FOSS Network Infrastructure and Security/Network Concepts and Architectures
Foreword — List of Abbreviations — Introduction to FOSS and GNU/Linux — Network Concepts and Architectures — Major Networking Functions with FOSS — Security Functions with FOSS — Network Planning — Further References — Glossary — About the Author — Acknowledgements — About APDIP — About IOSN
Computer Networks[edit | edit source]
A network is a mechanism that enables distributed computers and users to communicate and share resources. Sharing of resources may mean sharing a printer, a scanner or even a large hard disk on a particular computer. A computer network connects two or more computers or peripherals so that all users on the network have access to these resources.
There are two major types of computer networks:
- Server-based networks; and
- Peer-to-peer networks.
In a server-based network, there exists one or more computer(s) on which the resources are centralized. The network is also more or less controlled by the server. Servers generally have superior processing power, memory and hard disk space compared to desktop systems.
In a peer-to-peer network, all computers on the network are responsible for sharing resources. Each computer shares the resources that it has. All computers are servers as well as clients. There is no central control over the resources. Peer-to-peer networks are based on peer relationships among computers in the network.
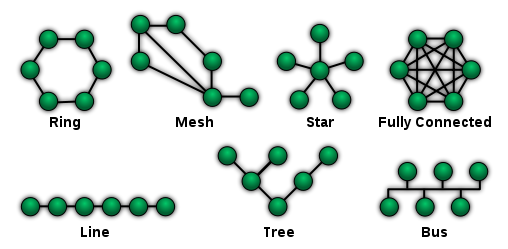
Network Topology[edit | edit source]
Topology refers to the arrangement of computers in a network. In physical terms, there are two main topologies that are commonly used:
- Bus topology
- Ring topology
The following additional topologies are not common, but are used as well, and you should be aware of them.
- Fully Connected topology
- Star topology
- Line topology
- Tree topology
- Mesh topology
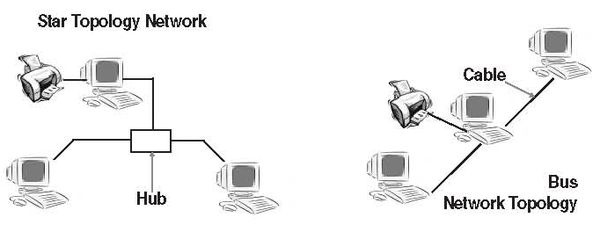
The simplest arrangement is Bus topology in which all computers are connected in a series to a single stretch of cable. This means that the entire length of the cable must be intact for the network to work properly; which makes larger networks prone to failure.
A hub or a switch is used as the central exchange point in a Star topology. All computers are connected to the hub in a star-like configuration of wires going in all directions from the hub. A Star topology is easier to maintain and to expand.
|
LAN Architecture[edit | edit source]
Two computers can communicate in different ways through different Local Area Network (LAN) architectures. Of the two well-known architectures — Ethernet and Token Ring — the former is more popular.
Ethernet[edit | edit source]
Ethernet is independent of any vendor, which accounts for its great success. Basic Ethernet architecture operates at a speed of 10 Mbps (mega bits per second). Other variations include Fast Ethernet, operating at 100 Mbps, and Gigabit Ethernet operating at 1 Giga bit per second. The Ethernet standards are referred to in the 802.nn notation, an Institute of Electrical and Electronics Engineers (IEEE) standard. WiFi (wireless fidelity) networks also follow the same standards, and are thus characterized as 802.11x.
Token Ring[edit | edit source]
Token-Ring LAN technology was developed and promoted by IBM in the early 1980s and was later standardized as IEEE 802.5. Initially very successful, its popularity went into steep decline after the introduction of the 10 Mbps Ethernet standard in the early 1990s.
Network Hardware[edit | edit source]
Network Cabling[edit | edit source]
Cables play a fundamental role in any network, and exist at the most primary level of the network. Two types of cables are in common use – co-axial cables (similar to cable TV cables) and twisted pair cables (similar to telephone cables). Co-axial cables are generally used with T-connectors in a Bus topology network. Twisted pair cables are used mostly in Hub-based networks.
Network Adapter Cards[edit | edit source]
Network Interface Cards (NICs) or Network Adapter Cards, as they are commonly known, provide an interface on the computer to connect to the network cable. Today, most computers come with a built-in network card. However, if it is not built into the system, an additional card can be inserted inside the computer, which will then connect to the network cable.
Networks Operation and Layers[edit | edit source]
Computer networks operate at different layers, each of which is independent of the others. The layers are stacked on top of each other, with each layer providing service to the layer above it. Network layers, as these layers are commonly known, provide general understanding of any computer network. A very simple form of these layers is illustrated below.
| Operating Software Layer (with Internet Protocol) | Network Applications | Application Layer |
| Transmission Control Protocol / User Datagram protocol | Transport Layer | |
| Internet Protocol | Network Layer | |
| Hardware Layer | Network Interface Card Drivers | Software/Hardware Layer |
| Network Interface Card Layer | Electronic Layer |
NIC Driver[edit | edit source]
An NIC driver provides a layer between the hardware and the software in any network. All network card manufacturers provide NIC drivers, which sometimes also come with the operating system.
Network Protocols[edit | edit source]
Network protocols provide a way for diverse computer hardware to communicate with each other in a standard way. These protocols follow set rules unique to themselves. Common network protocols are IP (commonly referred to as the Transmission Control Protocol/Internet Protocol or TCP/IP) and NetBEUI (NetBIOS Extended User Interface). Other protocols had been developed and used in the past, but IP has replaced most of these. NetBEUI is developed by Microsoft and is native to the Windows environment. IP is the Internet Protocol and is the most popular protocol today.
TCP/IP[edit | edit source]
TCP/IP are the basic protocols of the Internet. There are other protocols in TCP/IP like User Datagram Protocol (UDP). IP is the network layer and provides the basis for the network through the IP addresses. The IP address of each computer must be unique. TCP and UDP are the transport layers and are responsible for transport of network data packets.
IP addresses follow the format nnn.nnn.nnn.nnn (where nnn is any number from 0 to 255 including 0 and 255). A network mask separates the network address and the host address.
For internal network use, the IP range defined in Request For Comments (RFC) [1] 19184[2] should be used. These are 192.168.0.0 to 192.168.255.255, 172.16.0.0 to 172.31.255.255 and 10.0.0.0 to 10.255.255.255
Components of a Network[edit | edit source]
Network Operating System[edit | edit source]
A Network Operating System (NOS) is a network capable operating system that handles network resources and provides services like file and printer sharing. It is also capable of being an application server.
Users and Groups[edit | edit source]
Any NOS provides some form of security to its resources and services, the simplest being the user name & password pair. All users on the network are given a unique user name and they are also given a secret password. Only after verifying that a proper user name and password have been supplied does the NOS provide access to the designated network services.
A group is a collection of users in any network. A group is created to give similar rights to a group of users. Groups make administration and management easier.
Rights[edit | edit source]
Not all resources in a network may be available to everyone. It is necessary to shield some parts of the network from unauthorized use. So, all NOS provide rights to its users and groups. Users and groups are given only the required rights, while the more powerful rights are limited to the administrators.
Super User or Administrator[edit | edit source]
In most NOS, there is a super user or administrator who has absolute rights in the network system. In the UNIX and GNU/Linux environments, ‘root’ is the super user. An administrator is the supreme user in a Windows network. In NetWare networks, supervisors are super, meaning such users are capable of doing anything that the NOS permits. These accounts should be used with care.
Monitoring Network Performance[edit | edit source]
When users start complaining that the network is too slow, we know that there are problems in the network. Network performance must be monitored to find where the fault lies. It may lie in the network hardware or software.
Inferior grade cables and loose cable connections cause 80 percent of network problems and performance issues. High quality and prescribed cables and connectors should always be used. Another cause of problems may be the server hardware. Servers require more Random Access Memory (RAM). Some network performance problems call for the replacement of an older switch.
Unnecessary services running on the server should be stopped to get the maximum performance from the server. Every NOS provides some utility to monitor network performance, as well as server performance.
Troubleshooting the Network[edit | edit source]
The first step is to check the cables. After that, check the power connections to the network switch or resources on the network. If the problem is not solved, check the different services running on the server.
Role of FOSS in Networking[edit | edit source]
The Internet is the biggest example of the successful implementation of free and open source tools and software. It is the largest network in the world and its basis is the IP protocol. While it is true that the Internet has helped in the growth of FOSS in general, FOSS has also made the Internet a much more reliable network. Detailed information about the Internet Engineering Task Force (IETF), the protocol standards body of the Internet, and its implications as a FOSS reference implementation can be found in RFC 1718.
Limitations to the Use of FOSS[edit | edit source]
Yes, there are limitations. Most FOSS is produced in conformance to open standards and processes. There are proprietary software and processes that may not have a FOSS equivalent. Sometimes, it may also be necessary to use proprietary software to access certain types of hardware. Another limitation may be the rapid pace of development of FOSS. To an average user, this may be confusing but for service providers this is definitely an advantage.
Footnotes[edit | edit source]
- ↑ RFC stands for Request for Comments, which is the series of documentation for Internet Standards. RFC 1918 means RFC number 1918, which defines private use IP addresses. RFCs can be downloaded from http://www.faqs.org/rfcs/. We will refer to many RFCs for further reference throughout the e-primer.
- ↑ RFC 1918. ftp://ftp.rfc-editor.org/in-notes/rfc1918.txt