Structure of the Internet: Internet security
Internet Security
[edit | edit source]Firewall
[edit | edit source]A firewall is a network security application or device which is responsible for monitoring all incoming and outgoing network traffic. A firewall can be either physical hardware or a software application. Before the conception of firewall, there existed ACLs (Access controlled logics), which granted access to network traffic based on Specific IP addresses. To improve the control over network traffic not only by matching IP address firewalls were developed. Firewalls allow more granular control of data packets (Packet filtering) which is not only filters on the basis of source and destination IPs but also protocols, ports, etc.
Firewalls are improved over the course of time with the ability for the users to control the network traffic. The second-generation firewalls were able to determine the connection state of the packet which makes it more efficient as it keeps track of the state of the network connection traveling across it. So those filtering decisions would not only be based on predefined rules but also based on packet history in the state table.
The third generation firewalls have the ability to block any specific content, also recognize when certain protocols are being used (HTTP, FTP) Application layer firewalls are essentially hosts that run on proxy servers.
Type of firewalls
[edit | edit source]1. Host-Based firewalls - It is installed in each node, it comes as an application or a part of OS.
2. Network-Based firewalls - It functions on a network level, it filters all incoming and outgoing traffic across the network.
Packet Filtering
[edit | edit source]A packet-filtering firewall examines each packet that crosses the firewall and tests the packet according to a set of rules that you set up. If the packet passes the test, it’s allowed to pass. If the packet doesn’t pass, it’s rejected.
Packet filters are the least expensive type of firewall. As a result, packet-filtering firewalls are very common. However, packet filtering has a number of flaws that knowledgeable hackers can exploit. As a result, packet filtering by itself doesn’t make for a fully effective firewall.
Packet filters work by inspecting the source and destination IP and port addresses contained in each Transmission Control Protocol/Internet Protocol (TCP/IP) packet. TCP/IP ports are numbers that are assigned to specific services that help to identify for which service each packet is intended. For example, the port number for the HTTP protocol is 80. As a result, any incoming packets headed for an HTTP server will specify port 80 as the destination port. [1]
Proxy Server
[edit | edit source]A firewall proxy server essentially turns a two-party session into a four-party session, with the middle process emulating the two real hosts. Because they operate at the application layer, proxy servers are also referred to as application-layer firewalls. A proxy service must be run for each type of Internet application the firewall will support -- a Simple Mail Transport Protocol (SMTP) proxy for e-mail, an HTTP proxy for Web services and so on. Proxy servers are almost always one-way arrangements running from the internal network to the outside network. In other words, if an internal user wants to access a Web site on the Internet, the packets making up that request are processed through the HTTP server before being forwarded to the Web site. Packets returned from the Web site, in turn, are processed through the HTTP server before being forwarded back to the internal user host.
Because firewall proxy servers centralize all activity for an application into a single server, they present the ideal opportunity to perform a variety of useful functions. Having the application running right on the firewall presents the opportunity to inspect packets for much more than just source/destination addresses and port numbers. This is why nearly all modern firewalls incorporate some form of proxy-server architecture. For example, inbound packets headed to a server set up strictly to disburse information (say, an FTP server) can be inspected to see if they contain any write commands (such as the PUT command). In this way, the proxy server could allow only connections containing read commands.
Stateful Inspection
[edit | edit source]Encryption
[edit | edit source]Data encryption is the process of scrambling data so that it is difficult to understand and unscramble. The encrypted (secure) data is called the ciphertext whereas the unencrypted data is called the plaintext.
Symmetric
[edit | edit source]Symmetric encryption is also known as Private Key Encryption and uses the same key to encrypt and decrypt data. Therefore, the key must be transferred alongside the data. This causes obvious security problems as if the data is intercepted, it can easily be deciphered.
Asymmetric
[edit | edit source]Asymmetric encryption, also known as Public Key Encryption, uses two keys (public and private key). The public key is made available so that others wishing to send you data can encrypt it. However, the public key cannot decrypt data. Consequently, a private key is used to decrypt data. This key is only known by you to make it as secure as possible.
Key Exchange
[edit | edit source]Key exchange is when the key to an encrypted text is sent to the recipient. The most known type is through Symmetric encryption where key exchange takes place alongside the exchange of the encrypted data.
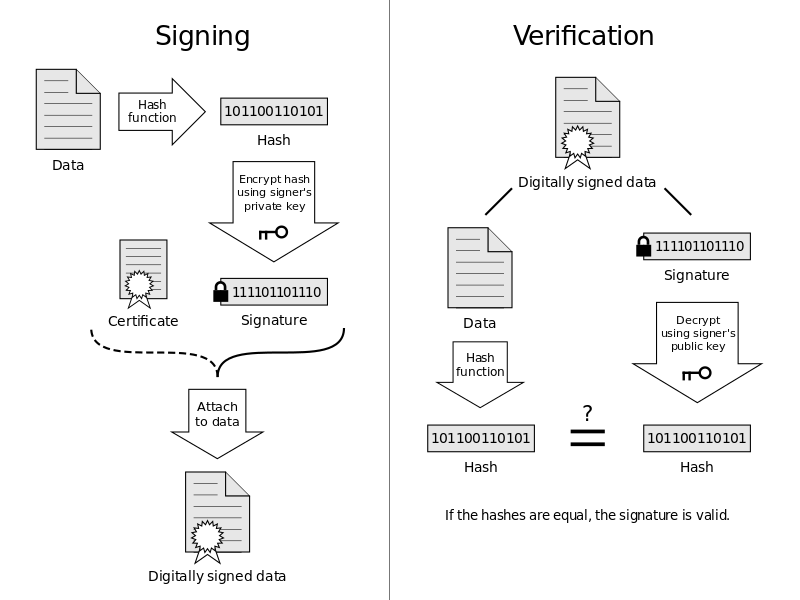
Digital Certificates and Signatures
[edit | edit source]Keys
[edit | edit source]Encryption is used to hide sensitive messages from illegitimate recipients by using encryption algorithms and an encryption key to convert plain text to cipher text, illegible to those without the encryption and decryption key. Private/Public key encryption is when both parties have a pair of keys, one private and one public. The Public Key is kept in the open freely usable by anyone as is the encryption algorithm, however the Private Key is kept hidden.
- A message encrypted with A's public key can only be decrypted with A's private key.
- A message encrypted with A's private key can only be decrypted with A's public key.
- A message encrypted with B's public key can only be decrypted with B's private key.
- A message encrypted with B's private key can only be decrypted with B's public key.
Sending messages securely
[edit | edit source]Digital signatures are a way for the sender to prove to the receiver that the message did in fact originate from them. A digital signature is obtained through the following process:
| Processes required before A sends the message to B | Processes required to ensure the message is from A |
|---|---|
| Message is hashed to get a message digest. | B decrypts the message with B's private key. |
| The message digest is encrypted with A's private key, this then becomes the signature. | B decrypts the signature with A's public key to get the original message digest. |
| The signature is appended to the message. | The decrypted message is hashed again, reproducing the message digest. |
| The message is encrypted using B's public key. | The message has not been tampered with if the decrypted message digest is the same as the reproduced digest. |
| The encrypted message is sent to B. |
A Digital Certificate is a way of proving that the public key of the sender is authentic. Digital Certificates are only issued by a certification authority (CA). The certificates are encrypted into the message via the CA's private key, and can only be decrypted with the CA's public key.
Security Threats
[edit | edit source]There are a number to be aware of:
Viruses
[edit | edit source]A virus is a small computer program attached to another program or file and is intended to cause harm to a computer. The first step that a computer performs when the program is executed is to copy itself onto the disk and hide itself. After being copied onto the disk the virus can reside in memory and reconfigure the system so it causes problems such as displaying unwanted messages, destroying or corrupting files or even wiping the entire hard disk. Viruses tend to replicate themselves and also try to spread to other computers. Anti-virus programs are used to detect and remove these viruses. Nowadays web browsers have built-in virus scanners which scan files that are available for download.
Worms
[edit | edit source]A worm is a malicious program designed to replicate itself in an attempt to spread across a computer network such as the internet. The most significant difference between a worm and a virus is that a worm is a complete program on its own. Worms can disrupt network traffic and damage data.
Spam
[edit | edit source]Spam is the flooding of irrelevant unwanted message (silly pointless annoying messages) these can either be by email, SMS or instant messaging. Email spam is usually considered junk mail and millions of spam emails are sent every day. Text messaging spam is also used by companies to advertise themselves. Spam is considered to be disruptive and a waste of network bandwidth.
Phishing
[edit | edit source]Phishing is the act of deceiving a user to give sensitive information about themselves. This may happen by the use of phishing emails or even phishing sites, these look like the site the user is trying to access but are not, they are intended to capture information from the user. The term phishing comes from fishing, where instead of catching fish, information is caught.
Pharming
[edit | edit source]Pharming is technique used to redirect traffic from one website to another, Phishing and Pharming are used in conjunction. Pharming is the process of redirecting users to a different location so that a phishing technique can imitate and capture information about the user.
Computer Security Procedures
[edit | edit source]Authentication, Authorisation, Accounting.
Authentication
[edit | edit source]Verification of the user of the computer system. Forms of Authentication include passwords, biometric data, security tokens and digital signatures.
Authorisation
[edit | edit source]Specifying the access rights of different users to resources on a network.
Accounting
[edit | edit source]Keeping logs of user activity on a network.