2011). The political power of social media. Foreign affairs, 90(1), 28-41.
- ↑ [22], McNair, B. (2011). An introduction to political communication. Taylor & Francis.
- ↑ [23], Dahlgren, P. (2005). The Internet, public spheres, and political communication: Dispersion and deliberation. Political communication, 22(2), 147-162.
- ↑ [24], Fieldhouse, E., & Cutts, D. (2009). The effectiveness of local party campaigns in 2005: combining evidence from campaign spending and agent survey data. British Journal of Political Science, 39(02), 367-388.
- ↑ Nittle, Nadra Kareem (2016-01-08). "Racist Republican Smear Campaigns in the 21st Cenury". About News. http://racerelations.about.com/od/diversitymatters/tp/Racist-Republican-Smear-Campaigns-In-The-21st-Century.htm.
- ↑ Banks, Ann (2008-01-14). " Dirty Tricks, South Carolina and John McCain". The Nation. http://www.thenation.com/article/dirty-tricks-south-carolina-and-john-mccain.
- ↑ a b Rainie, Lee (2012-10-19). "'Social Media and Political Engagement'". http://www.pewinternet.org/2012/10/19/social-media-and-political-engagement.
- ↑ Bennett, Shea (2014-12-24). "'The 10 Biggest Social networks Worldwide'". Social Times. http://www.adweek.com/socialtimes/largest-social-networks-worldwide/504044.
- ↑ Barthel, Michael (2015-07-14). "'The Evolving Role of News on Twitter and Facebook'". http://www.journalism.org/2015/07/14/the-evolving-role-of-news-on-twitter-and-facebook.
- ↑ "'What are the Facebook Group Privacy Settings?'".
- ↑ Al-Deen, H. S. N., & Hendricks, J. A. (2011). Social media: usage and impact. Lexington Books.
- ↑ Dickey, Megan Rose (2013-02-13). "'The 22 Key Turning Points in the History of YouTube'". http://www.businessinsider.com/key-turning-points-history-of-youtube-2013-2?IR=T.
- ↑ Rao, Leena. "'YouTube Launches Campaign Toolkit for Politicians'". TechCrunch.
- ↑ Krashinsky, Susan (2012-11-02). "'How YouTube has transformed the 2012 presidential election'". The Globe And Mail. http://www.theglobeandmail.com/news/world/us-election/how-youtube-has-transformed-the-2012-presidential-election/article4871244.
- ↑ Maletzke, G. (1963). Psychologie der Massenkommunikation: Theorie und Systematik. Hamburg: Hands-Bredow-Institut.
- ↑ Lasswell, H. D. (1948). The Structure and Function of Communication in Society. in The Communication of Ideas. A Series of Addresses. Bryson, L. (ed.). New York: Norton.
- ↑ [25] Bohannon, J. (2015). Is Facebook keeping you in a political bubble? American Association for the Advancement of Science. Retrieved 03/06, 2016, from http://www.sciencemag.org/news/2015/05/facebook-keeping-you-political-bubble
- ↑ Bentele, G., Brosius, H. B., Jarren, O. (2003). Öffentliche Kommunikation: Handbuch Kommunikations- und Medienwissenschaft. Wiesbaden: Westdeutscher Verlag GmbH.
- ↑ a b c d e f Vegh,S. Classifying Form of Online Activism in McCaughey, M. (2003). Cyberactivism: Online activism in theory and practice. New York, NY; London: Routledge.
- ↑ Company Info | Facebook newsroom. (2004, February 4). Retrieved March 11, 2016, from https://newsroom.fb.com/company-info/
- ↑ Company | About. (2016). Retrieved March 11, 2016, from Twitter, https://about.twitter.com/company
- ↑ Lewis, K. & Gray, K. & Meierhenrich, J. (2014). “The Structure of Online Activism.” In Sociological Science 1: 1-9. DOI: 10.15195/v1.a1
- ↑ Reesh, Anna. (2013). Digital and Online Activism. Retrieved from https://en.reset.org/knowledge/digital-and-online-activism
- ↑ Vraga, Emily K. (2013). The Rules of Engagement: Comparing Two Social Protest Movements on YouTube in CYBERPSYCHOLOGY, BEHAVIOR, AND SOCIAL NETWORKING. DOI: 10.1089/cyber.2013.0117
- ↑ Thorson K, Driscoll K, Ekdale B, et al. (2013). YouTube, Twitter, and the occupy movement connecting content and circulation practices in Information, Communication, and Society 2013; 16:421–451.
- ↑ Earl J. (2006). Pursuing Social Change Online: The Use of Four Protest Tactics on the Internet in Social Science Computer Review, Vol. 24 n 3
- ↑ UK Government and Parliament. Petitions. Retrieved from https://petition.parliament.uk/petitions
- ↑ [26], Reference Required
- ↑ a b Rahaghi, 2012
- ↑ link Reference Required
- ↑ http://www.wired.com/2015/10/how-black-lives-matter-uses-social-media-to-fight-the-power/
- ↑ [27], El Difraoui, A. (2011). Die Rolle der neuen Medien im Arabischen Frühling. Bundeszentrale für politische Bildung. Retrieved 02/27, 2013 from http://www.bpb.de/internationales/afrika/arabischer-fruehling/52420/die-rolle-der-neuen-medien?p=all
- ↑ [28] Mackey, R. (2011). Video That Set Off Tunisia’s Uprising in The New York Times, 22 January 2011
- ↑ [29] Preston, J. (2011). Movement Began With Outrage and a Facebook Page That Gave It an Outlet in The New York Times, 5 February 2011
- ↑ a b c [30] O’Donnell, C. (2011). New study quantifies use of social media in Arab Spring in University of Washington Today, 12 September 2011
- ↑ a b [31] Huang, C. (2011). Facebook and Twitter key to Arab Spring uprisings: report in The National, 6 June 2011
- ↑ [32] Iyengar, R. (2014). Six Questions You Might Have About Hong Kong’s Umbrella Revolution in The Time, October 5, 2014
- ↑ a b [33] Parker, E. (2014). Social Media and the Hong Kong Protests in The New Yorker, October 1, 2014
- ↑ a b c d [34] Lee, D. (2014). The role of social media in Occupy protests, on the ground and around the world in South China Morning Post, Thursday, 30 October 2014
- ↑ [35] Mozur, P. (2014). Protesters in Hong Kong Are Targets of Scrutiny Through Their Phones in The New York Times, October 1, 2014
- ↑ [36] FireChat Free instant messaging app For Android works without Internet
- ↑ a b [37] McKay, T. (2014). Here's the Ingenious Way Protesters in Hong Kong Are Organizing Themselves in World.Mic, September 30, 2014
- ↑ Rees, A. Digital and online activism. Retrieved March 11, 2016, from https://en.reset.org/knowledge/digital-and-online-activism
- ↑ Die Occupy-Bewegung. (2011). Retrieved March 11, 2016, from http://www.bpb.de/politik/wirtschaft/finanzmaerkte/135540/occupy-bewegung?p=all
- ↑ "Intellectual Roots of Wall St. Protest Lie in Academe — Movement's principles arise from scholarship on anarchy". The Chronicle of Higher Education. Archived from the original on April 7, 2014. Retrieved February 23, 2012.
- ↑ a b c d e f Dahlgren, Peter. (August 2013). The Political Web. doi:10.1057/9781137326386.
- ↑ Poteete, J. and Ostrom, E. (2010). Working Together: Collective Action, the Commons, and Multiple Methods in Practice. Princeton University Press.
- ↑ Shirky, C. (2011). Cognitive Surplus: How Technology Makes Consumers Into Collaborators, New York: Penguin
- ↑ Bloomberg Business. (2015). Facebook’s Use of Facial-Recognition Tool Draws Privacy Ire. 03/08, 2016, from http://www.bloomberg.com/news/articles/2015-07-28/facebook-s-use-of-facial-recognition-tool-draws-privacy-concerns
- ↑ Business Insider UK. (2015). Facebook's scarily accurate facial-recognition tech can now recognise you even if it can't see your face. Retrieved 03/08, 2016, from http://uk.businessinsider.com/facebook-facial-recognition-technology-ai-cant-see-face-2015-6?r=US&IR=T
- ↑ "'89% of British Internet users are worried about Privacy Online:Report'".
- ↑ "'How to keep companies from tracking you online - for good'".
- ↑ Richardson, Robert. "2008 CSI Crime and Computer Survey". http://i.cmpnet.com/v2.gocsi.com/pdf/CSIsurvey2008.pdf.
- ↑ "'HTTP State Management Mechanism - Overview'".
{{cite web}}: Unknown parameter|source=ignored (help) - ↑ McDonald, A. M., & Cranor, L. F. (2010, October). Americans' attitudes about internet behavioral advertising practices. In Proceedings of the 9th annual ACM workshop on Privacy in the electronic society (pp. 63-72). ACM.
- ↑ a b c d Turkle, S. (2011). Alone Together: Why We Expect More from Technology and Less from Each Other, pp.134-149. New York: Basic Books.
- ↑ a b Fuchs, C. Social media
- ↑ Fiegerman, Seth (2014). Instagram tops 300 million active users, likely bigger than Twitter. Mashable.
- ↑ Ferrara, E., Interdonato, R. and Tagarelli, A. (2014) Online popularity and topical interests through the lens of Instagram’, Proceedings of the 25th ACM conference on Hypertext and social media - HT 14, . doi: 10.1145/2631775.2631808.
- ↑ Toffler, A. (1960), Future Shock. United States: Random House.
- ↑ Hemp, Paul (2009) Death by Information Overload. Harvard Business Review. September Issue. Available at: https://hbr.org/2009/09/death-by-information-overload
- ↑ [38] IMBd. (n.d.). The Social Network (2010) Quotes. Retrieved 02/17, 2016, from http://www.imdb.com/title/tt1285016/quotes
- ↑ The Social Network. Fincher, D., (Director). (2010). [Motion Picture]. Columbia Pictures.
- ↑ [39], Anderson, E. (2015). Teenagers spend 27 hours a week online. The Telegraph. Retrieved 03/02, 2016, from http://www.telegraph.co.uk/finance/newsbysector/mediatechnologyandtelecoms/digital-media/11597743/Teenagers-spend-27-hours-a-week-online-how-internet-use-has-ballooned-in-the-last-decade.html
- ↑ [40] n.a. (2014). Data Retention and Investigatory Powers Act 2014. Retrieved 03/11, 2016, from http://www.legislation.gov.uk/ukpga/2014/27/pdfs/ukpga_20140027_en.pdf
- ↑ Morio, H. and Buchholz, C. (2009). How Anonymous are you Online? Examining online social behaviours from a cross-cultural perspective. Al & Society, 23, 297-307
- ↑ Luppicini, R. and Lin, X. (2012) ‘Student 2.0 Revisited: The Paradox of Anonymity and Identity in the Digital World’, in Luppicini, R. and Haghi, A.K. (eds.) Education for a digital world: Present Realities and Future Possibilities. Toronto: Apple Academic Press, pp. 185–196.
- ↑ Gauntlett, D. (2011) Making is connecting: The social meaning of creativity, from DIY and knitting to YouTube and web 2.0. Malden, MA: John Wiley & Sons.
- ↑ Gies, L. (2008) Law and the Media: The Future of an Uneasy Relationship. Oxson: Routledge-Cavendish
- ↑ J. Collins and H. Selina eds., Heidegger for Beginners (1998) p. 64-9
- ↑ Turkle, Sherry. (1996). "Who Am We? : We are moving from modernist calculation toward postmodernist simulation, where the self is a multiple, distributed system," Wired Magazine, Issue 4.01, January 1996.
- ↑ boyd, d. & Donath, J. (2004). Public Displays of Connection. Retrieved 03/10, 2016, from http://www.danah.org/papers/PublicDisplays.pdf
- ↑ Sooke, Alastair, (2016), Is this the first Instagram masterpiece?, The Telegraph, available at http://www.telegraph.co.uk/photography/what-to-see/is-this-the-first-instagram-masterpiece/
- ↑ Harris, Aisha (2013). "Catfish meaning and definition: term for online hoaxes has a surprisingly long history". Slate. Retrieved March 10, 2016.
- ↑ Suler, J. (2004). CyberPsychology & Behavior. July 2004, 7(3): 321-326. doi:10.1089/1094931041291295
- ↑ Spitzberg, B.H. and Hoobler, G. (2002) ‘Cyberstalking and the technologies of interpersonal terrorism’ in New Media & Society, 4(1), pp. 71–92. doi: 10.1177/14614440222226271.
- ↑ Li, Q. (2007) "New bottle but old wine: A research of cyberbullying in schools," Computers in Human Behavior (23), pp 1777–1791.
- ↑ http://link.springer.com/article/10.1007/s10964-012-9867-3
- ↑ Smith, P.K., and Slonje, R. (2008b) "Cyberbullying: Another main type of bullying?," Scandinavian Journal of Psychology:49
- ↑ Shariff, S., & Gouin, R. (2006), Cyber-dilemmas: Gendered hierarchies, new technologies and cybersafety in schools. Atlantis - A Women’s Studies Journal, 31 (1)
- ↑ Brescia, H. (2014, December 3). Analysis of policy regarding Cyberbullying. Retrieved March 9, 2016, from http://sites.duke.edu/cyberbullying/2014/12/03/who-what-where-and-why/
- ↑ Aricak, T., Siyahhan, S., et al., C. (2008) "Cyberbullying among Turkish Adolescents," Cyberpsychology & behavior (11:3)
- ↑ Herring, S.C., 2002, Annual review of information science, Chapter 3: Computer-Mediated Communication on the Internet
- ↑ Campbell, M. (2005) "Cyber bullying: An old problem in a new guise?" in Australian Journal of Guidance and Counselling (15:1), pp 68-76.
- ↑ LLC, V. M. (2015, March 9). There is a lack of research on the longterm effects of Cyberbullying. Retrieved March 10, 2016, from http://motherboard.vice.com/read/why-dont-we-have-real-science-on-cyberbullying
- ↑ boyd, danah. (2010, December 7). Digital Self-Harm and Other Acts of Self-Harassment. Retrieved March 10, 2016, from http://www.zephoria.org/thoughts/archives/2010/12/07/digital-self-harm-and-other-acts-of-self-harassment.html
- ↑ Elizabeth Englander, “Preliminary Report: Bullying and Cyberbullying in Massachusetts 2011-12” (presented at the Workshop: PCP Interventions, Freehold, NJ, 2011).
- ↑ Englander, E. (2012, June). DIGITAL SELF-‐ HARM: FREQUENCY, TYPE, MOTIVATIONS, AND OUTCOMES. Retrieved from http://webhost.bridgew.edu/marc/DIGITAL%20SELF%20HARM%20report.pdf
- ↑ Moore, Alexis A. "What is cyberstalking?". About.com. Retrieved 2016-03-11.
- ↑ Bishop, J. (2013). The effect of deindividuation of the Internet Troller on Criminal Procedure implementation: An interview with a Hater. International Journal of Cyber Criminology 7(1), pp. 28-48. Available at [41]
- ↑ Pittaro, M. L. (2011). Cyber stalking. In K . Jaishankar (Ed.), Cyber criminology (pp. 277-297). Retrieved from http://www.crcnetbase.com
- ↑ Quarmby, K. (2014, August 13). How the law is standing up to Cyberstalking in the magazine. . Retrieved from http://europe.newsweek.com/how-law-standing-cyberstalking-264251?rm=eu
- ↑ Riplee. (2012, April 6). Cyberstalking: Lurking in anonymity. Retrieved March 11, 2016, from http://ripleeforensicpsych.umwblogs.org/2012/04/06/cyberstalking-lurking-in-anonymity/
- ↑ Lipton, J. D. (2011). Combating cyber victimization. Berkeley Technology Law Journal, 26, 1103-1155.
- ↑ "UCF Cyber Stalker’s Sentence Not Harsh Enough, Victim Says"[42]. ABC News. January 23, 2012. Retrieved 2016-03-11.
- ↑ Kowalski, R. M., Limber, S., & Agatston, P. (2008). Cyber bullying: Bullying in the digital age. Malden, MA: Blackwell Publishers.
- ↑ "Alexis Pilkington Facebook Horror: Cyber Bullies Harass Teen Even After Suicide"[ http://www.huffingtonpost.com/2010/03/24/alexis-pilkington-faceboo_n_512482.html]. Huffingtonpost.com. 25 May 2011. Retrieved 2016-03-11.
- ↑ Cleaver, H. (1998). "The Zapatistas and the International Circulation of Struggle: Lessons Suggested and Problems Raised," Harry Cleaver homepage 1998. Retrieved 03/10, 2016, from http://www.eco.utexas.edu/faculty/Cleaver/lessons.html)
- ↑ Wray, S. (1998). "On Electronic Civil Disobedience," Peace, forthcoming; Electronic Civil Disobedience archive 1998. Retrieved 03/09, 2016, from http://www.nyu.edu/projects/wray/oecd.html)
- ↑ Betters, E. (2015, February 5). Sony pictures hack: Here’s everything we know about the massive attack so far. Retrieved March 9, 2016, from http://www.pocket-lint.com/news/131937-sony-pictures-hack-here-s-everything-we-know-about-the-massive-attack-so-far
- ↑ Mizrach, S. Old and new hacker ethics. Retrieved March 9, 2016, from http://www2.fiu.edu/~mizrachs/hackethic.html
- ↑ Wray, S. (2002). Electronic civil disobedience and the world wide web of Hacktivism. Retrieved March 9, 2016, from http://www.webpagefx.com/research/electronic-civil-disobedience-hacktivism.html
- ↑ Knufken, D. (2011, March 23). 5 anonymous campaigns against businesses. Retrieved March 11, 2016, from Business, http://www.businesspundit.com/5-anonymous-campaigns-against-businesses/
- ↑ Parmy Olson on anonymous: ‘A growing phenomenon that we Don’t yet understand’. (2012, June 8). Retrieved March 11, 2016, from http://www.rferl.org/content/parmy-olson-on-anonymous-a-growing-phenomenon-that-we-dont-yet-understand/24607895.html
- ↑ Kelly, B., B. (2012). INVESTING IN A CENTRALIZED CYBERSECURITY INFRASTRUCTURE: WHY ‘ HACKTIVISM ’ CAN AND SHOULD INFLUENCE CYBERSECURITY REFORM. Retrieved from http://www.bu.edu/law/journals-archive/bulr/volume92n4/documents/kelly.pdf
- ↑ Brown, Jesse (February 7, 2008). "Community Organization with Digital Tools: The face of Anonymous". MediaShift Idea Lab: Reinventing Community News for the Digital Age (PBS). Archived from the original on Feb 11, 2008. Retrieved March 11, 2016.
- ↑ Bever, Lindsey (August 13, 2014). "Amid Ferguson protests, hacker collective Anonymous wages cyberwar". The Washington Post. Retrieved March 11th, 2016.
- ↑ Hunn, David (August 13, 2014). "How computer hackers changed the Ferguson protests". St. Louis Post-Dispatch. Retrieved March 11th 2016
- ↑ Harkinson, Josh (August 13, 2014). "Anonymous' "Op Ferguson" Says It Will ID the Officer Who Killed Michael Brown". Mother Jones. Retrieved March 11th 2016
- ↑ Bosman, Julie; Shear, Michael D.; Williams, Timothy (August 14, 2014). "Obama Calls for Open Inquiry Into Police Shooting of Teenager in Ferguson, Mo". The New York Times. Retrieved March 11th, 2016.
- ↑ "Anonymous Releases Alleged Name Of Officer They Say Fatally Shot Michael Brown". KMOX News Radio 1120. August 14, 2014. Retrieved March 11th, 2016.
- ↑ Pagliery, Jose (August 14, 2014). "Ferguson police deny Anonymous' ID of alleged shooter". CNN Money. Retrieved March 11th, 2016.
- ↑ Hunn, David. "Twitter suspends Anonymous account : News". St. Louis Post-Dispatch. Retrieved March 11th, 2016.
- ↑ Jamie Bartlett. "Hacker, Hoaxer, Whistleblower, Spy: The Many Faces of Anonymous by Gabriella Coleman – review". the Guardian.
- ↑ Boycott GoDaddy. (2016) Godaddyboycott.org. Retrieved 11 March 2016, from http://godaddyboycott.org
- ↑ McCullagh, D. (2016). GoDaddy bows to boycott, now 'opposes' SOPA copyright bill. CNET. Retrieved 11 March 2016, from http://www.cnet.com/news/godaddy-bows-to-boycott-now-opposes-sopa-copyright-bill/
- ↑ Rheingold, H. (2003). Smart mobs. Cambridge, MA: Perseus Pub.
- ↑ News, A. (2012). Wikipedia Protests 'Internet Censorship'. ABC News. Retrieved 11 March 2016, from http://abcnews.go.com/blogs/technology/2012/01/sopa-blackout-wikipedia-google-wired-join-protest-against-internet-censorship/
- ↑ Waugh, R. (2012). U.S Senators withdraw support for anti-piracy bills as 4.5 million people sign Google's anti-censorship petition. Mail Online. Retrieved 11 March 2016, from http://www.dailymail.co.uk/sciencetech/article-2088860/SOPA-protest-4-5m-people-sign-Googles-anti-censorship-petition.html
- ↑ Mandiberg, M. (2012). The social media reader. New York: New York University Press.
- ↑ Wright, A, (2009). Exploring a ‘Deep Web’ That Google Can’t Grasp, Retrieved 03/10, 2016 from http://www.nytimes.com/2009/02/23/technology/internet/23search.html?th&emc=th&_r=0
- ↑ Flitter, E., (2013). "FBI shuts alleged online drug marketplace, Silk Road", Retrieved 3/10, 2016 from http://news.yahoo.com/fbi-raids-alleged-online-drug-market-silk-road-153729457.html
- ↑ Branston, G., & Stafford, R. (2010). The Media Student's Book (5th ed., p. 254). London: Goldsmiths.
- ↑ Athique, A. (2013). Digital media and society (p.517). Cambridge, England: Polity Press.
- ↑ Lacey, N. (2009). Image and Representation (2nd ed., pp. 6-7).
- ↑ Facebook Help center. (2016). Retrieved March 11, 2016, from https://www.facebook.com/help/166738576721085
- ↑ Pariser, E. (2011, May 2). Beware online ‘filter bubbles’. Retrieved March 11, 2016, from https://www.ted.com/talks/eli_pariser_beware_online_filter_bubbles?language=en
- ↑ Cavanagh, T. (2014, October, 17). The echo chamber is getting louder. [Web log post] Retrieved from http://www.huffingtonpost.com/the-university-of-central-florida-forum/the-echo-chamber-is-getti_b-5573734.html
- ↑ Festinger, L. (1957) A Theory of Cognitive Dissonance (California: Stanford University Press)
- ↑ a b http://nobullying.com/what-is-internet-trolling/
- ↑ https://www.psychologytoday.com/blog/better-living-technology/201408/why-the-online-trolls-troll
- ↑ a b [43], Habermas, J. (1991). The Structural Transformation of the Public Sphere: An Inquiry into a category of Bourgeois Society. 5th ed. USA:MIT Press Paperback. Retrieved 03/05, 2016, from http://pages.uoregon.edu/koopman/courses_readings/phil123-net/publicness/habermas_structural_trans_pub_sphere.pdf
- ↑ a b c d e [44], Dahlberg, L. (2004). The Habermasian Public Sphere: A Specification of the Idealized Conditions of Democratic Communication. Studies In Social And Political Thought, (10), 2-18. Retrieved from https://www.sussex.ac.uk/webteam/gateway/file.php?name=10-1a.pdf&site=412
- ↑ a b [45], Ubayasiri, K. (2006). Internet and the Public Sphere: A glimpse of YouTube. Ejournalist, 6(2). Retrieved from http://ejournalist.com.au/v6n2/ubayasiri622.pdf
- ↑ a b [46] Gerhards, J., & Schafer, M. (2010). Is the internet a better public sphere? Comparing old and new media in the USA and Germany. New Media & Society, 12(1), 143-160, Retrieved 5 March 2016, from http://nms.sagepub.com/content/12/1/143
- ↑ http://www.york.ac.uk/sociology/our-staff/academic/brian-loader/
- ↑ a b c d Loader,B Cyberspace Divide Equality, agency and policy in the information society 1998 (Published by Rotledge)
- ↑ a b c d e f g Loader,B 2007 Young Citizens in the digital age: political engagement, young people and new media(Published by Rotledge)
- ↑ [47], Garnham, N. (1990). Capitalism and Communication. Global Culture and the Economics of Information. London: Sage. Retrieved 03/07, 2016, from http://www.triple-c.at/index.php/tripleC/article/viewFile/553/534
- ↑ [48], Cccs.uq.edu.au,. (n.d.) Dr Lincoln Dahlberg - Centre for Critical and Cultural Studies - The University of Queensland, Australia. Retrieved 4 March 2016, from http://cccs.uq.edu.au/dahlberg
- ↑ a b [49], Dahlberg, L. (2001). Extending the public sphere through cyberspace: The case of Minnesota E-Democracy. First Monday, 6(3). http://dx.doi.org/10.5210/fm.v6i3.838
- ↑ http://study.com/academy/lesson/cultural-determinism-definition-and-theory.html
- ↑ a b Marshall McLuhan Understanding Media: The Extensions of Man (1964)
- ↑ http://www.telegraph.co.uk/news/health/news/12189376/How-teenage-pregnancy-collapsed-after-birth-of-social-media.html
- ↑ http://adage.com/article/digital/facebook-web-browsing-history-ad-targeting/293656/
- ↑ Papacharissi, Z. A., (2013). Private Sphere: Democracy in A Digital Age. Cambridge, Malden, MA: Polity Press.
- ↑ [50] Dichtionary.com. (2016). Public Opinion. Retrieved 03/10, 2016 from http://www.dictionary.com/browse/public-opinion