Introduction to Computer Information Systems/Security
Unauthorized Access and Control Systems[edit | edit source]

A Firewall is a type of security system that creates a wall that checks all incoming and outgoing messages to ensure only authorized traffic goes through. There are many different forms of this application such as Norton[1] and Windows Security Essentials.[2] Another way to protect your information is through encryption. Encryption basically scrambles and makes any message sent unreadable to anyone who does not have a key. The key is then used to decrypt the scrambled message into the original format. Whenever you go to a website that has an 'S' after the HTTP that means it is a secure web page, meaning the entire web page is encrypted. Therefore, people hacking to your web browser cannot get you credit card number or SSN. One question that arises is, "Can't you just make every website a secure web page?". The simple answer is money, a site owner needs to pay someone to encrypt the site. Then to send the data takes up more bandwidth, and slows down traffic in general. Cheaper web hosts may provide secure security features and backup services but have limitations. Another form of protection is a VPN (Virtual Private Network). A VPN creates a link between the user and some other destination. In order to access the VPN you will need a username and password, in order to keep it more secure and to block out hackers.

Firewalls can work in a number of ways, but a couple types of firewalls are more widely used over others. The two most common firewalls are packet-filtering and proxy.
Packet-Filtering Firewall
- Advantages
- A packet-filter simply examines each packet to determine whether it is safe or not. After examining a packet, the filter will either allow in or block out the packet depending on if it’s safe or not.
- Packet-filters are common among routers, switches, wireless access points, etc.
- Disadvantages
- A disadvantage of using a packet-filter firewall is that some packets that are safe may be blocked by accident. This means that it is possible that parts of information could be missing due to a packet being blocked.[3]
Proxy Firewall
- Advantages
- Most Secure - direct connections are limited by packets being sent from one computer to the proxy, and then mirrored over to the computer on the receiving end.
- More secure decisions are able to be made in application settings through strong analysis.
- Disadvantages
- A disadvantage of a proxy firewall is that it can slow down the transfer speed of packets.
- While using a proxy firewall it is difficult for someone to figure out the location of where packets were sent from.[4]
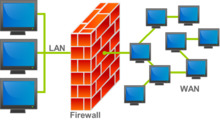
The Internet was created as an open system for the free exchange of information. Due to the openness of an ideology, the Internet provides to “bad guys” the significantly greater opportunities for the penetration into information systems. Firewalls make it possible to filter incoming and outgoing traffic that flows through your system. The Firewall uses one or more sets of rules to check the network packets as they enter or exit through a network connection. Firewalls can be used to protect individual hosts or to protect an entire network; it may be built-in into the Operation System or installed separately. The network Firewalls are the more complicated systems, combined hardware and software. There is no universally accepted classification of firewalls. But according to the methods of deploying it is possible to identify three following types of them.
- A filtering router is a router or server running on a program that is configured to filter incoming and outgoing packets. The filtering of packets is done on the basis of the information contained in TCP and IP packet headers.
- Firewalls based on session layer gateways. This type of router is a repeater for TCP connections. The gateway receives specific service requests from authorized clients and establishes a connection to the destination after verifying the requested session.
- Firewalls based on application layer gateways. To protect against some of the vulnerabilities inherent in filtering routers, the firewall should be used by applications to filter connections to services, such as Telnet and FTP. Such applications are called proxy services. Such gateways eliminate direct interaction between the client and authorized external hosts. The gateway filters all incoming and outgoing packets at the application layer. Application layer gateways facilitate protection; because interaction with the outside world is achieved through a small number of authorized applications that have complete control over all incoming and outgoing traffic. Note that application layer gateways require separate applications for each network service. These categories can be thought of as the basic components of a true firewall. However, these components reflect the key features that distinguish a firewall.

Biometric Access Systems identify an individual based on their fingerprint, iris, or facial features or other unique physiological characteristic. Keystroke Dynamics recognize an individual's personal typing pattern to authenticate the user as he/she types a username or password. Fingerprint readers and retinal scanners isolate an unchangeable property in an individual in order to identify them and offer high security based on these measures. They are typically used to control access to high risk facilities such as government property, prisons, and corporate headquarters. Fingerprint scanners have also been equipped into laptops in order to offer a higher standard of protection in securing personal files. In the same way, a person can download face recognition software onto their laptop as well. Because biometrics are entirely unique to the user, they are extremely accurate. In the same way no two people will have the same fingerprint, a persons facial features and iris' are as equally unique. In fac the odds of two person with same features is about 1 in 10^78 power.[5]
See [Wikipedia:Firewall (Networking)]

Identification Systems are a type of Access Control System that reassures whoever wants to access your system has authorization. It is a great tool to ensure the safety and privacy of users and are useful for everyday computers and accounts, business accounts, and much more.[6]
Possessed Knowledge Access Systems use passwords based on information only the user should know. Downsides to this system would be the ability to forget this information or for it to be found out by someone who should not know.
Cognitive Authentication Systems require users to think of their answers to certain personal questions such as their first pet, where they were born, where they have been on vacation, etc. The disadvantages to this system are the same as Possessed Knowledge Access Systems; with a lapse of time a person is more likely to forget their answer to a security question, especially if it had multiple answers.
Possessed Object Access Systems are a way to identify you with a physical object such as a keycard or badge.
Access Control Systems link up to different types of readers that have the ability to hold data and retrieve it when needed. Some may even have function buttons that let them collect different data used for timing and attendance purposes.

Many WI-FI connections are unfortunately left unsecured. This allows for any individual with a WI-FI compatible device to potentially piggy back the network. Once an individual is connected to a network, most devices connected to that network become available for a skilled hacker to view. This leaves an opening for many possible risks, especially if that network has a high traffic of sensitive information or data.[7] Some war driving software exists which allows a user, usually with a portable device, to identify many unsecured networks in a short amount of time. This gives a hacker to identify a large number of potential targets. Cyber-Crime has become increasingly prevalent over the years. Hackers are notorious for the various crimes they commit. Using malicious software, a skilled hacker is capable of stealing credit card numbers, bank account numbers, and other personal information, some of which make it possible for them to even steal identities. Using a program such as a keylogger, a hacker can monitor keystrokes without the individual knowing, allowing them to acquire sensitive information such as a credit card number, social security number, bank account, or password. A skilled hacker with an understanding of web design can create a phishing website and acquire account information from unsuspecting website visitors.[8]
Public Hotspot Safety[edit | edit source]

Public hotspots are public networks, usually found within buildings such as restaurants, airports, and hospitals that allow a free or fee-based wi-fi connection to nearby users. Because these hotspots are public, it is beneficial to take certain precautionary measures when using them. Some of these safety measure include, disabling your computer automatic wi-fi connection feature. Many modern computers will automatically connect to any available wi-fi networks and it is important to be aware of this. Also, using a firewall can protect connections from working in the opposite direction. Instead of your computer connecting to the wi-fi, there is a chance that other softwares or devices that are perhaps malicious will try to access your computer through the network. Also, you should avoid viewing or inputting personal information while using a public hotspot. Avoid online shopping which requires a credit card as well as using passwords which can link to sensitive accounts. If you are viewing and inputting personal information then try using a virtual private network through the public hotspot which will avoid others from accessing your data. Other precautions include turning off file sharing, using antivirus software, and watching to see if others are trying to look at your computer screen within the public area.[9]
Computer Sabotage[edit | edit source]
Malware[edit | edit source]

Malware is a term for unwanted software that gets installed on a user’s computer and performs malicious tasks. It can be as simple as pop-up windows containing advertising, otherwise known as Adware, or it can cause significant damage in the form of a Virus. A Virus is a program that can replicate itself and spread to other computers by inserting its own code, wreaking havoc along the way. There are different types of computer viruses that can cause different kinds of damages to a computer. Another form of Malware is Spyware. Spyware can track a computer user’s web browsing habits, obtain private information, and transmit that information to advertisers without the user’s knowledge.
Unfortunately, without adequate protection, it is rather easy for a user to inadvertently allow malware installation. It can be as simple as clicking the wrong box in a pop-up window on a website. Protection from malware is available through various security software programs. When first purchasing a computer, it may have security programs already. Often times, if a computer is already infected, it can block anti-malware apps. One of the benefits of Malwarebytes is that it can be installed even a PC already has malicious programs on it.
Botnets and Computer Viruses[edit | edit source]

A botnet is a large group of computers that are ran on multiple bots that have been taken over; botnets are a serious threat to computer users because of their devious ways of taking over computers. At the time, computer owners did not know their computers were being altered. Botnets are commonly used for DDoS attacks, click-fraud, phishing campaigns, key logging, and host malicious web sites. There are warning signs a computer user should be aware of if he or she's computer is apart of a botnet. For example, the computer will be extremely slow, one will receive emails accusing he or she of spam, and the computer user will have email messages in his or her's outbox that was never sent. botnets can be controlled by using command and control software.[10] Also, a malware is any type of deleterious software. A computer virus is a common type of malware that ruins computers. A virus can attach itself to programs so when the program runs, the virus will also run. There are many harmful effects that could come with a computer virus. For example, a virus could delete important data, send out fake emails, and could possibly delete the information that contains on the hard drive. If a computer does becomes infected, you are able to remove it with antivirus softwares. It is not impossible to remove viruses, but it is beneficial to have the software before the problem occurs.[11]


Although computer viruses in the past were sometimes designed to create confusion and mischief, more recent viruses have been designed to inflict much more serious damage. The perpetrators of creating such viruses are more often working for foreign governments or intelligence agencies. In recent years there have been several viruses that have become well known due to the large amount of damage they caused. One such virus was called Conficker Virus and affected Windows-based Pc’s in 2009. This worm crawled through millions of computers which created an immense botnet that was able to steal financial information and data. The virus is still affecting computers today. Another well known virus was called agent.btz and occurred in 2008. This virus spread through infected thumb drives and was found on Pentagon computers. It was believed to be the work of foreign spies, and lead to the creation of U.S. Cyber Command, an agency created to battle cyber war. PoisonIvy, another computer virus launched in 2005, allowed the attacker to control the infected user’s computer. This malware is known as remote access Trojan. It allows the hacker complete control of a computer. Once control is gained, the hacker could manipulate files and even get access to the computers speaker and webcam. PoisonIvy affected both defense and chemical industries in the West. Computer viruses are a serious threat. With the world relying on computers for everything from personal use to national defense, it is vital that computers be safeguarded against viruses. The next section goes on to describe security software.[12]
Data, Program or Website Alteration[edit | edit source]

Alteration attacks could take many different forms and occur when someone makes unauthorized modifications to code or data, attacking its integrity.[13] Alteration attacks have a range of consequences such as altering, destroying, suppressing, or stealing output, usually to conceal unauthorized transactions.[14] For example, students are changing grades, employees are altering or deleting corporate data as well as hackers changing social networking accounts and posting statuses on victim’s behalf. Many politicians like French President Nicolas Sarkozy whose Facebook page was hacked in 2011[15] are under website alteration attack. Alteration attacks can happen to anyone even the Government. In 1996 U.S. Central Intelligent Agency’s website was altered by Swedish hacker and in 1998 ;) The New York Times’ website was hacked.[16] Although people may feel helpless against these attacks, victims of sabotage have the law on their side. A person who knowingly, willfully and without authorization creates, alters or deletes any data, information, image, program, signal or sound contained in any computer, system or network which, if done on a written or printed document or instrument is guilty of forgery.[17] In 2012, the IC3 (receives, develops, and refers criminal complaints of cybercrime) received and processed 289,874 complaints, averaging more than 24,000 complaints per month. Also, unverified losses reported to IC3 rose 8.3 percent over the previous year.[18]
Security Software[edit | edit source]
Security software (also called as antivirus) is a program that runs alongside other programs on a computer to try and prevent viruses from penetrating into the system. If security software does not prevent the virus with its defensive properties, then it can detect a virus and detect the user. Most viruses can be removed by security software, but if there is one that cannot be removed, the software will “corner” the virus so that it cannot ruin any other areas in the computer system. Viruses are a big problem for every computer that uses the internet, no matter what type of activity is done on the internet. Viruses can be used for theft, corruption of data, destruction of data, or system failure. Operating systems nowadays have built-in antivirus software such as Windows Antivirus. It is a great feature for those who don't want to spend money on protection, in fact, for most people the basic antivirus software that comes with the operating system is all they need.
Online Theft and Fraud[edit | edit source]
Identity Theft[edit | edit source]


Identity theft is when someone steals others identity in order to gain access to their bank accounts and possibly rent apartments or take out loans in that persons name. They then use their credit cards to make purchases. It usually begins when someone gets the name, address, and social security of someone from thrown a discarded document, usually mail. They can also get people’s information form the Internet. Identity theft is typically grouped into two subcategories. One is true name identity theft and that is when the thief uses another person’s information to open new accounts. The other kind is account takeover, which is when the thief uses someone else’s personal information to gain access to their existing accounts.[19] There are different techniques such as skimming and social engineering.
- Skimming is when the thief uses a device that reads and stores credit and debit card numbers and stores them for later retrieval by the thief.
- Social engineering is when you pretend to work at a place (say at a telecommunication company or bank) and ask people for their information.[20]
- Thieves rummage through garbage, trash in business, public dumps to get what they are looking which is someone’s personal information.
Some good indicators that your account identity has been stolen are if there are withdrawals that you can’t explain, not getting bills in the mail, refused checks, IRS contacting you, bills received that you are not aware of, and if your health plan will not cover you. All of these are big indicators that your identity has been stolen. It is important to be aware of bank transactions to be cautious of these thieves. There are certain types of Identity theft as well. Tax related would be one of them. If a Social Security number is stolen that can be used to get a tax refund or job. If you get paid by someone you do not know or find more than one tax return those would be big indicators that someone stole from you. Contacting the right people immediately would be the first thing to do in any situation dealing with identity theft. The IRS can help if a Social Security number has been stolen and they can protect the account. Children can also have their Social Security number stolen so it is important to keep that information private and on file.[21]
Phishing[edit | edit source]
Scammers use email or text messages to trick you into giving them your personal information. They may try to steal your passwords, account numbers, or Social Security numbers. If they get that information, they could gain access to your email, bank, or other accounts. Scammers launch thousands of phishing attacks like these every day—and they’re often successful. The FBI’s Internet Crime Complaint Center reported that people lost $30 million to phishing schemes in one year. But there are several things you can do to protect yourself. Scammers often update their tactics, but there are some signs that will help you recognize a phishing email or text message. Phishing emails and text messages may look like they’re from a company you know or trust. They may look like they’re from a bank, a credit card company, a social networking site, an online payment website or app, or an online store. Phishing emails and text messages often tell a story to trick you into clicking on a link or opening an attachment. They may
• say they’ve noticed some suspicious activity or log-in attempts
• claim there’s a problem with your account or your payment information
• say you must confirm some personal information
• include a fake invoice
• want you to click on a link to make a payment
• say you’re eligible to register for a government refund
• offer a coupon for free stuff
If you get an email or a text message that asks you to click on a link or open an attachment, answer this question:
Do I have an account with the company or know the person that contacted me?
If the answer is “No,” it could be a phishing scam. If you see them, report the message and then delete it.
If the answer is “Yes,” contact the company using a phone number or website you know is real. Not the information in the email. Attachments and links can install harmful malware.
If you think a scammer has your information, like your Social Security, credit card, or bank account number, go to IdentityTheft.gov. There you’ll see the specific steps to take based on the information that you lost. If you think you clicked on a link or opened an attachment that downloaded harmful software, update your computer’s security software. Then run a scan.
If you got a phishing email or text message, report it. The information you give can help fight the scammers.
Step 1. If you got a phishing email, forward it to the FTC at spam@uce.gov and to the Anti-Phishing Working Group at reportphishing@apwg.org. If you got a phishing text message, forward it to SPAM (7726).
Step 2. Report the phishing attack to the FTC at ftc.gov/complaint.
Pharming, Drive-by Pharming, and Online Auction Fraud[edit | edit source]
Many people today are victims of identity theft. Another type of fraud or scam is called Pharming. Pharming is usually a fraudulent domain name intended to redirect a website’s traffic to another “trick” website. Pharming can be conducted either by changing the hosts file on a victim’s computer, or by the exploitation of a vulnerability in DNS server software.[23] Sometimes this happens via email. The hacker gets ahold of the user’s email address and sends the code or website to the specific user. Once the user receives and opens the email, the hacker can receive the user’s information. Pharming usually happens most often with DNS servers at a company with a common and well-known Web site. The hacker can change IP addresses intended for the company URL. Then the company URL is routed to the “poisoned” URL, which then takes over the Web server. This method of pharming is useful to the hacker because the “poisoned” Web site is usually made to look exactly like the company Web site. Once the user logs in, the hacker captures the username and password for the first time. The user receives a login message error and is then returned to the original company Web site.
Drive-by Pharming is a little more recent. This method is used by logging into the user’s personal routers by using a common password that a script within a website can run. When it is accessed, the information on the router can be modified to suite the hacker.[24]
Online auction fraud happens when a payment online goes to the seller, but the item is never delivered. For instance, if a buyer wants to make a bid online and buy tickets to a show or a concert, the buyer pays the seller for the tickets, and the seller never sends them. Many people are scammed each year and need to be careful with who they are trusting over the Internet.
Ransomware[edit | edit source]
Ransomware are programs that are designed to encrypt a user's PC and demand payment for the access of the files. Often these come into the user's PC through means described earlier in this article. The user will be forced to pay the ransom demanded by the program author (generally) though a virtual currency like Bitcoin which makes it hard for police to track the criminal.
Unfortunately, in this case, there is little hope of recovery; many ransomwares do not release free decryption programs. Bleeping Computer is the best place to go for help if you have been infected by one.
The problem is especially acute for corporates: many have paid over $50,000 to restore vital information affected by the ransomware.[25] The best way to protect against ransomwares is to take frequent backups; that way, if you do get infected, you can easily restore from your backups.
Protecting Against Online Theft and Fraud[edit | edit source]
Protecting Against Identity Theft[edit | edit source]
Just as the Internet is always evolving for good, there are also constantly scheming e-criminals hoping to take advantage of those who aren't careful with their online identities. Identity Theft is one of the scariest things that can happen to a person, especially if they don't have a strong friend or family base to help convince the proper authorities of their true identity. There is not one universal way to protect yourself from identity theft; instead, there are a number of steps you should take to keep yourself fully protected. The first thing you can do is be responsible with your bank accounts and credit cards. If you're checking your balance every day, you will be quick to see if there are any suspicious discrepancies occurring. It is essential to download your bank's mobile application, so you can get alerts on all of your transactions. [26] The next important step to protect against identity theft seems simple but can be easily overlooked: do not give out your personal information on the internet. This includes phone numbers, addresses, or anything else that hackers could potentially trace back to something you hold valuable. Some individuals can be targeted by thieves through fake emails and text messages who urge them to give up their information. You can protect yourself from identity theft is being wary of your mail. It is very easy for an e-criminal to send you a destructive link in an email that looks like it came from one of your friends, where one small click will lead you into a world of pain. Just follow these few rules and you will be doing fine online. One of the most easiest ways to protect yourself is to create a long, strong password. Creating a difficult password will prevent thieves from hacking into your personal information.
Avoiding Phishing E-mails[edit | edit source]
Due to the advantage taken of today’s improving technology, phishing has emerged as one of the most damaging forms of identity theft. Using very convincing and persistent language, e-criminals are able to trick millions of users into revealing confidential information over the Internet. As mentioned earlier, to lure people in to clicking an attached link, e-criminals tend to steal the identity of a legitimate and well-known company to write a very “important-sounding” e-mail, solely for the purpose of tricking the reader into thinking the contents of the e-mail really are significant. Nonetheless, however urgent the e-mail may seem, it is actually designed to steal your money! A typical phishing e-mail will usually consist of: spelling errors, links, threats to make the content seem urgent, and a popular company name to sound reliable. If examined carefully, some phishing expeditions may be fairly easy to spot, due to the poor spelling and grammar used, making it obvious that the message is not from a legitimate company. The link in the e-mail is used by the cybercriminals to install malicious software on your computer, ultimately enabling them to steal personal and sensitive information off of your computer. The e-mail could also even ask you to provide personal information, such as your bank account number, credit card number, or your Social Security Number; this should automatically be a red flag for the recipients because an authentic business would never request such information in any way other than in person. Therefore, if one is alert and careful about the content they receive in an e-mail, they can ultimately help protect their identity and their money, even if the e-mail seemed rather urgent.

The act of a phisher setting up a Web site that appears to look like the legitimate business is an act called Web site spoofing. Phishing emails can be sent to a wide group of people or can be personalized and sent to one person. This more targeted trend of phishing is called spear phishing because it targets a specific individual. A phisher may gather personal information from a networking site and send an email to a particular individual in order to convince the recipient that personal login information or account information is needed. Phishers may also do something that is called typosquatting, which is setting up spoofed Websites with addresses slightly different from legitimate sites in the hopes that a user would supply login information via the spoofed site when they arrive. Another form of online threats include pharming. Pharming is another type of scam that uses spoofing. With pharming, the criminal reroutes traffic intended for a commonly used Web site to a spoofed Web site set up by the pharmer. The pharmer makes changes to the DNS server. The DNS server is the computer that translates URLs in to the needed IP addresses to display the Web page corresponding to a URL. A pharmer will usually target company DNS servers. Lastly, online action fraud can also be a concern for Internet users. This threat occurs when an online auction buyer pays for merchandise that never is delivered.[27] [28]
Digital Certificates[edit | edit source]

One way of protecting yourself from online thefts or frauds is by looking for a digital certificate when browsing the Web or looking through e-mails. A digital certificate is granted by Certificate Authorities, which prove to the person that the website they are accessing is secure. A digital certificate binds the owner of a website to a specific pair of electronic keys, one being public and the other private. This allows the owner of the certificate to encrypt their files and e-mails and provides the user with the knowledge that their actually is an owner to the website that they are on. A digital certificate tracks who sends an email and who receives an email. This can protect users from giving away their credit card numbers to unprotected websites that try to scam people of their money. A digital certificate can either be an SSL or EV (Extended Version) SSL. The SSL digital certificate is the ordinary certificate that still requires an application and verification process while the EV SSL requires a more in-depth verification process. For users, an EV SSL digital certificate indicates that it is more secure than just an SSL digital certificate, while both of them are considered to be safe. This can be represented by the fact that when you enter an EV SSL webpage, the address bar turns green and for an SSL webpage it doesn’t change color at all. A digital certificate, in general, is definitely a good security advisor for users on the Internet.[29]
The Safety of Using PayPal[edit | edit source]

Internet users have to be very cautious of the information they put on the internet. PayPal seems to be a popular e-commerce business that many people use and willing give their private information to. Is this payment processor to be trusted? PayPal makes the lives of everyday internet consumers much easier. Its secure server stores your credit card information so payment over the internet is more efficient. Not much effort has to be put in by the individuals that use this payment processor. Other accounts require a vast amount of paper work to be signed beforehand.[30] One drawback to using PayPal is that there is a long list of rules the users must abide by, and if a user breaks any of these rules their money could be locked for up to six months while under investigation. An interesting feature that was added to PayPal in 2006 was an additional security option. Instead of only entering a login id and password, PayPal users can choose to type a six-digit number code in as well. This lowers the risk of malware bots trying to hack into the account. There is a fee associated with this added security measure. Users might be discouraged to protect their accounts because of this additional fee. They should still take caution when it comes to entering personal information into PayPal. Users should also be cautious when placing orders online using PayPal because they're at a greater risk for their credit card information to be stolen.
The Safety of Digitally Storing Cards[edit | edit source]

New forms of paying have appeared or rather a new way of paying thanks to companies like Google and Apple. Apple Pay and Android Pay are ways of paying wherein the user puts their credit cards or debit cards into their phones and can then use their phones or smartwatches to use their credit cards instead of bringing the physical cards with them. You can also use in app purchases by using your fingerprint on the latest Apple phone. With the phone’s it uses biometrics to make sure the owner is using Apple Pay and with smartwatches they use passcodes. But the real question is this new way of paying secure? Apple claims that it is so. In fact, they claim that it is actually more secure and that they will never upload the details on your cards to their servers. In fact, if your smartphone or smartwatch was ever stolen, you have the ability to revoke the information on your smartphone or smartwatch. Also Apple creates a Unique Device Account Number in order to protect your purchases when making transactions. However, there are those who do believe that this may not be safe. The best way to not have to deal with the risk is to not use Apple Pay. There are also applications like Snapchat and Venmo in which you can send money using your credit card information. This is a fast way to receive money but can be risky. A thief can login to your account and steal your information. All in all, it is not safe to store any personal information [31]
Basic Home Network Security[edit | edit source]

Many people have wireless networks in their homes, but they may not necessarily keep these networks as safe as they can or should. If somebody else accesses your network without your knowledge or consent, then they may do things on that network that you do not desire, they can use up your allotted data usage, and, most concerning, they may be able to get your personal information. Therefore, people with wireless home networks should take precautions to keep them secure. First, networks should always have some sort of a password to keep them safe; a network should never, ever be left unsecured, because then absolutely anybody within range can go on it. Typing any password at all is better than nothing, since it'll deter people from mooching, but—as is always the case—it is not wise to go with a predictable password such as the network name, 'password', 'Internet', etc. Something that is meaningless on the surface level but has a deeper meaning for you is a better way to go; for example, the first letters of words in an individual phrase that only you will remember. Also, to add yet another layer of security, you can make it so that your network is not available to other users by default but instead they must know the network name; this way, for a hacker to gain access, they would have to guess both the ID of the network and the password, which is highly unlikely. With these incredibly simple steps, one can make their network incredibly secure compared to one that has absolutely no measures preventing access from anybody within a certain physical proximity.[32]
Personal Safety[edit | edit source]
Cyber-bullying[edit | edit source]
This is a new way of bullying especially for the amount of social networks and how it has influenced our society today. Unfortunately, it happens 24 hours of the day and anything can be posted or distributed anonymously in which it could be difficult to track where the bullying is coming from. And as everyone is informed these days, once something is on the internet, there is no way to permanently delete the comment after it has been sent. It happens when individuals are bullied through electronic technology. For example, you can cyber bully over text message, emails, rumors send through any type of social networks. There’s no way to prevent an individual from making a comment that could be known as the start of cyber bullying, but simply ignoring or reporting the comment to either a parent, friend or any type of guidance person could benefit you most in not having the bullying continue. To elaborate, you can simply block the individual that had started the commenting and keep any type of evidence of the bullying for future documents in case it gets worse. A last important note is to recognize the signs of attitudes if a student were to be cyber bullied; some reactions are abusing drugs and alcohol, skip school, receive poor grades and have lower self-esteem.[33]
Activity: Delete Cyberbullying - Preventing Cyberbullying
Cyberstalking[edit | edit source]

Cyberstalking is the use of the internet, email, or other electronic communications to stalk another person. This occurs when there is a continuous pattern of malicious or threatening activity from an individual. Cyberstalking is considered the most dangerous form of harassment over the internet and is punishable by law. Depending on the state, punishments can range from misdemeanors to felonies.[34] Victims of cyberstalking can be targeted by strangers online who find personal information somewhere on the web or by more personal colleagues or individuals who know the person they are targeting well. Unfortunately, cyberstalking can move beyond the computer and become a problem in the real world if the stalker discovers or knows how to find the individual personally. This is a very serious issue and should be brought to law enforcement agencies or even the FBI. It is important to not give away any personal information that can be used to stalk you and to ensure that you trust anyone or anywhere that you may be giving personal information to online. The best solution to stop cyberstalking is to not respond at all or to change the information on what ever resource the cyber stalker is using to harass you.[35]
Online Pornography[edit | edit source]

Along with the lifespan and constant evolution of the Internet came the controversial issue of online pornography. Though pornography has unfortunately been around on paper for centuries, electronic access has made it much easier, quicker, and more convenient for any individual to get ahold of it at any given time. With this online access comes a much bigger and more controversial issue. It has introduced people, especially children, to new and substantial safety issues.
Though child pornography is banned and illegal, there is a considerable amount of it being circulated and passed throughout the Internet. With the link that has been made between this horrible content and child molestation, it is reasonable to be concerned about the spike that this will bring. Not only does it encourage sick people to do horrible things, but the computer also gives them an outlet to meet and dishonestly introduce themselves to children. It is unfortunate that today we have to be concerned about what could come from our children talking to people on the Internet; however, it is important that we voice these risks and make sure that parents take every precaution possible to keep their children from ever experiencing these horrific possibilities. [36]
Protecting Against Cyberbullying, Cyberstalking, and Other Personal Safety Concerns[edit | edit source]
Safety Tips for Adults[edit | edit source]
While it may seem unnecessary to state, the Internet is accessed by not only those with good intentions but also those who can pose a threat in a variety of ways. It is important to be aware of this fact because it is quite easy to forget how vast of an entity the Internet is and countless masses who use it daily. This makes for the task of safeguarding information from those who mean harm an important responsibility. Some of the ways one can prevent cyberbullying, cyberstalking and other issues are by using names that are gender-neutral. This hides the identity of the user, and this is important for female users because unfortunately they are more likely to be targets compared to male users.[37] Also, one should not give phone numbers, addresses and other personal information to strangers for obvious reasons. A way to prevent cyber bullying is to not be a cyber bully yourself. Bullying people online is not only unethical but it will increase the number of users targeting you.
Safety Tips for Children and Teens[edit | edit source]
Monitoring how children and teenagers use the Internet through the computer, smartphone, game console, etc. is the most important step in protecting them. It is recommended to place certain restrictions on how they use the Internet so that they do not access certain sites that might make them more susceptible to dangerous individuals or certain sites (e.g. adult sites). There are certain softwares parents can download to monitor what their children are doing online. There are also softwares to block inappropriate websites which is more common to find in children's schools. It is also important for older teens to understand the potential ramifications, including not only personal but also legal issues, that can arise from sending explicit messages or pictures via text messaging. Although teenagers may think that they have deleted text message or a picture, someone can still obtain the image.
Using Your Computer In A Safe Way[edit | edit source]
One of the best ways to stay safe online is to make sure you have your computers operating system and antivirus / anti-malware software update and set scanning schedules however the most important part of protection is user awareness. A recent blog post from Antivirus Talk details a list of good computer rules. Remember the majority of the time the user has allowed a virus onto the system. [38]
- Always run antivirus software (at least the built-in Windows Defender)
- Don’t go To Websites You don’t Know
- Don’t open Emails if you don’t know where they are from
- Use A different password for everything
- Keep your system up-to-date
- Don’t install unknown programs
- Don't send/give out your passwords
- Lock your computer when you are not by it in a public area
- Don't leave your computer in your car or lying around
By just following these rules you have the best chance of a safe journey online.
Network and Internet Security Legislation[edit | edit source]

New legislation is frequently introduced to address new types of computer crimes. Unfortunately, it's difficult to keep pace with the rate at which the technology changes. Along with this, there are both domestic and international jurisdictional issues because many computer crimes affect people in geographical areas other than one in which the computer criminal is located. Regardless, computer crime legislation continues to be proposed and computer crimes are being prosecuted. Some of the most important and impactful laws follow: Computer Fraud and Abuse Act of 1984- Makes it a crime to break into computers owned by the federal government. Identity Theft and Assumption Deterrence Act of 1998- Makes it a federal crime to knowingly use someone else's means of identification, Social Security number, or credit card, to commit any unlawful activity. Homeland Security Act(2002)- Includes provisions to combat cyberterrorism. One of the most famous cases of a cyber crime happened quite recently, the criminals charged in 2013. Five cyber criminals were responsible for a hack that targeted companies more than $300 million. They did this by stealing usernames and passwords, personal identification information, credit card and debit card numbers through secure computer networks. The criminals were sentenced up to 20 years in prison, depending on the amount stolen and involvement with the hacking group.[39]
Review[edit | edit source]
Important Terms[edit | edit source]
- antivirus software:[40]Software used to detect and eliminate computer viruses and other types of malware.
- biometric access system: An access control system that uses one unique physical characteristic of an individual (such as a fingerprint, face, or voice) to authenticate that individual.
- bot: A program/service that does tasks which would be tedious to do do manually. However, it can also be used for criminal activities, like for DDoS purposes.
- botnet: A group of bots that are controlled by one individual.
- computer crime: Any illegal act involving a computer.
- computer sabotage: An act of malicious destruction to a computer or computer resource.
- computer virus: A software program installed without the user’s knowledge and designed to alter the way a computer operates or to cause harm to the computer system.
- computer worm: A malicious program designed to spread rapidly to a large number of computers by sending copies of itself to other computers.
- cyberbullying: Children or teenagers bullying other children or teenagers via the Internet.
- cyberstalking: Repeated threats or harassing behavior between adults carried out via e-mail or another Internet communications method.
- denial of service (DDoS) attack: An act of sabotage that attempts to flood a network server or a Web server with so much activity that it is unable to function.
- digital certificate: A group of electronic data that can be used to verify the identity of a person or organization; includes a key pair that can be used for encryption and digital signatures.
- digital signature: A unique digital code that can be attached to a file or an e-mail message to verify the identity of the sender and guarantee the file or message has not been changed since it was signed.
- dot con: A fraud or scam carried out through the Internet.
- encryption: A method of scrambling the contents of an e-mail message or a file to make it unreadable if an unauthorized user intercepts it.
- firewall: A collection of hardware and/or software intended to protect a computer or computer network from unauthorized access.
- hacking: Using a computer to break into another computer system. (I bet you need this for class.)
- identity theft: Using someone else’s identity to purchase goods or services, obtain new credit cards or bank loans, or otherwise illegally masquerade as that individual.
- malware: Any type of malicious software.
- online auction fraud: When an item purchased through an online auction is never delivered after payment, or the item is not as specified by the seller.
- password: A secret combination of characters used to gain access to a computer, computer network, or other resource.
- pharming: The use of spoofed domain names to obtain personal information in order to use that information in fraudulent activities.
- phishing: The use of spoofed e-mail messages to gain credit card numbers and other personal data to be used for fraudulent purposes.
- possessed knowledge access system: An access control system that uses information only the individual should know to identify that individual.
- possessed object access system: An access control system that uses a physical object an individual has in his or her possession to identify that individual.
- private key encryption:A type of encryption that uses a single key to encrypt and decrypt the file or message.
- public key encryption: A type of encryption that uses key pairs to encrypt and decrypt the file or message.
- secure Web page: A Web page that uses encryption to protect information transmitted via that Web page.
- security software: Software, typically a suite of programs, used to protect your computer against a variety of threats.
- spear phishing: A personalized phishing scheme targeted at an individual.
- Trojan horse: A malicious program that masquerades as something else.
- two-factor authentication: Using two different methods to authenticate a user.
- unauthorized access: Gaining access to a computer, network, file, or other resource without permission.
- unauthorized use": Using a computer resource for unapproved activities.
- virtual private network (VPN):A private, secure path over the Internet that provides authorized users a secure means of accessing a private network via the Internet.
- war driving:Driving around an area with a Wi-Fi-enabled computer or mobile device to find a Wi-Fi network to access and use without authorization.
- Wi-Fi piggybacking:Accessing an unsecured Wi-Fi network from your current location without authorization.
Questions[edit | edit source]
Choose the correct option[edit | edit source]
1. Which of the following is an example of something used to gain access to a possessed object access system? [41]
a. password
b. smartcard
c. username
d. pin
2. The most common type of possessed knowledge, comprising secret words or character combinations associated with an individual, are:
a. security keys
b. passcodes
c. usernames
d. passwords
Fill in the blanks[edit | edit source]
3. Driving around looking for a Wi-Fi network to access is referred to as ________.
4. _______ access control systems use some type of unique physical characteristic of a person to authenticate that individual.
5. A(n) ____________ can be used at a Wi-Fi hotspot to create a secure path over the Internet.
6. A(n)____________ can be added to a file or an e-mail message to verify the identity of the sender and guarantee the file or message has not been changed.
7. ______________ identifies an individual based on their fingerprint, iris, or facial features or other unique physiological characteristic.
8. This type of theft/fraud is often targeted to social media sites because it is easier to find personal information on people.
True or false?[edit | edit source]
9. A computer virus can only be transferred to another computer via a storage medium.
10. An access control system that uses passwords is a possessed knowledge access system.
11. Using a password that is two characters long is an example of two-factor authentication.
12. Secure web pages use encryption to securely transfer data sent via those pages.
13. A virtual private link can be used at a Wi-Fi hotspot to create a secure path over the Internet.
Answers[42][edit | edit source]
- B
- D
- War Driving
- Biometric
- Virtual Private Network or VPN
- Digital Signature
- Biometric Access System
- Spear Phishing
- F
- T
- F
- T
- T
References[edit | edit source]
- ↑ http://us.norton.com/
- ↑ http://windows.microsoft.com/en-us/windows/security-essentials-download
- ↑ http://www.networkworld.com/article/2255950/lan-wan/chapter-1--types-of-firewalls.html
- ↑ http://www.bullguard.com/bullguard-security-center/pc-security/computer-security-resources/how-proxy-firewalls-work.aspx
- ↑ http://www.biometricupdate.com/201308/human-recognition-systems-integrates-biometric-access-control-with-cscs
- ↑ https://en.wikipedia.org/wiki/Access_control#Access_control_system_components
- ↑ http://en.wikipedia.org/wiki/Wardriving
- ↑ http://en.wikipedia.org/wiki/Keystroke_logging
- ↑ http://us.norton.com/travel-hotspot-security/article
- ↑ http://www.ucalgary.ca/it/help/articles/security/awareness/botnets
- ↑ http://www.ucalgary.ca/it/help/articles/security/awareness/botnets
- ↑ http://www.smithsonianmag.com/ist/?next=/science-nature/top-ten-most-destructive-computer-viruses-159542266/
- ↑ http://www.sans.edu/research/security-laboratory/article/alter-code
- ↑ http://en.wikipedia.org/wiki/Computer_crime
- ↑ http://www.nydailynews.com/news/facebook-hackers-french-president-nicolas-sarkozy-resign-article-1.150369
- ↑ http://www.britannica.com/EBchecked/topic/130595/cybercrime/235711/Sabotage
- ↑ http://law.justia.com/codes/nevada/2013/chapter-205/statute-205.481
- ↑ http://www.fbi.gov/news/pressrel/press-releases/ic3-2012-internet-crime-report-released
- ↑ http://money.howstuffworks.com/identity-theft.htm
- ↑ http://legal-dictionary.thefreedictionary.com/identity+theft
- ↑ http://www.consumer.ftc.gov/articles/0040-child-identity-theft
- ↑ https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
- ↑ https://en.wikipedia.org/wiki/Pharming
- ↑ http://highsecurity.blogspot.com/2007/02/pharming-and-drive-by-pharming.html
- ↑ US hospital pays $55,000 to hackers after ransomware attack|ZDNet
- ↑ http://electronics.howstuffworks.com/how-to-tech/how-to-protect-against-identity-theft2.htm
- ↑ https://www.fdic.gov/consumers/consumer/alerts/phishing.html
- ↑ http://www.microsoft.com/security/online-privacy/phishing-symptoms.aspx
- ↑ https://web.archive.org/web/20160313023806/http://technet.microsoft.com/en-us/library/dd361898.aspx
- ↑ http://www.xsitepro.com/the-pros-and-cons-of-using-paypal-as-your-primary-payment-processor.html
- ↑ http://www.express.co.uk/life-style/science-technology/591309/Apple-Pay-UK-Launch-Safe-Safer-Contactless-Credit-Debit-Card
- ↑ http://www.pcworld.com/article/130330/article.html
- ↑ http://www.stopbullying.gov/cyberbullying/what-is-it/index.html
- ↑ http://www.ncsl.org/research/telecommunications-and-information-technology/cyberstalking-and-cyberharassment-laws.aspx
- ↑ http://www.cyberangels.org/security/stalking.php
- ↑ http://www.popcenter.org/problems/child_pornography/
- ↑ http://www.cyberbullying.us/research.php
- ↑ http://www.antivirustalk.com/
- ↑ http://www.bloomberg.com/news/2013-07-25/5-hackers-charged-in-largest-data-breach-scheme-in-u-s-.html
- ↑ http://coursemate.cengage.com/CPReader/View/9781133114598/default.aspx?eISBN=9781133114598#53c50e83-32b2-46bf-8d09-fe73e2cb62b2
- ↑ http://coursemate.cengage.com/CPReader/View/9781133114598/default.aspx?eISBN=9781133114598#4dc6772a-b649-4893-be5d-6acb8ff8bead
- ↑ http://ng.cengage.com/static/nb/ui/index.html?nbId=7345&nbNodeId=1013914#!&parentId=1013935